Cyber
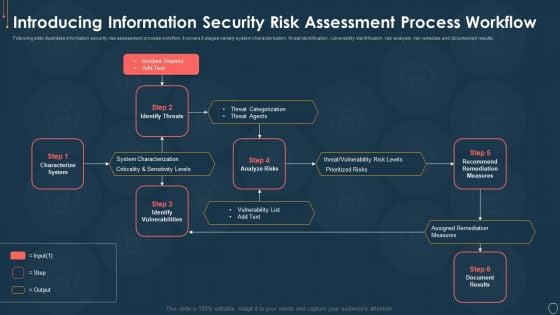
Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
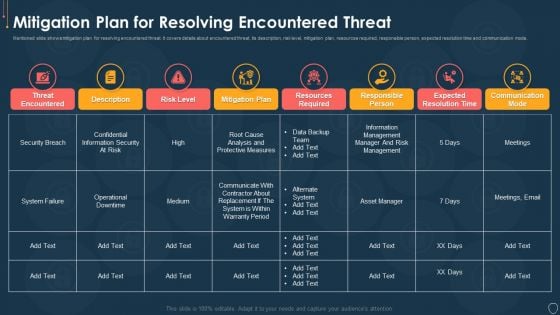
Cyber Security Risk Management Plan Mitigation Plan For Resolving Encountered Threat Pictures PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative cyber security risk management plan mitigation plan for resolving encountered threat pictures pdf bundle. Topics like threat encountered, mitigation plan, responsible person, communication mode, risk level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Present Security Management Capabilities Of The Firm Template PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan present security management capabilities of the firm template pdf. Use them to share invaluable insights on actual standard rating, required standard rating, key enablers, description, core functions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
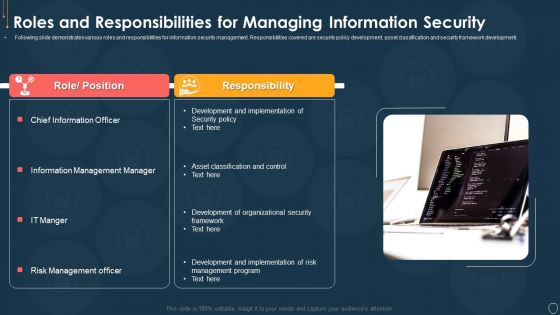
Cyber Security Risk Management Plan Roles And Responsibilities For Managing Information Security Mockup PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. Presenting cyber security risk management plan roles and responsibilities for managing information security mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like role or position, responsibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
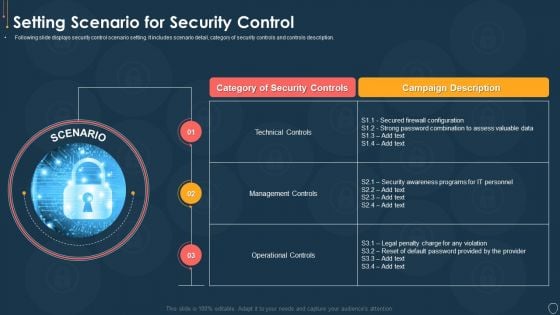
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
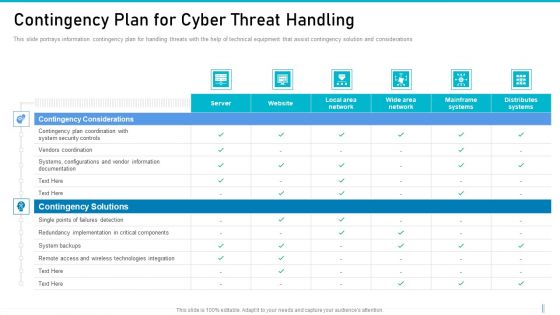
Risk Management For Organization Essential Assets Contingency Plan For Cyber Threat Handling Download PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets contingency plan for cyber threat handling download pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management For Organization Essential Assets Addressing Cyber Threats In Various Industries Structure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a risk management for organization essential assets addressing cyber threats in various industries structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

E Business And Cyber Risk Management Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This e business and cyber risk management ppt powerpoint presentation complete with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty two slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
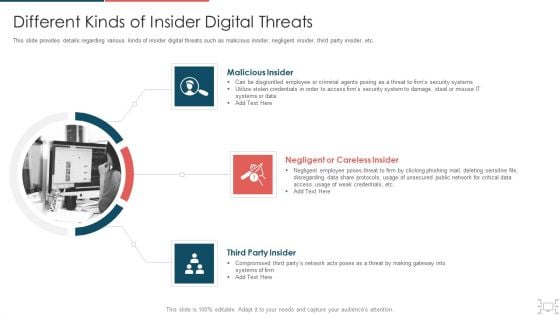
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
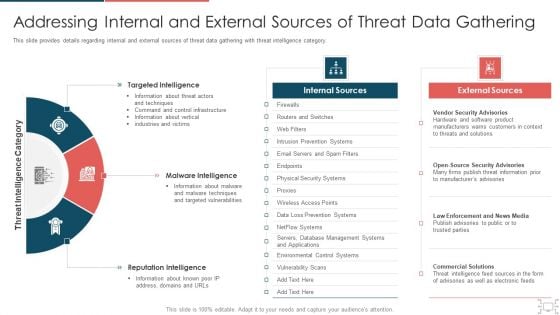
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
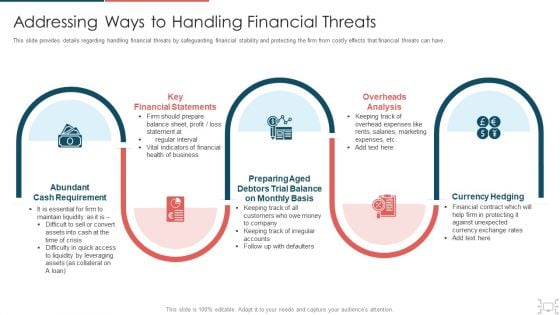
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
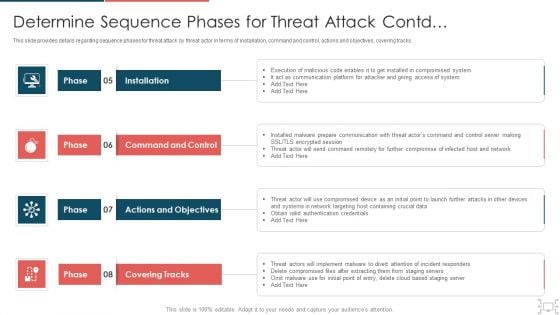
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
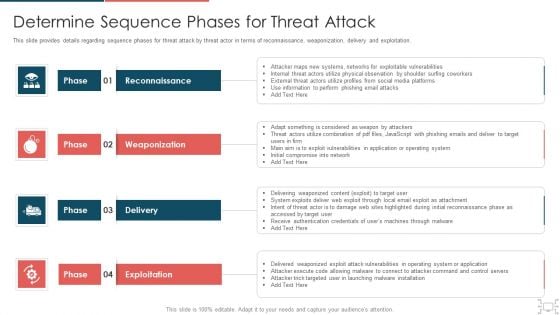
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
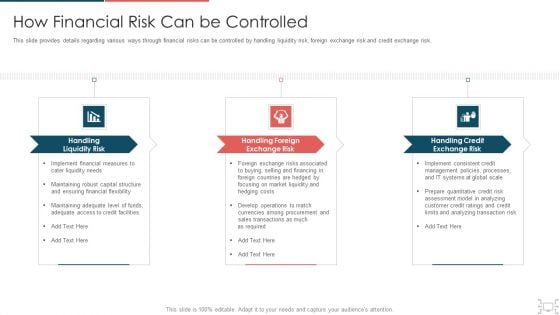
cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
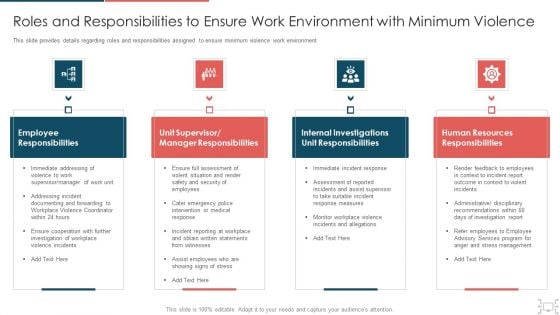
cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
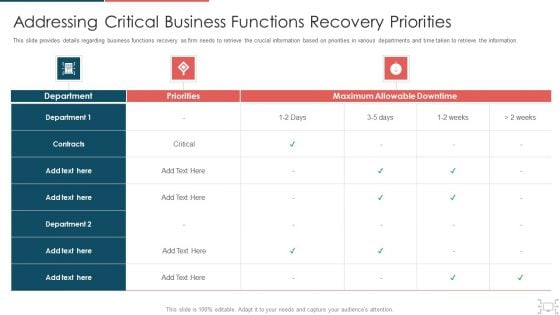
Cyber Security Administration In Organization Addressing Critical Business Functions Recovery Download PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing critical business functions recovery download pdf. Use them to share invaluable insights on addressing critical business functions recovery priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
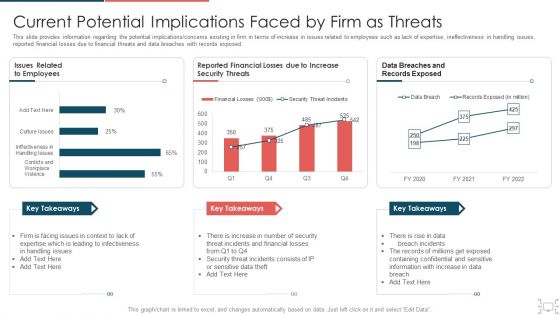
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
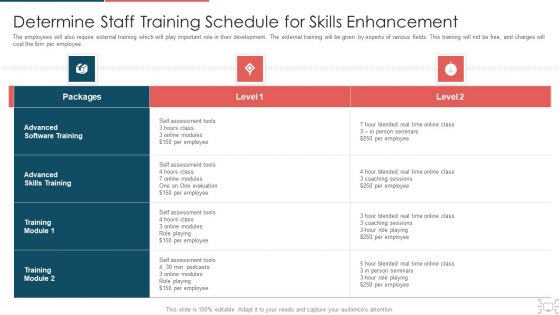
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
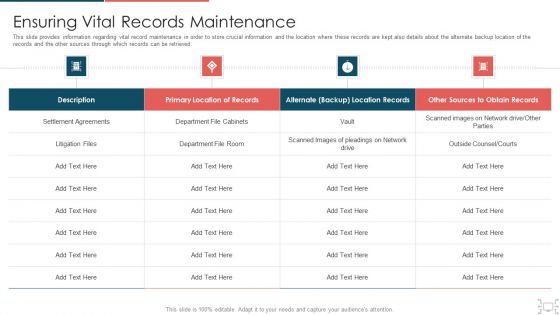
Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
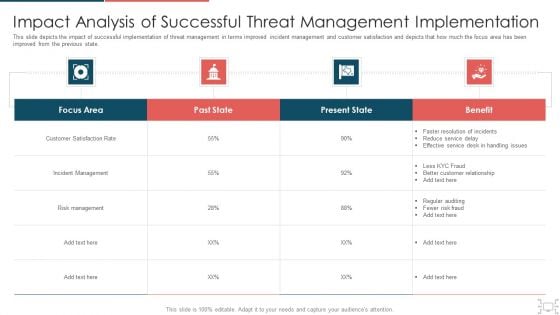
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
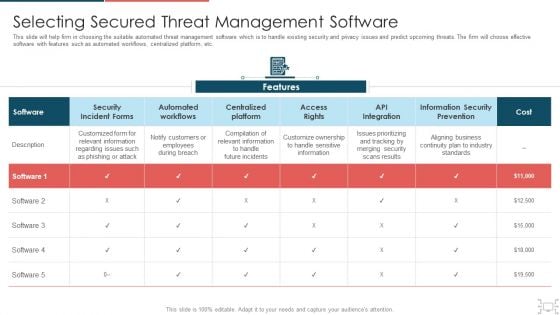
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
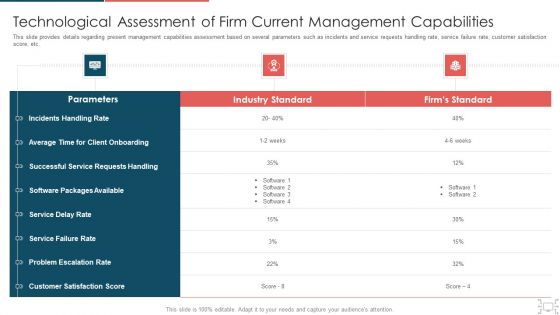
Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
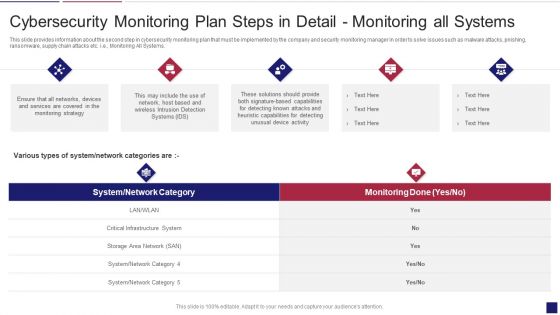
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
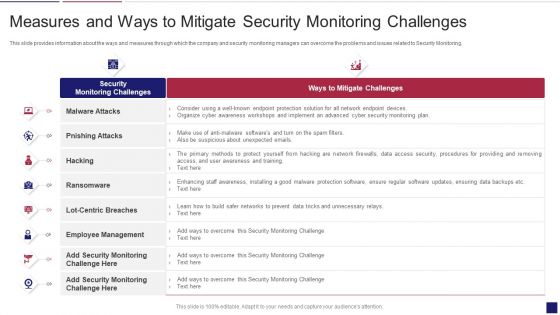
Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
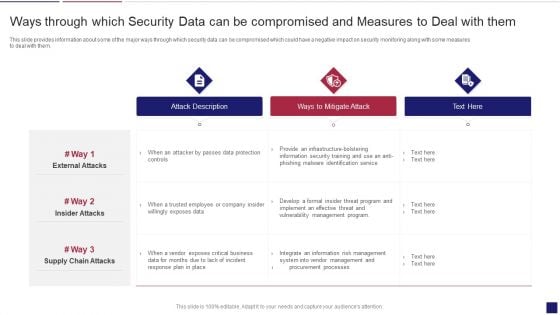
Continuous Development Evaluation Plan Eliminate Cyber Attacks Ways Through Which Security Clipart PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
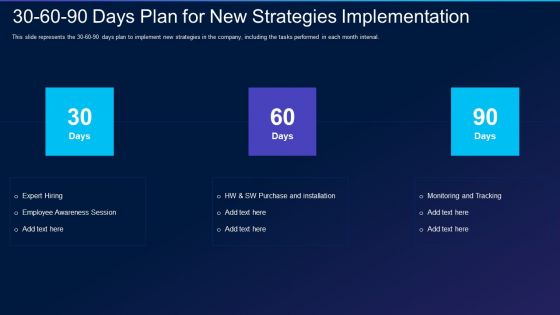
Cyber Exploitation IT 30 60 90 Days Plan For New Strategies Implementation Pictures PDF
This slide represents the 30-60-90 days plan to implement new strategies in the company, including the tasks performed in each month interval. This is a cyber exploitation it 30 60 90 days plan for new strategies implementation pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan for new strategies implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Altered Business Practices Due To Hacking Ideas PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions. Presenting cyber exploitation it altered business practices due to hacking ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like altered business practices due to hacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
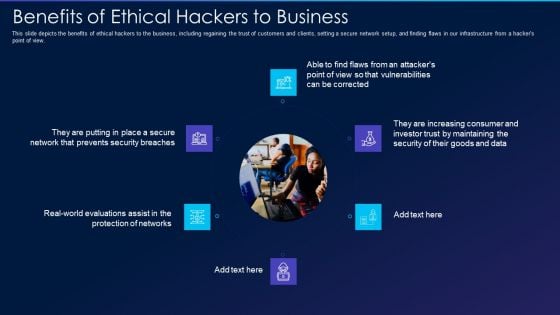
Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
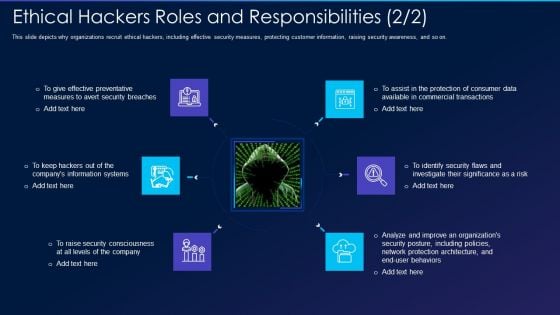
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Hacking Of Our Social Media Accounts Template PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2022 and the amount of money by running scam ads. This is a cyber exploitation it hacking of our social media accounts template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hacking of our social media accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Loss Of Customers And Client Information Guidelines PDF
This slide represents the loss of information that happened in the company and the causes of the data loss, including theft, hardware destruction, computer viruses, and human error. Deliver and pitch your topic in the best possible manner with this cyber exploitation it loss of customers and client information guidelines pdf. Use them to share invaluable insights on computer viruses, software corruption, hardware failure, hardware destruction, human error and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
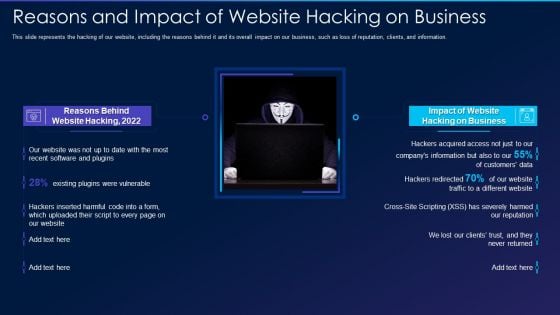
Cyber Exploitation IT Reasons And Impact Of Website Hacking On Business Elements PDF
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information. Presenting cyber exploitation it reasons and impact of website hacking on business elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reasons behind website hacking, 2022, impact of website hacking on business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
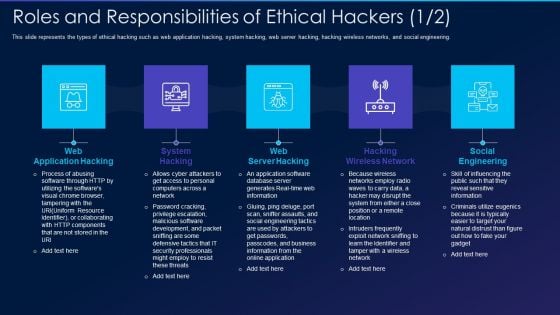
Cyber Exploitation IT Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Presenting cyber exploitation it roles and responsibilities of ethical hackers pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like web application hacking, system hacking, web server hacking, hacking wireless network, social engineering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Network Simulation Platform Capital Funding Pitch Deck An Introduction To Our Product Solution Icons PDF
The following slide displays the introduction about the product as it provides highlight of the VR by depicting the product segments such as HMD GTD and PDW along with key USP of the organization Deliver an awe inspiring pitch with this creative cyber network simulation platform capital funding pitch deck an introduction to our product solution icons pdf bundle. Topics like product captures, wireless experience, experience no motion sickness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
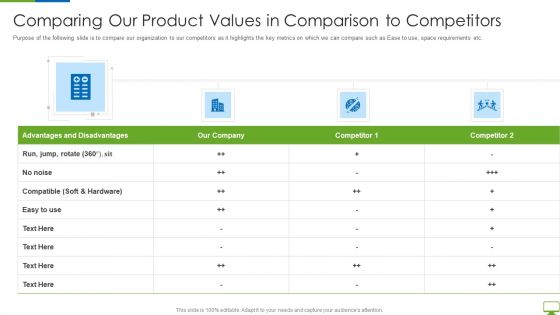
Cyber Network Simulation Platform Capital Funding Pitch Deck Comparing Our Product Values Portrait PDF
Purpose of the following slide is to compare our organization to our competitors as it highlights the key metrics on which we can compare such as Ease to use, space requirements etc. Deliver and pitch your topic in the best possible manner with this cyber network simulation platform capital funding pitch deck comparing our product values portrait pdf Use them to share invaluable insights on comparing our product values in comparison to competitors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
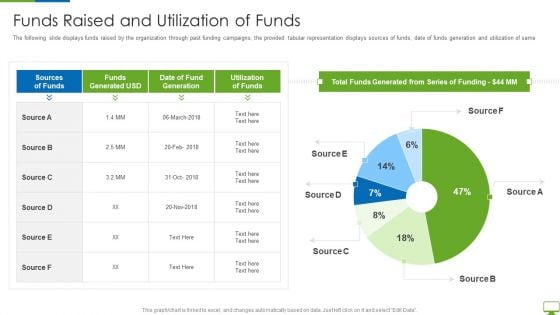
Cyber Network Simulation Platform Capital Funding Pitch Deck Funds Raised And Utilization Of Funds Background PDF
The following slide displays funds raised by the organization through past funding campaigns, the provided tabular representation displays sources of funds, date of funds generation and utilization of same Deliver an awe inspiring pitch with this creative cyber network simulation platform capital funding pitch deck funds raised and utilization of funds background pdf bundle. Topics like date of fund generation, utilization of funds, total funds generated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
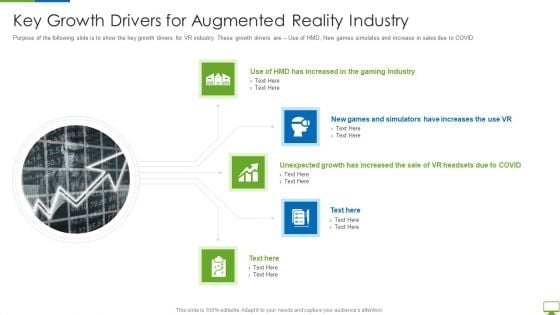
Cyber Network Simulation Platform Capital Funding Pitch Deck Key Growth Drivers Background PDF
Purpose of the following slide is to show the key growth drivers for VR industry. These growth drivers are Use of HMD, New games simulates and increase in sales due to COVID This is a cyber network simulation platform capital funding pitch deck key growth drivers background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like gaming industry, unexpected growth, simulators have increases You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
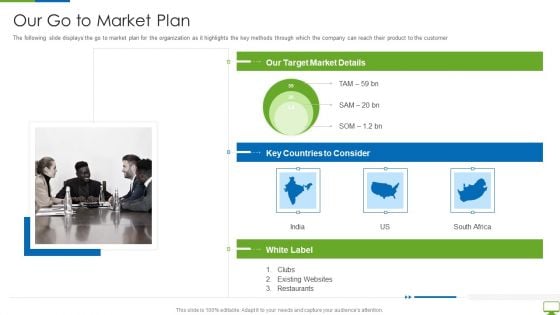
Cyber Network Simulation Platform Capital Funding Pitch Deck Our Go To Market Plan Slides PDF
The following slide displays the go to market plan for the organization as it highlights the key methods through which the company can reach their product to the customer Presenting cyber network simulation platform capital funding pitch deck our go to market plan slides pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like our go to market plan In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
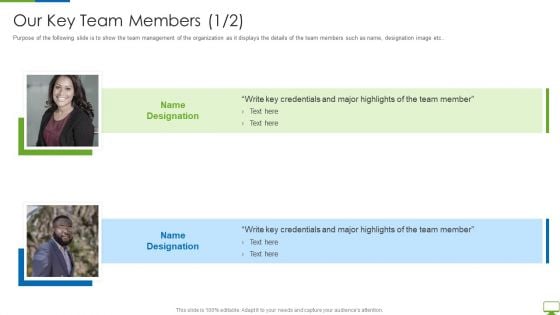
Cyber Network Simulation Platform Capital Funding Pitch Deck Our Key Team Members Background PDF
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc.This is a cyber network simulation platform capital funding pitch deck our key team members background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our key team members You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
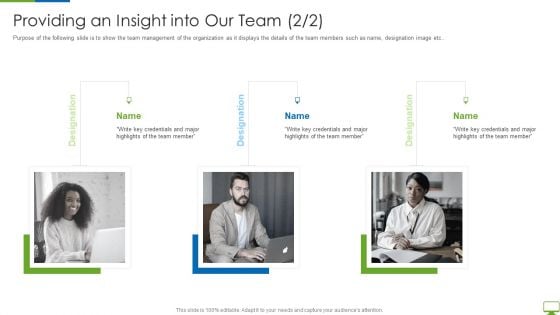
Cyber Network Simulation Platform Capital Funding Pitch Deck Providing An Insight Topics PDF
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc.Presenting cyber network simulation platform capital funding pitch deck providing an insight topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like providing an insight into our team In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
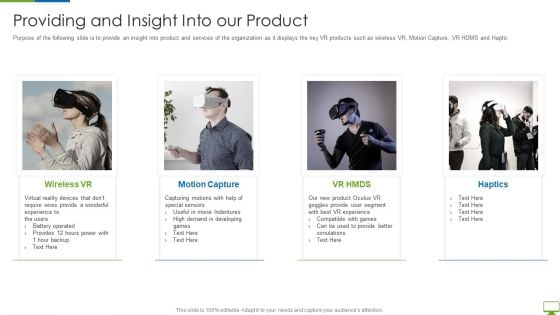
Cyber Network Simulation Platform Capital Funding Pitch Deck Providing And Insight Into Our Product Information PDF
Purpose of the following slide is to provide an insight into product and services of the organization as it displays the key VR products such as wireless VR, Motion Capture, VR HDMS and Haptic Deliver an awe inspiring pitch with this creative cyber network simulation platform capital funding pitch deck providing and insight into our product information pdf bundle. Topics like providing and insight into our product can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
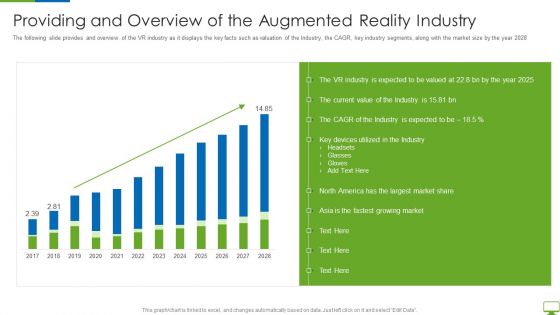
Cyber Network Simulation Platform Capital Funding Pitch Deck Providing And Overview Of The Augmented Designs PDF
The following slide provides and overview of the VR industry as it displays the key facts such as valuation of the Industry, the CAGR, key industry segments, along with the market size by the year 2028 Deliver and pitch your topic in the best possible manner with this cyber network simulation platform capital funding pitch deck providing and overview of the augmented designs pdf Use them to share invaluable insights on key devices utilized, fastest growing market, industry is expected and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
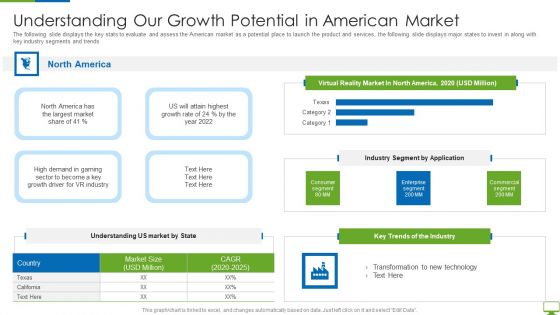
Cyber Network Simulation Platform Capital Funding Pitch Deck Understanding Our Growth Summary PDF
The following slide displays the key stats to evaluate and assess the American market as a potential place to launch the product and services, the following slide displays major states to invest in along with key industry segments and trends Deliver and pitch your topic in the best possible manner with this cyber network simulation platform capital funding pitch deck understanding our growth summary pdf Use them to share invaluable insights on high demand in gaming, transformation technology, key trends of the industry and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































