Business Security

Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112
We present our Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112.Use our Technology PowerPoint Templates because, The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business. Use our Business PowerPoint Templates because, Let your words be the drops of wisdom spreading knowledge and peace like ripples through the expectant minds of your devoted followers. Use our Computer PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Internet PowerPoint Templates because,The basic stages are in place, you need to build upon them with our PowerPoint templates. Use our Success PowerPoint Templates because, You have some great folks working with you, thinking with you.Use these PowerPoint slides for presentations relating to laptop screen, internet, computer, technology, business, success. The prominent colors used in the PowerPoint template are Gray, Blue, Black Your thoughts andour Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112 are destined to amalgamate. They will create a champion team.

Security And Performance Digital Marketing Build Personas And Value Props For The Targets Brochure PDF
This template covers the goal of profiling accounts, such as determining an accurate value proposition for each account. It also depicts that to get the compelling value proposition, companies have to research the role of the target and examine the targets perspective.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Build Personas And Value Props For The Targets Brochure PDF bundle. Topics like Value Proposition, Business Channels, Purchasing Characteristics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides
Arouses curiosity in the audience is the USP of this Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides. The image shown compliments the text provided. The holistic image conveys the message that we are on to something important, the deep world of business communication training. Download it now, and as always customize and edit each of the sixty five slides as per convenience and the data and the experience you are comfortable sharing with your audience.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
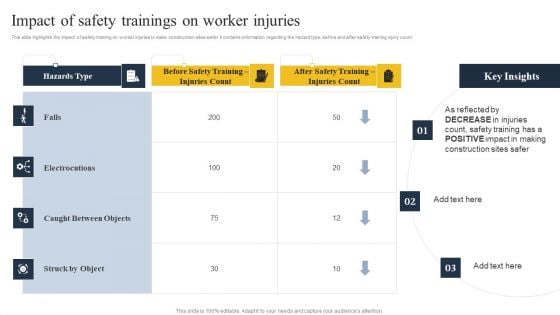
Security Control Techniques For Real Estate Project Impact Of Safety Trainings On Worker Injuries Ideas PDF
Retrieve professionally designed Security Control Techniques For Real Estate Project Impact Of Safety Trainings On Worker Injuries Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You donot have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Computer PowerPoint Templates because they pinpoint the core values of your organisation. Use our Technology PowerPoint Templates because these ideas abound in the strong branches of your brain. Download our Signs PowerPoint Templates because health of the determines the quality of our lives. Present our Business PowerPoint Templates because your fledgling career is in the chrysallis stage. Nurture it and watch it grow into a beautiful butterfly. Download and present our Triangles PowerPoint Templates because it unravels each one for your audience while setting key timelines as you go along.Use these PowerPoint slides for presentations relating to Alert button on a black computer keyboard, computer, technology, signs, business, triangles. The prominent colors used in the PowerPoint template are Red, Black, Yellow. We assure you our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Customers tell us our keyboard PowerPoint templates and PPT Slides are Classic. You can be sure our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. People tell us our a PowerPoint templates and PPT Slides are Splendid. Presenters tell us our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Adorable. People tell us our technology PowerPoint templates and PPT Slides are Efficient. Spread your ideas far and wide. Our Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212 are dependable carriers.

Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.

Security Officer Service Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Security Officer Service Company Profile Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Data Safety Initiatives For Effective IT Security Threats Administration Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This data safety initiatives for effective it security threats administration ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112
We present our House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112.Use our Americana PowerPoint Templates because, The Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination. Use our Finance PowerPoint Templates because, This business powerpoint template helps expound on the logic of your detailed thought process to take your company forward. Use our Money PowerPoint Templates because, All elements of the venture are equally critical. Use our Sales PowerPoint Templates because, Unravel the desired and essential elements of your overall strategy.Use these PowerPoint slides for presentations relating to House made from hundred Americana Business Finance Money Sales. The prominent colors used in the PowerPoint template are Yellow, Gray, Black Attend to details with our House Made Of Dollars Golden Key Security PowerPoint Templates And PowerPoint Themes 1112. You will come out on top.
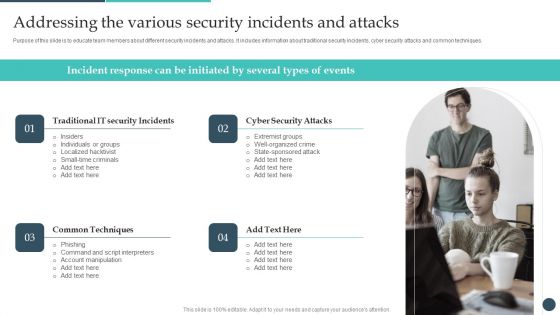
Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
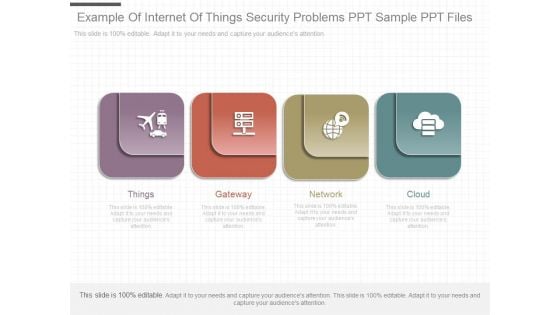
Example Of Internet Of Things Security Problems Ppt Sample Ppt Files
This is a example of internet of things security problems ppt sample ppt files. This is a four stage process. The stages in this process are things, gateway, network, cloud.
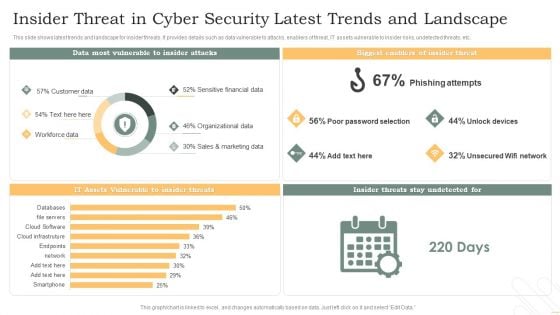
Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF
This slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF. The topics addressed in these templates are Phishing Attempts, Unlock Devices, Unsecured Wifi Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
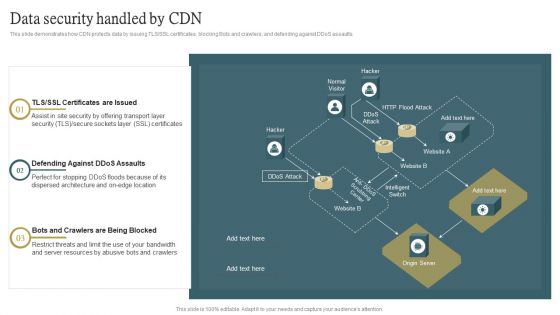
Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
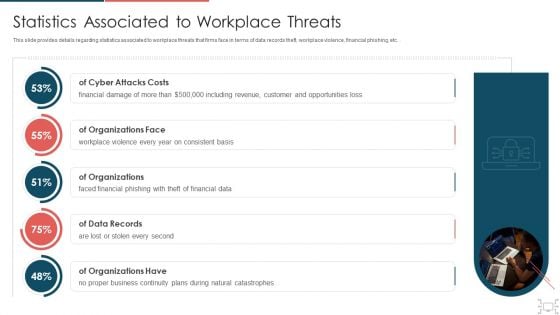
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Testimonials In The Security Guard Services Proposal Ppt Gallery Format Ideas PDF
This is a testimonials in the security guard services proposal ppt gallery format ideas pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like testimonials, security guard services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
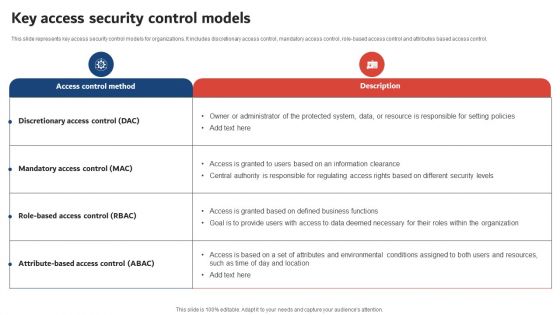
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
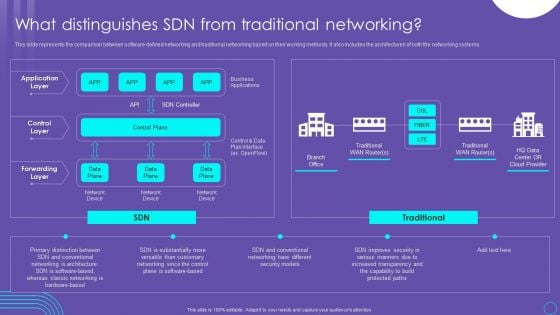
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
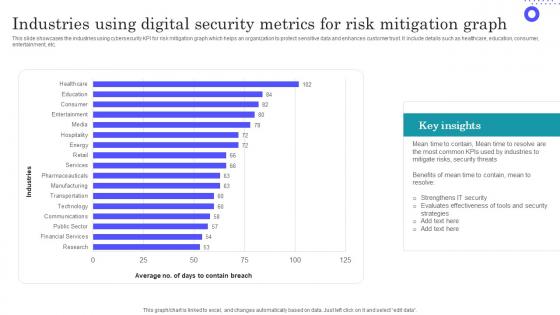
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
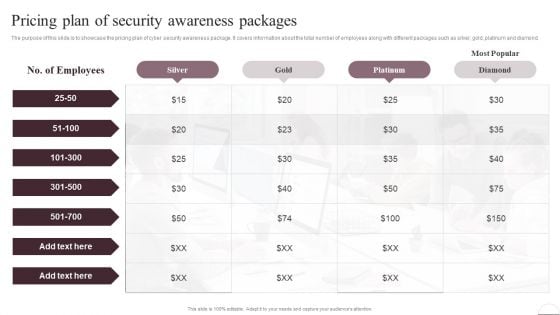
Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
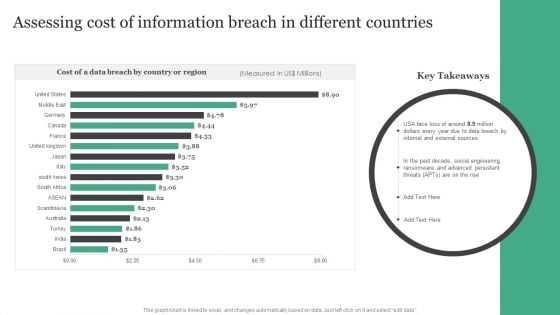
Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF
Retrieve professionally designed Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
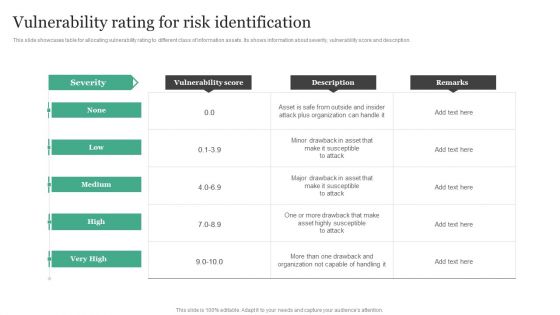
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF
Retrieve professionally designed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Location Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact urgency matrix for incidents prioritization location information pdf. Use them to share invaluable insights on business, location, inconvenient, moderate, preform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF today and make your presentation stand out from the rest.

Methods To Develop Advanced IT Security Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This methods to develop advanced it security monitoring plan ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty one slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
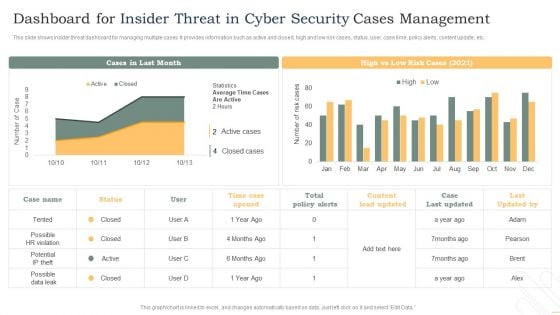
Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
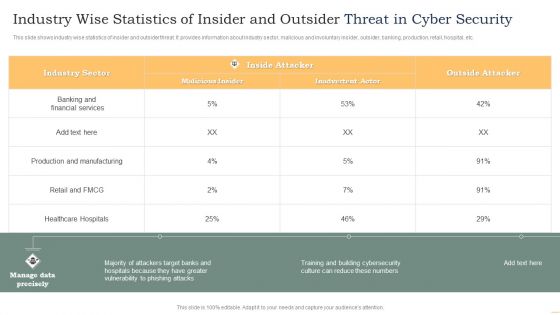
Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
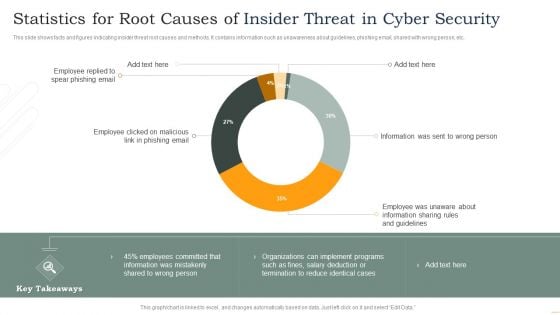
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
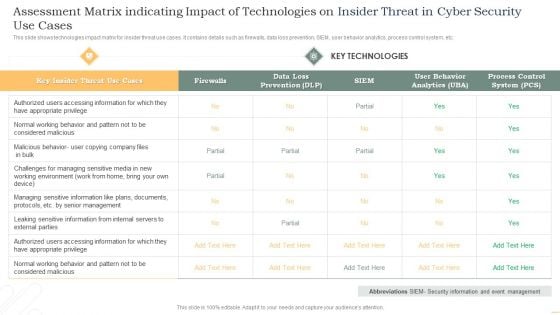
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
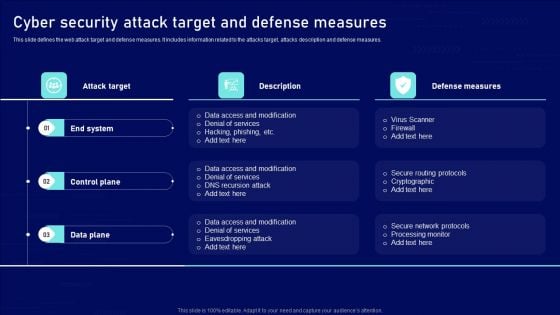
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
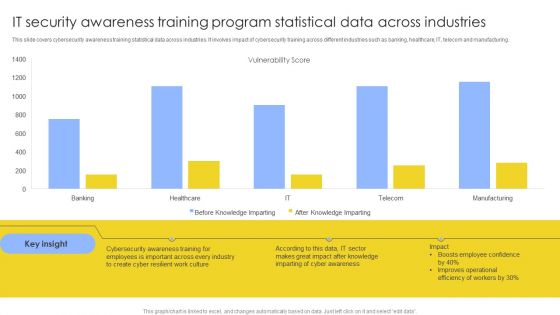
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
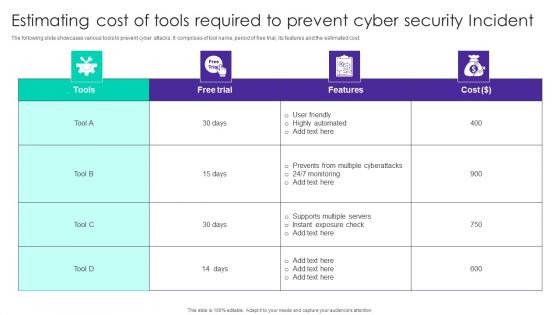
Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF
The following slide showcases various tools to prevent cyber attacks. It comprises of tool name, period of free trial, its features and the estimated cost. Showcasing this set of slides titled Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF. The topics addressed in these templates are Free Trial, Cost, User Friendly, Highly Automated. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Golden Key With Men Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with a man standing in a circle around a golden key Encourage entry into the area of excellence. Ease the doors open with our Golden Key With Men Security PowerPoint Templates And PowerPoint Backgrounds 0511.

Key With Dollar Finance Security PowerPoint Templates And PowerPoint Backgrounds 0911
Microsoft PowerPoint Template and Background with key made up of dollar sign and some dollars Our Key With Dollar Finance Security PowerPoint Templates And PowerPoint Backgrounds 0911 ensure a fair exchange. They give you many a penny for your thoughts.
Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a man standing in a circle around a golden key Bite the bullet with our Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511. Face the issues head-on.
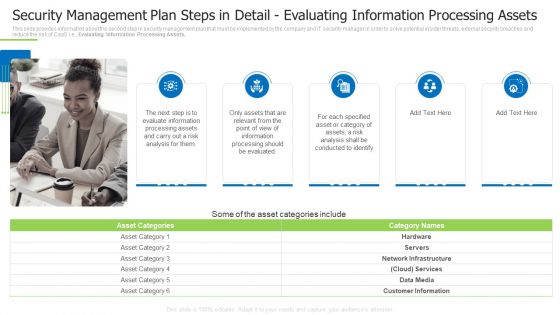
Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Template PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a way to overcome security monitoring challenges setting up an advanced cybersecurity template pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like establish security, monitoring strategy, supporting policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Prevention Of Information Roles And Responsibilities Of Cyber Security Team Icons PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Prevention Of Information Roles And Responsibilities Of Cyber Security Team Icons PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
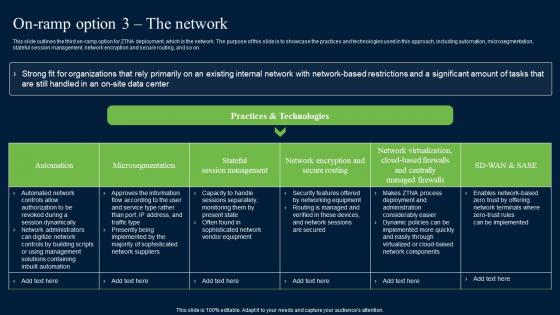
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
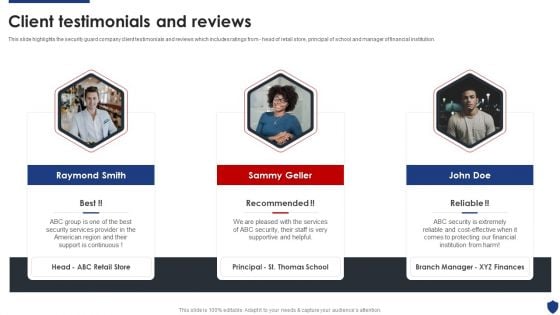
Security Officer Service Company Profile Client Testimonials And Reviews Sample PDF
This is a Security Officer Service Company Profile Client Testimonials And Reviews Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Our Financial, Support Continuous, Security Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
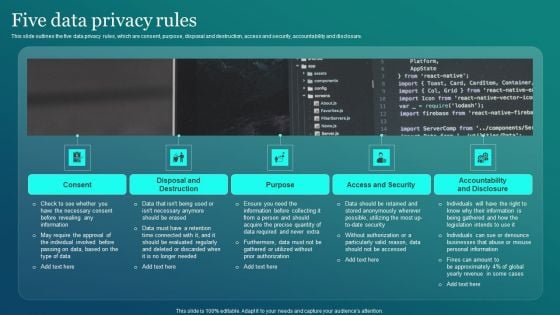
Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Slidegeeks is here to make your presentations a breeze with Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
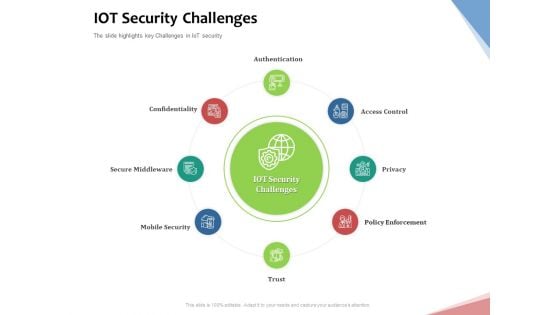
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
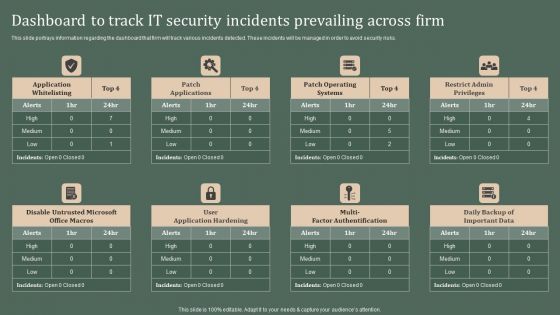
Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
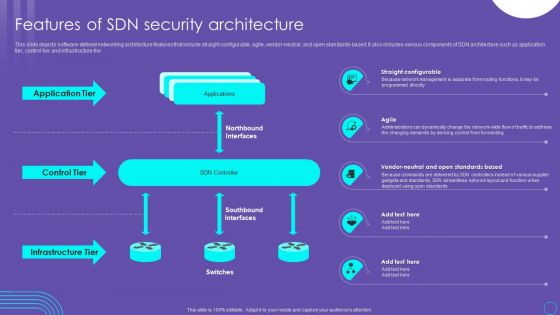
Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
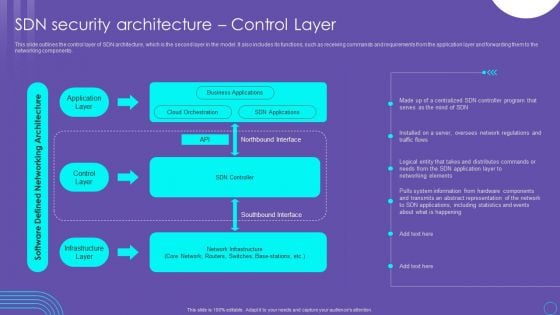
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF
Persuade your audience using this Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon, Cloud Security, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Firm Security Strategy Plan Contingency Plan For Threat Handling At Workplace Summary PDF
This slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative developing firm security strategy plan contingency plan for threat handling at workplace summary pdf bundle. Topics like server, website, local area network, wide area network, mainframe systems, distributes systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
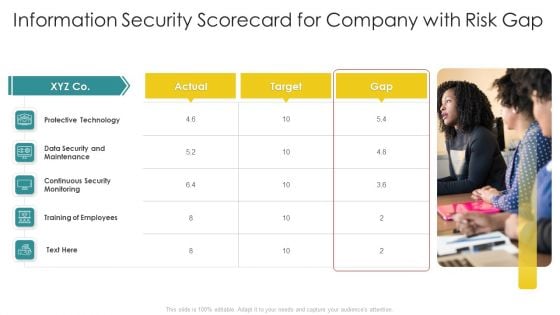
Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Camera System Company Profile Market Positioning With Technology Icons PDF
Presenting Security Camera System Company Profile Market Positioning With Technology Icons PDF to provide visual cues and insights. Share and navigate important information on One stage that need your due attention. This template can be used to pitch topics like Transformative, Security Experience, Service Capabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
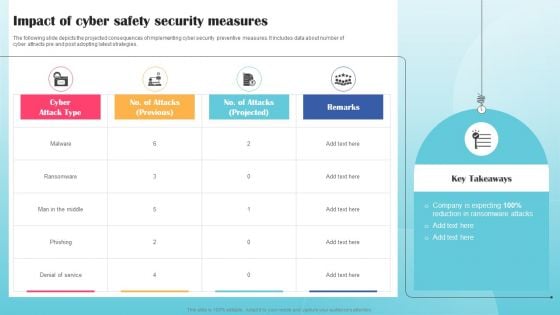
Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Slidegeeks has constructed Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
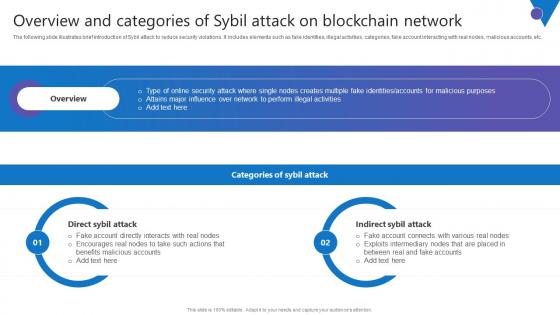
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































