Network Security
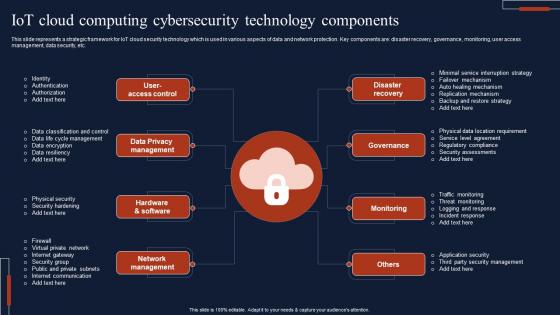
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
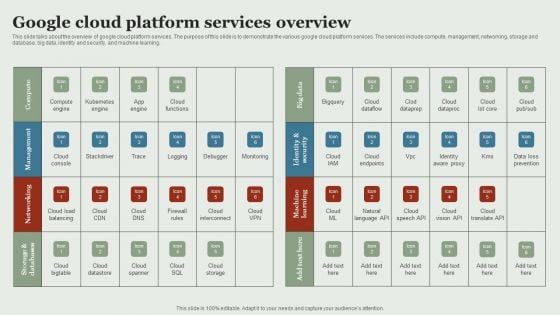
Google Cloud Service Models Google Cloud Platform Services Overview Information PDF
This slide talks about the overview of google cloud platform services. The purpose of this slide is to demonstrate the various google cloud platform services. The services include compute, management, networking, storage and database, big data, identity and security, and machine learning. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Google Cloud Service Models Google Cloud Platform Services Overview Information PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
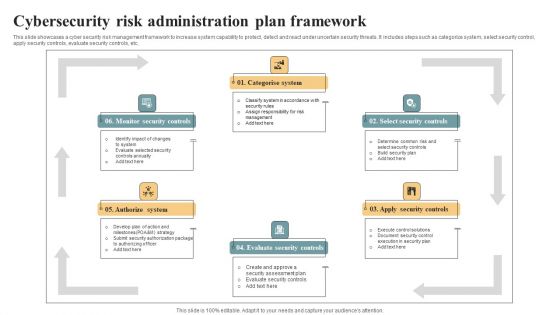
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates
We present our colorful illustration using arrows flow chart business plan PowerPoint templates.Use our Arrows PowerPoint Templates because,You are the Champion of your team shall anoint. Use our Shapes PowerPoint Templates because, This will helps you to explore the minutest detail of each concept and follow the trail to its conclusion. Use our Signs PowerPoint Templates because,You can take it along a sure fire road to good profit. Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Process and Flows PowerPoint Templates because,They will Amplify your basic corporate concept and forefront the benefits of overlapping processes to arrive at common goals.Use these PowerPoint slides for presentations relating to 3d, background, colorful, communication, computing, concept, connection, data, database, design, development, digital, download, glossy, graphic, illustration, information, internet, isolated, network, networking, online, orange, plastic, security, segment, server, store, symbol, system, technology, upload, website,. The prominent colors used in the PowerPoint template are Green, Red, Black. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are Spiffy. The feedback we get is that our data PowerPoint templates and PPT Slides are Versatile. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are designed by a team of presentation professionals. Presenters tell us our concept PowerPoint templates and PPT Slides are Appealing. The feedback we get is that our colorful illustration using arrows flow chart business plan PowerPoint templates are Tranquil. Professionals tell us our concept PowerPoint templates and PPT Slides are Gorgeous. Burn away doubts with our Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates. You will come out on top.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
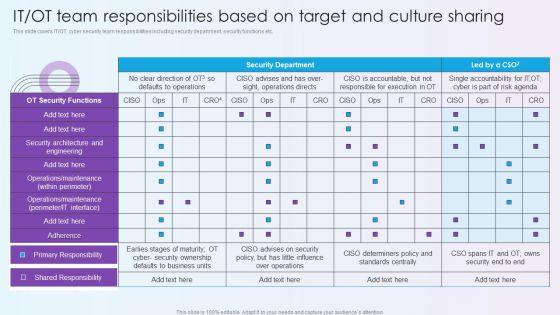
Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF
This slide covers IT or OT cyber security team responsibilities including security department, security functions etc. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF. Use them to share invaluable insights on Security Functions, Security Ownership, Determiners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
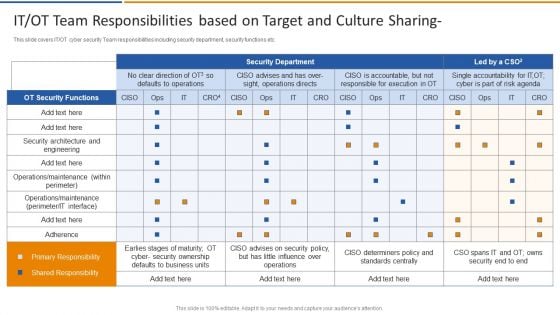
Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF bundle. Topics like OT Security Functions, Security architecture, Primary Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
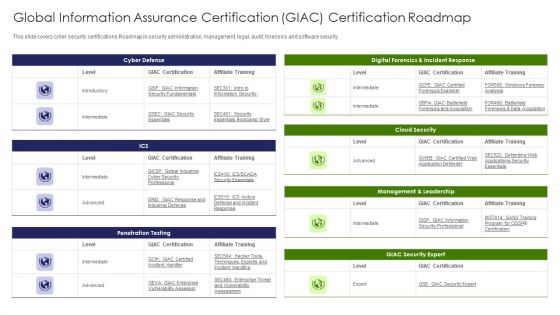
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stock Photo 3d Globe Green Glass PowerPoint Slide
This graphic image has been crafted with globe and chain. In this image globe is secured with chain which shows the concept of global security. Use this image to display global security issues and benefits in any presentation.
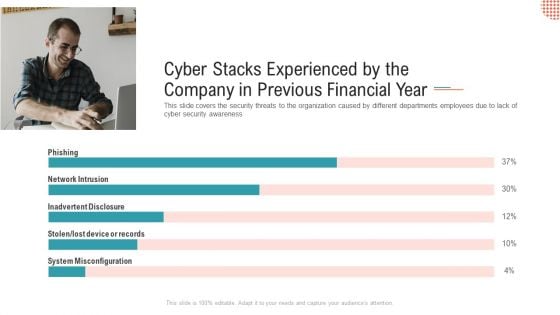
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
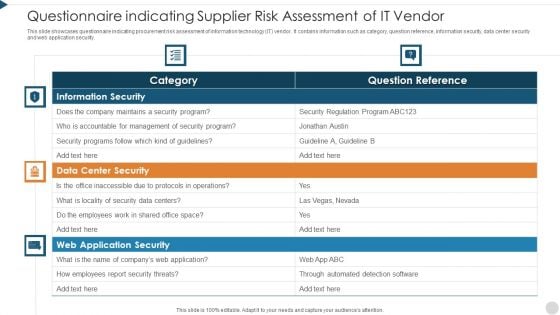
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
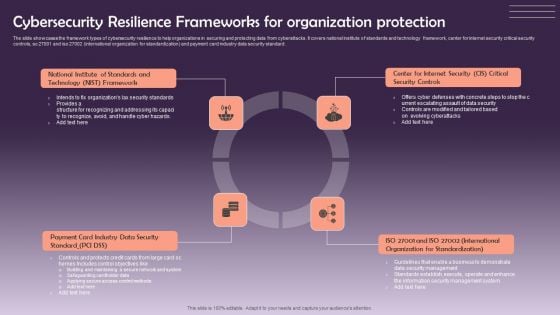
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
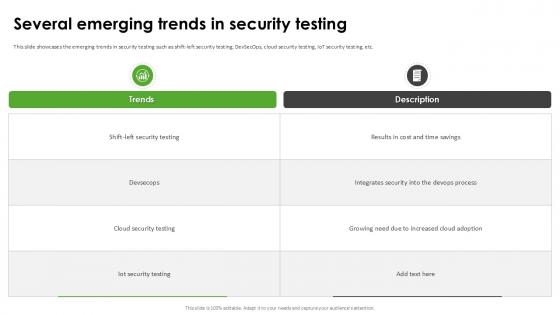
Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint
This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc. Are you searching for a Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint from Slidegeeks today. This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc.

Stock Photo Blue Umbrella Over Usa Flag Print Text PowerPoint Slide
This Power Point slide has been designed with graphic of blue umbrella and US flag design. This image slide contains the concept of USA security and protection schemes. Use this professional design to build presentation for security related topics.
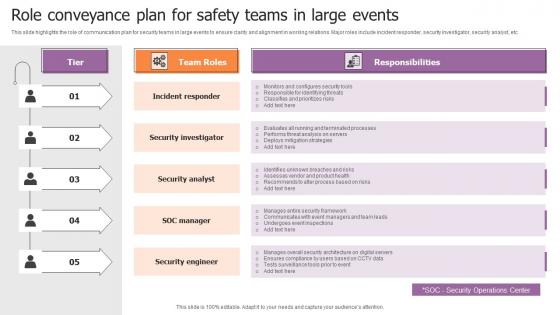
Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf
This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc. Showcasing this set of slides titled Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf. The topics addressed in these templates are Incident Responder, Security Investigator, Security Analyst. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc.
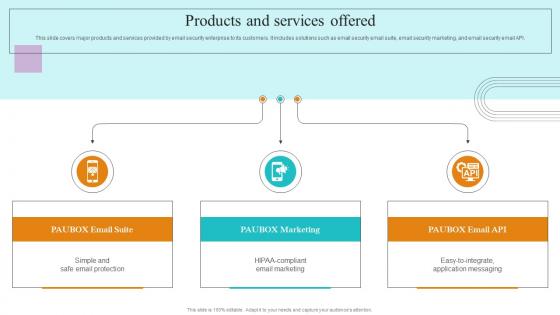
Products And Services Offered Paubox Capital Funding Pitch Deck Slides Pdf
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Products And Services Offered Paubox Capital Funding Pitch Deck Slides Pdf from Slidegeeks and deliver a wonderful presentation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
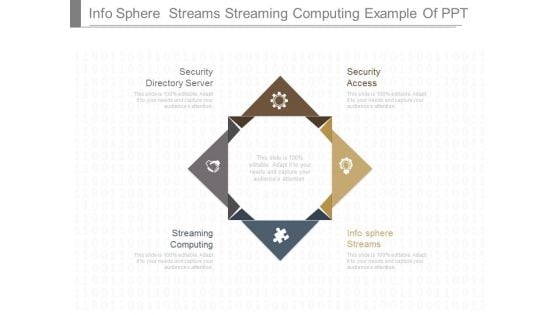
Info Sphere Streams Streaming Computing Example Of Ppt
This is a info sphere streams streaming computing example of ppt. This is a four stage process. The stages in this process are security directory server, security access, streaming computing, info sphere streams.

Critical Infrastructure And Climate Powerpoint Guide
This is a critical infrastructure and climate powerpoint guide. This is a four stage process. The stages in this process are critical infrastructure and climate, national security strategy, execute order, homeland security review.

Profile Monitoring Methodology Sample Diagram Sample Ppt Presentation
This is a profile monitoring methodology sample diagram sample ppt presentation. This is a five stage process. The stages in this process are macro analysis, security screening, gaussian kernel, security screening, sector and asset class focus.
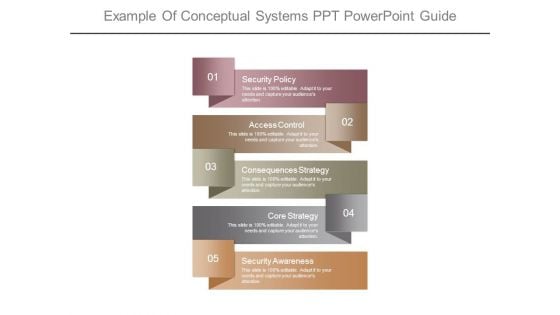
Example Of Conceptual Systems Ppt Powerpoint Guide
This is a example of conceptual systems ppt powerpoint guide. This is a five stage process. The stages in this process are security policy, access control, consequences strategy, core strategy, security awareness.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
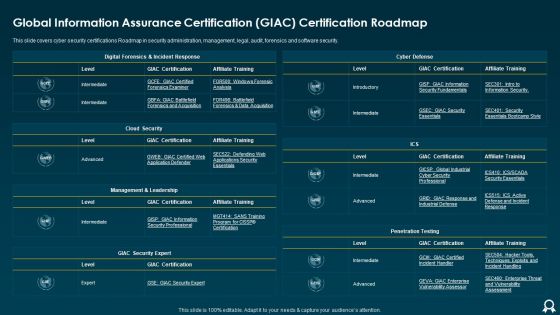
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
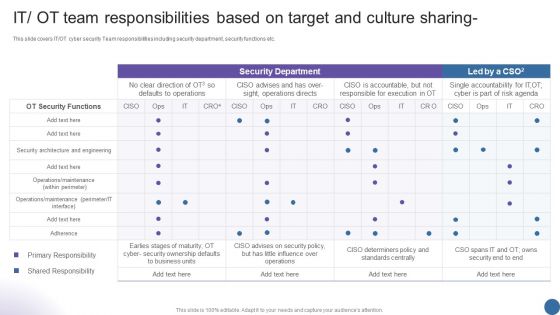
IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF bundle. Topics like Security Department, Team Responsibilities, Target can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
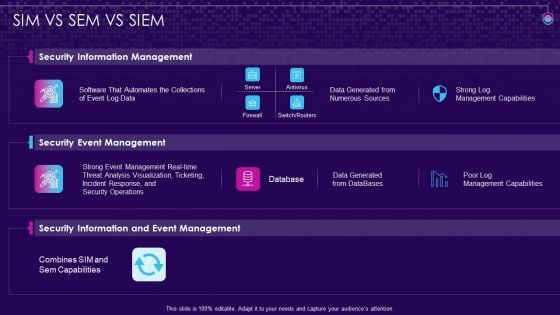
SIM VS SEM VS SIEM SIEM Services Ppt Show Slides PDF
Deliver and pitch your topic in the best possible manner with this sim vs sem vs siem siem services ppt show slides pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Ppt Inspiration Guide PDF
Deliver an awe inspiring pitch with this creative table of contents ppt inspiration guide pdf bundle. Topics like security awareness program, security strategies, budget, communication plan, security awareness, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
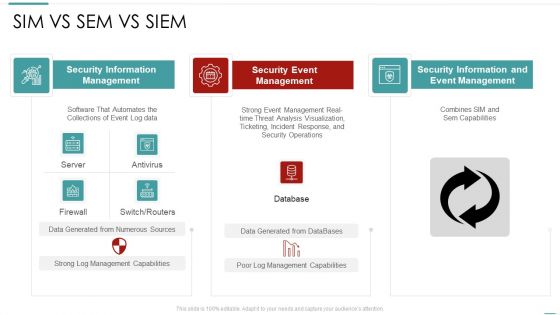
Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Addressing Cost Determination Framework For 5G Ideas PDF
This slide provides details regarding cost determination framework for 5G network including network capacity, network coverage, energy efficient network, etc. Deliver an awe inspiring pitch with this creative Addressing Cost Determination Framework For 5G Ideas PDF bundle. Topics like Network Capacity, Network Flexibility, Network Ownership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
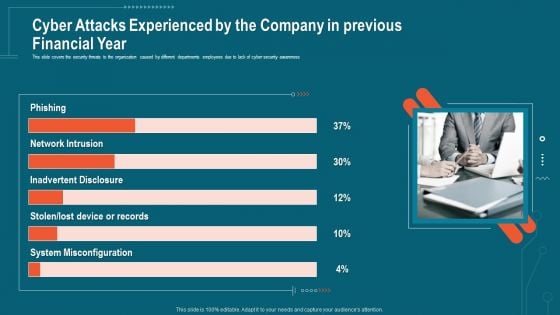
Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
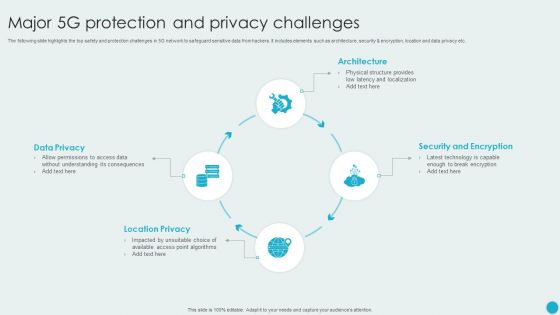
Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
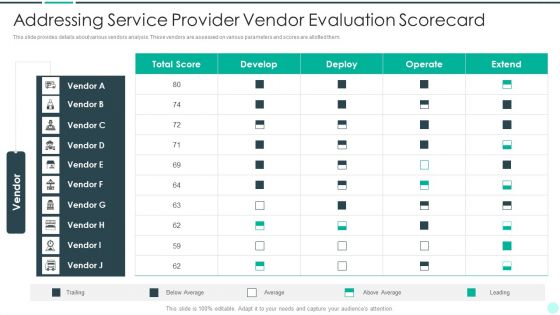
Executing Advance Data Analytics At Workspace Addressing Service Provider Vendor Formats PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing service provider vendor formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf
This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events. Pitch your topic with ease and precision using this Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf. This layout presents information on Outside Venue, Entrances, Interior Areas. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events.
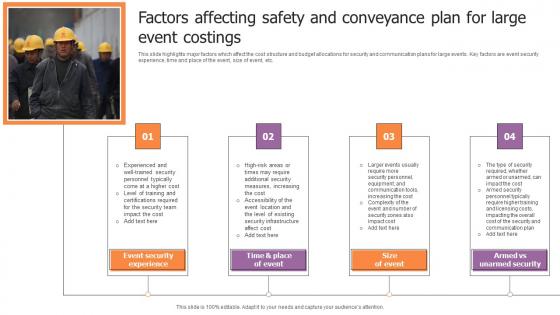
Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf
This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc. Pitch your topic with ease and precision using this Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf. This layout presents information on Event Security Experience, Size Of Event, Armed Vs Unarmed Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc.
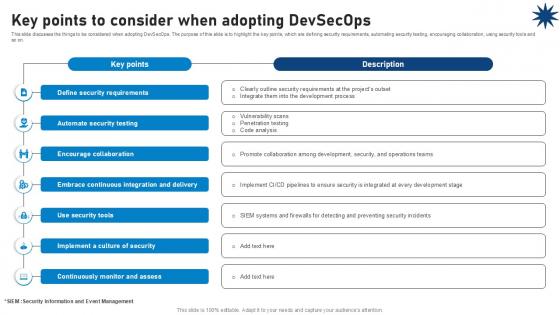
Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample
This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on. Find a pre-designed and impeccable Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on.
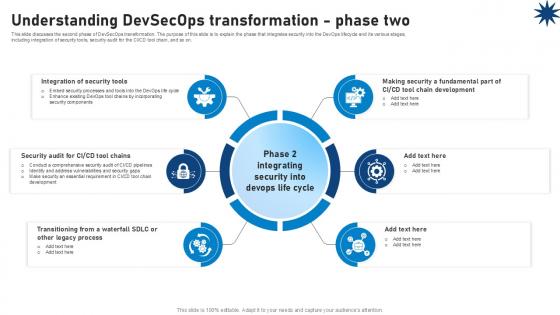
Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint
This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on.
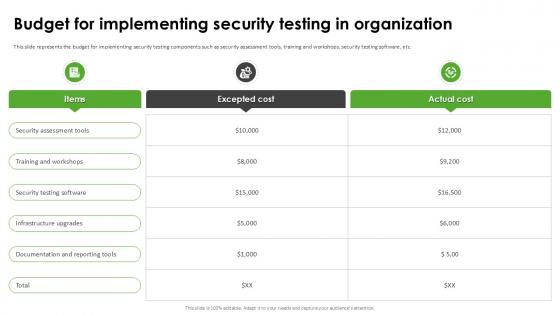
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.

Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint
This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc.
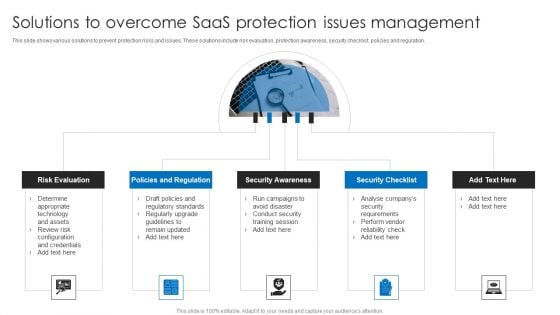
Solutions To Overcome Saas Protection Issues Management Information PDF
This slide shows various solutions to prevent protection risks and issues. These solutions include risk evaluation, protection awareness, security checklist, policies and regulation. Presenting Solutions To Overcome Saas Protection Issues Management Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Policies And Regulation, Security Awareness, Security Checklist, Risk Evaluation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
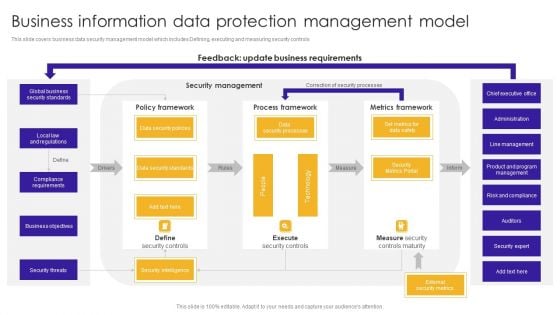
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
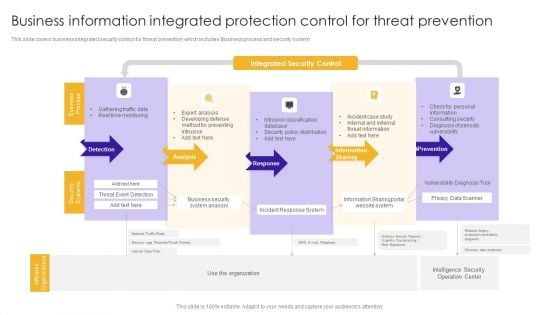
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
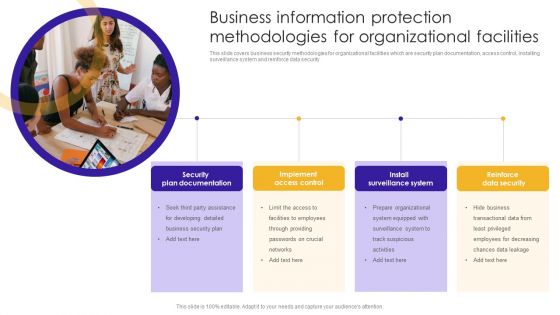
Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
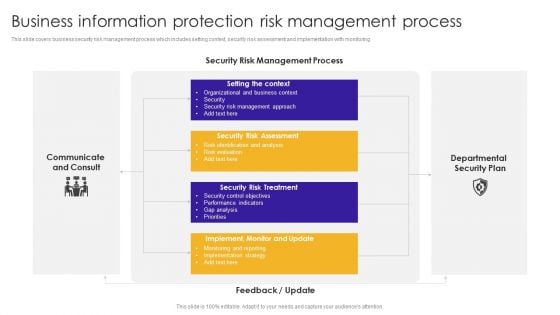
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
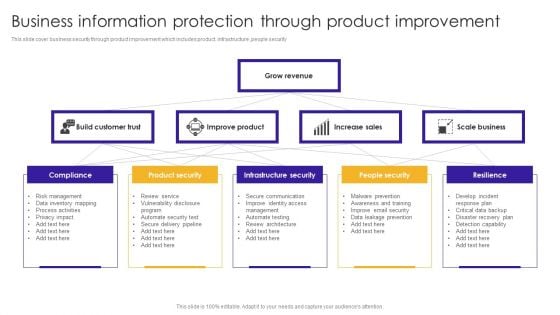
Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
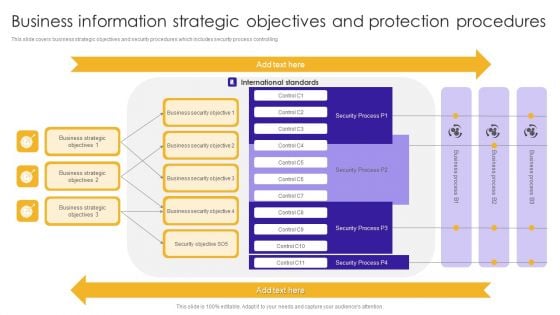
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
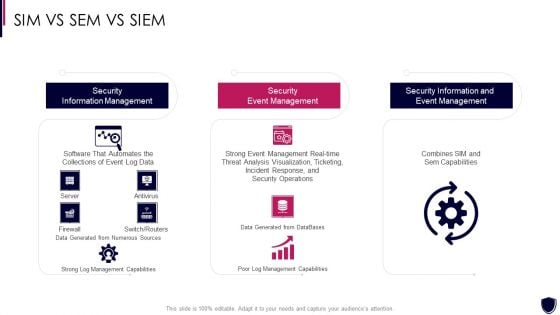
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
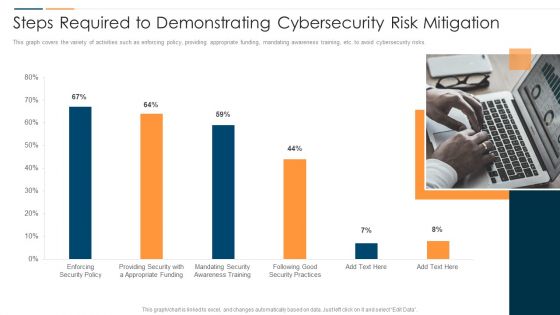
Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
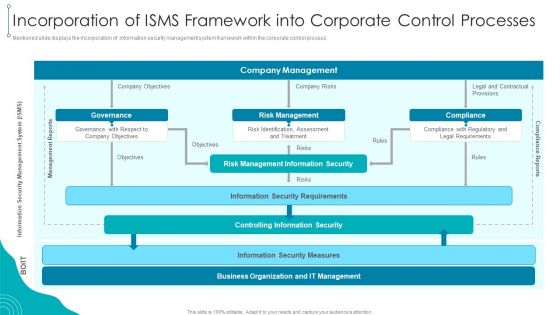
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
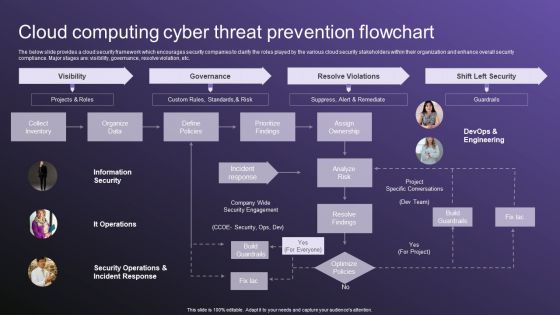
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
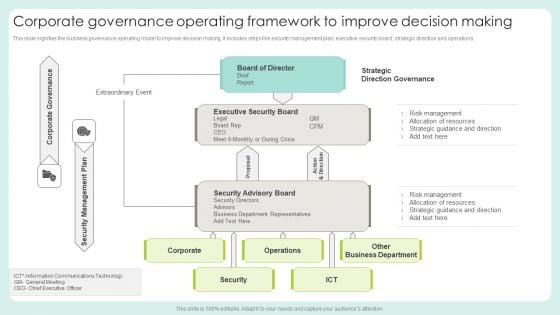
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security
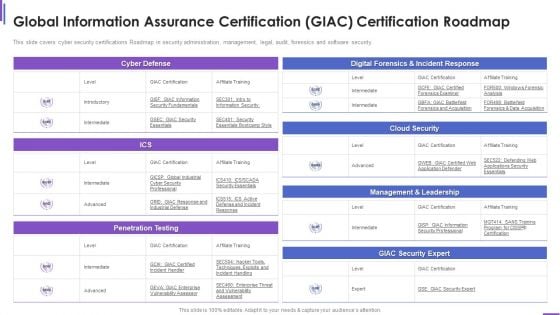
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Roles And Responsibilities Involved In Secops Elements PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure.Deliver an awe inspiring pitch with this creative essential roles and responsibilities involved in secops elements pdf bundle. Topics like security incident responder, security alert investigator, security engineers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
SIEM Sim Vs Sem Vs SIEM Ppt Icon Format Ideas PDF
This is a siem sim vs sem vs siem ppt icon format ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information management, security event management, security information and event management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































