Business Problem
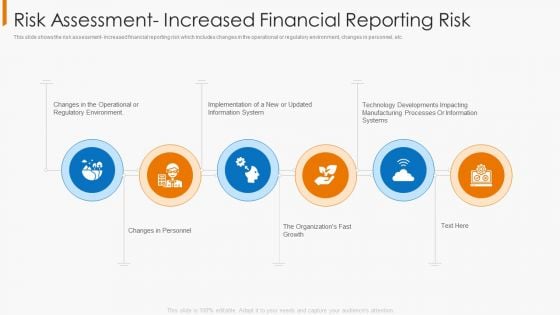
Risk Assessment Increased Financial Reporting Risk Themes PDF
This slide shows the risk assessment- increased financial reporting risk which includes changes in the operational or regulatory environment, changes in personnel, etc. Presenting risk assessment increased financial reporting risk themes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like environment, implementation, information system, manufacturing processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Configuration Risk Management And Risk Analysis Software Report Download PDF
This slide covers the summary status report of different risks and errors accumulated during system configuration. It includes data backup error, roll back of source code, data recovery failure, unauthorised access, etc. with solutions. Persuade your audience using this Configuration Risk Management And Risk Analysis Software Report Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Source Code, Data Backup Error, Risk Summary. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Risk Mitigation Strategies For Property Stakeholders Ideas PDF
Presenting Table Of Contents Risk Mitigation Strategies For Property Stakeholders Ideas PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Financial Performance, Real Estate Business, Risk Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

External Analysis In Strategic Management With Opportunity Threat Ppt PowerPoint Presentation Outline Styles
Presenting this set of slides with name external analysis in strategic management with opportunity threat ppt powerpoint presentation outline styles. This is a five stage process. The stages in this process are product, competitors, market, opportunity threat, distribution This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Assessment Vector Icon Ppt PowerPoint Presentation Outline Design Templates PDF
Presenting this set of slides with name threat assessment vector icon ppt powerpoint presentation outline design templates pdf. This is a three stage process. The stages in this process are threat assessment vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Downward Graph With Threat Symbol Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name downward graph with threat symbol vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are downward graph with threat symbol vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Program To Stop Virus Threats Ppt PowerPoint Presentation Portfolio Information PDF
Presenting this set of slides with name computer program to stop virus threats ppt powerpoint presentation portfolio information pdf. This is a three stage process. The stages in this process are computer program to stop virus threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Detected Message On Computer Monitor Ppt PowerPoint Presentation Icon Show PDF
Presenting this set of slides with name threat detected message on computer monitor ppt powerpoint presentation icon show pdf. This is a three stage process. The stages in this process are threat detected message on computer monitor. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Code On Computer For Cyber Threat Assessment Ppt PowerPoint Presentation File Infographics PDF
Presenting this set of slides with name code on computer for cyber threat assessment ppt powerpoint presentation file infographics pdf. This is a three stage process. The stages in this process are code on computer for cyber threat assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Expert Assessing Cyber Threats On Laptop Ppt PowerPoint Presentation Gallery Brochure PDF
Presenting this set of slides with name it expert assessing cyber threats on laptop ppt powerpoint presentation gallery brochure pdf. This is a three stage process. The stages in this process are it expert assessing cyber threats on laptop. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Scanning QR Code For Threat Detection Ppt PowerPoint Presentation File Structure PDF
Presenting this set of slides with name scanning qr code for threat detection ppt powerpoint presentation file structure pdf. This is a three stage process. The stages in this process are scanning qr code for threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Scanning For IT Security Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting this set of slides with name threat scanning for it security ppt powerpoint presentation gallery smartart pdf. This is a three stage process. The stages in this process are threat scanning for it security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Lock Shield For Virus Threat Ppt PowerPoint Presentation Gallery Outfit PDF
Presenting this set of slides with name security lock shield for virus threat ppt powerpoint presentation gallery outfit pdf. This is a three stage process. The stages in this process are security lock shield for virus threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
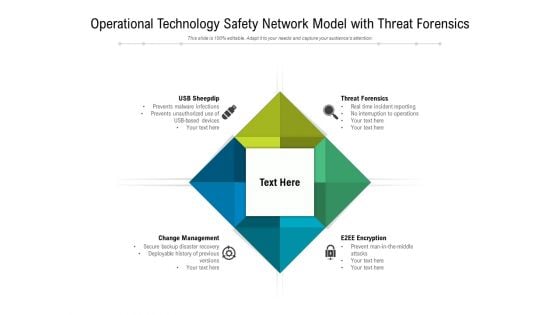
Operational Technology Safety Network Model With Threat Forensics Ppt PowerPoint Presentation Example File PDF
Presenting operational technology safety network model with threat forensics ppt powerpoint presentation example file pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including threat forensics, e2ee encryption, change management, usb sheepdip. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Emerging Threats In Cyber Security Ppt PowerPoint Presentation Model Images PDF
Presenting emerging threats in cyber security ppt powerpoint presentation model images pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including emerging threats in cyber security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Of Email Virus In Computer System Shape Ppt PowerPoint Presentation Inspiration Files PDF
Presenting threat of email virus in computer system shape ppt powerpoint presentation inspiration files pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including threat of email virus in computer system shape. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Crisis Management Icon With Threat Sign Ppt PowerPoint Presentation Inspiration Background PDF
Presenting crisis management icon with threat sign ppt powerpoint presentation inspiration background pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including crisis management icon with threat sign. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Virus Threat Vector Icon Ppt PowerPoint Presentation Professional Graphics Pictures PDF
Presenting computer virus threat vector icon ppt powerpoint presentation professional graphics pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer virus threat vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Clipboard With Threat Management Checklist Vector Icon Ppt PowerPoint Presentation Icon Outfit PDF
Presenting clipboard with threat management checklist vector icon ppt powerpoint presentation icon outfit pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including clipboard with threat management checklist vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Threat On Pc Monitor Vector Icon Ppt PowerPoint Presentation Layouts Information PDF
Presenting internet threat on pc monitor vector icon ppt powerpoint presentation layouts information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet threat on pc monitor vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Customer Getting Threat For The System Failure Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting customer getting threat for the system failure ppt powerpoint presentation gallery layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including customer getting threat for the system failure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vector Showing Protection Of Database From External Threats Ppt PowerPoint Presentation Styles Sample PDF
Presenting vector showing protection of database from external threats ppt powerpoint presentation styles sample pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including vector showing protection of database from external threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Global Warming Threat Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Presenting global warming threat vector icon ppt powerpoint presentation file microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including global warming threat vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
7 Petal Visual For Insider Threat Management Ppt PowerPoint Presentation File Brochure PDF
Presenting 7 petal visual for insider threat management ppt powerpoint presentation file brochure pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including 7 petal visual for insider threat management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Strengths Weaknesses Opportunities And Threats Analysis Matrix Icon With Arrows Icons PDF
Presenting Strengths Weaknesses Opportunities And Threats Analysis Matrix Icon With Arrows Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths Weaknesses, Opportunities Threats, Analysis Arrows This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strength Weakness Opportunity Threat Analysis Of Social Media Strategy Portrait PDF
Presenting Strength Weakness Opportunity Threat Analysis Of Social Media Strategy Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strength, Weakness, Threats, Opportunity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF
Presenting Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Survey Insights, Data Breach Threats, Incidents Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
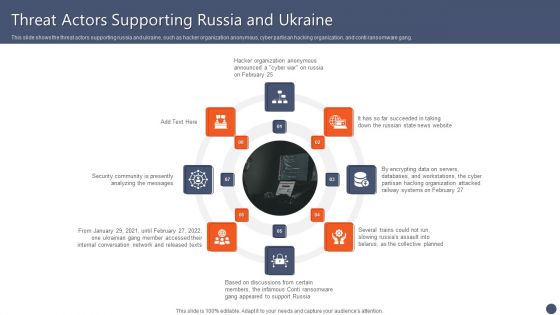
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
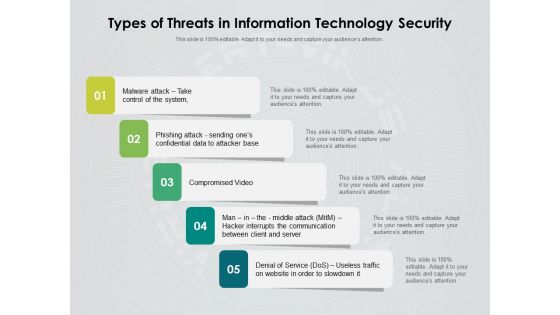
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
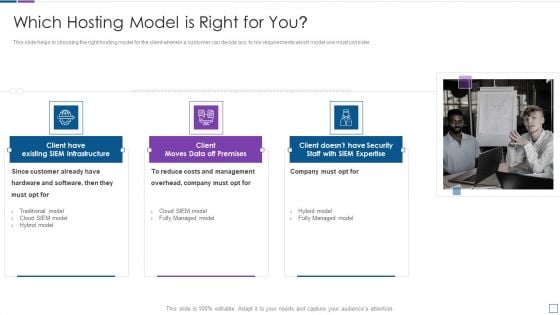
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
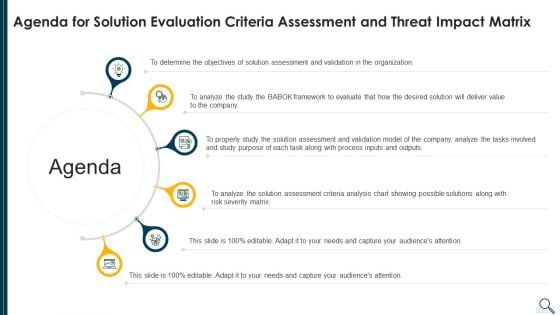
Agenda For Solution Evaluation Criteria Assessment And Threat Impact Matrix Summary PDF
This is a agenda for solution evaluation criteria assessment and threat impact matrix summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analyze, determine, organization, value, severity matrix. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
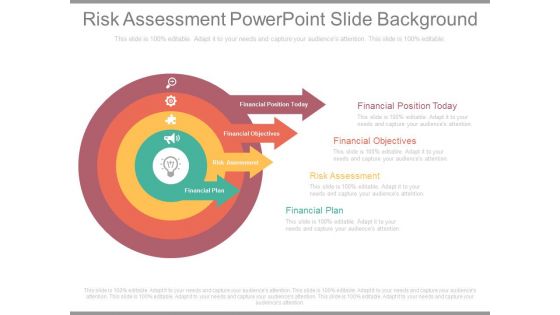
Risk Assessment Powerpoint Slide Background
This is a risk assessment powerpoint slide background. This is a four stage process. The stages in this process are financial position today, financial objectives, risk assessment, financial plan.
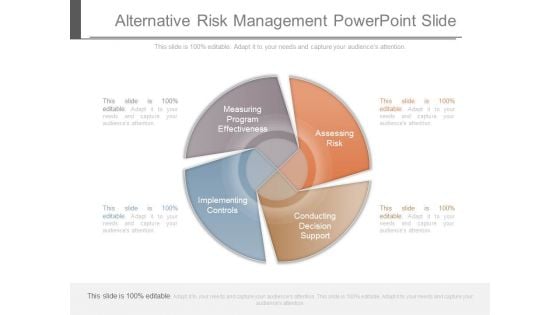
Alternative Risk Management Powerpoint Slide
This is a alternative risk management powerpoint slide. This is a four stage process. The stages in this process are measuring program effectiveness, assessing risk, implementing controls, conducting decision support.

OP Risk Management Budget For Operational Risk Management Pictures PDF
Mentioned slide shows budget for operational risk management. It includes information such as functional department, training course, training duration, training cost, number of employees and total training cost. Presenting op risk management budget for operational risk management pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like training duration, training course, employees to be trained. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
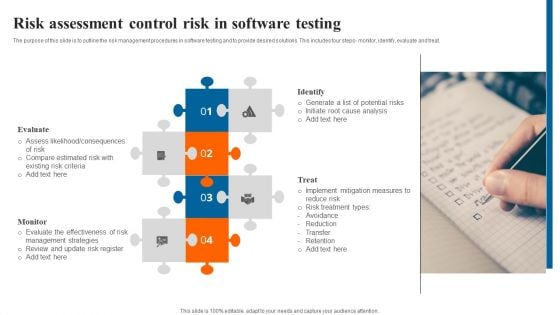
Risk Assessment Control Risk In Software Testing Themes PDF
The purpose of this slide is to outline the risk management procedures in software testing and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Persuade your audience using this Risk Assessment Control Risk In Software Testing Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Treat, Evaluate, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Methodology Common Quality Risk Management Tools Guidelines PDF
This slide covers most of the frequently used approaches for quality risk management including tools name, description, and applications. This modern and well-arranged Risk Based Methodology Common Quality Risk Management Tools Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Financial Instruments Comparative Statement Ppt Powerpoint Presentation Outline Objects
This is a financial instruments comparative statement ppt powerpoint presentation outline objects. This is a five stage process. The stages in this process are financial instruments, comparative statement, components of risk, financial risk identification, business.

Risk Identification Swot Analysis Procurement Risk Identification Sample PDF
This slide provides an overview of the SWOT analysis conducted to understand the strengths and determine areas of improvement. Major strengths covered are skilled workforce and good vendor network. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Risk Identification Swot Analysis Procurement Risk Identification Sample PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Risk Identification Swot Analysis Procurement Risk Identification Sample PDF today and make your presentation stand out from the rest.

Risk Assessment Key Steps To Perform Risk Analysis Download PDF
This slide provides an overview of the risk analysis process. Major steps covered are identifying risks and uncertainty, estimating impact, developing an analysis model, analyzing results and implementing solutions. Present like a pro with Risk Assessment Key Steps To Perform Risk Analysis Download PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Opportunities And Threats For Penetrating In New Market Segments Porters Five Forces Analysis Elements PDF
Presenting opportunities and threats for penetrating in new market segments porters five forces analysis elements pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like threat of new entrants, bargaining of suppliers, bargaining power of buyers, threat of substitute product or service, rivalry among existing competitors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
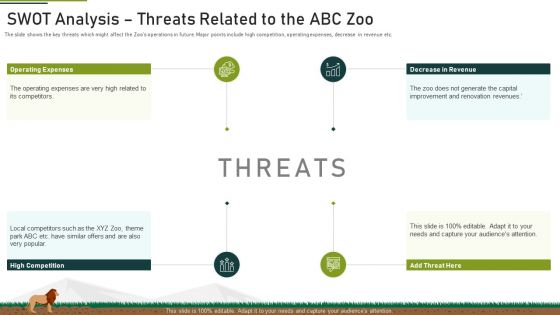
Swot Analysis Threats Related To The Abc Zoo Ppt Summary Rules PDF
The slide shows the key threats which might affect the Zoos operations in future. Major points include high competition, operating expenses, decrease in revenue etc. This is a swot analysis threats related to the abc zoo ppt summary rules pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operating expenses, high competition, decrease in revenue, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
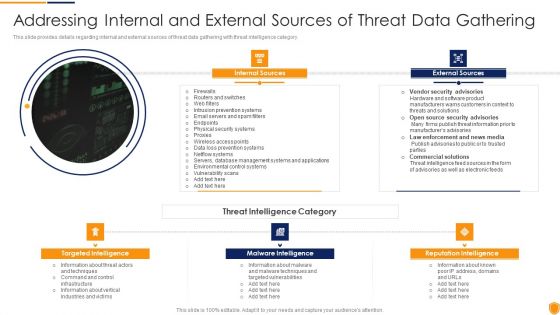
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Different Kinds Of Insider Information PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a mitigating cybersecurity threats and vulnerabilities different kinds of insider information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like different kinds of insider digital threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
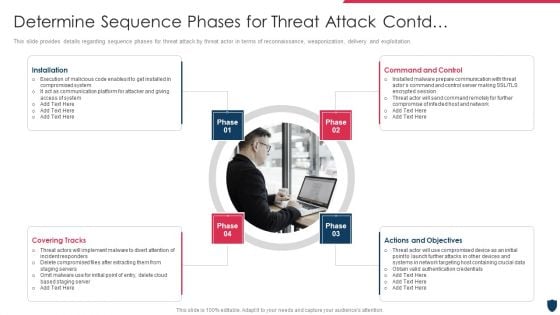
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
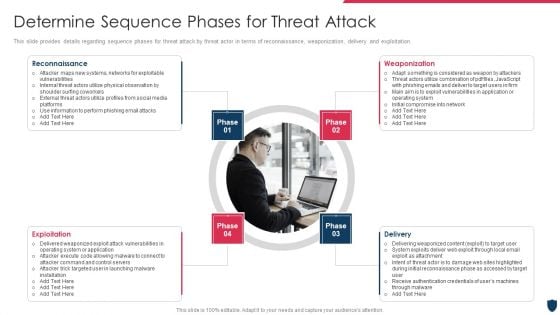
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
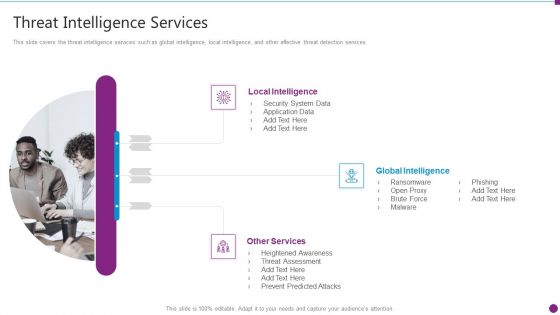
Security Information And Event Management Strategies For Financial Audit And Compliance Threat Intelligence Services Graphics PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting security information and event management strategies for financial audit and compliance threat intelligence services graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like local intelligence, global intelligence, other services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
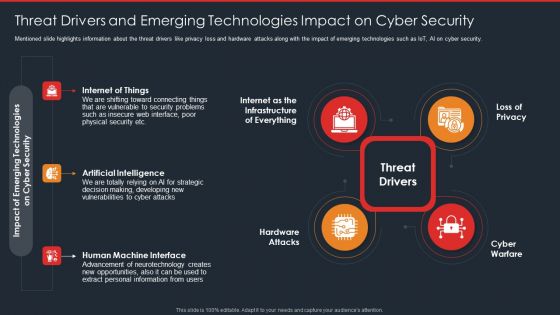
Data Safety Initiatives Threat Drivers And Emerging Technologies Impact On Cyber Security Brochure PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a data safety initiatives threat drivers and emerging technologies impact on cyber security brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat drivers, loss privacy, cyber warfare, hardware attacks, artificial intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
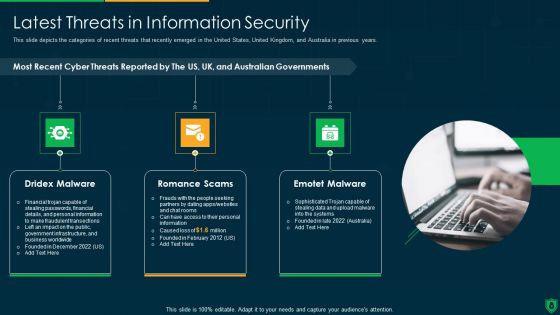
Info Security Latest Threats In Information Security Ppt PowerPoint Presentation Gallery Shapes PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a info security latest threats in information security ppt powerpoint presentation gallery shapes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like most recent, cyber threats reported, dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
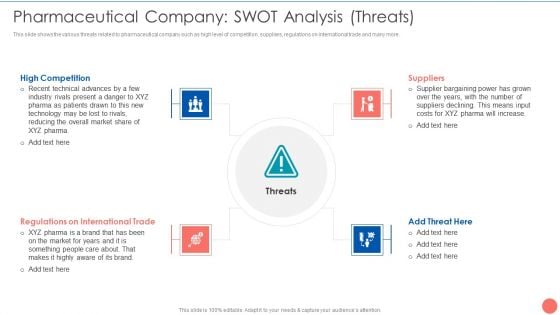
Tactics To Achieve Sustainability Pharmaceutical Company SWOT Analysis Threats Elements PDF
This slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Presenting Tactics To Achieve Sustainability Pharmaceutical Company SWOT Analysis Threats Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like High Competition Threats, Regulations International Trade, Suppliers Bargaining Power. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
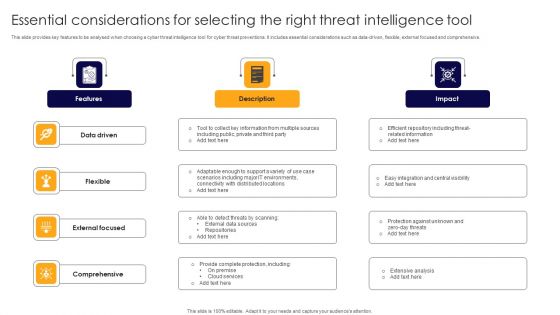
Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF
This slide provides key features to be analysed when choosing a cyber threat intelligence tool for cyber threat preventions. It includes essential considerations such as data-driven, flexible, external focused and comprehensive. Presenting Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Driven, Flexible, External Focused. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































