Collateral Management
Security Dashboard Examples Ppt PowerPoint Presentation Infographics Background Cpb Pdf
Presenting this set of slides with name security dashboard examples ppt powerpoint presentation infographics background cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security dashboard examples to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Enterprise Security Review Ppt PowerPoint Presentation File Visuals Cpb Pdf
Presenting this set of slides with name enterprise security review ppt powerpoint presentation file visuals cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like enterprise security review to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Assessment Ppt PowerPoint Presentation File Infographics Cpb
Presenting this set of slides with name security assessment ppt powerpoint presentation file infographics cpb. This is an editable Powerpoint six stages graphic that deals with topics like security assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Company Security Policies Ppt PowerPoint Presentation Summary Portrait Cpb Pdf
Presenting this set of slides with name company security policies ppt powerpoint presentation summary portrait cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like company security policies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Assessment Checklist Ppt PowerPoint Presentation Model Rules Cpb Pdf
Presenting this set of slides with name security assessment checklist ppt powerpoint presentation model rules cpb pdf. This is an editable Powerpoint nine stages graphic that deals with topics like security assessment checklist to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Privileged Account Security Tools Ppt PowerPoint Presentation Styles Cpb Pdf
Presenting this set of slides with name privileged account security tools ppt powerpoint presentation styles cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like privileged account security tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
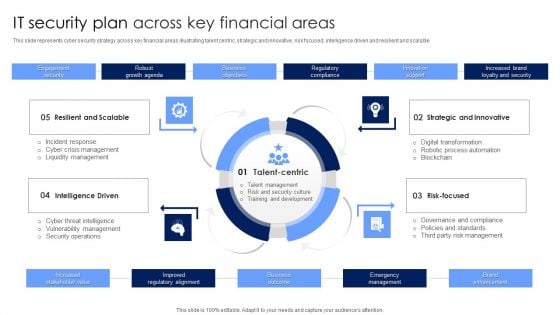
IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
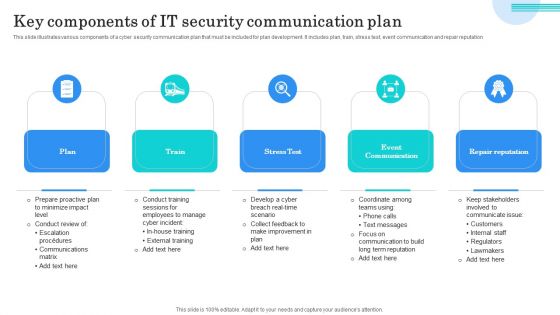
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Diagram Five Staged Colorful Key Diagram Text Boxes Presentation Template
This business diagram has been designed with graphic of five staged keys and text boxes. Download this diagram to analyze the key points. This diagram offers a way for your audience to visually conceptualize the process.
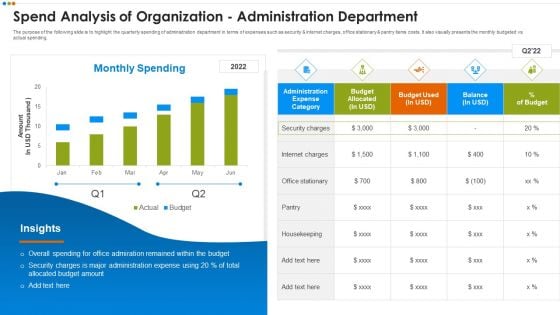
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
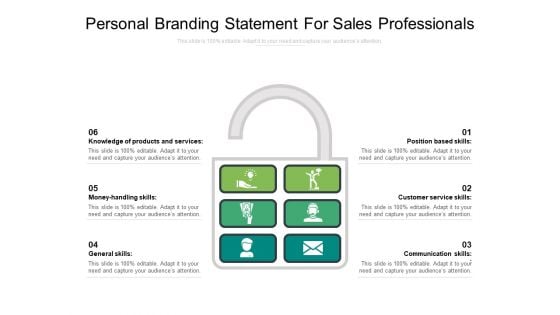
Personal Branding Statement For Sales Professionals Ppt PowerPoint Presentation Infographics Influencers PDF
Presenting this set of slides with name personal branding statement for sales professionals ppt powerpoint presentation infographics influencers pdf. This is a six stage process. The stages in this process are position based skills, customer service skills, communication skills, knowledge of products and services, money handling skills, general skills. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
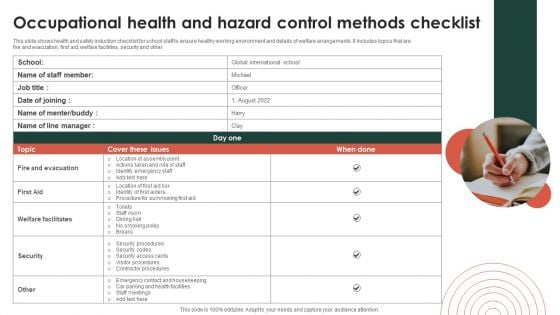
Occupational Health And Hazard Control Methods Checklist Ppt Pictures Themes PDF
This slide shows health and safety induction checklist for school staff to ensure healthy working environment and details of welfare arrangements. It includes topics that are fire and evacuation, first aid, welfare facilities, security and other. Presenting Occupational Health And Hazard Control Methods Checklist Ppt Pictures Themes PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Fire And Evacuation, Cover These Issues, Welfare Facilitates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
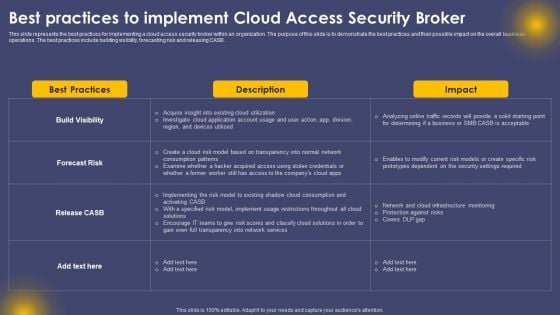
Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. There are so many reasons you need a Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
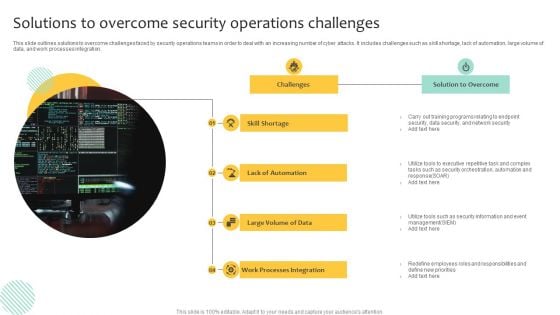
Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Operating Systems Security Auditing Procedures Ppt PowerPoint Presentation Slides Gallery Cpb
Presenting this set of slides with name operating systems security auditing procedures ppt powerpoint presentation slides gallery cpb. This is an editable Powerpoint four stages graphic that deals with topics like operating systems security auditing procedures to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Circle Procedure Slide Of Hybrid Cloud Security System Requirements Ppt Infographic Template Graphics Pictures PDF
Persuade your audience using this circle procedure slide of hybrid cloud security system requirements ppt infographic template graphics pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure slide of hybrid cloud security system requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
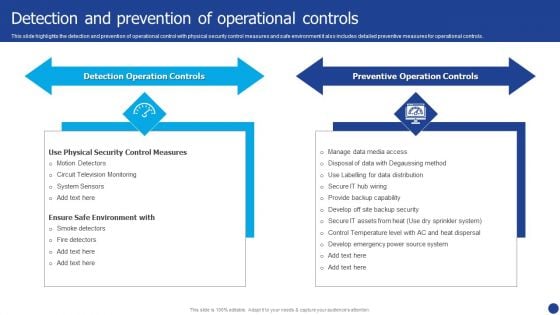
Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
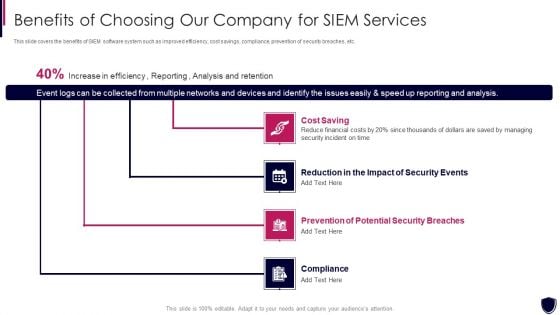
Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Sample Business Process Flow Diagram Bar Graph PowerPoint Templates Ppt Backgrounds For Slides
We present our sample business process flow diagram bar graph PowerPoint templates PPT backgrounds for slides.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Present our People PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Present our Marketing PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Present our Leadership PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate.Use these PowerPoint slides for presentations relating to 3d, administrative, arrow, business, businessman, chart, colleague, community, conference, cooperation, director, discussion, finance, financial, graph, growth, guy, human, icon, idea, leader, leadership, manager, meeting, men, occupation, office, organization, partnership, people, person, plan, presentation, problem, project, round, session, sitting, slump, staff, stockholder, table, talking, team, teamwork, thinking, tie, white, women, worker. The prominent colors used in the PowerPoint template are Green, Gray, Black. PowerPoint presentation experts tell us our sample business process flow diagram bar graph PowerPoint templates PPT backgrounds for slides are incredible easy to use. Use our colleague PowerPoint templates and PPT Slides look good visually. You can be sure our sample business process flow diagram bar graph PowerPoint templates PPT backgrounds for slides will make the presenter successul in his career/life. Presenters tell us our colleague PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. You can be sure our sample business process flow diagram bar graph PowerPoint templates PPT backgrounds for slides will make the presenter successul in his career/life. Professionals tell us our chart PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Edit plans with our Sample Business Process Flow Diagram Bar Graph PowerPoint Templates Ppt Backgrounds For Slides. Download without worries with our money back guaranteee.
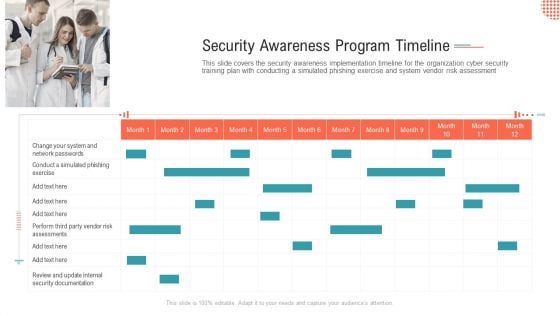
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
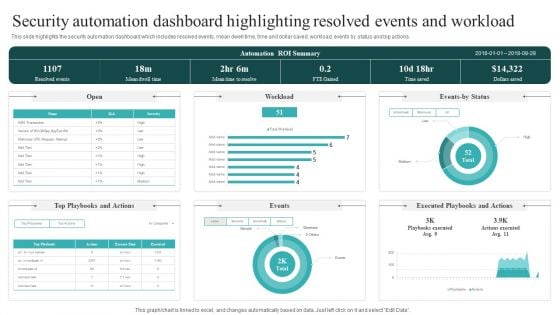
Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. This Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
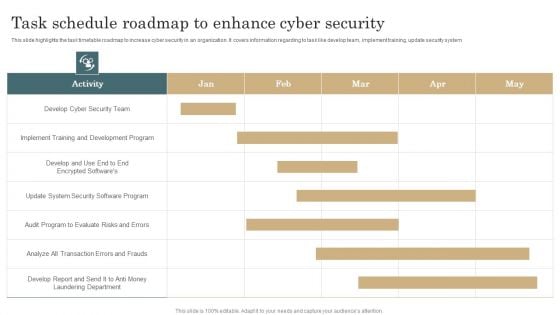
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Security Gap Analysis With Risk Level Information PDF
The following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Pitch your topic with ease and precision using this Information Technology Security Gap Analysis With Risk Level Information PDF. This layout presents information on Organize Security, Regularly Analyze, Gap Assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
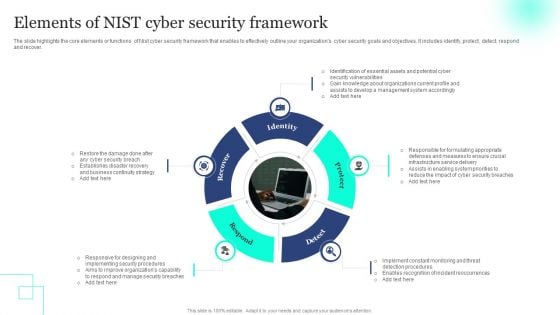
Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
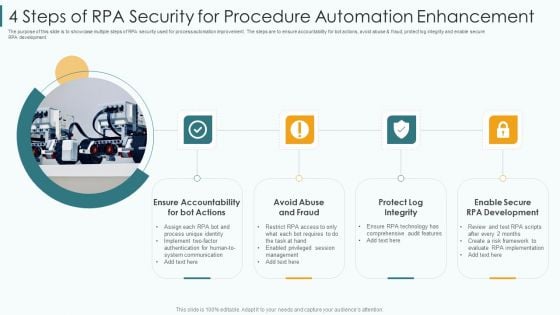
4 Steps Of RPA Security For Procedure Automation Enhancement Slides PDF
The purpose of this slide is to showcase multiple steps of RPA security used for process automation improvement. The steps are to ensure accountability for bot actions, avoid abuse and fraud, protect log integrity and enable secure RPA development. Presenting 4 steps of rpa security for procedure automation enhancement slides pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication, implement, requires. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Our Strategies To Secure Network Load Balancer Ppt Outline Topics PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. Presenting our strategies to secure network load balancer ppt outline topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like our strategies to secure network load balancer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
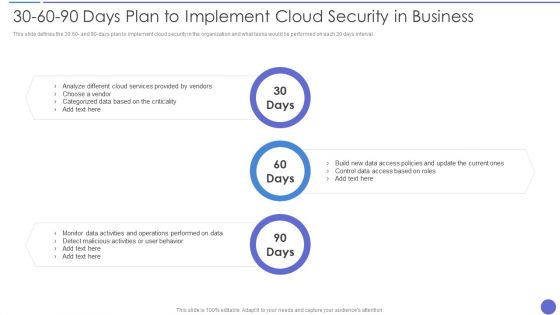
30 60 90 Days Plan To Implement Cloud Security In Business Information PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 Days Plan To Implement Cloud Security In Business Information PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Cloud Services Provided , Control Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
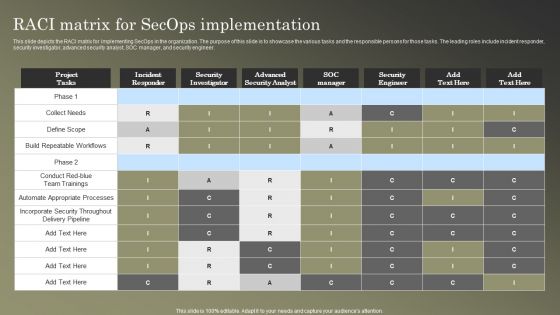
Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF
This slide depicts the RACI matrix for implementing SecOps in the organization. The purpose of this slide is to showcase the various tasks and the responsible persons for those tasks. The leading roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Present like a pro with Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
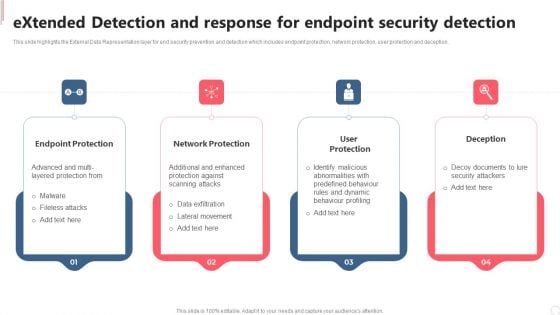
Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.

Information Technology Security Risk Assessment Framework Demonstration PDF
The following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting Information Technology Security Risk Assessment Framework Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
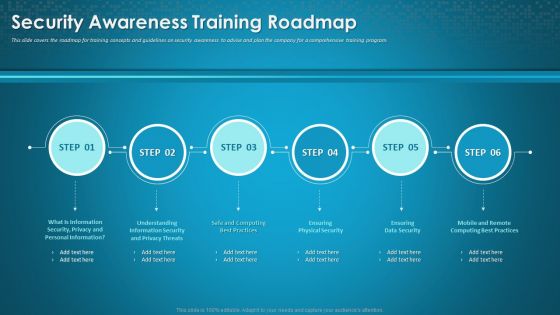
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
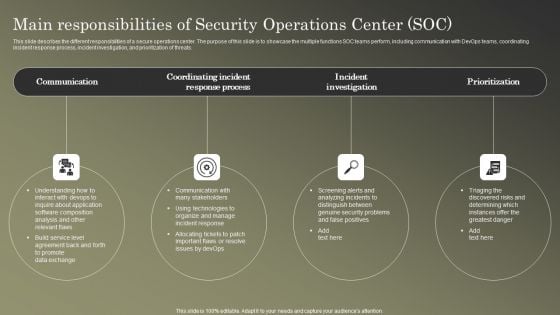
Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF
This slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. There are so many reasons you need a Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
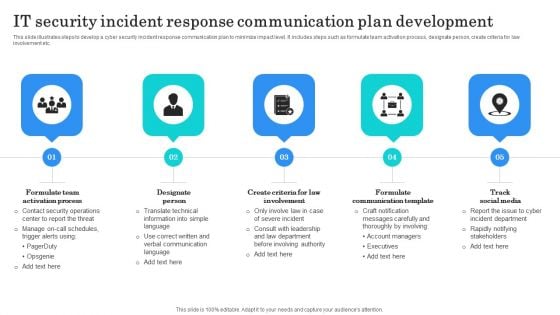
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
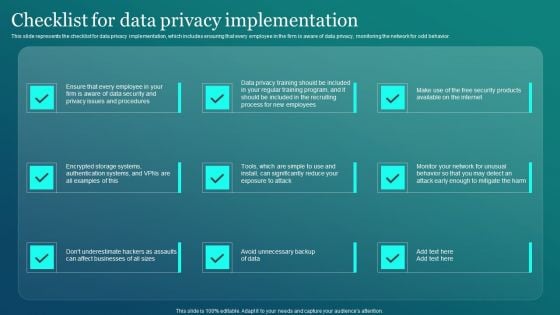
Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
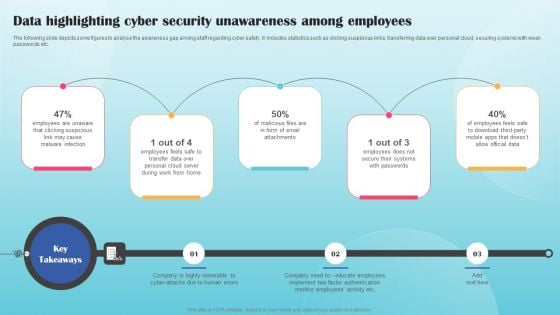
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
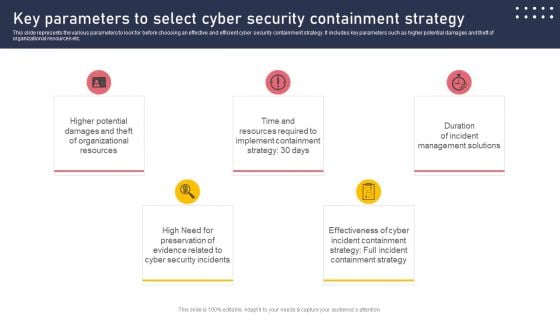
Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
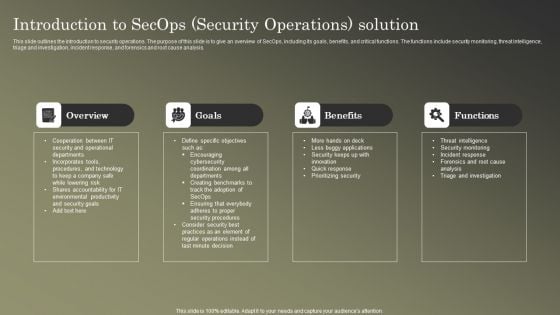
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Data Governance And Security Model Vector Icon Ppt PowerPoint Presentation Show PDF
Pitch your topic with ease and precision using this data governance and security model vector icon ppt powerpoint presentation show pdf. This layout presents information on data governance and security model vector icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Protection Of Environment Is Very Important PowerPoint Templates Ppt Backgrounds For Slides 0513
When in doubt use our Protection Of Environment Is Very Important PowerPoint Templates PPT Backgrounds For Slides. The way ahead will become crystal clear. With our Umbrellas PowerPoint Templates you will be doubly sure. They possess that stamp of authority. Our Globe PowerPoint Templates do it in double quick time. Speed up the process in a tangible way. Spread it out in equal doses. Get the portions right with our Protection Of Environment Is Very Important PowerPoint Templates Ppt Backgrounds For Slides 0513.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Security Systems Trendy Business Ppt PowerPoint Presentation Gallery Objects
This is a security systems trendy business ppt powerpoint presentation gallery objects. This is a six stage process. The stages in this process are security systems, trendy business.

Enterprise Security Tools Ppt PowerPoint Presentation Infographics Skills Cpb
This is a enterprise security tools ppt powerpoint presentation infographics skills cpb. This is a four stage process. The stages in this process are enterprise security tools.
Security Workforce Ppt PowerPoint Presentation Infographics Format Ideas Cpb
This is a security workforce ppt powerpoint presentation infographics format ideas cpb. This is a five stage process. The stages in this process are security workforce.
Online Security Ppt PowerPoint Presentation Pictures Layout Ideas Cpb
This is a online security ppt powerpoint presentation pictures layout ideas cpb. This is a four stage process. The stages in this process are online security.

Cybersecurity Security Framework In Cloud Computing Ppt Portfolio Grid PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a cybersecurity security framework in cloud computing ppt portfolio grid pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, identify, protect, detect, respond. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
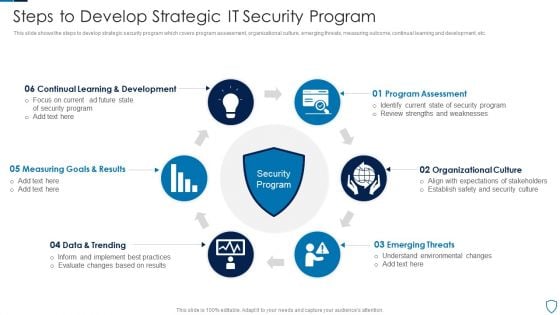
Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
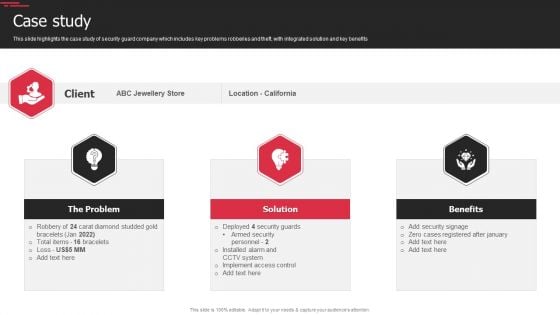
Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Case Study Mockup PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. This is a Manpower Corporate Security Business Profile Case Study Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solution, Benefits, The Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
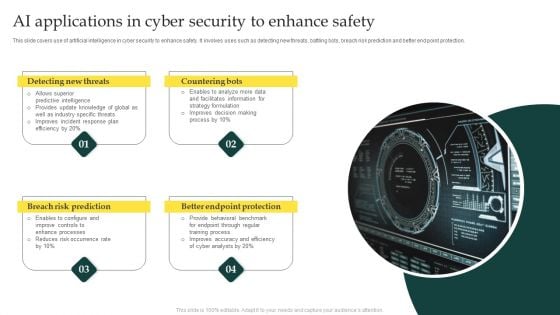
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
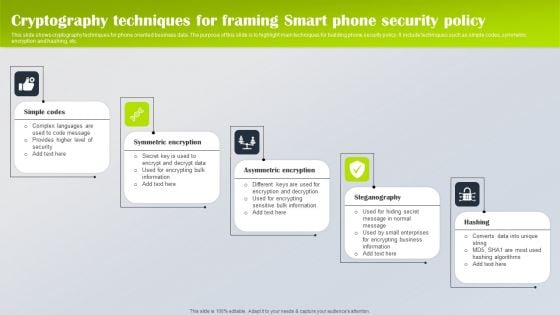
Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF
This slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Simple Codes, Symmetric Encryption, Asymmetric Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
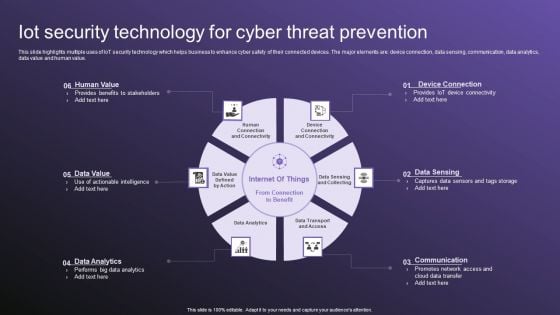
Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Firm Security Strategy Plan Impact Of Critical Security Concerns Issues On Overall Firms Performance Pictures PDF
This slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Deliver an awe inspiring pitch with this creative developing firm security strategy plan impact of critical security concerns issues on overall firms performance pictures pdf bundle. Topics like loss in sales, customer dissatisfaction, tarnished reputation, decrease in customer loyalty, increase in expenses can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
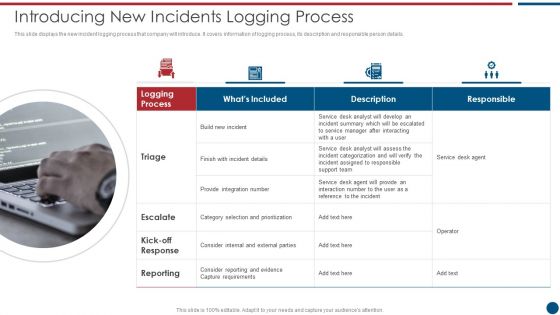
Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
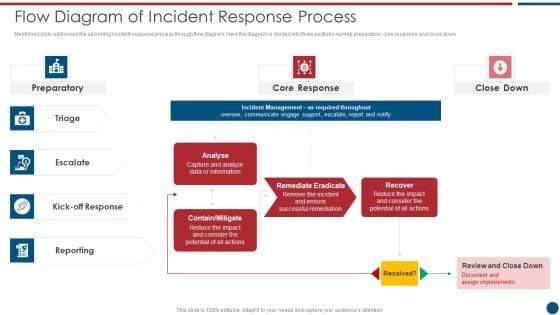
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Privacy IT Purpose Limitation Principle Of Gdpr Law Topics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































