Business Problem
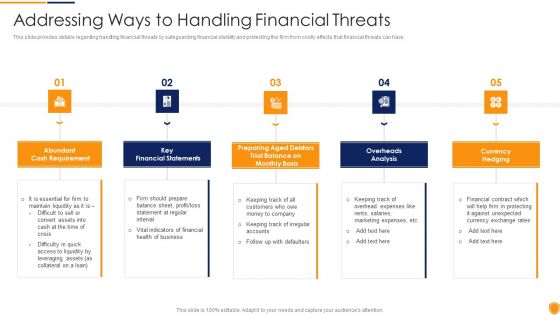
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Ways To Handling Professional PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting mitigating cybersecurity threats and vulnerabilities addressing ways to handling professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cash requirement, key financial statements, overheads analysis, currency hedging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
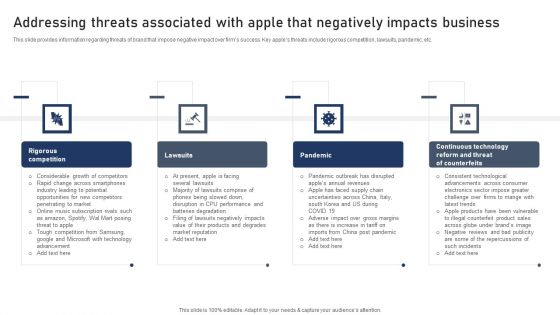
Discovering Apples Billion Dollar Branding Secret Addressing Threats Associated With Apple Negatively Impacts Portrait PDF
This slide provides information regarding threats of brand that impose negative impact over firms success. Key apples threats include rigorous competition, lawsuits, pandemic, etc. Boost your pitch with our creative Discovering Apples Billion Dollar Branding Secret Addressing Threats Associated With Apple Negatively Impacts Template PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Risks Associated With Event Planning And Management Stakeholder Engagement Plan For Launch Event Sample PDF
This slide provides an overview of risks faced by event planners. The risks covered are medical emergency, potential fire hazard, food safety and crowd management. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Risks Associated With Event Planning And Management Stakeholder Engagement Plan For Launch Event Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
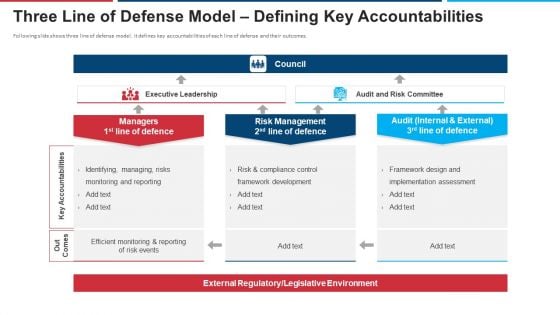
Mitigation Strategies For Operational Threat Three Line Of Defense Model Defining Key Accountabilities Ppt Summary Styles PDF
Following slide shows three line of defense model. It defines key accountabilities of each line of defense and their outcomes. Presenting mitigation strategies for operational threat three line of defense model defining key accountabilities ppt summary styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like managers, risk management, audit internal and external. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

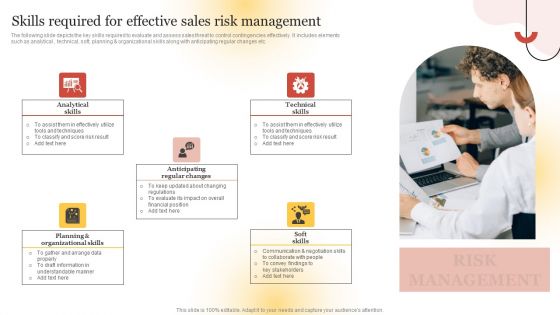
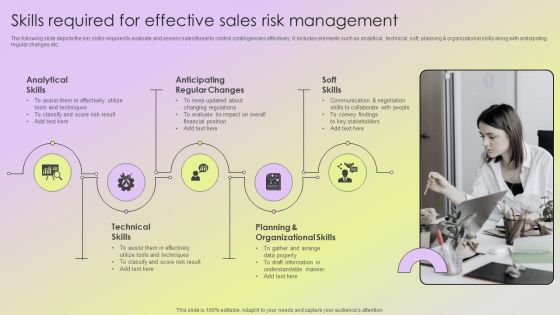
Performing Sales Risk Analysis Procedure Skills Required For Effective Sales Risk Management Ideas PDF
The following slide depicts the key skills required to evaluate and assess sales threat to control contingencies effectively. It includes elements such as analytical , technical, soft, planning and organizational skills along with anticipating regular changes etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Performing Sales Risk Analysis Procedure Skills Required For Effective Sales Risk Management Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Performing Sales Risk Analysis Procedure Skills Required For Effective Sales Risk Management Ideas PDF today and make your presentation stand out from the rest.
Executing Sales Risk Reduction Plan Skills Required For Effective Sales Risk Management Slides PDF
The following slide depicts the key skills required to evaluate and assess sales threat to control contingencies effectively. It includes elements such as analytical , technical, soft, planning and organizational skills along with anticipating regular changes etc. Find highly impressive Executing Sales Risk Reduction Plan Skills Required For Effective Sales Risk Management Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Executing Sales Risk Reduction Plan Skills Required For Effective Sales Risk Management Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Risk Detection And Management Five Steps For Risk Identification And Management Template PDF
This slide provides an overview of the risk identification process that helps to mitigate and manage project threats. Major steps covered are risk identification, analysis, prioritization, treatment and monitoring. Slidegeeks has constructed Risk Detection And Management Five Steps For Risk Identification And Management Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Ppt Round Arrow Speech Bubbles 2 Power Point Stage PowerPoint Templates
PPT round arrow speech bubbles 2 power point stage PowerPoint Templates-Use this PowerPoint Diagram to elaborate the Round Implementation through speech bubbles. This Diagram portrays the concepts of arrows pointing, circled, activity, analysis, arrows, business, medical, science, health and shapes.-PPT round arrow speech bubbles 2 power point stage PowerPoint Templates-Add, Aqua, Arrows, Badges, Bar, Blend, Blue, Bright, Bubbles, Buttons, Caution, Circle, Drop, Elements, Glossy, Glowing, Graphic, Heart, Help, Icons, Idea, Illustration, Navigation, Oblong, Plus, Round, Service, Shadow, Shiny, Sign, Speech, Squares With our Ppt Round Arrow Speech Bubbles 2 Power Point Stage PowerPoint Templates there is no end. They will take you even further.

Agenda For Risk Management Model For Data Security Structure PDF
This is a Agenda For Risk Management Model For Data Security Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Effectively Managing, Organizational Risks Arising, Threats And Vulnerabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
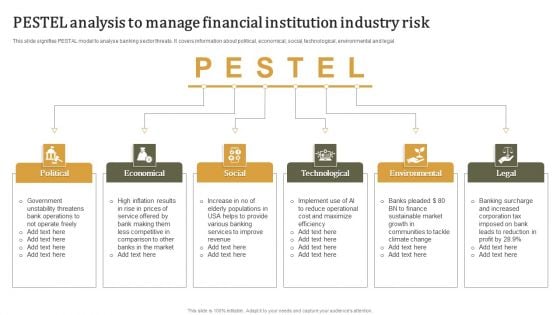
PESTEL Analysis To Manage Financial Institution Industry Risk Template PDF
This slide signifies PESTAL model to analyse banking sector threats. It covers information about political, economical, social, technological, environmental and legal. Presenting PESTEL Analysis To Manage Financial Institution Industry Risk Template PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Manage Financial, Institution Industry Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
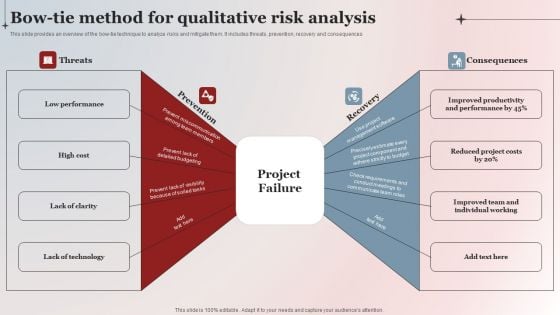
Bow Tie Method For Qualitative Risk Analysis Themes PDF
This slide provides an overview of the bow-tie technique to analyze risks and mitigate them. It includes threats, prevention, recovery and consequences. Presenting Bow Tie Method For Qualitative Risk Analysis Themes PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Low Performance, Lack Of Clarity, Lack Of Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mitigation Strategies Adopted By Food Retailers To Overcome Supply Chain Risks Information PDF
Following slide portrays information about the mitigation strategies adopted by the food retailers based on situational characteristics that in return will help them to overcome supply chain risks. This is a mitigation strategies adopted by food retailers to overcome supply chain risks information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategies, inventory, supply, manufacturing, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
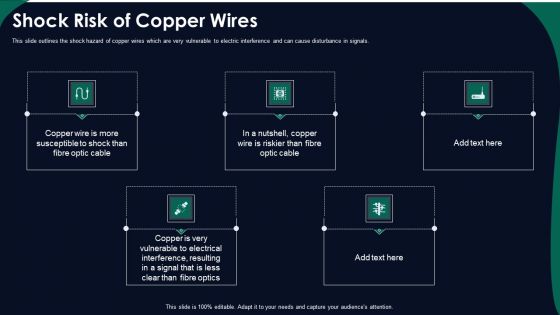
FDDI Network Standard IT Shock Risk Of Copper Wires Ppt Professional Smartart PDF
This slide outlines the shock hazard of copper wires which are very vulnerable to electric interference and can cause disturbance in signals. This is a fddi network standard it shock risk of copper wires ppt professional smartart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like shock risk of copper wires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

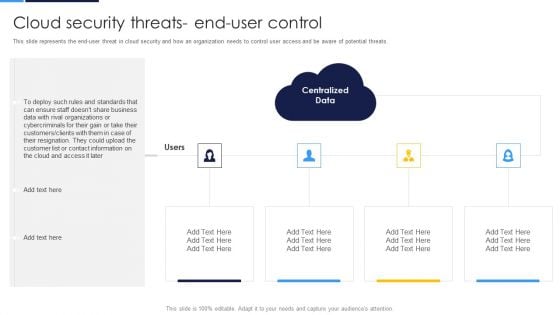
Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF
This slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer List, Rival Organizations, Could Upload. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cyber Threats, Organizations Could, Drastic Decrease. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Risks And Risk Mitigation Strategies Rules PDF
The slide shows the key risks operational risk, financial risk, reputation risk and mitigation strategies in the gym and fitness sector.This is a major risks and risk mitigation strategies rules pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operational risk, financial risk, reputation risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Investor Personality Template 1 Ppt PowerPoint Presentation Infographics Icons
This is a investor personality template 1 ppt powerpoint presentation infographics icons. This is a four stage process. The stages in this process are risk tolerance score, time horizon score.
Return On Investment Icons Ppt Powerpoint Presentation Gallery Brochure
This is a return on investment icons ppt powerpoint presentation gallery brochure. This is a two stage process. The stages in this process are risks, sales, capital, return, finance.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
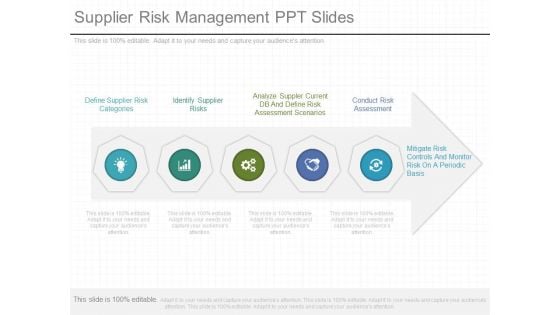
Supplier Risk Management Ppt Slides
This is a supplier risk management ppt slides. This is a five stage process. The stages in this process are define supplier risk categories, identify supplier risks, analyze suppler current db and define risk assessment scenarios, conduct risk assessment, mitigate risk controls and monitor risk on a periodic basis.\n\n\n\n\n\n\n\n\n\n\n\n
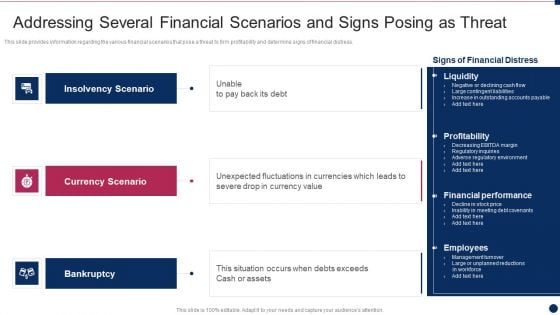
Threat Management At Workplace Addressing Several Financial Scenarios And Signs Portrait Pdf
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting threat management at workplace addressing several financial scenarios and signs portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like currency scenario, insolvency scenario, bankruptcy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
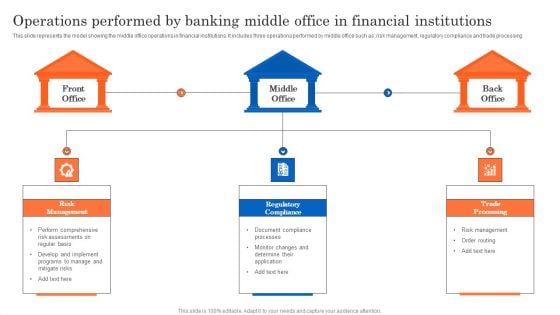
Operations Performed By Banking Middle Office In Financial Institutions Designs PDF
This slide represents the model showing the middle office operations in financial institutions. It includes three operations performed by middle office such as risk management, regulatory compliance and trade processing. Presenting Operations Performed By Banking Middle Office In Financial Institutions Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Front Office, Middle Office, Back Office, Risk Management, Regulatory Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sales Risk Assessment For Profit Maximization Skills Required For Effective Sales Risk Management Sample PDF
The following slide depicts the key skills required to evaluate and assess sales threat to control contingencies effectively. It includes elements such as analytical , technical, soft, planning and organizational skills along with anticipating regular changes etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Sales Risk Assessment For Profit Maximization Skills Required For Effective Sales Risk Management Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Mitigating Sales Risks With Strategic Action Planning Skills Required For Effective Sales Risk Management Brochure PDF
The following slide depicts the key skills required to evaluate and assess sales threat to control contingencies effectively. It includes elements such as analytical , technical, soft, planning and organizational skills along with anticipating regular changes etc. Slidegeeks is here to make your presentations a breeze with Mitigating Sales Risks With Strategic Action Planning Skills Required For Effective Sales Risk Management Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Law And Governance Icons Set Ppt PowerPoint Presentation Inspiration Design Templates
This is a law and governance icons set ppt powerpoint presentation inspiration design templates. This is a two stage process. The stages in this process are risk management icon, governance icon, compliance icon.

Risks Involved And Mitigation Strategies To Eliminate Risks Brochure PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, and Key Strategies or Measures for effectively mitigating the risk. This is a risks involved and mitigation strategies to eliminate risks brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like skilled labor shortage, technology failure risk, high competition risk, recruitment processes mitigation strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Risk Intelligence Services For Enterprise Security Icons PDF
Persuade your audience using this cyber risk intelligence services for enterprise security icons pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including incident resolution, threat protection, it services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
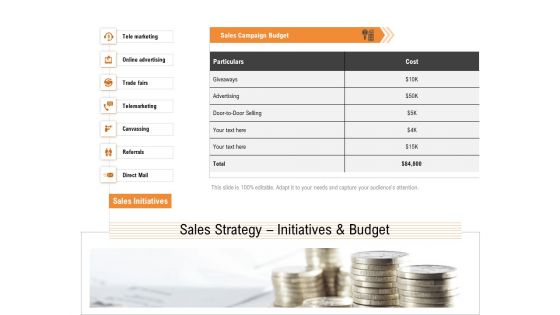
Opportunities And Threats For Penetrating In New Market Segments Sales Strategy Initiatives And Budget Sample PDF
Presenting opportunities and threats for penetrating in new market segments sales strategy initiatives and budget sample pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like tele marketing, online advertising, trade fairs, telemarketing, canvassing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
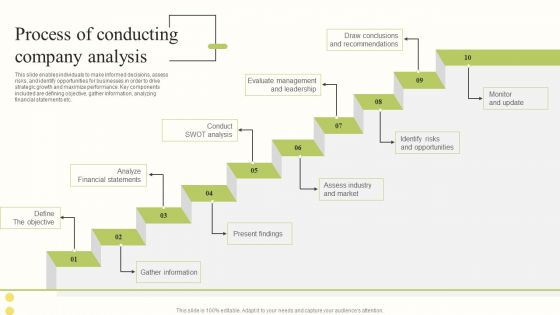
Comprehensive Company Profiling For A Coaching Firm Process Of Conducting Company Analysis Information PDF
This slide enables individuals to make informed decisions, assess risks, and identify opportunities for businesses in order to drive strategic growth and maximize performance. Key components included are defining objective, gather information, analyzing financial statements etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comprehensive Company Profiling For A Coaching Firm Process Of Conducting Company Analysis Information PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Best Practices In Risk Reporting Plan Of Construction Sites Icons PDF
The following slide presents the best practices that can be implemented in the hazard communication plan of construction sites. Major tips include using warning signs, conducting regular safety inspections, safety consultant, etc. Presenting Best Practices In Risk Reporting Plan Of Construction Sites Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Use Warning Signs, Safety Consultant, Establish Communication Procedures. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
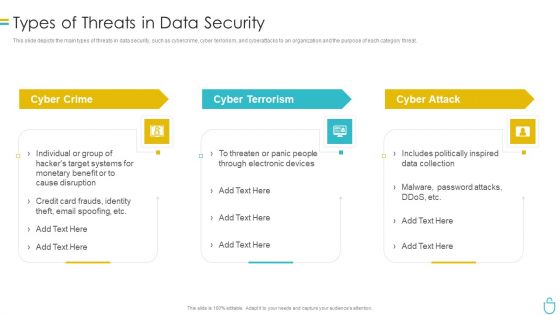
Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
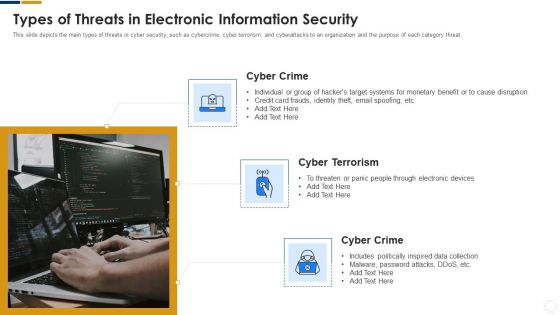
Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
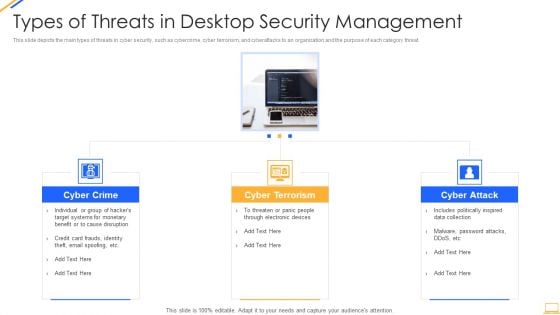
Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
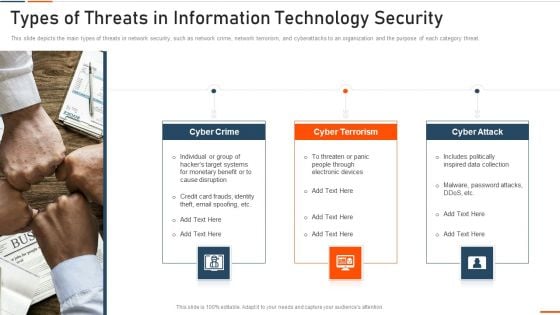
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
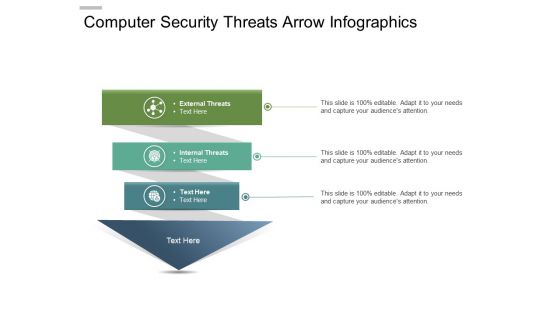
Computer Security Threats Arrow Infographics Ppt PowerPoint Presentation Gallery Background PDF
Presenting this set of slides with name computer security threats arrow infographics ppt powerpoint presentation gallery background pdf. This is a three stage process. The stages in this process are external threats, internal threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Threats Loss Of Data Cloud Computing Security IT Ppt Infographics Graphic Tips PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a cloud security threats loss of data cloud computing security it ppt infographics graphic tips pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like locations, cloud service, strategies, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
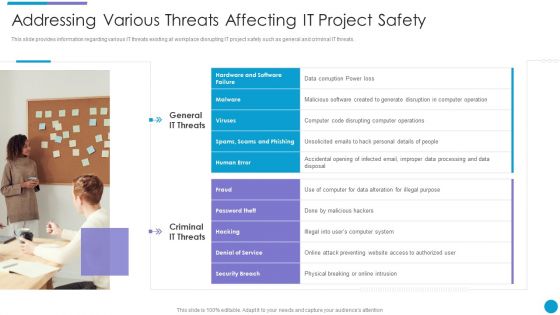
Major Techniques For Project Safety IT Addressing Various Threats Affecting IT Project Safety Structure PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. This is a major techniques for project safety it addressing various threats affecting it project safety structure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like general it threats, criminal it threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Addressing Various Threats Affecting It Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. This is a upgrading total project safety it addressing various threats affecting it project safety designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like general it threats, criminal it threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Assessment For Legal Regulations Ppt Risk Powerpoint Guide
This is a risk assessment for legal regulations ppt risk powerpoint guide. This is a five stage process. The stages in this process are compliance, rules, guidelines, regulations, laws.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risks Involved And Mitigation Strategies To Eliminate Risks Background PDF
This is a risks involved and mitigation strategies to eliminate risks background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like skilled labor shortage, technology failure risk, high competition risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
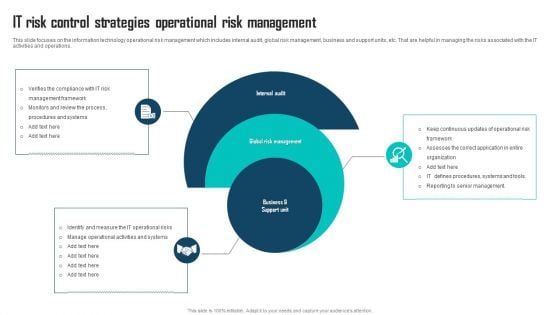
IT Risk Control Strategies Operational Risk Management Brochure PDF
Persuade your audience using this IT Risk Control Strategies Operational Risk Management Brochure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including IT Risk Control, Strategies Operational, Risk Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Company Project Planning Risk Identification Risk Ppt Styles Elements PDF
Presenting company project planning risk identification risk ppt styles elements pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like risk, severity, plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
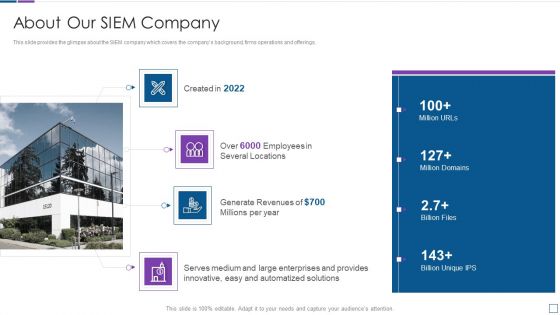
Real Time Assessment Of Security Threats About Our SIEM Company Structure PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a real time assessment of security threats about our siem company structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
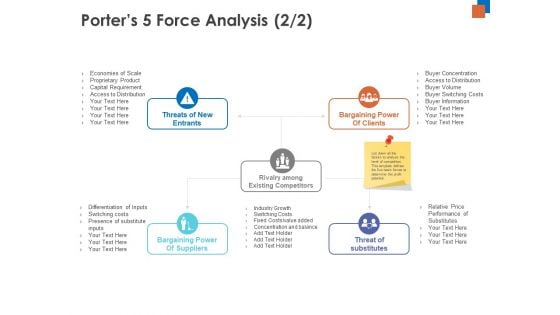
Micro Macro Environment Research Porters 5 Force Analysis Threat Ppt Ideas Aids PDF
Presenting this set of slides with name micro macro environment research porters 5 force analysis threat ppt ideas aids pdf. This is a five stage process. The stages in this process are threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute product or services, rivalry among competitors. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF
This slide covers the strategies that are been developed by doing the SWOT strengths, weakness, opportunities and threats analysis of an organization to help the managers or owners to make decisions accordingly.Persuade your audience using this Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Ineffective Marketing, Unable To Establish, Large Diversified Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Client Prospecting Risk Suitability Ppt Example
This is a client prospecting risk suitability ppt example. This is a five stage process. The stages in this process are client prospecting, risk suitability, account opening, periodic client review, marketing campaigns.
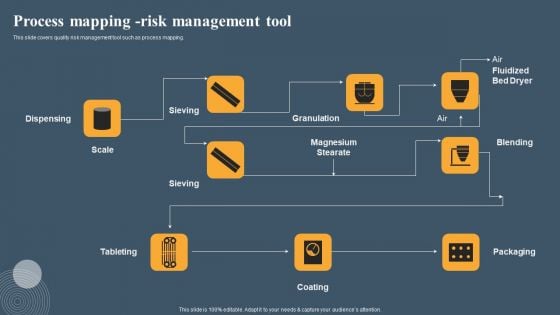
Risk Based Methodology Process Mapping Risk Management Tool Template PDF
This slide covers quality risk management tool such as process mapping. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Risk Based Methodology Process Mapping Risk Management Tool Template PDF from Slidegeeks and deliver a wonderful presentation.


 Continue with Email
Continue with Email

 Home
Home


































