Information Security Gap Analysis
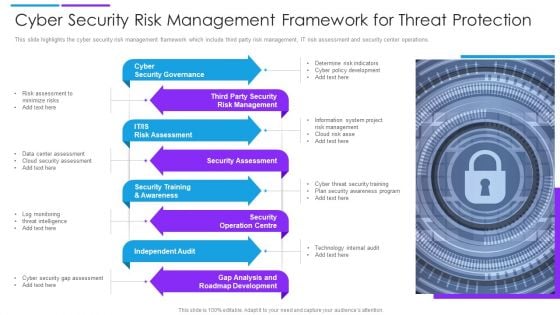
Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
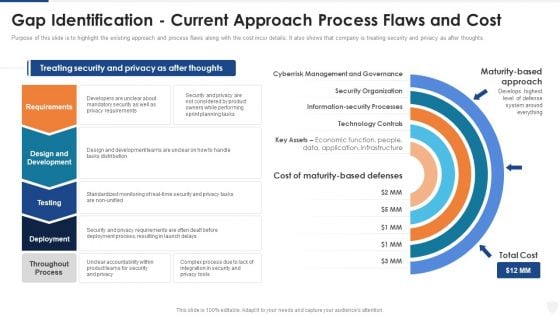
Gap Identification Current Approach Process Flaws And Cost Ppt Show Model PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. This is a gap identification current approach process flaws and cost ppt show model pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology controls, management, planning, requirements, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
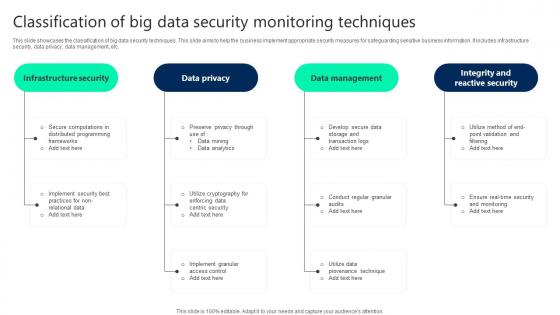
Classification Of Big Data Security Monitoring Techniques Professional pdf
This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Pitch your topic with ease and precision using this Classification Of Big Data Security Monitoring Techniques Professional pdf. This layout presents information on Infrastructure Security, Data Privacy, Data Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc.

Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, This template with an image of helps you chart the course of your presentation. Use our Success PowerPoint Templates because,Break it all down to Key Result Areas. Use our Future PowerPoint Templates because, You have some exciting plans to spread goodwill among the underprivileged, Expound on your ideas and show to your colleagues how they can help others and in the process increase your Brand value. Use our Business PowerPoint Templates because, Expound on how you plan to gain their confidence and assure them of continued and consistent excellence in quality of service. Use our Finance PowerPoint Templates because, Watch their mental juices begin to flow.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock, success, future, security, business, finance. The prominent colors used in the PowerPoint template are Blue, Yellow, Black Enjoy success and praise with our Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112. You will come out on top.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
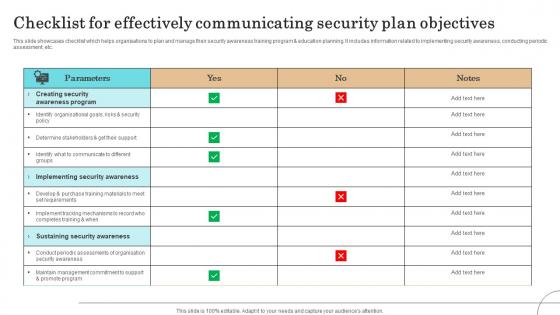
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.
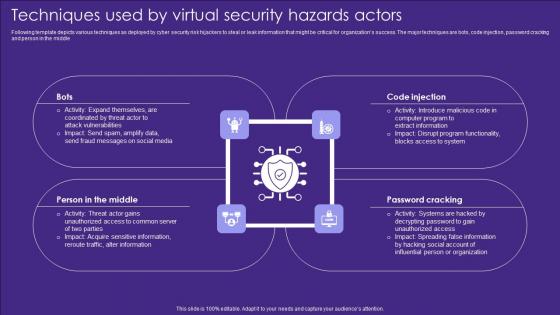
Techniques Used By Virtual Security Hazards Actors Professional Pdf
Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Pitch your topic with ease and precision using this Techniques Used By Virtual Security Hazards Actors Professional Pdf. This layout presents information on Code Injection, Password Cracking, Middle. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle
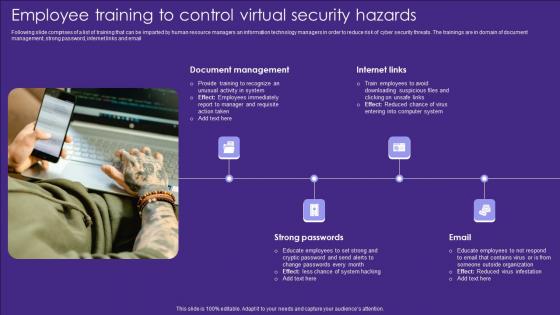
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email
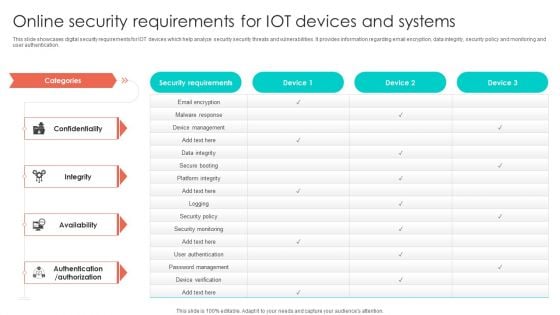
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
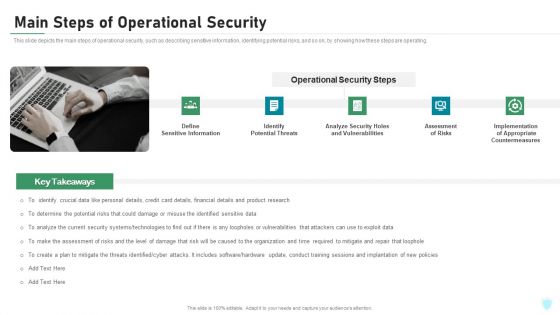
Main Steps Of Operational Security Ppt Ideas Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a main steps of operational security ppt ideas summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential threats, analyze security holes and vulnerabilities, assessment of risks, implementation of appropriate countermeasures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
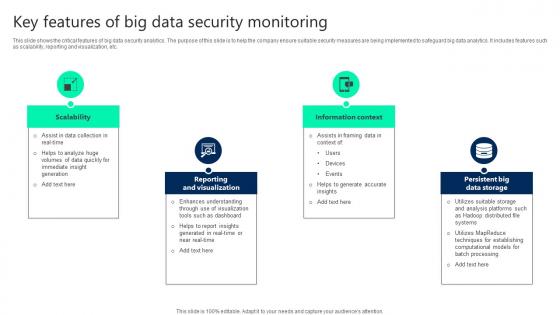
Key Features Of Big Data Security Monitoring Ideas pdf
This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Pitch your topic with ease and precision using this Key Features Of Big Data Security Monitoring Ideas pdf. This layout presents information on Scalability, Reporting And Visualization, Information Context. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc.
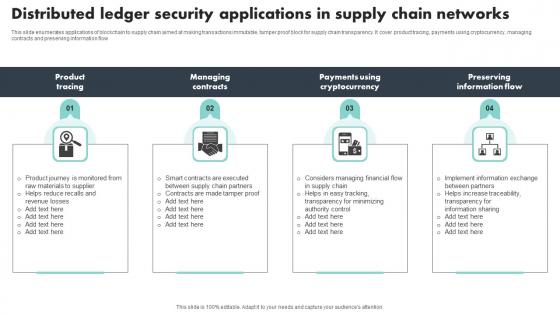
Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf
This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow Pitch your topic with ease and precision using this Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf This layout presents information on Product Tracing, Managing Contracts, Preserving Information Flow It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow

Table Of Contents Cyber Safety Incident Management Security Microsoft PDF
This is a table of contents cyber safety incident management security microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current scenario assessment, handling cyber threats to secure digital assets, ensuring physical security, securing firm from natural calamity threats . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
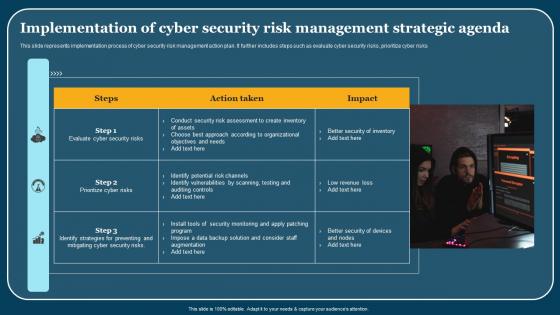
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
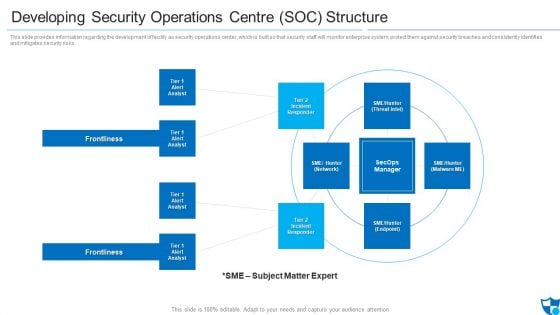
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
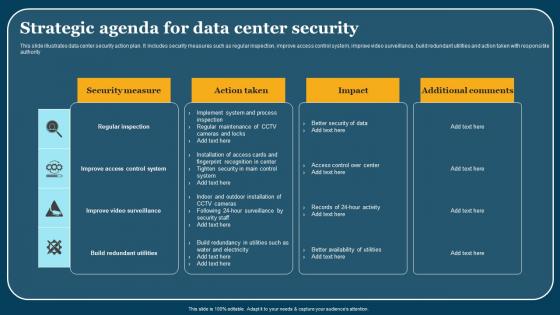
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.
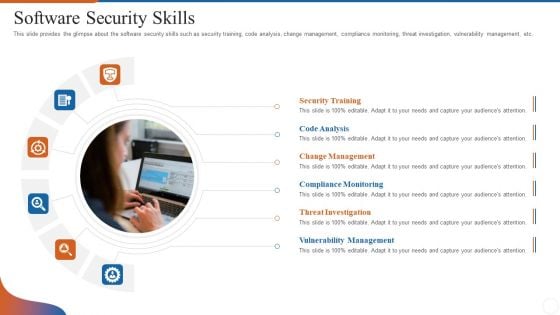
Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
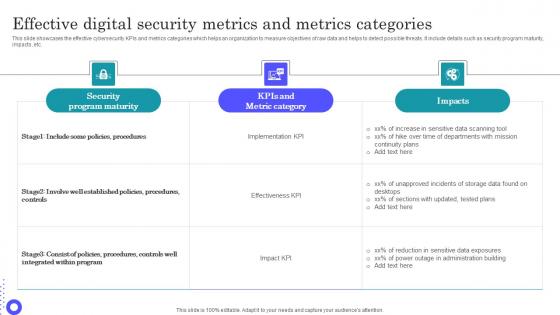
Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the effective cybersecurity KPIs and metrics categories which helps an organization to measure objectives of raw data and helps to detect possible threats. It include details such as security program maturity, impacts, etc.
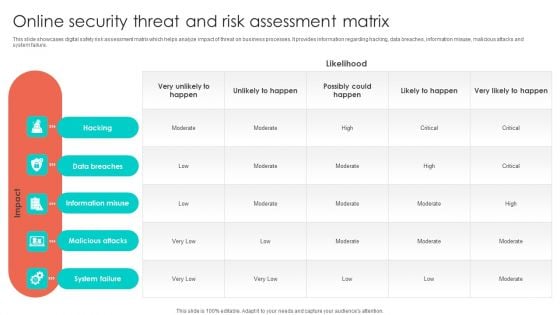
Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
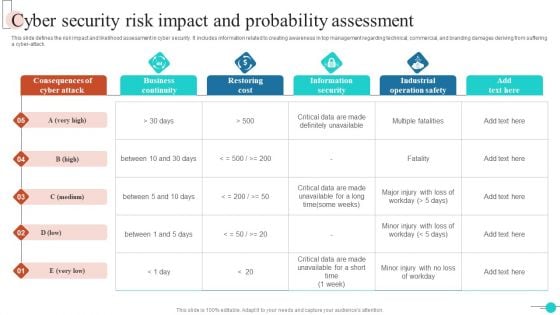
Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
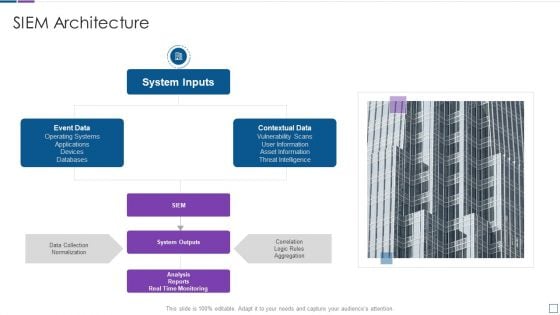
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
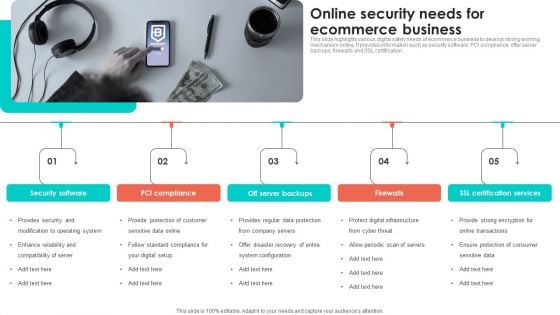
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
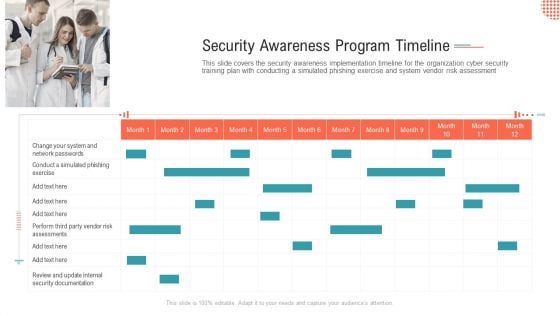
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Data Science In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Data Science In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Data Science. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Data Science In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
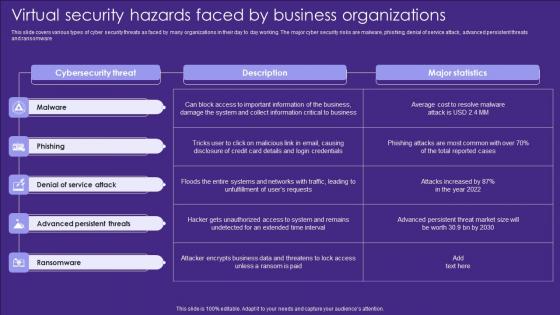
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
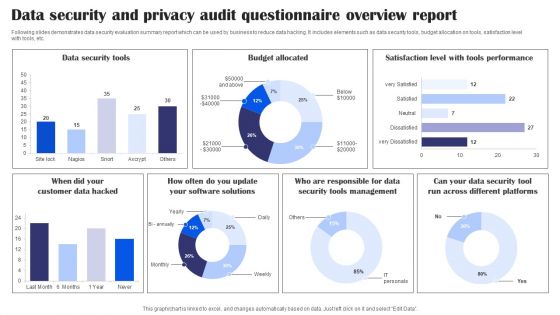
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
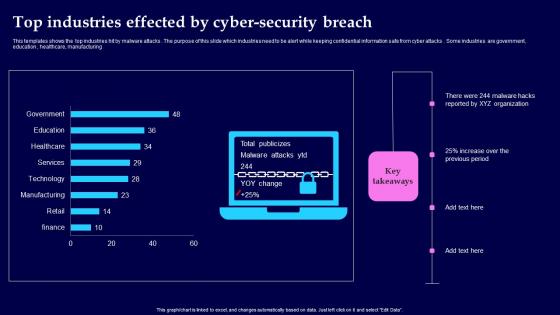
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing
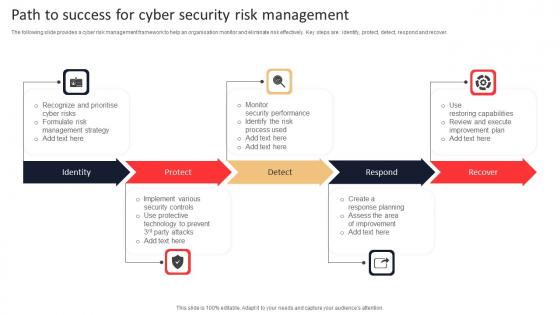
Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.
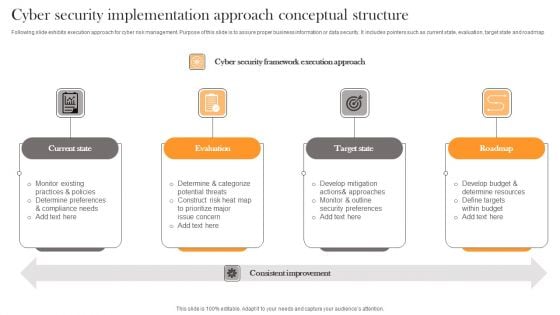
Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
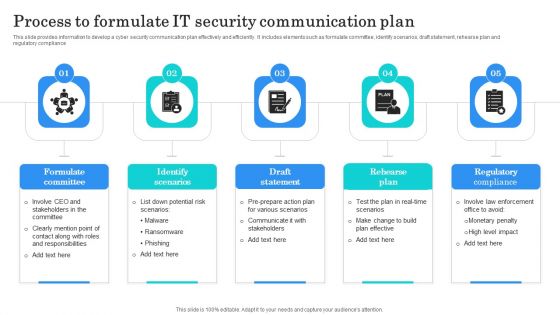
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
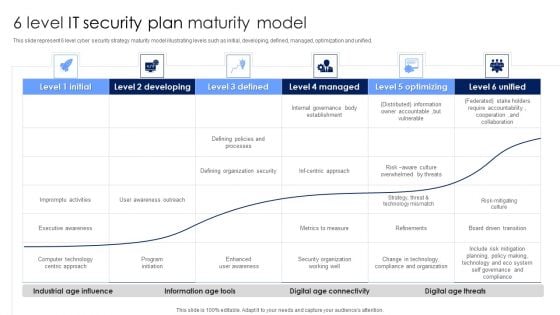
6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Customer Engagement Data Security In Powerpoint And Google Slides Cpb
Introducing our well designed Customer Engagement Data Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Customer Engagement Data Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Customer Engagement Data Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Analytics Use Cases In Powerpoint And Google Slides Cpb
Introducing our well designed Security Analytics Use Cases In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Analytics Use Cases. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Analytics Use Cases In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
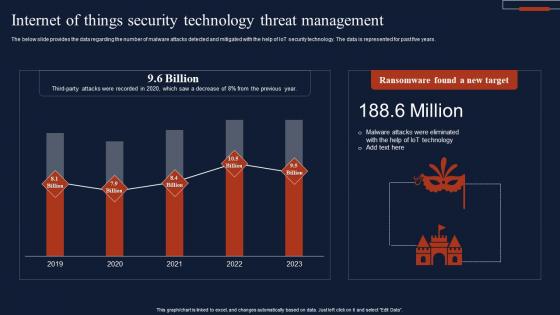
Internet Of Things Security Technology Threat Management Summary Pdf
The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Pitch your topic with ease and precision using this Internet Of Things Security Technology Threat Management Summary Pdf This layout presents information on Ransomware Found, New Target, Threat Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years.
Protection Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IT Security Roadmap In Powerpoint And Google Slides Cpb
Introducing our well designed IT Security Roadmap In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like IT Security Roadmap. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our IT Security Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
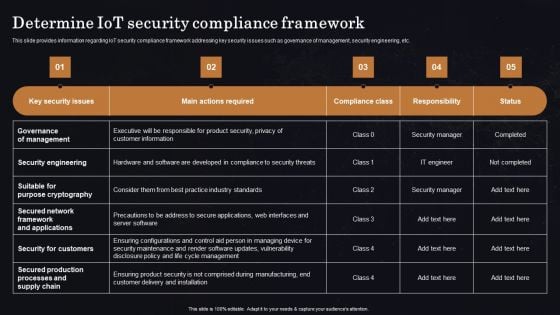
Determine Iot Security Compliance Framework Ppt Professional Vector PDF
This slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Get a simple yet stunning designed Determine Iot Security Compliance Framework Ppt Professional Vector PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Iot Security Compliance Framework Ppt Professional Vector PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
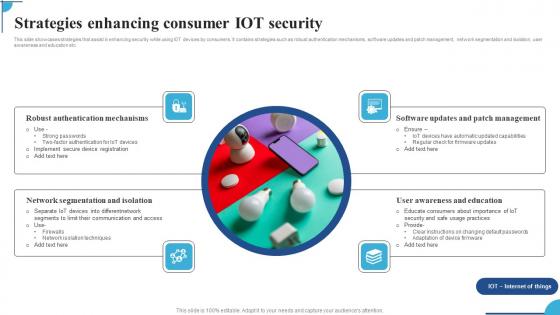
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.
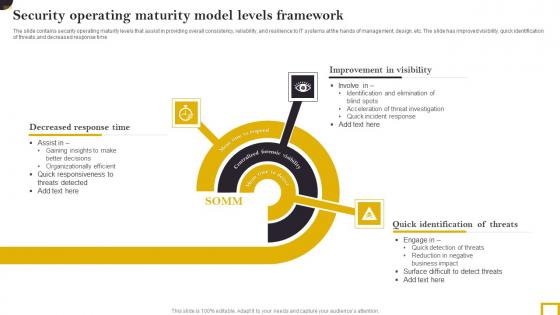
Security Operating Maturity Model Levels Framework Elements Pdf
The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Pitch your topic with ease and precision using this Security Operating Maturity Model Levels Framework Elements Pdf. This layout presents information on Decreased Response Time,Improvement Visibility, Quick Identification Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time.

RPA Security Framework In Powerpoint And Google Slides Cpb
Introducing our well designed RPA Security Framework In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like RPA Security Framework. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our RPA Security Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf
Introducing our well designed Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Tokenization Strategies For Data Security PPT Presentation
Introducing our well designed Icons Slide For Tokenization Strategies For Data Security PPT Presentation set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Tokenization Strategies For Data Security PPT Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Personal Security Apps Android In Powerpoint And Google Slides Cpb
Introducing our well designed Personal Security Apps Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Personal Security Apps Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Personal Security Apps Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Application Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Application Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Application Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































