Cyber

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
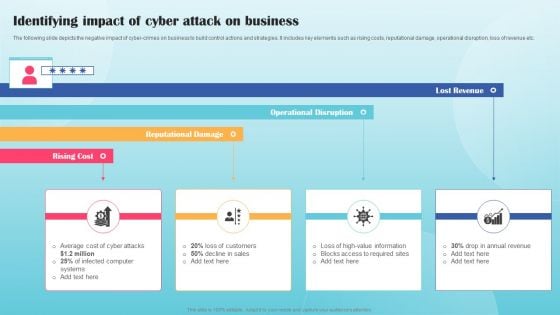
Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Retrieve professionally designed Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF
The following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Take your projects to the next level with our ultimate collection of Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Present like a pro with Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
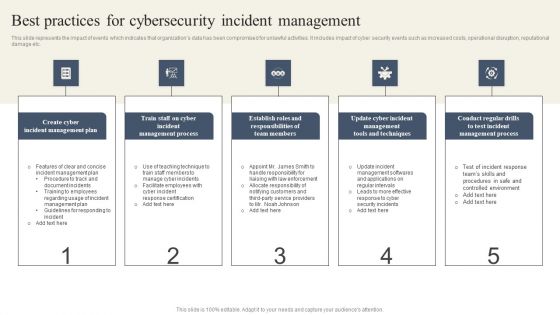
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
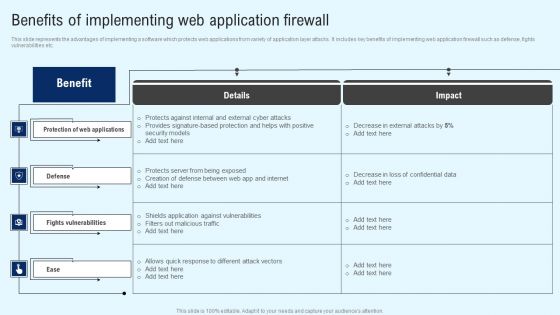
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
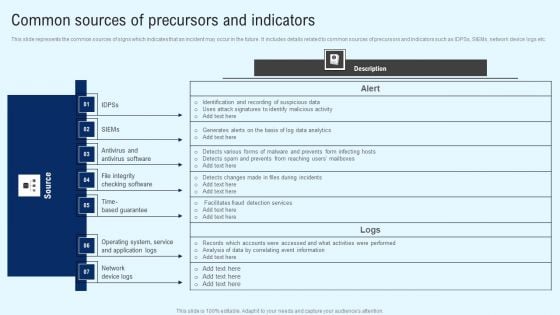
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
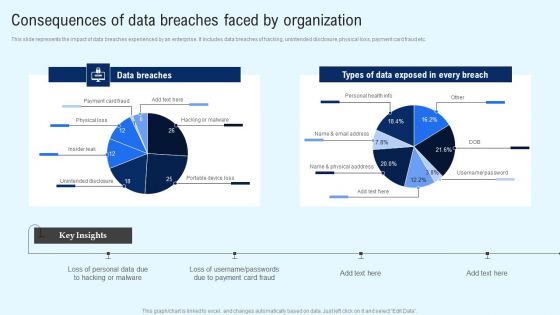
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Boost your pitch with our creative Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
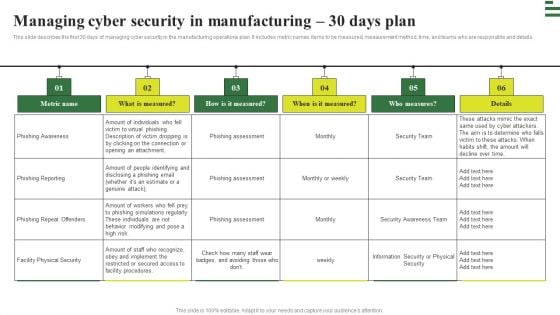
Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This modern and well arranged Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Compliance Framework With Individual Rights Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name cyber security compliance framework with individual rights ppt powerpoint presentation infographics graphics pictures. This is a twelve stage process. The stages in this process are raise awareness, information held, communicating privacy, individual rights, subject access requests, legalities of processing personal data, consent, protecting childrens data, data breaches, data protection by design, data protection officers, international work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
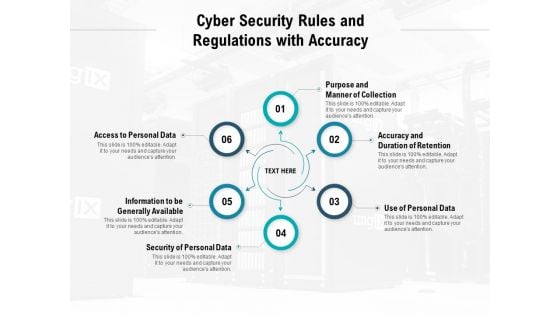
Cyber Security Rules And Regulations With Accuracy Ppt PowerPoint Presentation Slides Outfit
Presenting this set of slides with name cyber security rules and regulations with accuracy ppt powerpoint presentation slides outfit. This is a six stage process. The stages in this process are purpose and manner of collection, accuracy and duration of retention, use of personal data, security of personal data, information to be generally available, access to personal data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Detection Response Ppt PowerPoint Presentation Model Infographic Template Cpb Pdf
Presenting this set of slides with name cyber security detection response ppt powerpoint presentation model infographic template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like customer centric systems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security For Your Organization Business Impact Assessment Ppt Icon Designs PDF
Presenting this set of slides with name cyber security for your organization business impact assessment ppt icon designs pdf. This is a three stage process. The stages in this process are department function, executive dexter hastings, employees, bcp representative, primary business function, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Business Impact Assessment Ppt Pictures Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks business impact assessment ppt pictures summary pdf. This is a three stage process. The stages in this process are strengths, weaknesses, loss impact, primary business function, bcp representative, number employees, executive dexter hastings, department, function. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
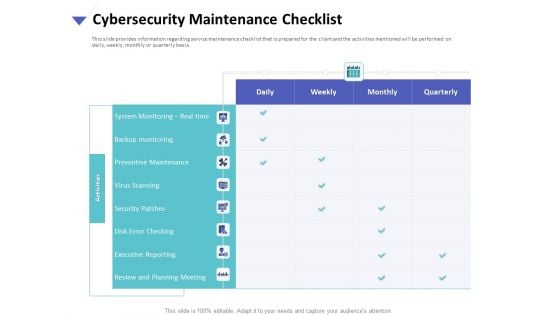
Strategies To Mitigate Cyber Security Risks Cybersecurity Maintenance Checklist Ppt Slides Graphics Tutorials PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity maintenance checklist ppt slides graphics tutorials pdf. The topics discussed in these slides are system monitoring, real time, backup monitoring, preventive maintenance, virus scanning, security patches, disk error checking, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Dashboard Incident Tracking Ppt Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard incident tracking ppt model pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, disable untrusted microsoft office macros, user application hardening, multi factor authentication, daily backup important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
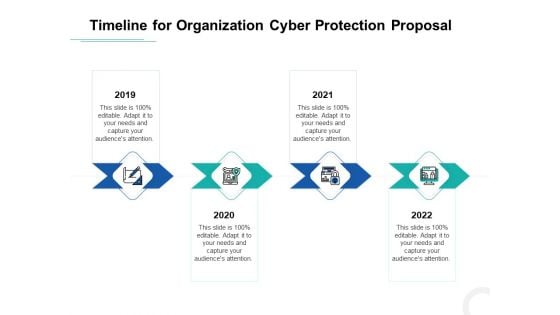
Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
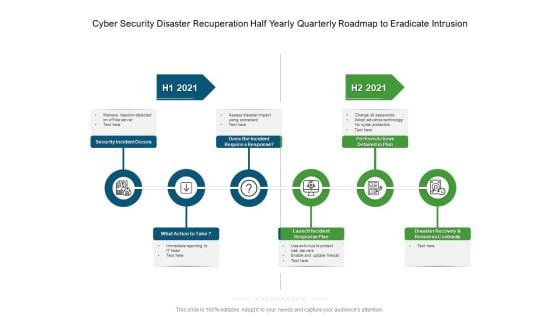
Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
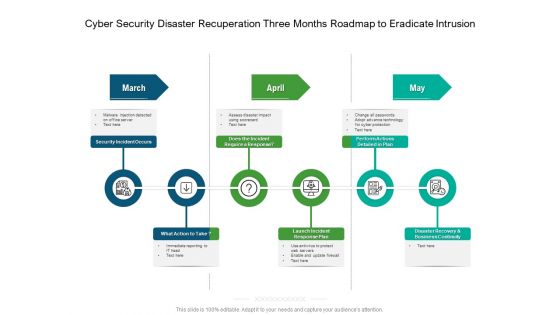
Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Stages To Develop Strong Cyber Security Analysis Process Ppt PowerPoint Presentation Outline Example File PDF
Persuade your audience using this stages to develop strong cyber security analysis process ppt powerpoint presentation outline example file pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including formulate remediation steps and prioritize risks, analysing collected, recipient on the phone, teleconference. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
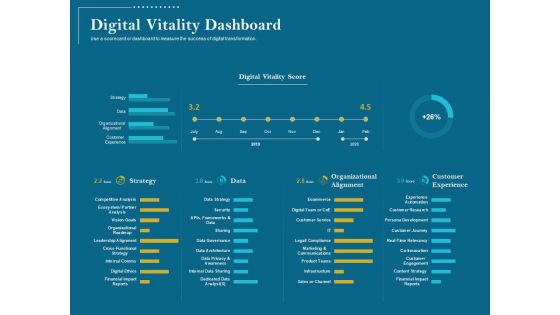
Utilizing Cyber Technology For Change Process Digital Vitality Dashboard Guidelines PDF
Use a scorecard or dashboard to measure the success of digital transformation. Deliver an awe-inspiring pitch with this creative utilizing cyber technology for change process digital vitality dashboard guidelines pdf. bundle. Topics like organizational alignment, ecommerce, digital team or coe, customer service, marketing and communications, product teams, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
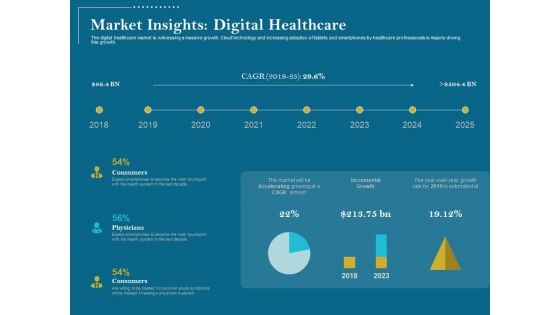
Utilizing Cyber Technology For Change Process Market Insights Digital Healthcare Brochure PDF
The digital healthcare market is witnessing a massive growth. Cloud technology and increasing adoption of tablets and smartphones by healthcare professionals is majorly driving this growth.Deliver an awe-inspiring pitch with this creative utilizing cyber technology for change process market insights digital healthcare brochure pdf bundle. Topics like consumers, physicians, consumers, incremental, growth, 2018 to 2025 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Utilizing Cyber Technology For Change Process Table Of Contents Introduction PDF
Presenting utilizing cyber technology for change process table of contents introduction pdf. to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital review, consumer insights, digital strategy, market insights digital healthcare, challenges in digital transformation, digital transformation growth drivers, telehealth services, digital plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
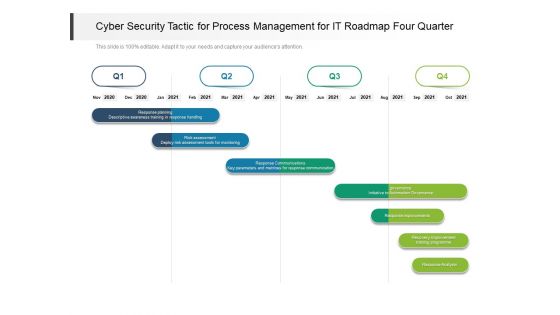
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
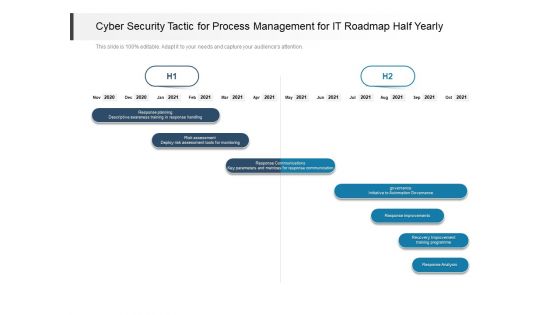
Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Key Safety Audits To Stop Cyber Attacks Ppt PowerPoint Presentation File Example Topics PDF
Persuade your audience using this key safety audits to stop cyber attacks ppt powerpoint presentation file example topics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including inventory, secure configurations, continuous vulnerability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
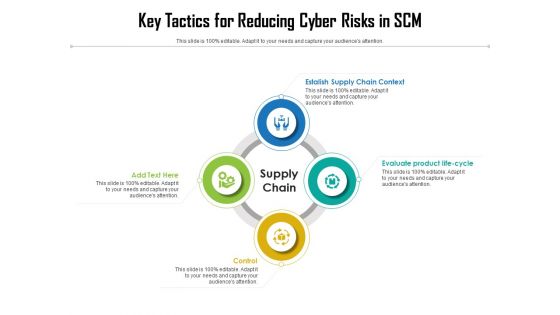
Key Tactics For Reducing Cyber Risks In SCRM Ppt PowerPoint Presentation Ideas Visual Aids PDF
Persuade your audience using this key tactics for reducing cyber risks in scm ppt powerpoint presentation ideas visual aids pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including establish supply chain context, evaluate product life cycle, control, supply chain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
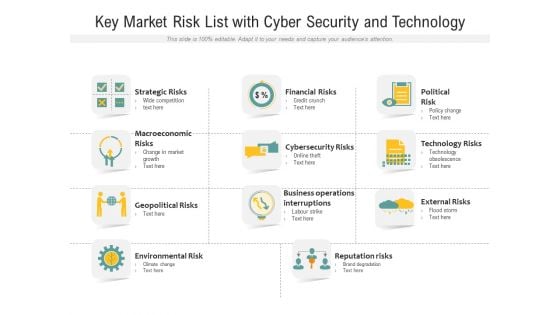
Key Market Risk List With Cyber Security And Technology Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled key market risk list with cyber security and technology ppt powerpoint presentation file show pdf. The topics addressed in these templates are strategic risks, macroeconomic, geopolitical risks, environmental risk, financial risks, cybersecurity risks, political risk, technology risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
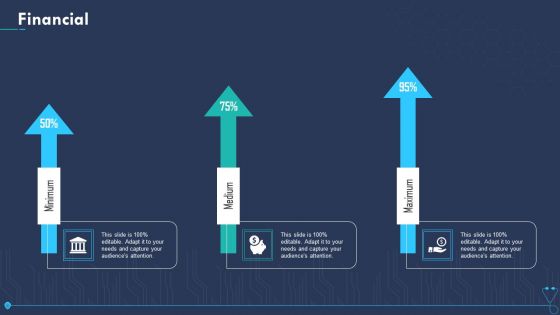
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Financial Elements PDF
Presenting case competition overpower the obstacle of cyber security in medicare financial elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Post It Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare post it sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
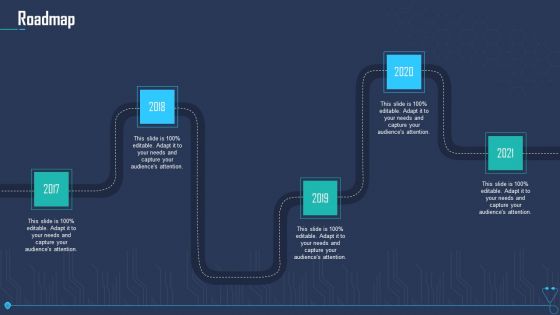
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Roadmap Inspiration PDF
Presenting case competition overpower the obstacle of cyber security in medicare roadmap inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap, 2017 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
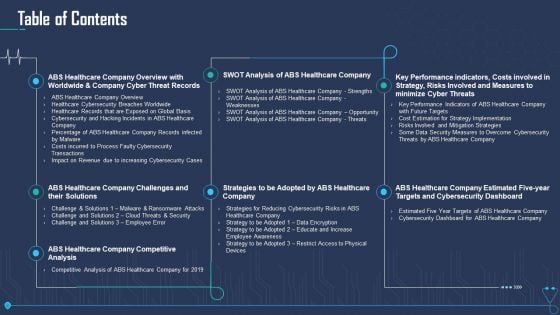
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Table Of Contents Guidelines PDF
Deliver an awe inspiring pitch with this creative case competition overpower the obstacle of cyber security in medicare table of contents guidelines pdf bundle. Topics like swot analysis of abs healthcare company, abs healthcare company competitive analysis, abs healthcare company challenges and their solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
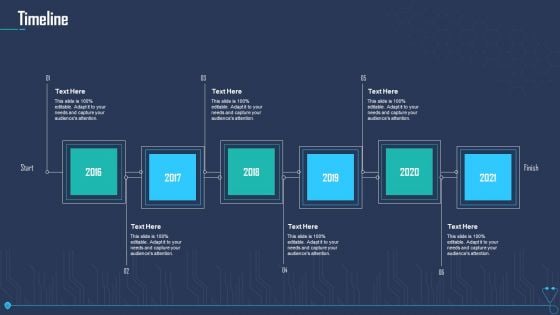
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Timeline Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare timeline sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 2 Banks Cyber Security Infrastructure Ppt Pictures Example PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Deliver an awe inspiring pitch with this creative case study 2 banks cyber security infrastructure ppt pictures example pdf bundle. Topics like implemented, integrated, approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Addressing The Incidents Logging Process Diagrams PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative cyber security risk management plan addressing the incidents logging process diagrams pdf bundle. Topics like process id, procedure, description, responsible person can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
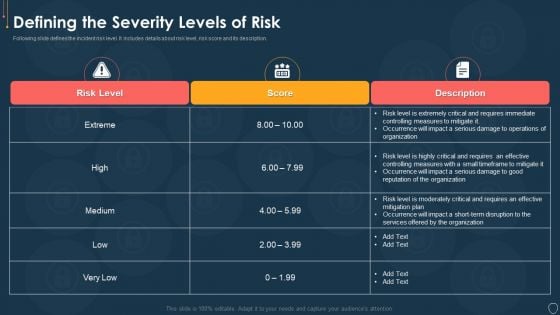
Cyber Security Risk Management Plan Defining The Severity Levels Of Risk Template PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan defining the severity levels of risk template pdf. Use them to share invaluable insights on risk level, risk score, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
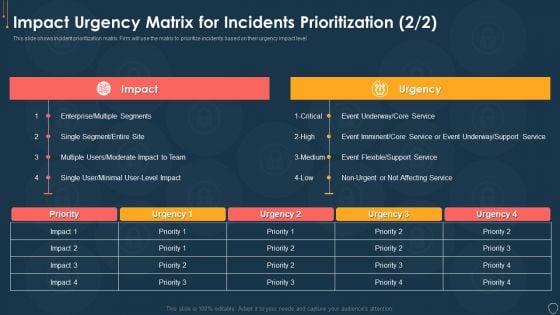
Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Event Topics PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative cyber security risk management plan impact urgency matrix for incidents prioritization event topics pdf bundle. Topics like impact urgency matrix for incidents prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Location Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact urgency matrix for incidents prioritization location information pdf. Use them to share invaluable insights on business, location, inconvenient, moderate, preform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
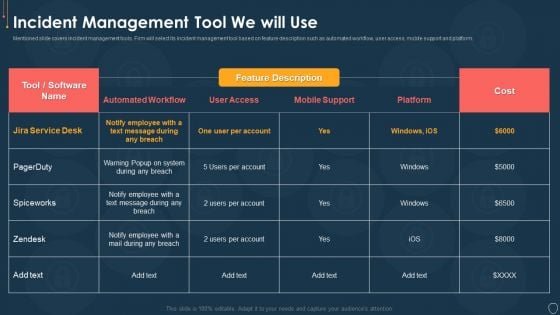
Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
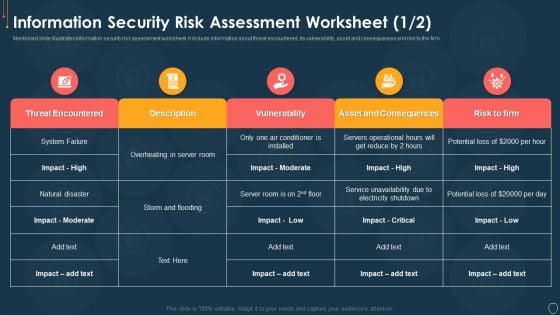
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Consequences Diagrams PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk assessment worksheet consequences diagrams pdf bundle. Topics like threat encountered, its vulnerability, asset and consequences, risk to the firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
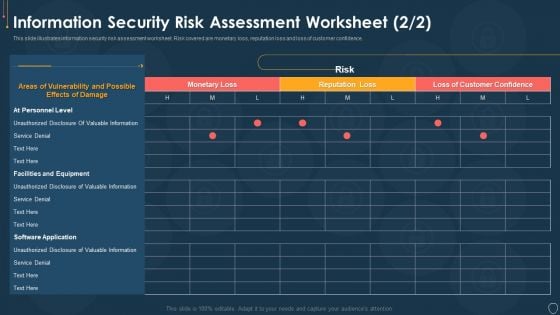
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
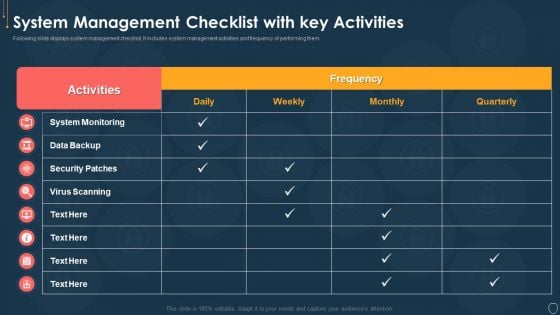
Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Using System Categorization Sheet For Asset Identification Template PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Deliver an awe inspiring pitch with this creative cyber security risk management plan using system categorization sheet for asset identification template pdf bundle. Topics like location, accessibility, organization, access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan 30 60 90 Days Plan Infographics PDF
This is a cyber security risk management plan 30 60 90 days plan infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
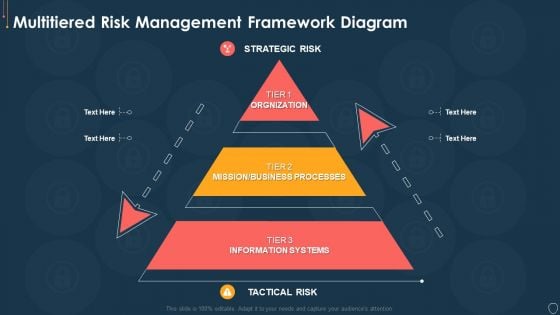
Cyber Security Risk Management Plan Multitiered Risk Management Framework Diagram Inspiration PDF
This is a cyber security risk management plan multitiered risk management framework diagram inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like orgnization, mission or business processes, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Risk Reporting And Likelihood Elements PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative cyber security risk management plan risk reporting and likelihood elements pdf bundle. Topics like risk encountered, frequency, reported by status, attack scenario, affected asset, likelihood can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Risk Management Plan Current Security Infrastructure Performance Analysis Icons PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative cyber security risk management plan current security infrastructure performance analysis icons pdf bundle. Topics like technology, target, plan, vulnerability intelligence, security infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































