Incident Response Plan

IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. This is a IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Alert Monitoring, Attack Investigation, Threat Hunting, Incident Response. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
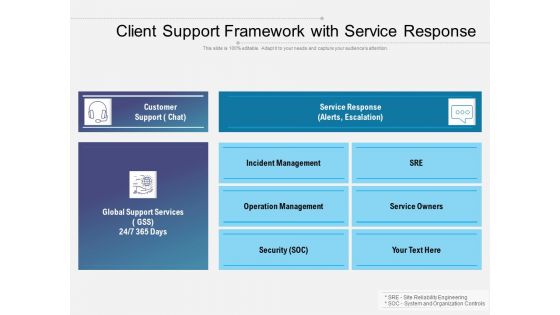
Client Support Framework With Service Response Ppt PowerPoint Presentation Styles Layout Ideas PDF
Presenting this set of slides with name client support framework with service response ppt powerpoint presentation styles layout ideas pdf. The topics discussed in these slides are customer support chat, service response, alerts, escalation, global support services, incident management, operation management, security, service owners, sre. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
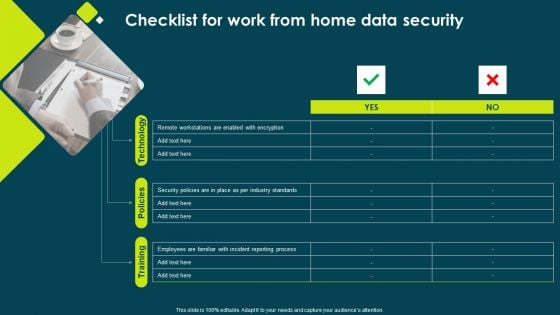
IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
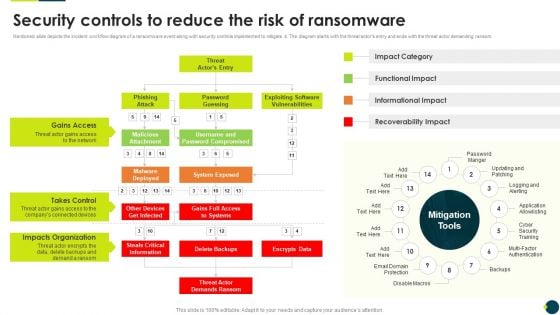
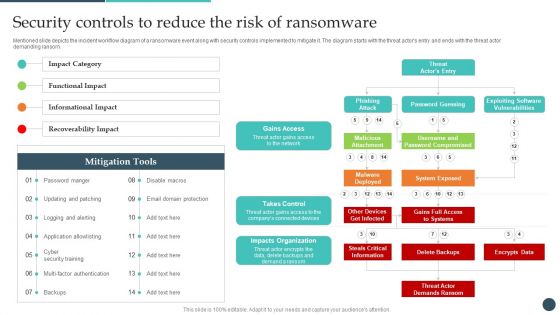
IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
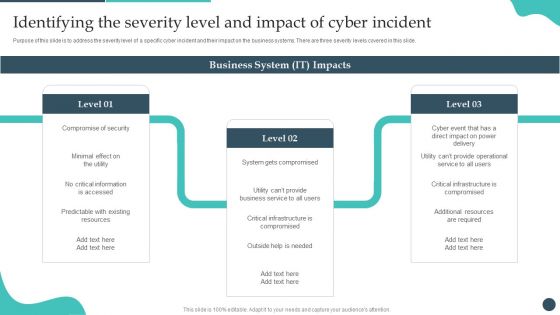
Safety Breach Response Playbook Identifying The Severity Level And Impact Pictures PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. There are so many reasons you need a Safety Breach Response Playbook Identifying The Severity Level And Impact Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
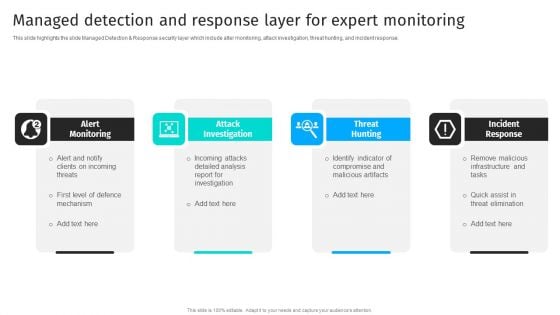
Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF
This slide highlights the slide Managed Detection Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
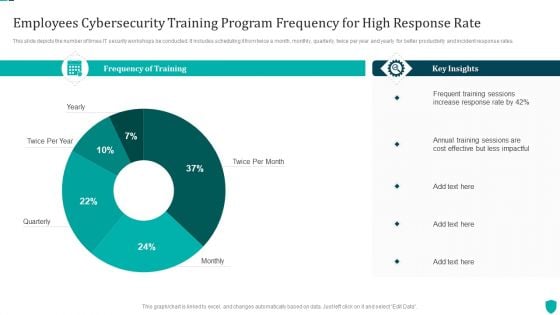
Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF
This slide depicts the number of times IT security workshops be conducted. It includes scheduling it from twice a month, monthly, quarterly, twice per year and yearly for better productivity and incident response rates.Showcasing this set of slides titled Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF. The topics addressed in these templates are Frequency Of Training, Key Insights, Frequent Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Presenting this PowerPoint presentation, titled Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
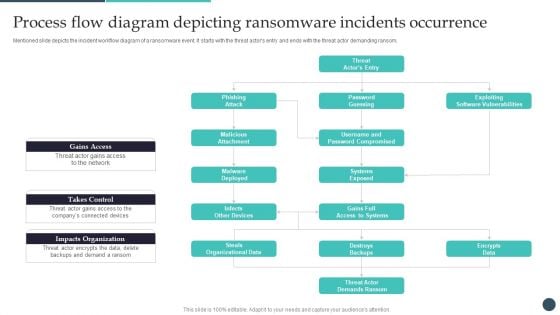
Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF today and make your presentation stand out from the rest.
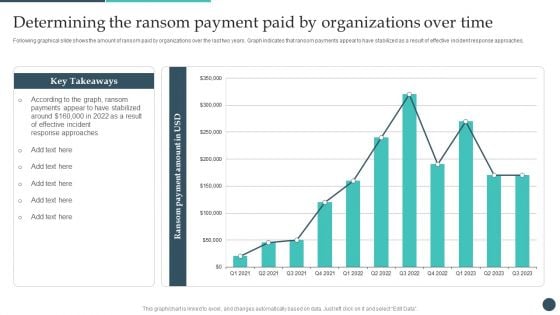
Safety Breach Response Playbook Determining The Ransom Payment Paid Structure PDF
Following graphical slide shows the amount of ransom paid by organizations over the last two years. Graph indicates that ransom payments appear to have stabilized as a result of effective incident response approaches. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Safety Breach Response Playbook Determining The Ransom Payment Paid Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
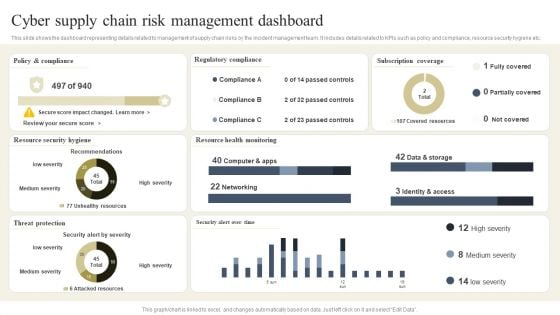
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Social Media Marketing To Boost Direct Response Marketing Emerging Trends Guidelines Pdf
This slide provides insight into the emerging trends of direct response marketing that assist marketers to choose channels and conduct campaigns. Major trends covered are the use of click-to-messenger ads, referral marketing, giveaways and drip marketing campaigns. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Social Media Marketing To Boost Direct Response Marketing Emerging Trends Guidelines Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Social Media Marketing To Boost Direct Response Marketing Emerging Trends Guidelines Pdf. This slide provides insight into the emerging trends of direct response marketing that assist marketers to choose channels and conduct campaigns. Major trends covered are the use of click-to-messenger ads, referral marketing, giveaways and drip marketing campaigns.
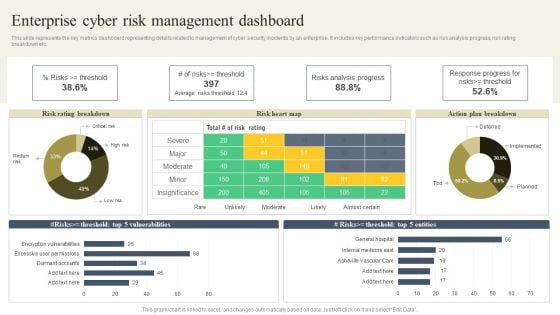
CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.
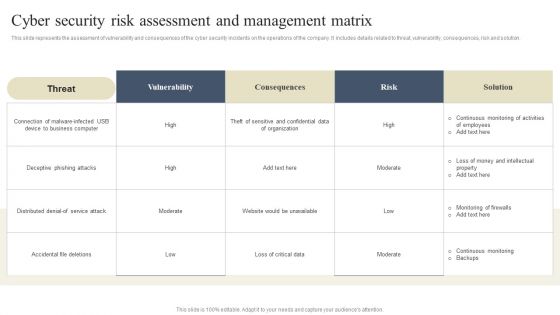
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
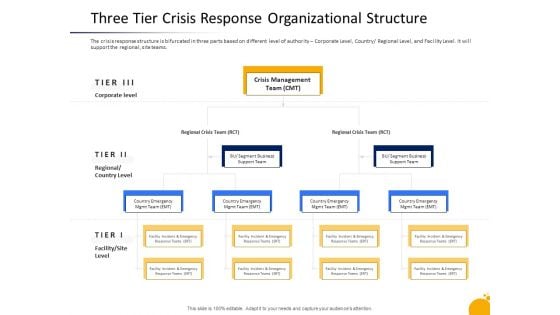
Management Program Presentation Three Tier Crisis Response Organizational Structure Graphics PDF
The crisis response structure is bifurcated in three parts based on different level of authority Corporate Level, Country Regional Level, and Facility Level. It will support the regional, site teams. Presenting management program presentation three tier crisis response organizational structure graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like crisis management team CMT, segment business, facility incident, corporate level, three tier crisis response organizational structure. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For IT Threats Response Playbook Slide Structure PDF
Presenting Table Of Contents For IT Threats Response Playbook Slide Structure PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Responsibilities Incident, Asset Protection, Risk Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
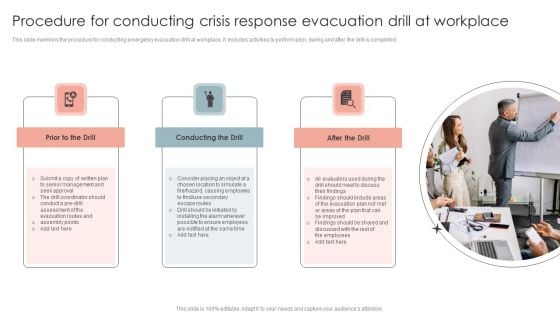
Procedure For Conducting Crisis Response Evacuation Drill At Workplace Diagrams PDF
This slide mentions the procedure for conducting emergency evacuation drill at workplace. It includes activities to perform prior, during and after the drill is completed. Persuade your audience using this Procedure For Conducting Crisis Response Evacuation Drill At Workplace Diagrams PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Prior Drill, Conducting The Drill, After The Drill. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
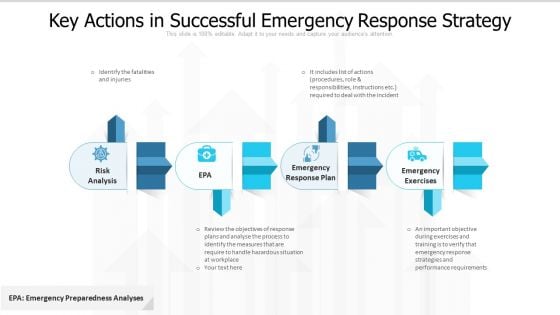
Key Actions In Successful Emergency Response Strategy Ppt PowerPoint Presentation File Design Templates PDF
Presenting key actions in successful emergency response strategy ppt powerpoint presentation file design templates pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including risk analysis, emergency response plan, emergency exercises. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
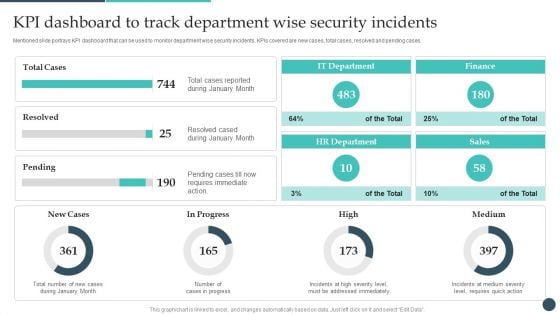
Safety Breach Response Playbook KPI Dashboard To Track Department Wise Rules PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Present like a pro with Safety Breach Response Playbook KPI Dashboard To Track Department Wise Rules PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
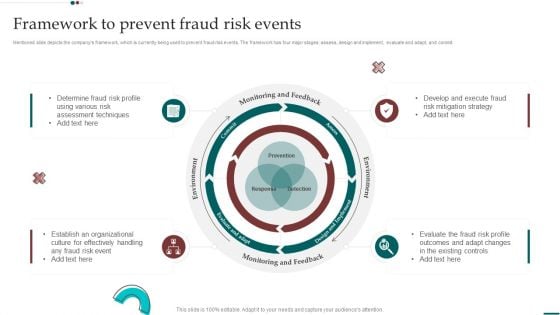
Scam Inquiry And Response Playbook Framework To Prevent Fraud Risk Events Guidelines PDF
Following slide depicts a checklist that the company is using to assess its readiness to effectively deal with any fraud risk events. It also includes considerations about fraud prevention. Get a simple yet stunning designed Scam Inquiry And Response Playbook Framework To Prevent Fraud Risk Events Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Scam Inquiry And Response Playbook Framework To Prevent Fraud Risk Events Guidelines PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
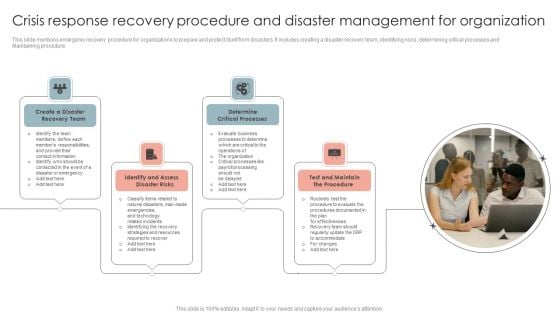
Crisis Response Recovery Procedure And Disaster Management For Organization Template PDF
This slide mentions emergency recovery procedure for organizations to prepare and protect itself from disasters. It includes creating a disaster recovery team, identifying risks, determining critical processes and Maintaining procedure. Persuade your audience using this Crisis Response Recovery Procedure And Disaster Management For Organization Template PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Create a Disaster, Recovery Team, Determine Critical Processes. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Safety Breach Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Safety Breach Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Improving Client Response Rate Through Smooth Onboarding Journey Ppt PowerPoint Presentation Complete Deck With Slides
This Improving Client Response Rate Through Smooth Onboarding Journey Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This fifty nine slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.

Table Of Contents Establishing Workplace Safety Management For Lowering Incident Rates Ppt PowerPoint Presentation File Pictures PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents Establishing Workplace Safety Management For Lowering Incident Rates Ppt PowerPoint Presentation File Pictures PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents Establishing Workplace Safety Management For Lowering Incident Rates Ppt PowerPoint Presentation File Pictures PDF today and make your presentation stand out from the rest.

How Aviation Industry Coping With COVID 19 Pandemic Facilitating Electronic Incident Reporting System Post COVID 19 Topics PDF
This slide shows the framework of EIRS that organizations can facilitate post COVID 19. The system can be used for reporting incidents takin place at workstation.Deliver and pitch your topic in the best possible manner with this how aviation industry coping with COVID 19 pandemic facilitating electronic incident reporting system post COVID 19 topics pdf. Use them to share invaluable insights on incident occurs, team takes action, incident resolved, incident resolution, organize your team and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
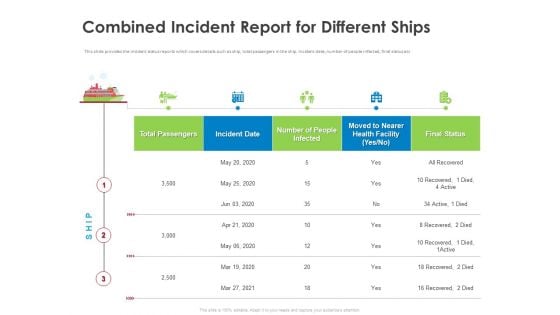
COVID 19 Risk Analysis Mitigation Policies Ocean Liner Sector Combined Incident Report For Different Ships Clipart PDF
This slide provides the incident status reports which covers details such as ship, total passengers in the ship. Incident date, number of people infected, final status etc. Deliver an awe inspiring pitch with this creative covid 19 risk analysis mitigation policies ocean liner sector combined incident report for different ships clipart pdf bundle. Topics like combined incident report for different ships can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
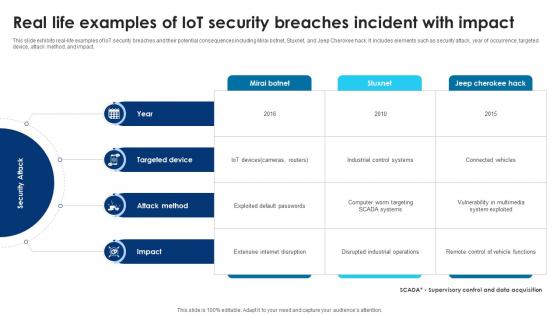
Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V
This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact. Get a simple yet stunning designed Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact.
Contingency Plan Template 6 Ppt PowerPoint Presentation Visual Aids Icon
This is a contingency plan template 6 ppt powerpoint presentation visual aids icon. This is a two stage process. The stages in this process are section, event handling, incident topology, response plans, description.

Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
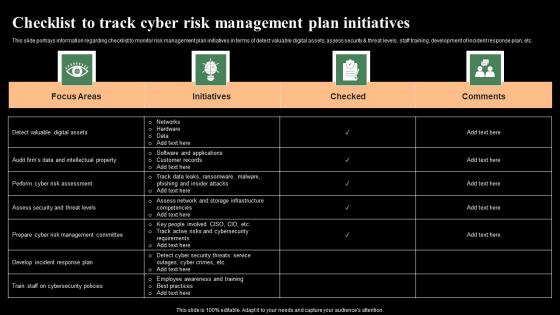
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc.
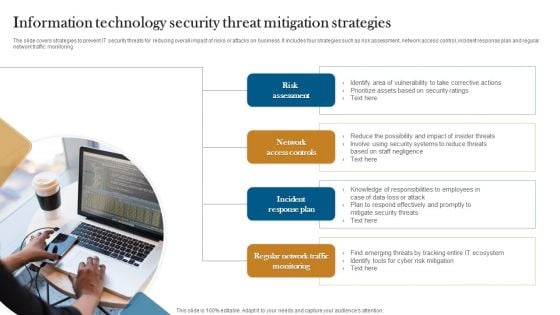
Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
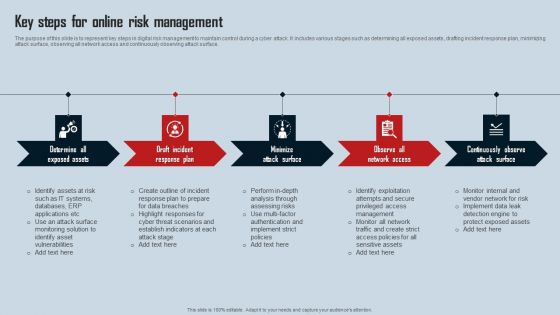
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
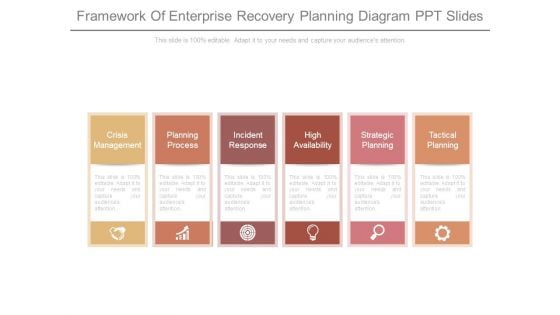
Framework Of Enterprise Recovery Planning Diagram Ppt Slides
This is a framework of enterprise recovery planning diagram ppt slides. This is a six stage process. The stages in this process are crisis management, planning process, incident response, high availability, strategic planning, tactical planning.

Contingency Plan Introduction Ppt PowerPoint Presentation Inspiration Graphic Images
This is a contingency plan introduction ppt powerpoint presentation inspiration graphic images. This is a eight stage process. The stages in this process are section, description, introduction, response plans, incident topology.
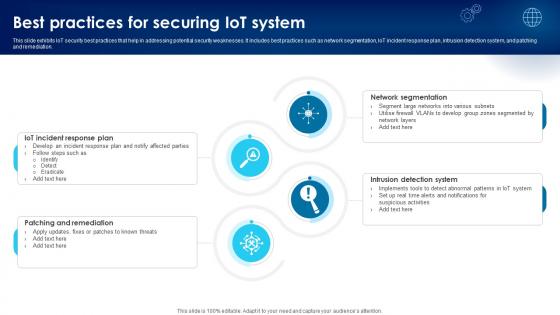
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.
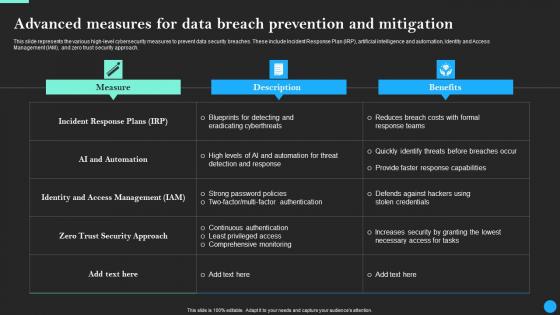
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
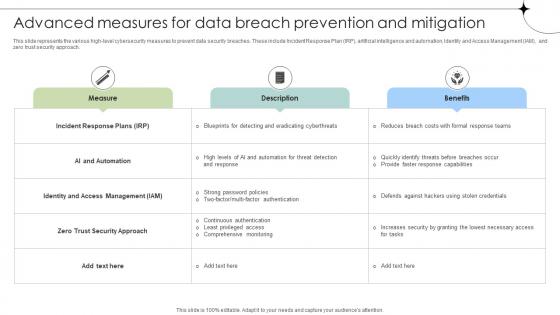
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
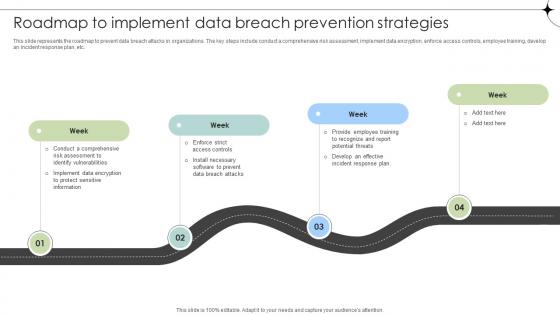
Roadmap To Implement Data Breach Prevention Strategies Data Fortification Strengthening Defenses
This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.Boost your pitch with our creative Roadmap To Implement Data Breach Prevention Strategies Data Fortification Strengthening Defenses. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
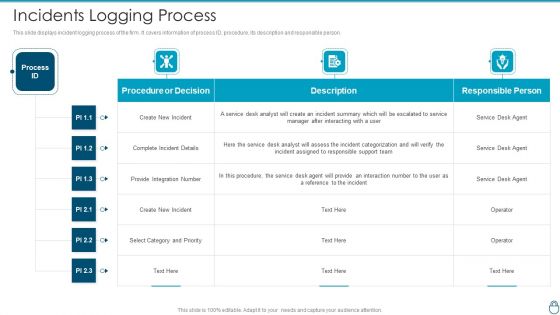
Cybersecurity Risk Administration Plan Incidents Logging Process Sample PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Logging Process Sample PDF Use them to share invaluable insights on Incident Assigned, Select Category And Priority, Reference To The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managing ITIL Incidents Planning Content Introduction PDF
Presenting this set of slides with name managing itil incidents planning content introduction pdf. This is a nine stage process. The stages in this process are management, implement, performance, matrix, roles and responsibilities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Managing ITIL Incidents Planning Quotes Rules PDF
Presenting this set of slides with name managing itil incidents planning quotes rules pdf. The topics discussed in these slide is quotes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
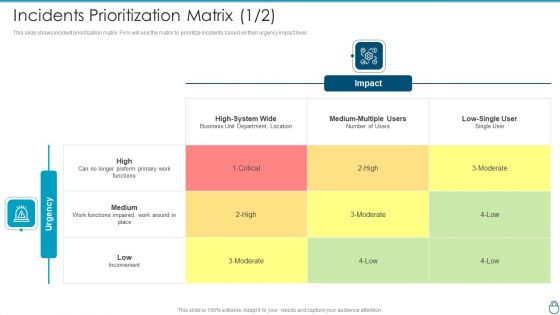
Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF bundle. Topics like Business Unit Department, Functions Impaired, Medium Multiple can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Service Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Service Information PDF Use them to share invaluable insights on Enterprise Or Multiple Segments, Event Imminent, Affecting Service and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
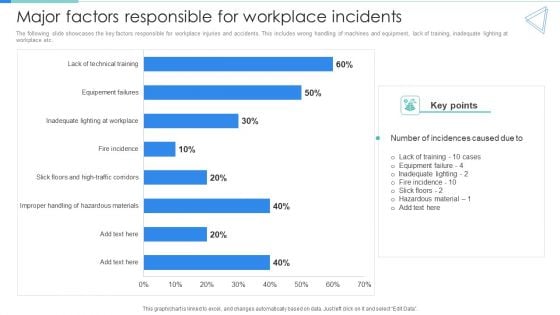
Deployment Of Workplace Safety Management Program Major Factors Responsible For Workplace Incidents Ideas PDF
The following slide showcases the key factors responsible for workplace injuries and accidents. This includes wrong handling of machines and equipment, lack of training, inadequate lighting at workplace etc. Do you know about Slidesgeeks Deployment Of Workplace Safety Management Program Major Factors Responsible For Workplace Incidents Ideas PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
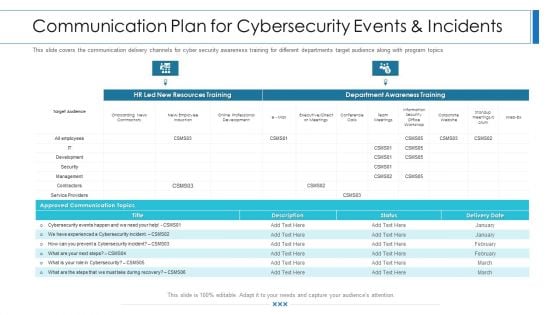
Workforce Security Realization Coaching Plan Communication Plan For Cybersecurity Events And Incidents Graphics PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan communication plan for cybersecurity events and incidents graphics pdf bundle. Topics like resources training, department awareness training, approved communication topics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
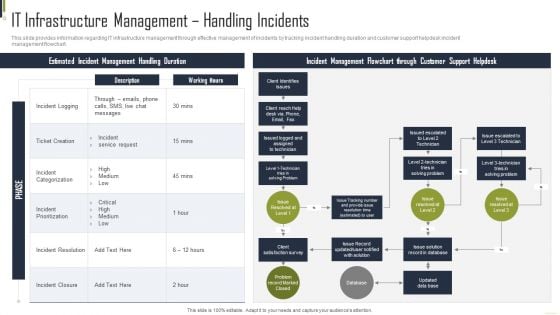
IT Infrastructure Management Handling Incidents Microsoft PDF
This slide provides information regarding IT infrastructure management through effective management of incidents by tracking incident handling duration and customer support helpdesk incident management flowchart. Deliver an awe inspiring pitch with this creative IT Infrastructure Management Handling Incidents Microsoft PDF bundle. Topics like Estimated Incident, Management Handling, Issue Solution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
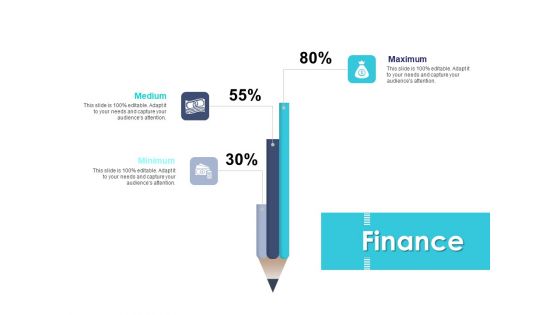
Managing ITIL Incidents Planning Finance Ppt Outline Files PDF
Presenting this set of slides with name managing itil incidents planning finance ppt outline files pdf. This is a three stage process. The stages in this process are medium, maximum, minimum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
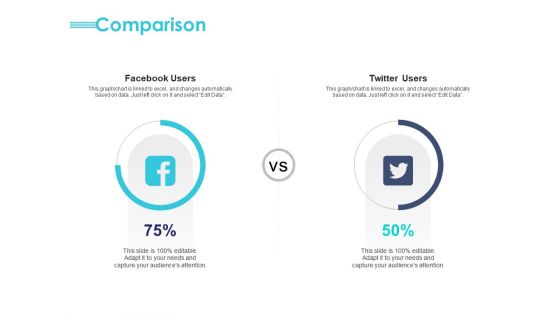
Managing ITIL Incidents Planning Comparison Ppt Inspiration Portrait PDF
Presenting this set of slides with name managing itil incidents planning comparison ppt inspiration portrait pdf. This is a two stage process. The stages in this process are facebook users, twitter users. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
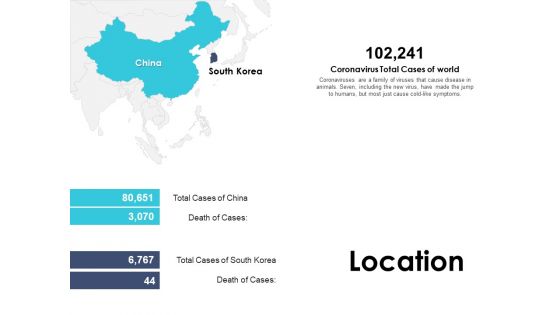
Managing ITIL Incidents Planning Location Ppt Infographics Slide Portrait PDF
Presenting this set of slides with name managing itil incidents planning location ppt infographics slide portrait pdf. This is a two stage process. The stages in this process are location. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Managing ITIL Incidents Planning Timeline Ppt Icon Tips PDF
Presenting this set of slides with name managing itil incidents planning timeline ppt icon tips pdf. This is a three stage process. The stages in this process are timeline, 2018 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































