Data Risk
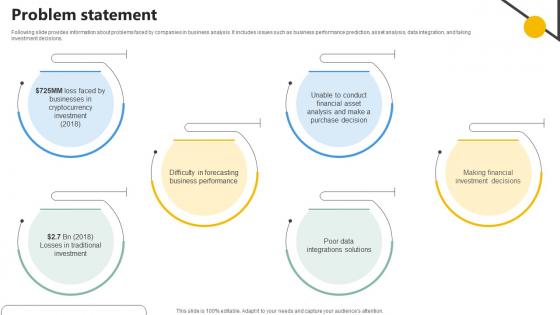
Problem Statement Analytics Company Investor Funding Elevator
Following slide provides information about problems faced by companies in business analysis. It includes issues such as business performance prediction, asset analysis, data integration, and taking investment decisions.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Problem Statement Analytics Company Investor Funding Elevator and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Following slide provides information about problems faced by companies in business analysis. It includes issues such as business performance prediction, asset analysis, data integration, and taking investment decisions.

Problem Statement Investor Funding Elevator Pitch Deck For Business Operations Management Platform
Following slide provides information about problems faced by businesses in record management and work allocation. It includes problems such as data visualization, applications integration, repetitive tasks, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Investor Funding Elevator Pitch Deck For Business Operations Management Platform was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Investor Funding Elevator Pitch Deck For Business Operations Management Platform Following slide provides information about problems faced by businesses in record management and work allocation. It includes problems such as data visualization, applications integration, repetitive tasks, etc.
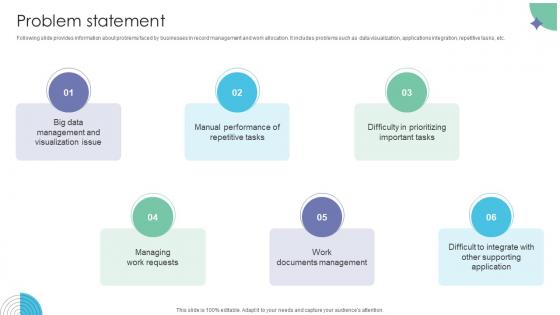
Problem Statement Workflow Management Investor Funding Elevator Pitch Deck
Following slide provides information about problems faced by businesses in record management and work allocation. It includes problems such as data visualization, applications integration, repetitive tasks, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Workflow Management Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Workflow Management Investor Funding Elevator Pitch Deck. Following slide provides information about problems faced by businesses in record management and work allocation. It includes problems such as data visualization, applications integration, repetitive tasks, etc.
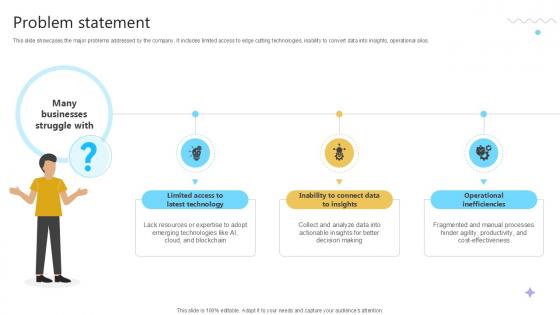
Problem Statement Cloud Computing Services Business Model PPT Presentation BMC SS V
This slide showcases the major problems addressed by the company. It includes limited access to edge cutting technologies, inability to convert data into insights, operational silos. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Cloud Computing Services Business Model PPT Presentation can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Cloud Computing Services Business Model PPT Presentation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the major problems addressed by the company. It includes limited access to edge cutting technologies, inability to convert data into insights, operational silos.
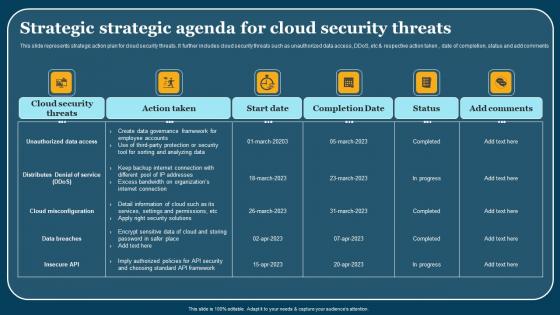
Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf
This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments. Showcasing this set of slides titled Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf. The topics addressed in these templates are Cloud Security Threats, Action Taken, Start Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments.
Survey Results Depicting Problems Building Utility Billing And Invoicing Management System Icons Pdf
Following slide shows survey results to understand challenges in company billing system. It include pointers such as management issue, data manipulation, complexity, reporting concern etc. This Survey Results Depicting Problems Building Utility Billing And Invoicing Management System Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. Following slide shows survey results to understand challenges in company billing system. It include pointers such as management issue, data manipulation, complexity, reporting concern etc.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
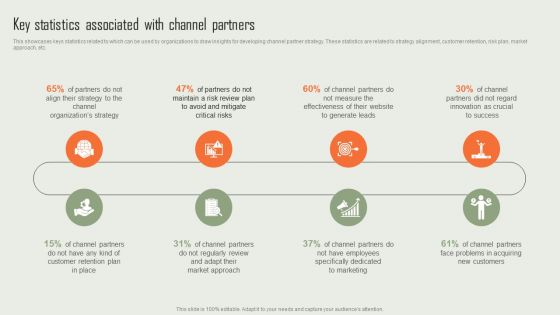
Product Marketing And Sales Expansion Through Channel Key Statistics Associated With Channel Partners Download PDF
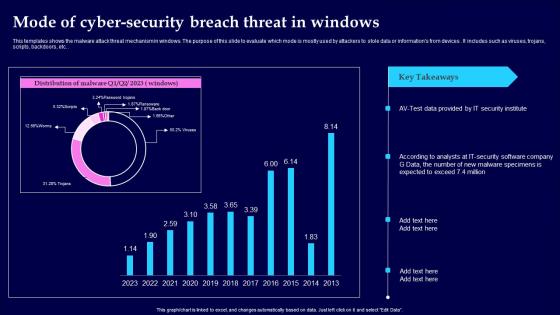
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
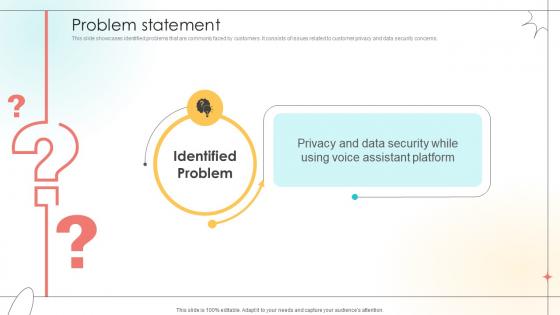
Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck
This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck. This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns.
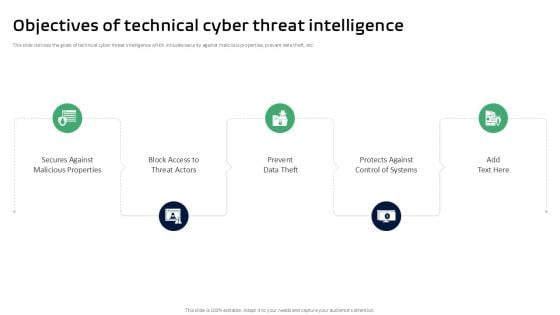
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.

Features Of Next Generation Secure Web Gateway Web Threat Protection System
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Find highly impressive Features Of Next Generation Secure Web Gateway Web Threat Protection System on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Next Generation Secure Web Gateway Web Threat Protection System for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.
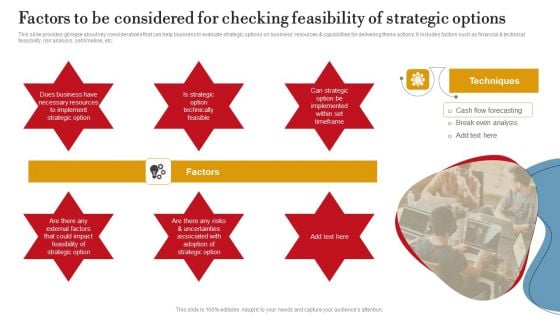
Factors To Be Considered For Checking Feasibility Of Strategic Options Rules PDF
This slide provides glimpse about key considerations that can help business to evaluate strategic options on business resources and capabilities for delivering these actions. It includes factors such as financial and technical feasibility, risk analysis, set timeline, etc. The Factors To Be Considered For Checking Feasibility Of Strategic Options Rules PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Edtech Service Launch And Promotion Plan What Strategies Can Be Adopted For Overcoming Issues Designs PDF
This slide showcases organic and inorganic strategies that can help organization to achieve goals and grow in target market. It also showcases risk and investment involved in both strategies. The Edtech Service Launch And Promotion Plan What Strategies Can Be Adopted For Overcoming Issues Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Formulating International Promotional Campaign Strategy Step 1 Perform Market Research To Evaluate Potential Template PDF
This slide represents first step in international marketing plan i.e. performing marketing assessment and evaluation to find its potential and effectiveness. It includes market growth, competitive analysis, potential risk etc. The Formulating International Promotional Campaign Strategy Step 1 Perform Market Research To Evaluate Potential Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Deploying AML Transaction Monitoring Major Roles And Responsibilities Of Financial Microsoft PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The Deploying AML Transaction Monitoring Major Roles And Responsibilities Of Financial Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
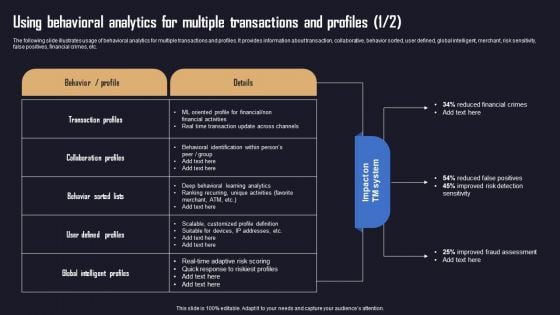
Ensuring Organizational Safety Using AML Transaction Using Behavioral Analytics Microsoft PDF
The following slide illustrates usage of behavioral analytics for multiple transactions and profiles. It provides information about transaction, collaborative, behavior sorted, user defined, global intelligent, merchant, risk sensitivity, false positives, financial crimes, etc. The Ensuring Organizational Safety Using AML Transaction Using Behavioral Analytics Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
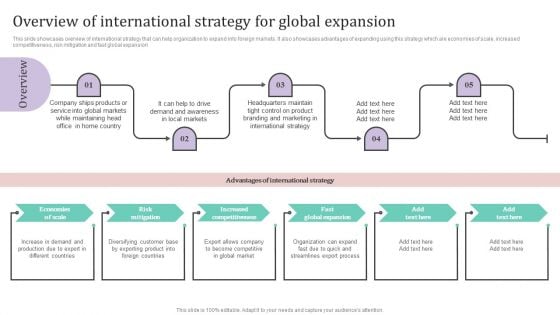
Overview Of International Strategy For Global Expansion Ppt PowerPoint Presentation File Layouts PDF
This slide showcases overview of international strategy that can help organization to expand into foreign markets. It also showcases advantages of expanding using this strategy which are economies of scale, increased competitiveness, risk mitigation and fast global expansion.The Overview Of International Strategy For Global Expansion Ppt PowerPoint Presentation File Layouts PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
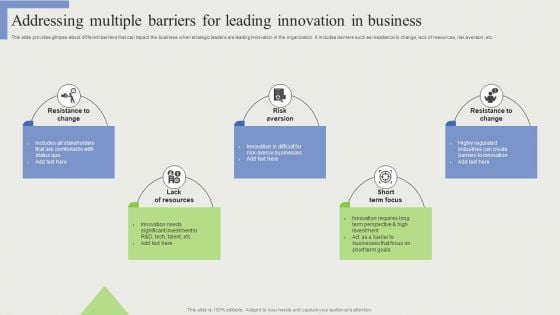
Addressing Multiple Barriers For Leading Innovation In Business Microsoft PDF
This slide provides glimpse about different barriers that can impact the business when strategic leaders are leading innovation in the organization. It includes barriers such as resistance to change, lack of resources, risk aversion, etc. The Addressing Multiple Barriers For Leading Innovation In Business Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
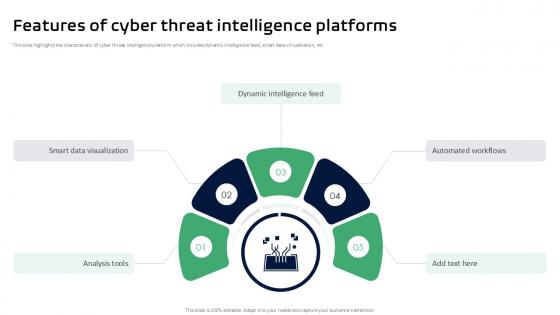
Features Of Cyber Threat Intelligence Platforms Threat Intelligence Ppt Template
This slide highlights the characteristic of cyber threat intelligence platform which includes dynamic intelligence feed, smart data virtualization, etc. . Find highly impressive Features Of Cyber Threat Intelligence Platforms Threat Intelligence Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Cyber Threat Intelligence Platforms Threat Intelligence Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the characteristic of cyber threat intelligence platform which includes dynamic intelligence feed, smart data virtualization, etc. .
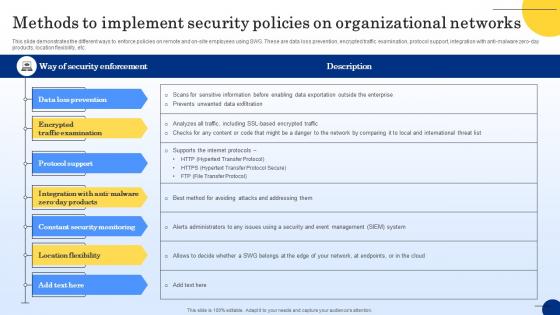
Methods To Implement Security Policies On Web Threat Protection System
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Are you searching for a Methods To Implement Security Policies On Web Threat Protection System that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Methods To Implement Security Policies On Web Threat Protection System from Slidegeeks today. This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.
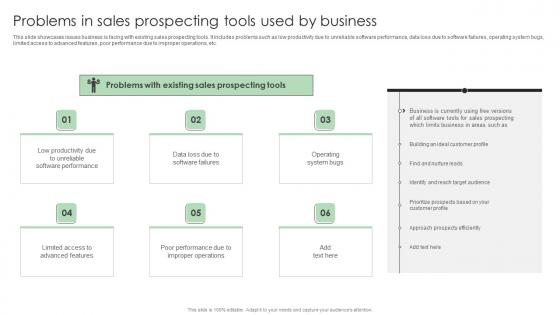
Performance Enhancement Plan Problems In Sales Prospecting Tools Used Ideas Pdf
This slide showcases issues business is facing with existing sales prospecting tools. It includes problems such as low productivity due to unreliable software performance, data loss due to software failures, operating system bugs, limited access to advanced features, poor performance due to improper operations, etc. The Performance Enhancement Plan Problems In Sales Prospecting Tools Used Ideas Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases issues business is facing with existing sales prospecting tools. It includes problems such as low productivity due to unreliable software performance, data loss due to software failures, operating system bugs, limited access to advanced features, poor performance due to improper operations, etc.

Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.
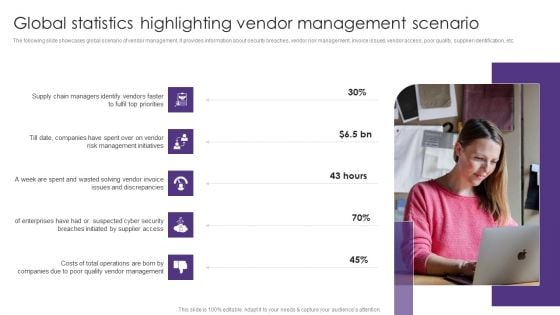
Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches, vendor risk management, invoice issues, vendor access, poor quality, supplier identification, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Problems In Sales Prospecting Tools Sales Performance Enhancement Elements Pdf
This slide showcases issues business is facing with existing sales prospecting tools. It includes problems such as low productivity due to unreliable software performance, data loss due to software failures, operating system bugs, limited access to advanced features, poor performance due to improper operations, etc. The Problems In Sales Prospecting Tools Sales Performance Enhancement Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases issues business is facing with existing sales prospecting tools. It includes problems such as low productivity due to unreliable software performance, data loss due to software failures, operating system bugs, limited access to advanced features, poor performance due to improper operations, etc.
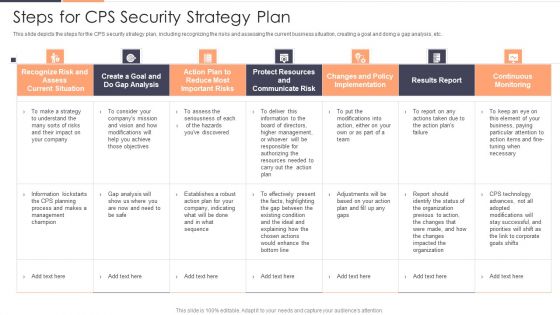
Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF. Use them to share invaluable insights on Recognize Risk, Communicate Risk, Protect Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
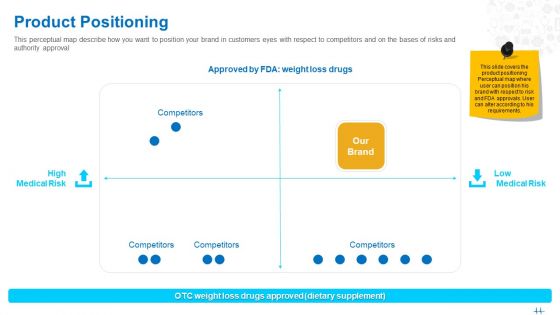
Health Clinic Marketing Product Positioning Ppt Outline Design Templates PDF
This perceptual map describe how you want to position your brand in customers eyes with respect to competitors and on the bases of risks and authority approval Presenting health clinic marketing product positioning ppt outline design templates pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high medical risk, low medical risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
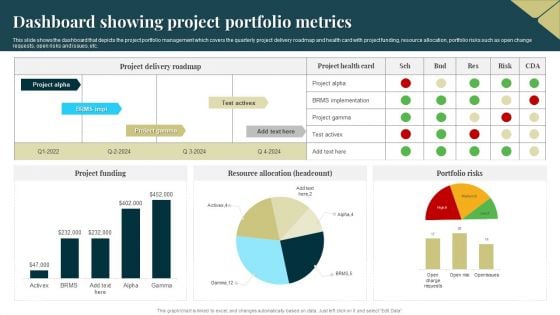
Dashboard Showing Project Portfolio Metrics Microsoft PDF
This slide shows the dashboard that depicts the project portfolio management which covers the quarterly project delivery roadmap and health card with project funding, resource allocation, portfolio risks such as open change requests, open risks and issues, etc. Pitch your topic with ease and precision using this Dashboard Showing Project Portfolio Metrics Microsoft PDF. This layout presents information on Resource Allocation, Portfolio Risks, Project Funding. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Categories Of Practices For Effective Financial Investment Slides PDF
The slide highlights the tips to select efficient portfolios with low risks and high returns. Various types of practices included are identify goals, research, take consultant, optimize the portfolio and define risk. Presenting Categories Of Practices For Effective Financial Investment Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk, Portfolio, Goals. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
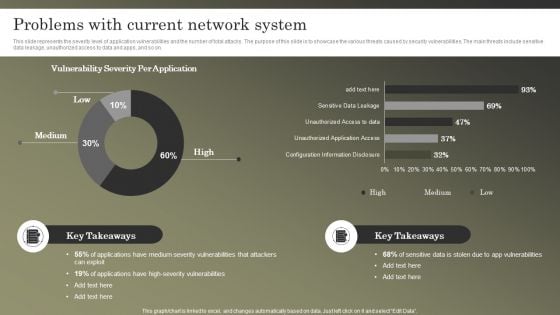
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enhancing Information Technology With Strategic Critical Skills Essential For Cios Designs PDF
This slide provides information regarding major skills equipped by CIOs to sustain a productive work environment in terms of leadership, technical depth, communication, risk management, budgeting, multi-tasker, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Enhancing Information Technology With Strategic Critical Skills Essential For Cios Designs PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
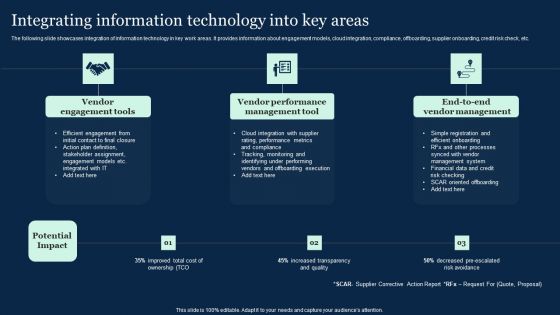
Integrating Information Technology Into Key Areas Effective Vendor Management For Enhancing Brochure PDF
The following slide showcases integration of information technology in key work areas. It provides information about engagement models, cloud integration, compliance, offboarding, supplier onboarding, credit risk check, etc. Explore a selection of the finest Integrating Information Technology Into Key Areas Effective Vendor Management For Enhancing Brochure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Information Technology Into Key Areas Effective Vendor Management For Enhancing Brochure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
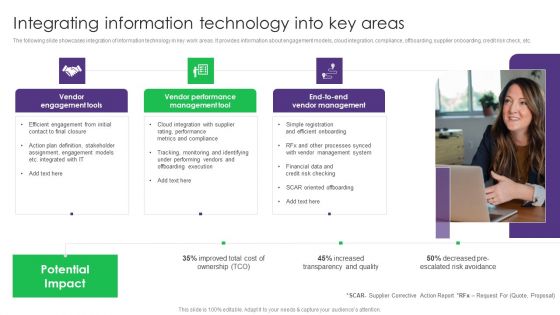
Integrating Information Technology Into Key Areas Vendor Management System Deployment Graphics PDF
The following slide showcases integration of information technology in key work areas. It provides information about engagement models, cloud integration, compliance, offboarding, supplier onboarding, credit risk check, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Integrating Information Technology Into Key Areas Vendor Management System Deployment Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Integrating Information Technology Into Key Areas Vendor Management System Deployment Graphics PDF today and make your presentation stand out from the rest
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
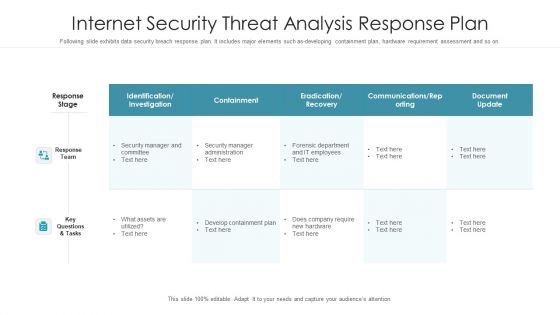
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
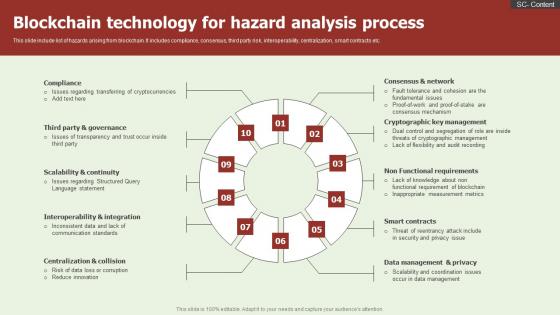
Blockchain Technology For Hazard Analysis Process Microsoft Pdf
This slide include list of hazards arising from blockchain. It includes compliance, consensus, third party risk, interoperability, centralization, smart contracts etc. Showcasing this set of slides titled Blockchain Technology For Hazard Analysis Process Microsoft Pdf. The topics addressed in these templates are Compliance, Smart Contracts, Data Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide include list of hazards arising from blockchain. It includes compliance, consensus, third party risk, interoperability, centralization, smart contracts etc.
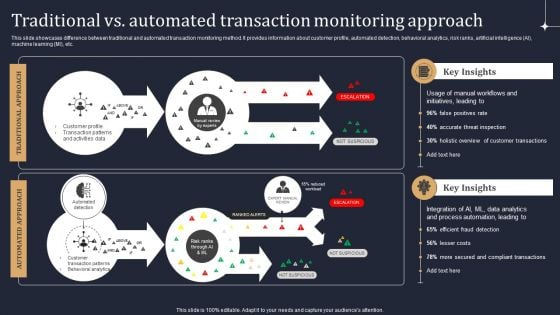
Traditional Vs Automated Transaction Monitoring Approach Information PDF
This slide showcases difference between traditional and automated transaction monitoring method. It provides information about customer profile, automated detection, behavioral analytics, risk ranks, artificial intelligence AI, machine learning MI, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Traditional Vs Automated Transaction Monitoring Approach Information PDF can be your best option for delivering a presentation. Represent everything in detail using Traditional Vs Automated Transaction Monitoring Approach Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Isolation Protocol Guidelines For Workplace Pandemic Company Playbook Information PDF
This template covers isolation coordinator guidelines for the workplace. It also depicts that communication at a distance or through the telephone is preferable to minimize the risk of exposure to other workers, including the isolation coordinator.Slidegeeks is here to make your presentations a breeze with Isolation Protocol Guidelines For Workplace Pandemic Company Playbook Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
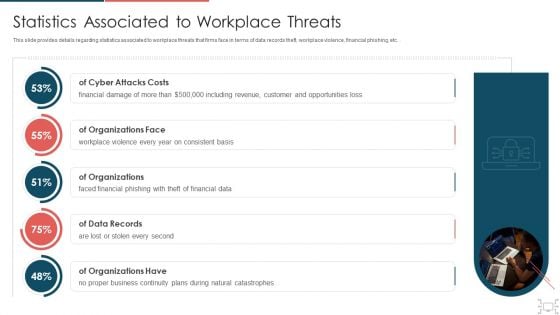
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
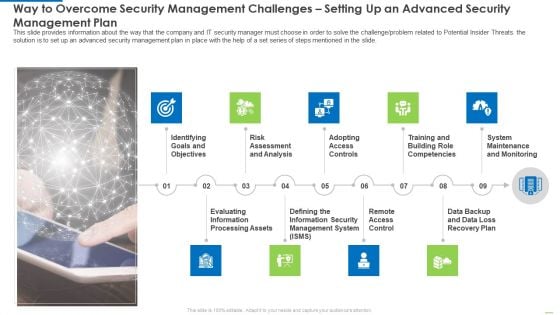
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
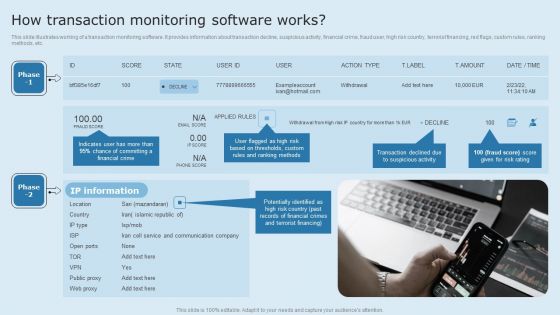
Actual Time Transaction Monitoring Software And Strategies How Transaction Monitoring Software Works Information PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Actual Time Transaction Monitoring Software And Strategies How Transaction Monitoring Software Works Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Actual Time Transaction Monitoring Software And Strategies How Transaction Monitoring Software Works Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Problems In Sales Prospecting Tools Used By Business Ppt File Introduction PDF
This slide showcases issues business is facing with existing sales prospecting tools. It includes problems such as low productivity due to unreliable software performance, data loss due to software failures, operating system bugs, limited access to advanced features, poor performance due to improper operations, etc. The Problems In Sales Prospecting Tools Used By Business Ppt File Introduction PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Effective Financial Planning Assessment Techniques Key Benefits Of Financial Planning And Analysis Inspiration PDF
The following slide outlines multiple advantages of financial planning and analysis. Cost reduction, risk mitigation, smooth fundraising and sales growth are some of the major benefits which are outlined in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Effective Financial Planning Assessment Techniques Key Benefits Of Financial Planning And Analysis Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
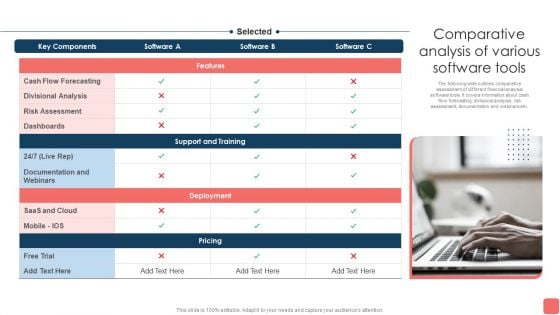
Effective Financial Planning Assessment Techniques Comparative Analysis Of Various Software Tools Rules PDF
The following slide outlines comparative assessment of different financial analysis software tools. It covers information about cash flow forecasting, divisional analysis, risk assessment, documentation and webinars etc. Slidegeeks is here to make your presentations a breeze with Effective Financial Planning Assessment Techniques Comparative Analysis Of Various Software Tools Rules PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
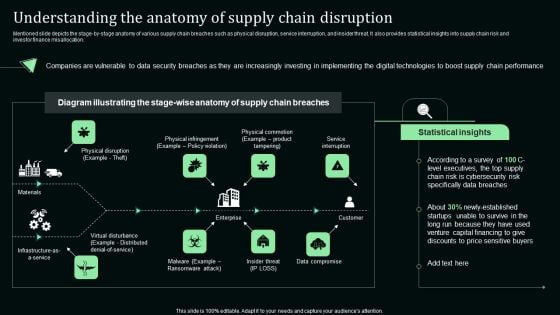
Understanding The Anatomy Of Supply Chain Disruption Stand Out Digital Supply Chain Tactics Enhancing Background PDF
Mentioned slide depicts the stage-by-stage anatomy of various supply chain breaches such as physical disruption, service interruption, and insider threat. It also provides statistical insights into supply chain risk and investor finance misallocation.Slidegeeks has constructed Understanding The Anatomy Of Supply Chain Disruption Stand Out Digital Supply Chain Tactics Enhancing Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Problem Tracker And Mitigation KPI Dashboard Sample PDF
The following slide summarizes the annual data of issue management. It mainly constitutes of number of issues, status, average time taken to resolve, statistics for resolved and resolved issues etc. Showcasing this set of slides titled Problem Tracker And Mitigation KPI Dashboard Sample PDF. The topics addressed in these templates are Problem Tracker, Mitigation KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
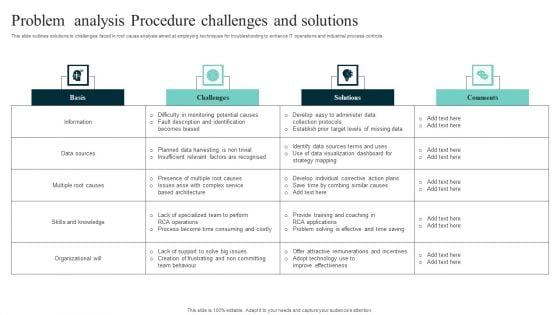
Problem Analysis Procedure Challenges And Solutions Themes PDF
This slide outlines solutions to challenges faced in root cause analysis aimed at employing techniques for troubleshooting to enhance IT operations and industrial process controls Showcasing this set of slides titled Problem Analysis Procedure Challenges And Solutions Themes PDF. The topics addressed in these templates are Data Sources, Information, Organizational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
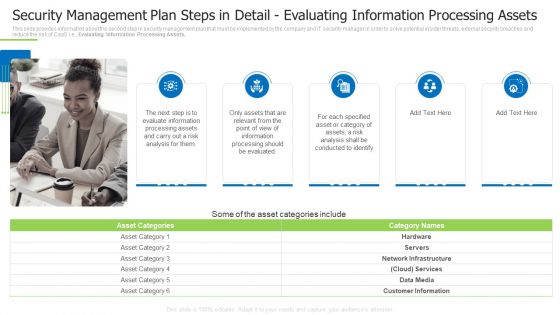
Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
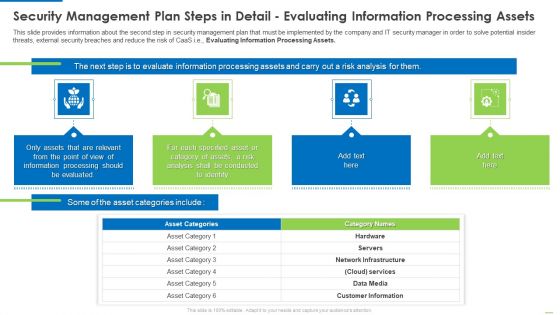
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
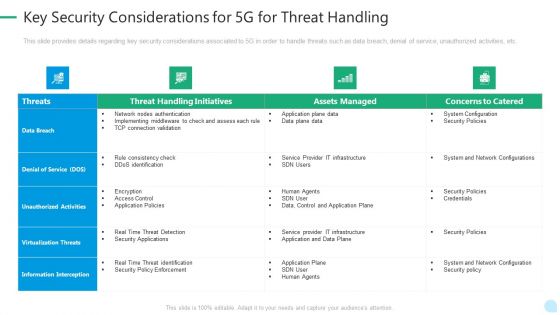
5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Why We Need To Invest In New Technology Investment In Latest Technology To Ensure Diagrams PDF
Mentioned slide provides information on the reasons why the firm should invest in new technology. Reasons covered are generating higher return, improving operational efficiency and risk management.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Why We Need To Invest In New Technology Investment In Latest Technology To Ensure Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
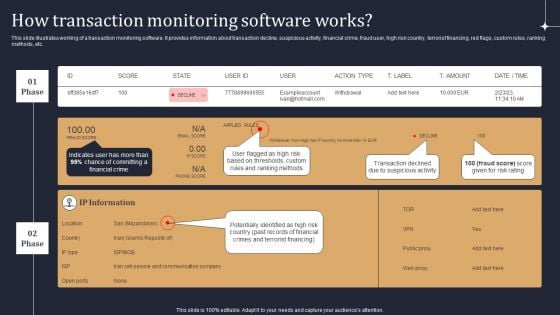
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.
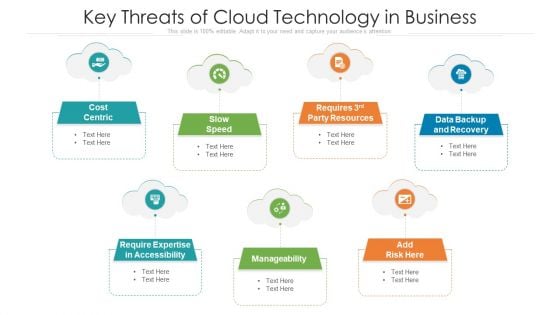
Key Threats Of Cloud Technology In Business Ppt PowerPoint Presentation Gallery Microsoft PDF
Persuade your audience using this key threats of cloud technology in business ppt powerpoint presentation gallery microsoft pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including cost centric, data backup and recovery, manageability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































