Network Security
Defining Risk Events Based On Impact Size And Likelihood Of Occurrence Ppt Pictures Background PDF
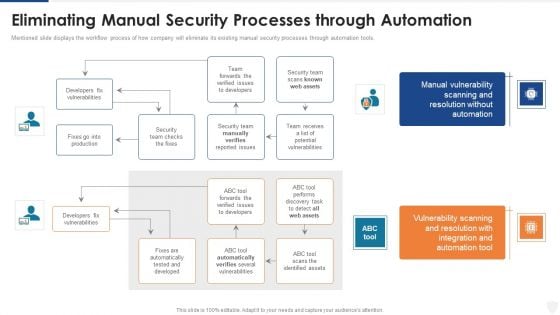
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this eliminating manual security processes through automation ppt styles images pdf. Use them to share invaluable insights on security, team, production, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
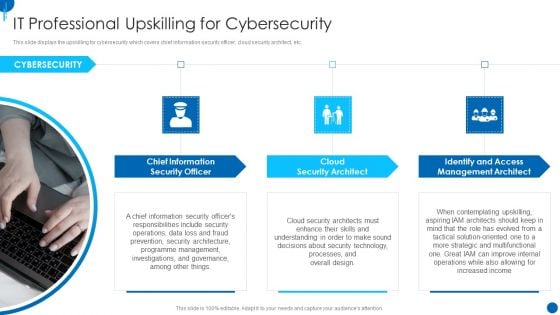
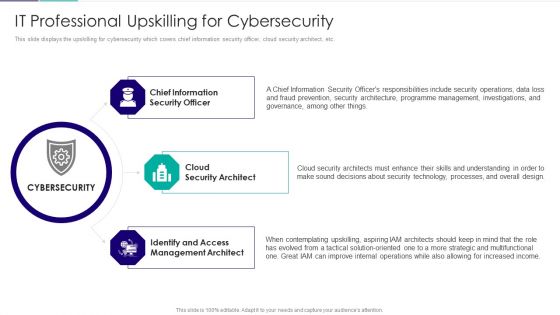
Information Technology Strategy IT Professional Upskilling For Cybersecurity Guidelines PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a information technology strategy it professional upskilling for cybersecurity guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like chief information, security officer, cloud security architect, identify and access management architect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
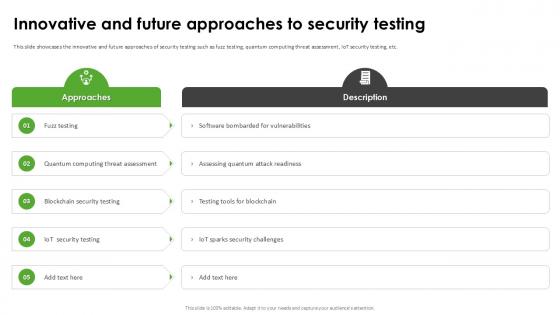
Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide
This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.
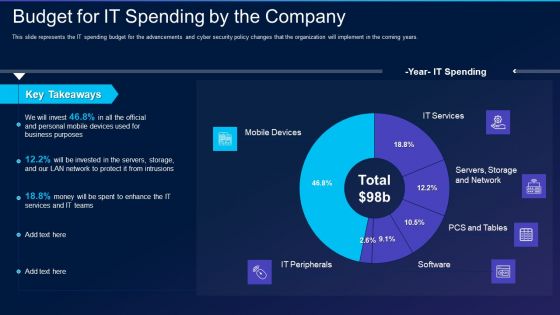
Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ITIL Strategy Service Excellence What Services Do We Offer To Clients Ppt PowerPoint Presentation Pictures Structure PDF
Presenting this set of slides with name itil strategy service excellence what services do we offer to clients ppt powerpoint presentation pictures structure pdf. The topics discussed in these slides are core offerings, server monitoring, network monitoring, backup monitoring, application monitoring, patch management, automated maintenance, performance reporting, endpoint security esm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
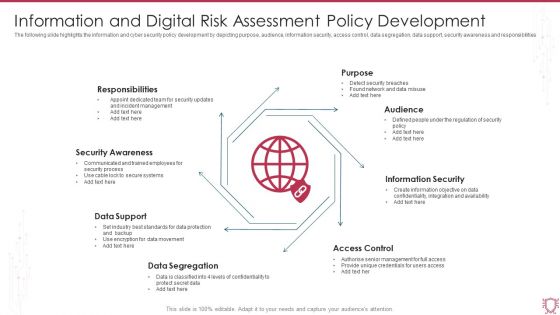
Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effective IT Risk Management Process Roles And Responsibilities For Managing Elements PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a effective it risk management process roles and responsibilities for managing elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, development, security, organizational, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Depositing Presentation Powerpoint Templates
This is a mobile depositing presentation powerpoint templates. This is a four stage process. The stages in this process are cross selling, security services, mobile depositing, credit scoring.
Mobile Depositing Sample Presentations
This is a mobile depositing sample presentations. This is a four stage process. The stages in this process are mobile depositing, credit scoring, security services, cross selling.
Property Management Template Ppt PowerPoint Presentation Pictures Format
This is a property management template ppt powerpoint presentation pictures format. This is a seven stage process. The stages in this process are security deposits, leasing, accounting services.
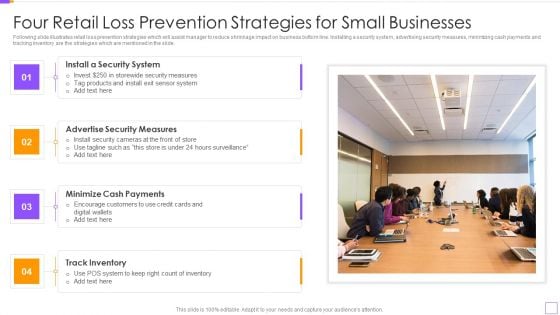
Four Retail Loss Prevention Strategies For Small Businesses Themes PDF
Following slide illustrates retail loss prevention strategies which will assist manager to reduce shrinkage impact on business bottom line. Installing a security system, advertising security measures, minimizing cash payments and tracking inventory are the strategies which are mentioned in the slide. Persuade your audience using this Four Retail Loss Prevention Strategies For Small Businesses Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Install A Security System, Advertise Security Measures, Minimize Cash Payments, Track Inventory. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
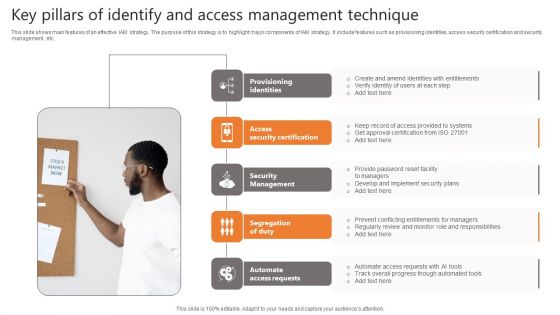
Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide
This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc.

Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF
Presenting Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information System Categorization, Security Control Selection, Security Control Implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Motel Safety Computers Operator Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name motel safety computers operator ppt powerpoint presentation complete deck. The topics discussed in these slides are wireless security, card access, security guard, operator, computers. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Diagram Magnifying Glass With Puzzle Pieces Slide Presentation Template
This business plan power point template has been designed with graphic of lock which is made by puzzles pieces and with one missing puzzle. This PPT contains the concept of security and solution development. Add this PPT in your presentations and display solution and security related topics.

Company Vulnerability Administration Overview Structure PDF
This is a company vulnerability administration overview structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it is a security weakness or flaw of a component in the technology stack of an organization, vulnerabilities may exist on network devices, servers pcs mobile devices applications or any other elements connected to the network, a typical organizations network has many vulnerabilities per device or system therefore even a small organization may have tens of thousands of vulnerabilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
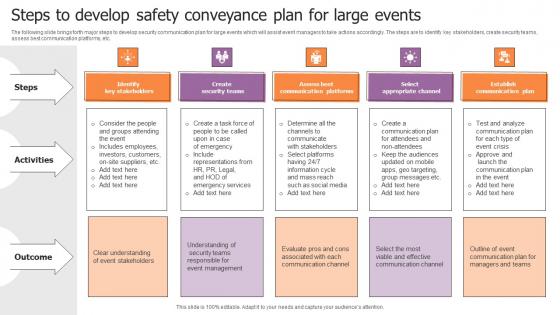
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.
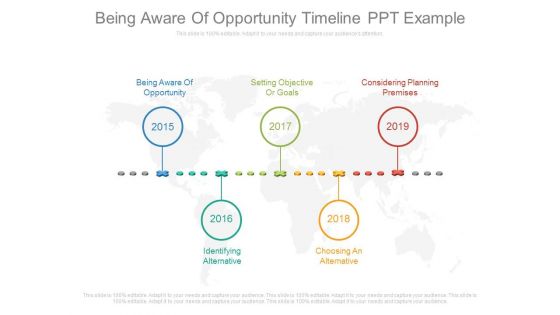
Being Aware Of Opportunity Timeline Ppt Example
This is a being aware of opportunity timeline ppt example. This is a five stage process. The stages in this process are marketing, business, success, time planning.

Viral Marketing Ppt PowerPoint Presentation Model Clipart
This is a viral marketing ppt powerpoint presentation model clipart. This is a one stage process. The stages in this process are business, social, communication, management, planning.
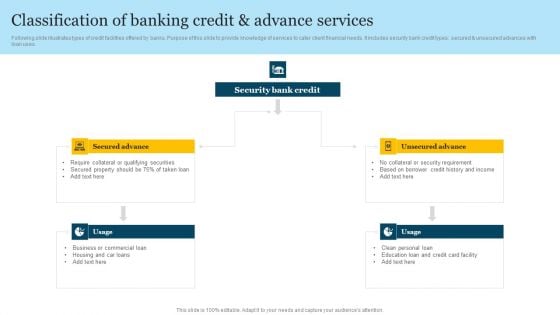
Classification Of Banking Credit And Advance Services Summary PDF
Following slide illustrates types of credit facilities offered by banks. Purpose of this slide to provide knowledge of services to cater client financial needs. It includes security bank credit types secured and unsecured advances with loan uses. Presenting Classification Of Banking Credit And Advance Services Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Bank Credit, Security Requirement, Education Loan This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Naas Integrated Solution IT Comparison Between Service Models Of Naas Portrait PDF
This slide depicts the comparison between different service models of the network as a service, including bandwidth on demand, virtual private network, and mobile network virtualization. The virtual private network is of two types remote access and site to site connection. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Comparison Between Service Models Of Naas Portrait PDF bundle. Topics like Virtual Private Network, Mobile Network Virtualization, Bandwidth On Demand can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.
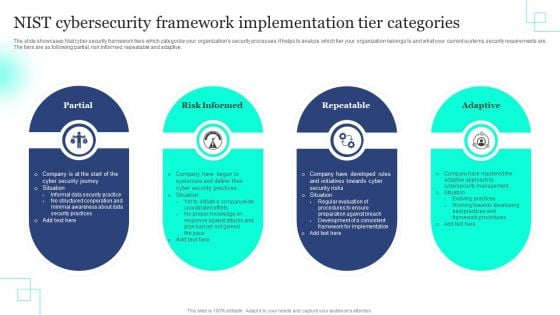
NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents Risk Management For Organization Essential Assets Brochure PDF
Presenting table of contents risk management for organization essential assets brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, natural calamity threats, ensuring physical security, security against workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
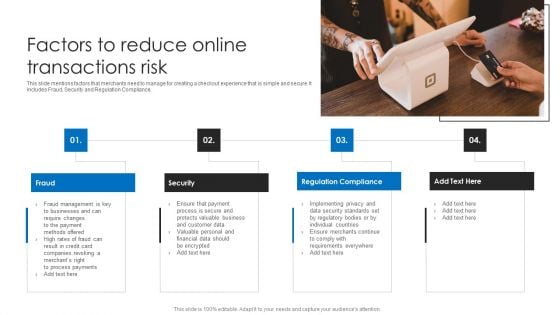
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
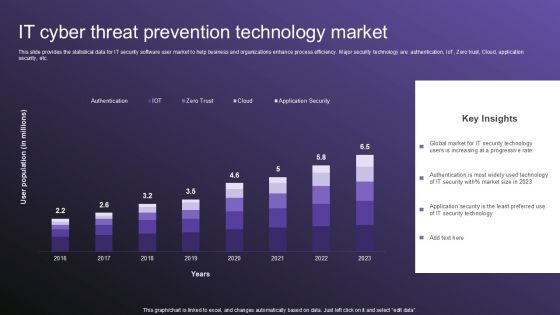
IT Cyber Threat Prevention Technology Market Topics PDF
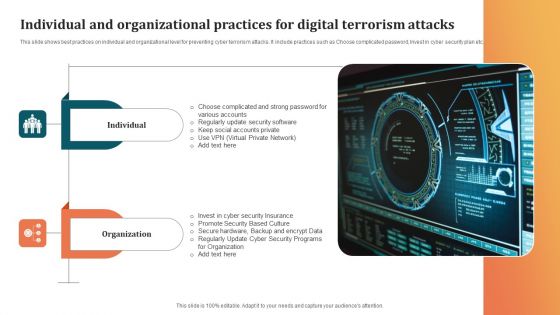
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
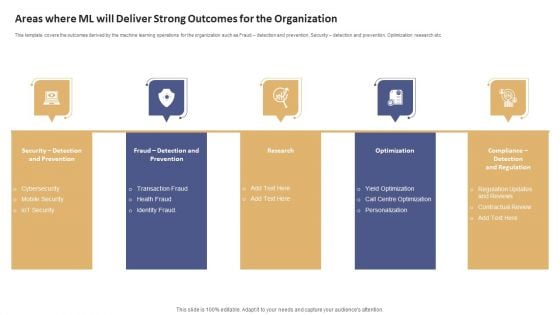
Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
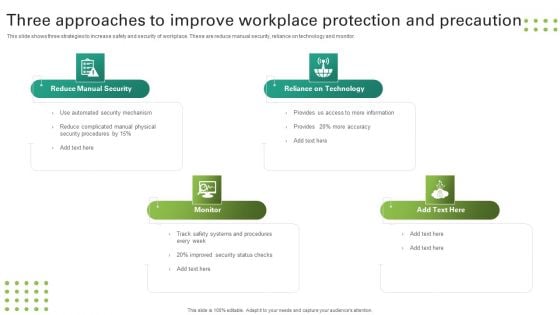
Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
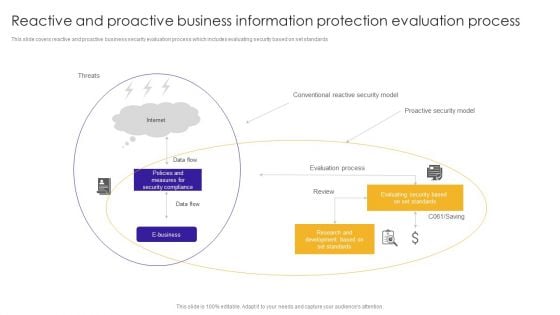
Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
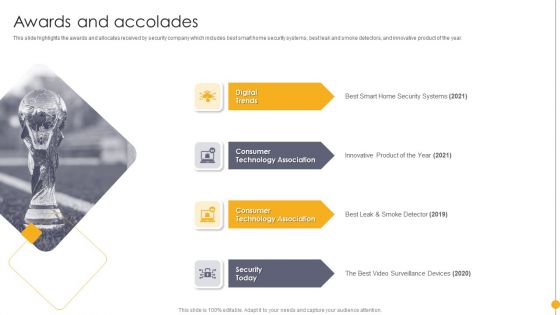
Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends, Consumer, Technology Association, Consumer Technology Association, Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
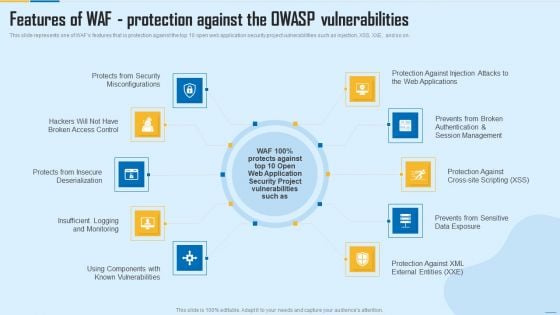
Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
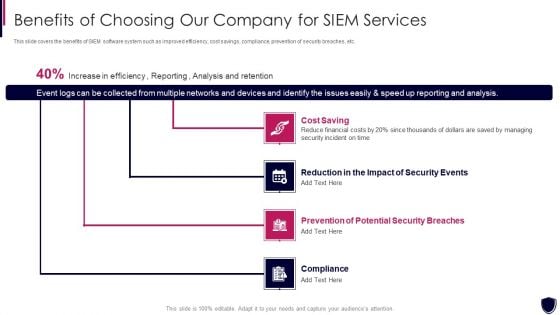
Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
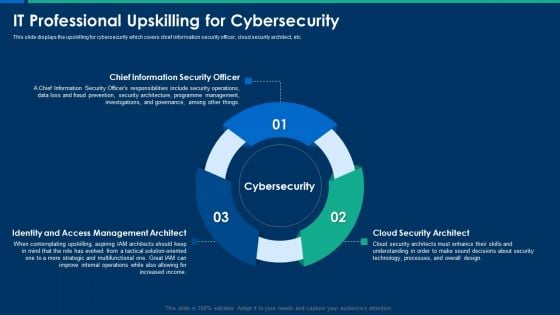
CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Overview Of New IT Policy Framework Pictures PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. This is a data safety initiatives overview of new it policy framework pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it policy framework, it security and usage policies, data policies, it security policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Intelligence Framework For Application Consumption Determining The Suitable Software For Organization Icons PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption determining the suitable software for organization icons pdf. Use them to share invaluable insights on process automation, data security, improve productivity, process automation and data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
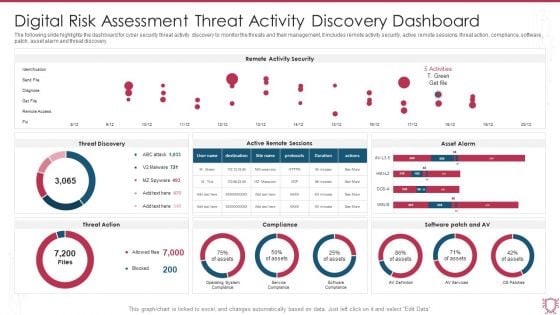
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
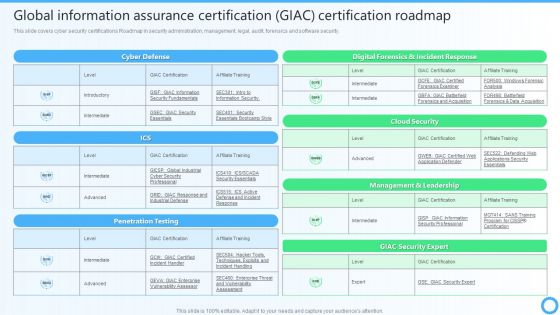
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
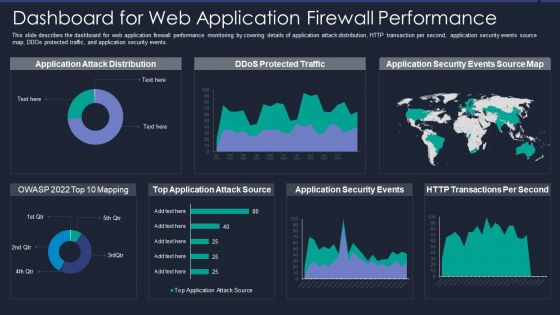
Web App Firewall Services IT Dashboard For Web Application Firewall Performance Microsoft PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver and pitch your topic in the best possible manner with this web app firewall services it dashboard for web application firewall performance microsoft pdf. Use them to share invaluable insights on application, source, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
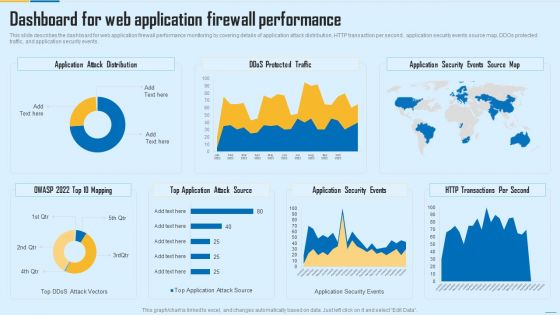
Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver an awe inspiring pitch with this creative Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF bundle. Topics like Application Attack Distribution, Application Security Events, Transactions Per Second can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
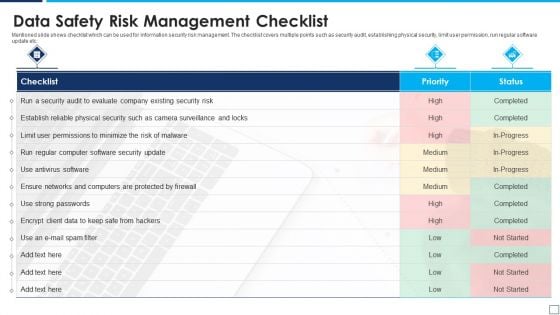
Data Safety Risk Management Checklist Information PDF
Mentioned slide shows checklist which can be used for information security risk management. The checklist covers multiple points such as security audit, establishing physical security, limit user permission, run regular software update etc. Presenting data safety risk management checklist information pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including data safety risk management checklist. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
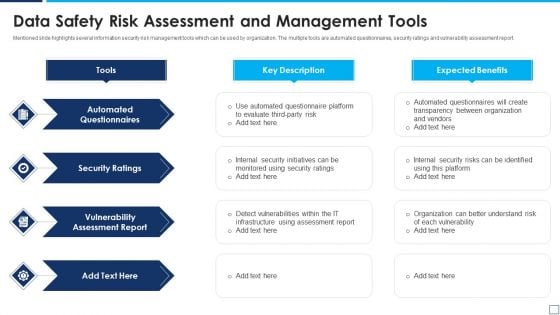
Data Safety Risk Assessment And Management Tools Demonstration PDF
Mentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Presenting data safety risk assessment and management tools demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including automated questionnaires, security ratings, vulnerability assessment report. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Home Security, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

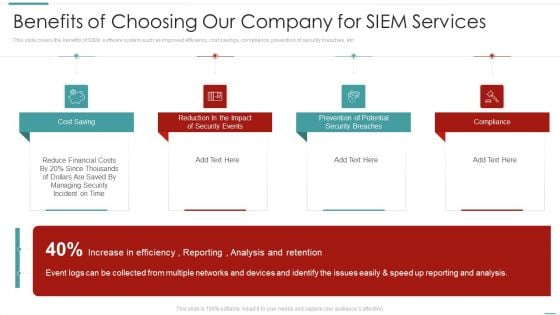
SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
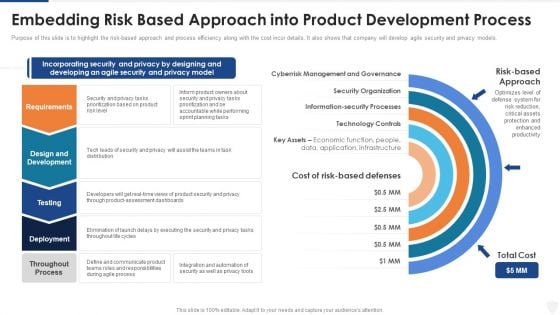
Embedding Risk Based Approach Into Product Development Process Ppt Model Files PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Presenting embedding risk based approach into product development process ppt model files pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like technology controls, information security processes, security organization, economic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
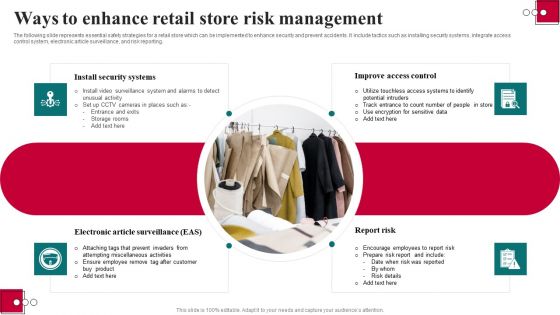
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Need For Ethical Hacking Ppt Gallery Portfolio PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a need for ethical hacking ppt gallery portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like quality control, development, security, system, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
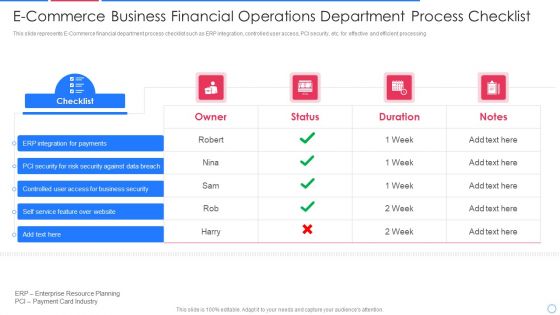
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


 Continue with Email
Continue with Email

 Home
Home


































