Cyber Attack

Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF
Welcome to our selection of the Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
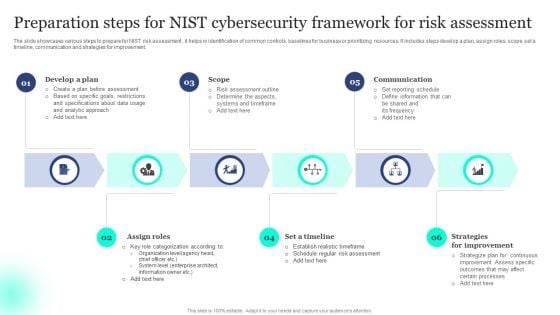
Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF
The slide showcases various steps to prepare for NIST risk assessment , it helps in identification of common controls, baselines for business or prioritizing resources. It includes steps develop a plan, assign roles, scope, set a timeline, communication and strategies for improvement. Presenting Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Scope, Communication, Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides
Arouses curiosity in the audience is the USP of this Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides. The image shown compliments the text provided. The holistic image conveys the message that we are on to something important, the deep world of business communication training. Download it now, and as always customize and edit each of the sixty five slides as per convenience and the data and the experience you are comfortable sharing with your audience.

Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V
The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. This Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects.
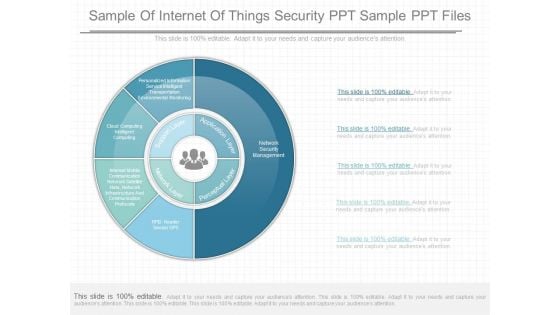
Sample Of Internet Of Things Security Ppt Sample Ppt Files
This is a sample of internet of things security ppt sample ppt files. This is a five stage process. The stages in this process are personalized information service intelligent transportation environmental monitoring, cloud computing intelligent computing, interest mobile communication network satellite nets, network infrastructure and communication protocols, supports layer, network layer, perceptual layer, application layer, network security management, rfid reader sensor gpb.
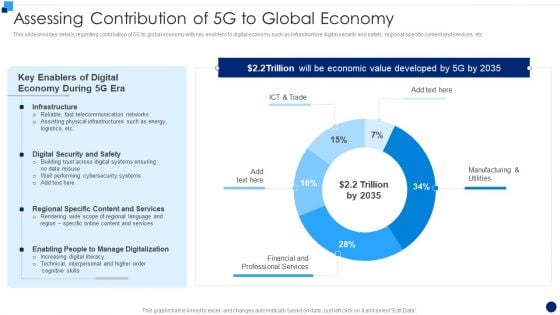
Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF. Use them to share invaluable insights on Telecommunication Networks, Cybersecurity Systems, Content And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Audit Commission Strengthening Cybersecurity Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured audit commission strengthening cybersecurity ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twenty seven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.

Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
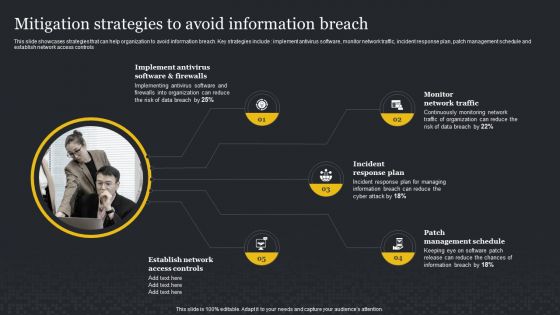
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. This modern and well-arranged Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
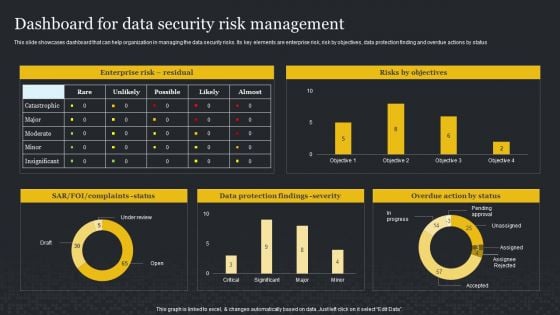
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
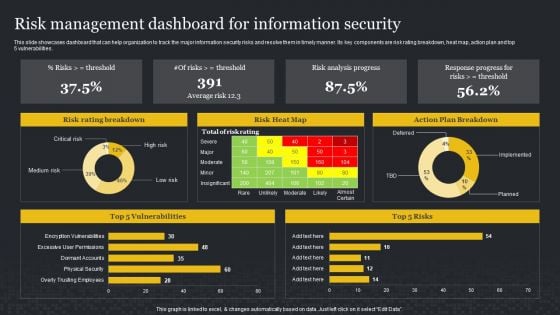
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
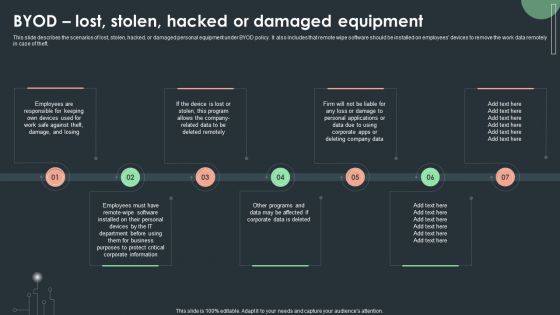
Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
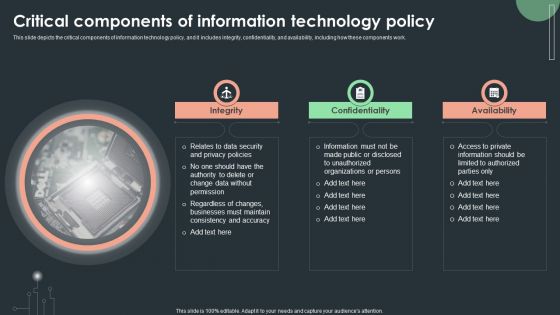
Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF
This slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF
This slide represents the vendor management policy, and it also includes points to be considered when choosing a vendor. This policy is about the vendor with whom organizations share their critical information. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF
This slide represents the company stipend for BYOD policy, including the stats for 2022, such as percent the age of employees using their personal devices, BYOD generated value of each worker per year, and so on. Present like a pro with Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
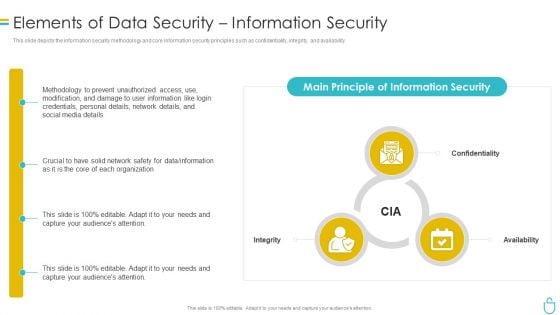
Information Security Elements Of Data Security Information Security Ppt Ideas Design Inspiration PDF
This is a information security elements of data security information security ppt ideas design inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, organization, confidentiality, integrity, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
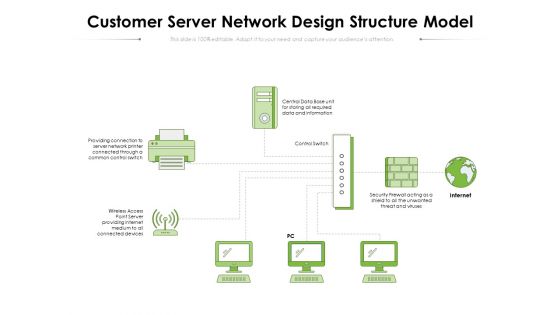
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
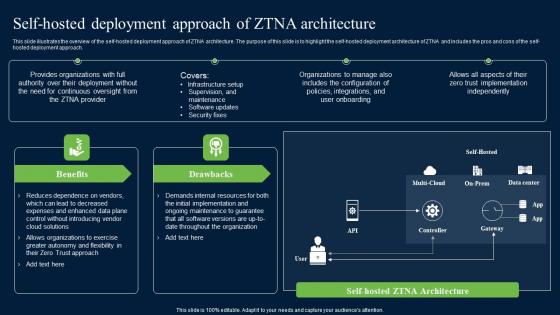
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Do you know about Slidesgeeks Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Boost your pitch with our creative Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.
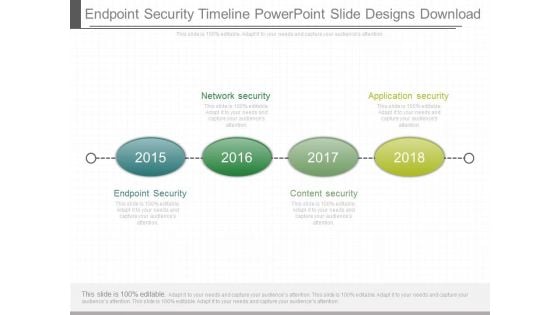
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.
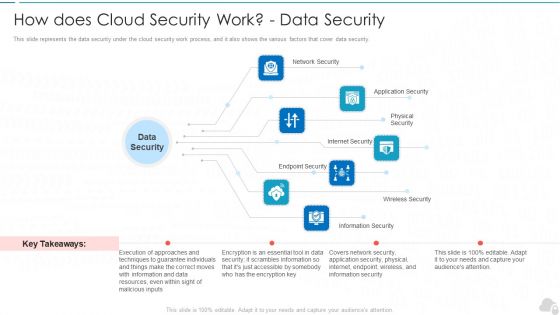
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
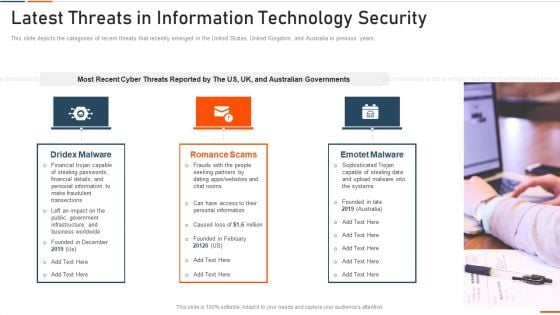
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
PowerPoint Design Teamwork Gears Ppt Designs
PowerPoint Design Teamwork Gears PPT Designs-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go. There is never a dull moment with our PowerPoint Design Teamwork Gears Ppt Designs. They keep it going at fever pitch.
Business Strategy Implementation People Gears Work Together Images
Our Business Strategy Implementation People Gears Work Together Images Powerpoint Templates Abhor Doodling. They Never Let The Interest Flag.

Business Framework Green Supply Chain Management PowerPoint Presentation
This image slide displays chain management. This image slide has been crafted with circle icons with distribution, product recovery, extraction of raw material and manufacturing attributes. Use this image slide in marketing and business presentations to depict strategic management. This image slide will enhance the quality of your presentations.
Business Diagram Icons For Supply Chain Logistics Presentation Template
This diagram slide has been designed with business flow chart. This slide can be used as framework to analyze level of competition within an industry and business strategy development. Mesmerize your audience with this slide.
Three Staged Gear Diagram And Icons Powerpoint Template
This PowerPoint template contains three staged gear diagram with icons. Download this diagram slide to display business activities. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Three Funnel For Sales Process PowerPoint Templates
This multi colored creative slide has been created by our top designers and is one of the most downloaded slides. The three funnels have appropriate markings to describe the input, output and the steps involved in a process and its flow. The diagram can be effectively used to different kind of advertisements or sales strategies and the expected or received results. The PPT template can be included in the presentation to show a filtration process of some kind. It can be an effective slide in demonstrating the work of different departments as well. The slide can be edited easily to show the raw data that is received by each department, the processing done by that unit and the output produced by that unit.

Sales Call Procedure Example Ppt Presentation
This is a sales call procedure example ppt presentation. This is a four stage process. The stages in this process are sales call procedure, logical and progressive sequence, post call analysis, pre call planning. \n \n
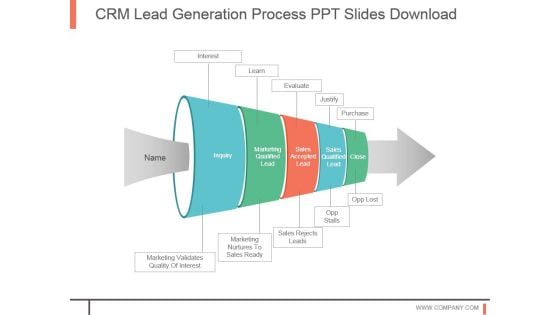
Crm Lead Generation Process Ppt Slides Download
This is a crm lead generation process ppt slides download. This is a five stage process. The stages in this process are inquiry, marketing qualified lead, sales accepted lead, sales qualified lead, close, interest, learn, evaluate, justify, purchase, marketing validates quality of interest, marketing nurtures to sales ready, sales rejects leads, opp stalls, opp lost.

Customer Lifecycle Management Ppt Examples Slides
This is a customer lifecycle management ppt examples slides. This is a six stage process. The stages in this process are attract, engage, retain, loyalty, reward, grow.
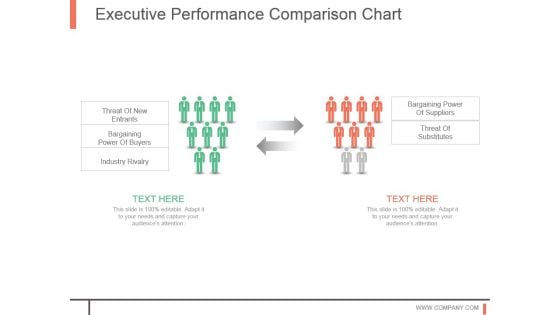
Executive Performance Comparison Chart
This is a executive performance comparison chart. This is a two stage process. The stages in this process are threat of new entrants, bargaining power of buyers, industry rivalry, bargaining power of suppliers, threat of substitutes.
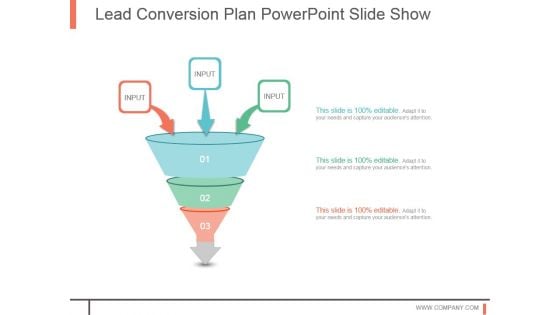
Lead Conversion Plan Powerpoint Slide Show
This is a lead conversion plan powerpoint slide show. This is a three stage process. The stages in this process are business, strategy, marketing, management, funnel, arrow.
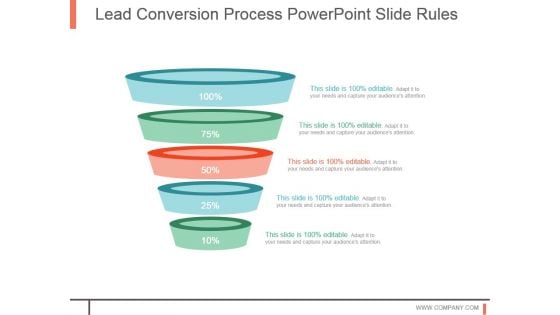
Lead Conversion Process Powerpoint Slide Rules
This is a lead conversion process powerpoint slide rules. This is a five stage process. The stages in this process are business, strategy, marketing, finance, funnel, analysis.

Comparison Chart For Performance Analysis Ppt Design
This is a comparison chart for performance analysis ppt design. This is a two stage process. The stages in this process are compare, scale, measurement, business, marketing.
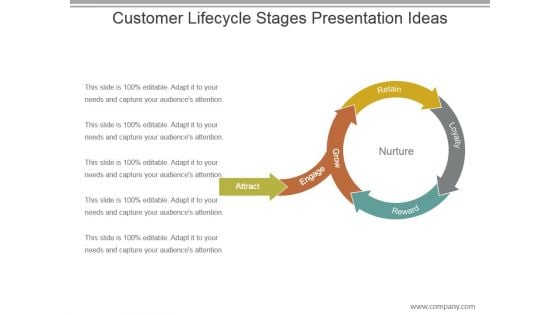
Customer Lifecycle Stages Presentation Ideas
This is a customer lifecycle stages presentation ideas. This is a five stage process. The stages in this process are retain, loyalty, reward, grow, nurture, engage, attract.
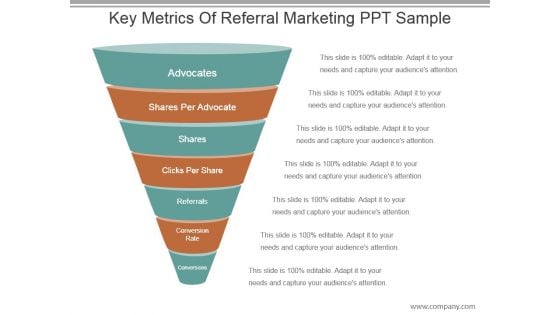
Key Metrics Of Referral Marketing Ppt Sample
This is a key metrics of referral marketing ppt sample. This is a seven stage process. The stages in this process are advocates, shares per advocate, shares, clicks per share, referrals, conversion rate, conversions.

Sales Performance In Us States Ppt Slide Design
This is a sales performance in us states ppt slide design. This is a three stage process. The stages in this process are montana, average sales, higher sales, lowest sales, new mexico, california.
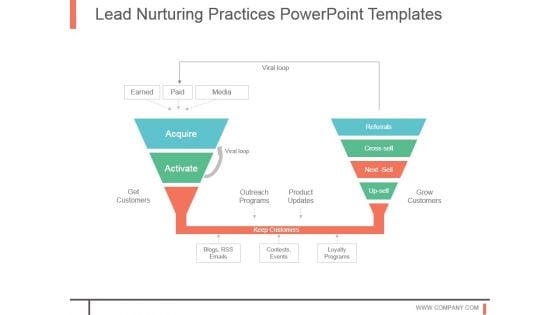
Lead Nurturing Practices Powerpoint Templates
This is a lead nurturing practices powerpoint templates. This is a two stage process. The stages in this process are acquire, activate, get customers, outreach programs, product updates, referrals, cross sell, next sell, up sell, grow customers, blogs rss emails, contests events, loyalty programs, viral loop.
Loyalty Program Metrics Ppt Icon
This is a loyalty program metrics ppt icon. This is a four stage process. The stages in this process are enrollments, reward outstanding, loyalty revenue, gift sales.
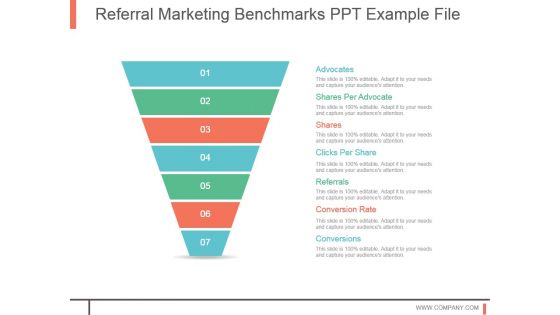
Referrral Marketing Benchmarks Ppt Example File
This is a referrral marketing benchmarks ppt example file. This is a seven stage process. The stages in this process are advocates, shares per advocate, shares, clicks per share, referrals, conversion, rate, conversions.
Lead Generation Funnel Presentation Ideas
This is a lead generation funnel presentation ideas. This is a five stage process. The stages in this process are business, marketing, funnel, filter, step.
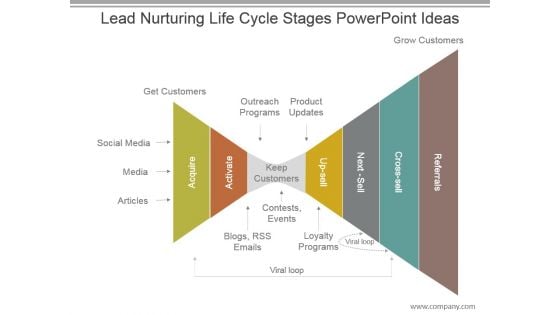
Lead Nurturing Life Cycle Stages Powerpoint Ideas
This is a lead nurturing life cycle stages powerpoint ideas. This is a seven stage process. The stages in this process are get customers, outreach programs, product updates, social media, media, articles, acquire, activate, keep customers, up sell, next sell, cross sell, referrals, grow customers, contests, events, blogs rss emails, loyalty programs, viral loop.
Loyalty Program Performance Metrics Ppt Background
This is a loyalty program performance metrics ppt background. This is a four stage process. The stages in this process are enrollments, reward outstanding, revenue, gift sales.
Sales Force Automation Framework Ppt Templates
This is a sales force automation framework ppt templates. This is a seven stage process. The stages in this process are lead management, opportunity management, contact management, client management, task management, team management, add more.
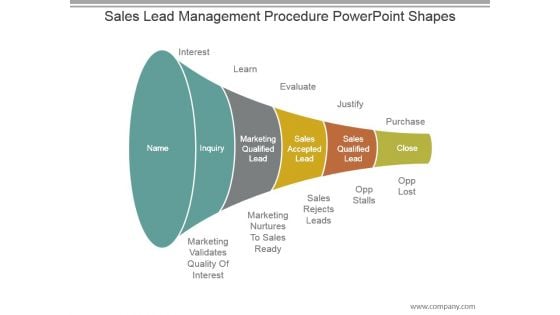
Sales Lead Management Procedure Powerpoint Shapes
This is a sales lead management procedure powerpoint shapes. This is a five stage process. The stages in this process are interest, learn, evaluate, justify, purchase, name, inquiry, marketing qualified lead, sales accepted lead, sales qualified lead, close, marketing validates quality of interest, marketing nurtures to sales ready, sales rejects leads, opp stalls, opp lost.

Sales Management Funnel Powerpoint Topics
This is a sales management funnel powerpoint topics. This is a three stage process. The stages in this process are input.
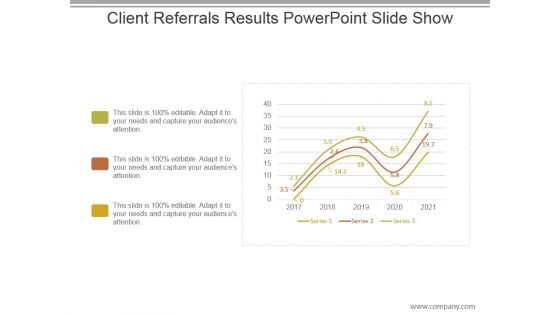
Client Referrals Results Powerpoint Slide Show
This is a client referrals results powerpoint slide show. This is a three stage process. The stages in this process are series, year, success, planning, growth.
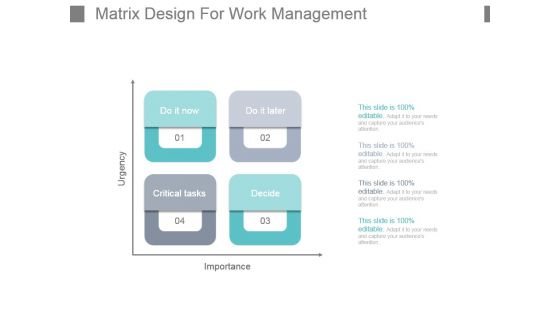
Matrix Design For Work Management Powerpoint Slide Presentation Examples
This is a matrix design for work management powerpoint slide presentation examples. This is a four stage process. The stages in this process are do it now, do it later, critical tasks, decide, importance, urgency.


 Continue with Email
Continue with Email

 Home
Home


































