Cyber Attack
Approaches To Implement Advanced Cybersecurity Monitoring Plan Table Of Contents Information PDF
Deliver an awe inspiring pitch with this creative approaches to implement advanced cybersecurity monitoring plan table of contents information pdf bundle. Topics like essential elements, estimated security monitoring, advanced cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template
Here we present the Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template. This One-pager template includes everything you require. You can edit this document and make changes according to your needs it offers complete freedom of customization. Grab this Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template Download now.

Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V
The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts. Get a simple yet stunning designed Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts.

Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V
The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions. There are so many reasons you need a Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Importance Of Firewall Network Security In Business Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name importance of firewall network security in business vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are importance of firewall network security in business vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Transfer On Secured Network Vector Icon Ppt PowerPoint Presentation File Demonstration PDF
Presenting this set of slides with name data transfer on secured network vector icon ppt powerpoint presentation file demonstration pdf. This is a two stage process. The stages in this process are data transfer on secured network vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Network Protection With Firewall Security System Ppt PowerPoint Presentation File Pictures PDF
Presenting network protection with firewall security system ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network protection with firewall security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Of Wireless Network Security System Camera Via Internet Diagrams PDF
Presenting icon of wireless network security system camera via internet diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including icon of wireless network security system camera via internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Wireless Network Security System Camera Connected With Computer System Portrait PDF
Presenting wireless network security system camera connected with computer system portrait pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system camera connected with computer system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF
Help your business to create an attention-grabbing presentation using our Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
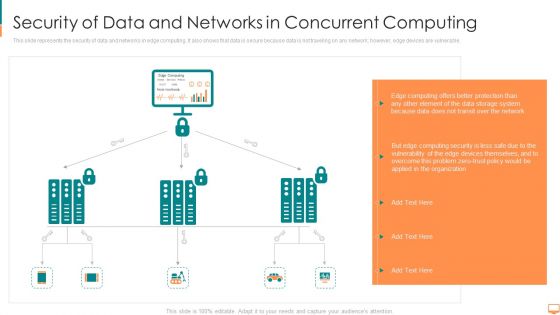
Security Of Data And Networks In Concurrent Computing Ppt File Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. This is a security of data and networks in concurrent computing ppt file themes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computing, transit, storage, system, protection, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
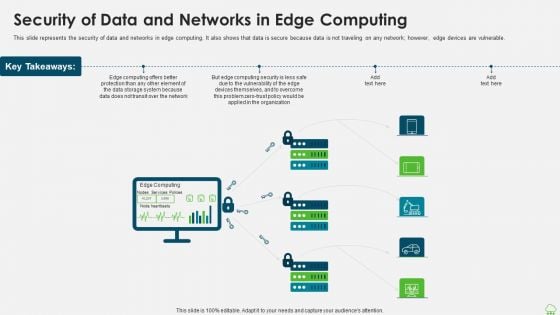
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
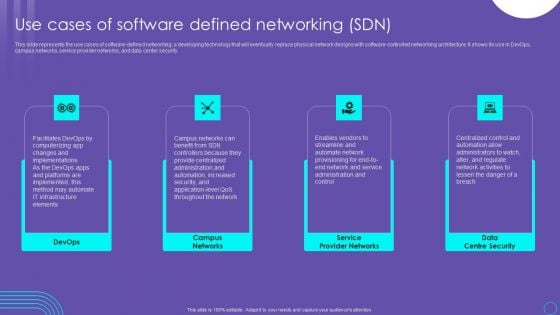
SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
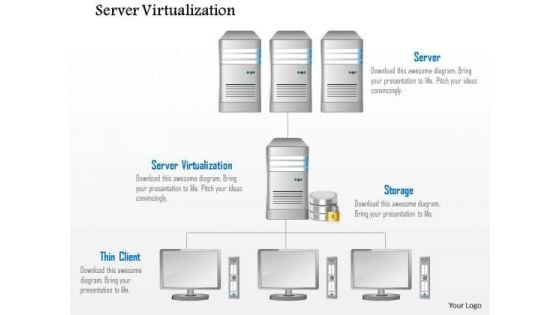
Business Diagram Server Virtulization Thin Client Storage And Database Ppt Slide
This image slide displays network of servers. This image slide has been designed with graphic of server workstation with concepts of server virtualization storage and thin client. This image slide will enhance the quality of your presentations.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents
This one pager covers details regarding the latest industry trends that are existing in the Cybersecurity industry and will prevail in upcoming future. Presenting you a fantastic Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents. This piece is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents A4 One-pager now.

One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents
This one pager shows the detailed summary of a firm in cybersecurity industry such as company name and overview, segment information, revenue split, key financials, key performance indicators, business strategy, major competitors etc. Presenting you an exemplary One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents brilliant piece now.
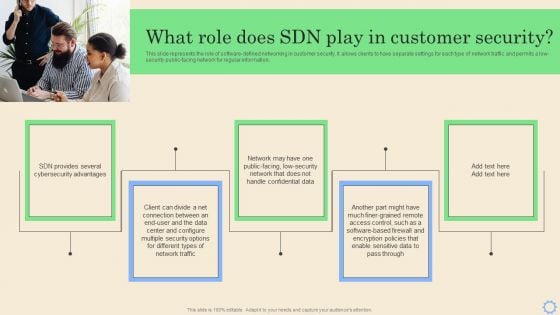
Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
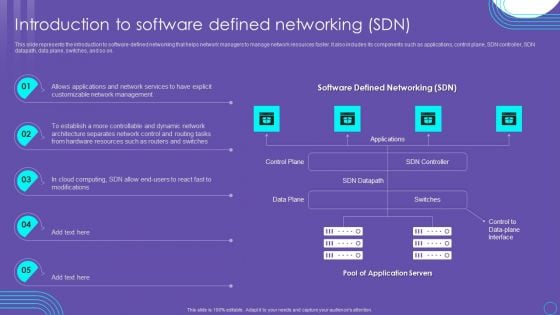
SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
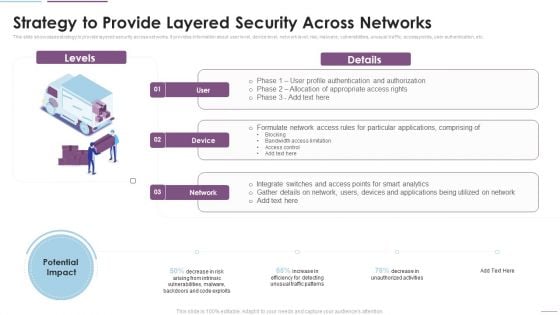
Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF. Use them to share invaluable insights on Formulate Network, Access Rules, Particular Applications, Bandwidth Access Limitation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems.

Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.
Difference Cybersecurity Information Security Ppt PowerPoint Presentation Summary Slide Download Cpb
Presenting this set of slides with name difference cybersecurity information security ppt powerpoint presentation summary slide download cpb. This is an editable Powerpoint five stages graphic that deals with topics like difference cybersecurity information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cybersecurity Incident Response Workflow System Ppt PowerPoint Presentation Gallery Examples Cpb
Presenting this set of slides with name cybersecurity incident response workflow system ppt powerpoint presentation gallery examples cpb. This is an editable Powerpoint four stages graphic that deals with topics like cybersecurity incident response workflow system to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Shield Icon On Computer Monitor For Cybersecurity Ppt PowerPoint Presentation Gallery Show PDF
Persuade your audience using this shield icon on computer monitor for cybersecurity ppt powerpoint presentation gallery show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including shield icon on computer monitor for cybersecurity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
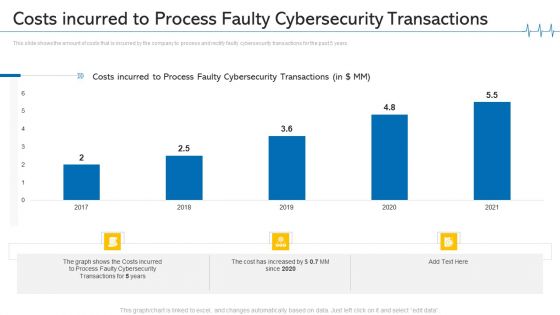
Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Portfolio Graphic Tips PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt portfolio graphic tips pdf bundle. Topics like costs incurred, process faulty, 2017 to 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt File Format PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver and pitch your topic in the best possible manner with this costs incurred to process faulty cybersecurity transactions ppt file format pdf. Use them to share invaluable insights on cost, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda For Effective Cybersecurity Training To Raise Awareness Ppt Summary Templates PDF
This is a agenda for effective cybersecurity training to raise awareness ppt summary templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for effective cybersecurity training to raise awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Phase Procedure Infographics For Cybersecurity In Financial Services Ppt PowerPoint Presentation File Smartart PDF
Persuade your audience using this 5 phase procedure infographics for cybersecurity in financial services ppt powerpoint presentation file smartart pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 phase procedure infographics for cybersecurity in financial services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

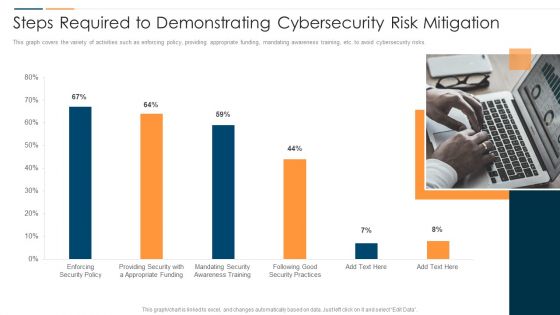
Comprehensive Business Digitization Deck Steps Required To Demonstrating Cybersecurity Risk Mitigation Microsoft PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative comprehensive business digitization deck steps required to demonstrating cybersecurity risk mitigation microsoft pdf bundle. Topics like enforcing policy, providing appropriate funding, mandating awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Budget For Effective Threat Ideas PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities budget for effective threat ideas pdf bundle. Topics like incident management, risk management, client onboarding process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Agenda For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
This is a agenda for modern security observation plan to eradicate cybersecurity risk and data breach information pdf template with various stages. Focus and dispense information on senen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for modern security observation plan to eradicate cybersecurity risk and data breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
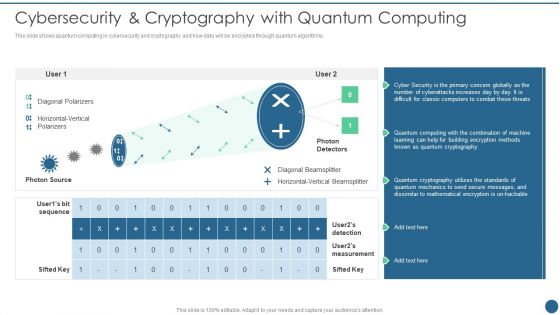
Quantum Key Distribution Cybersecurity And Cryptography With Quantum Computing Designs PDF
This slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Deliver and pitch your topic in the best possible manner with this Quantum Key Distribution Cybersecurity And Cryptography With Quantum Computing Designs PDF Use them to share invaluable insights on Diagonal Polarizers, Diagonal Beamsplitter, Horizontal Vertical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
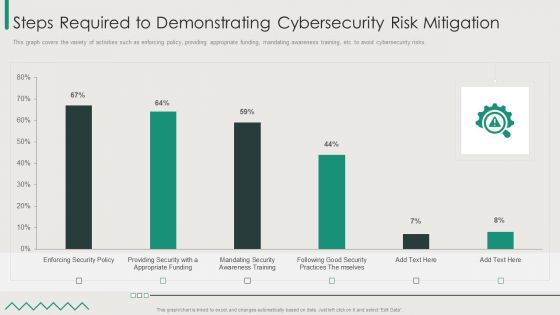
Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents
Presenting you an exemplary One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents brilliant piece now.

Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents
Looking for a predesigned Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents. Here is the perfect piece for you It has everything that a well-structured Annual Report PowerPoint Deck should have. Besides, it is 100 percent editable, which offers you the cushion to make adjustments according to your preferences. Grab this Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents A4 One-pager now.

Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents
Presenting you an exemplary Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents brilliant piece now.
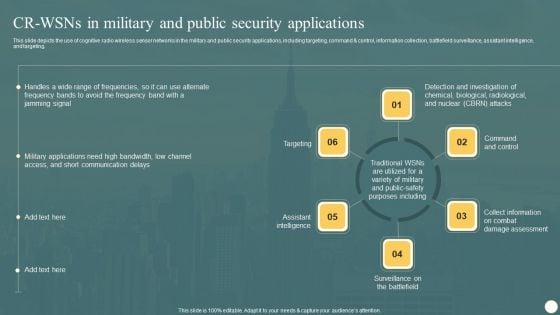
Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Presenting this PowerPoint presentation, titled Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Security Vs Firewall Ppt PowerPoint Presentation Infographic Template Gridlines Cpb
Presenting this set of slides with name network security vs firewall ppt powerpoint presentation infographic template gridlines cpb. This is an editable Powerpoint five stages graphic that deals with topics like network security vs firewall to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Network Security Training Ppt PowerPoint Presentation Slides Portfolio Cpb Pdf
Presenting this set of slides with name computer network security training ppt powerpoint presentation slides portfolio cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like computer network security training to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Protection Icon For Securing Customer Information Ppt PowerPoint Presentation Icon Pictures PDF
Persuade your audience using this network protection icon for securing customer information ppt powerpoint presentation icon pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network protection icon for securing customer information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Secured Public Cloud Network On Premises Vector Icon Ppt PowerPoint Presentation Gallery Slideshow PDF
Persuade your audience using this secured public cloud network on premises vector icon ppt powerpoint presentation gallery slideshow pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including secured public cloud network on premises vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone With Wireless Network Security Alarm Icon Ppt Pictures Graphics Tutorials PDF
Persuade your audience using this smart phone with wireless network security alarm icon ppt pictures graphics tutorials pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone with wireless network security alarm icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virtual Private Network With Internet Security Firewall Protection Ppt PowerPoint Presentation File Master Slide PDF
Persuade your audience using this virtual private network with internet security firewall protection ppt powerpoint presentation file master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network with internet security firewall protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Of Wireless Network Security System With WIFI Lock Elements PDF
Persuade your audience using this icon of wireless network security system with wifi lock elements pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system with wifi lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































