Network Security

ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF
This slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Pitch your topic with ease and precision using this ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF. This layout presents information on SOC Team Roles, Responsibilities, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
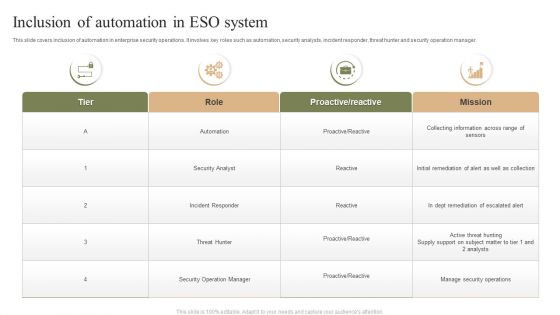
Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
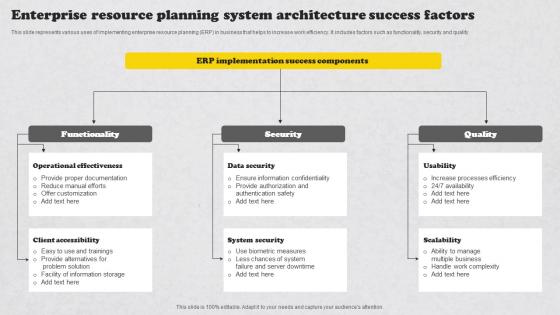
Enterprise Resource Planning System Architecture Success Factors Background Pdf
This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality Showcasing this set of slides titled Enterprise Resource Planning System Architecture Success Factors Background Pdf. The topics addressed in these templates are Quality, Security, Functionality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality
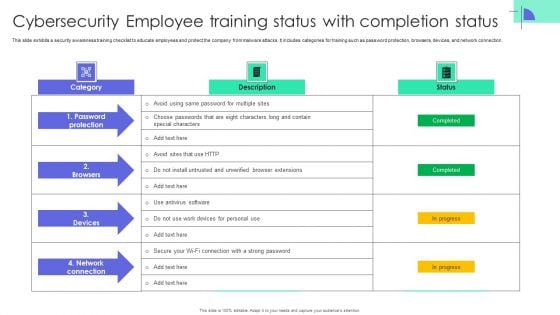
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
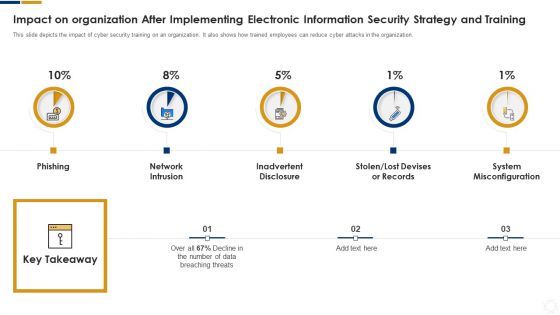
Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between ZTNA And Software Defined Perimeter Diagrams PDF
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Make sure to capture your audiences attention in your business displays with our gratis customizable Difference Between ZTNA And Software Defined Perimeter Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
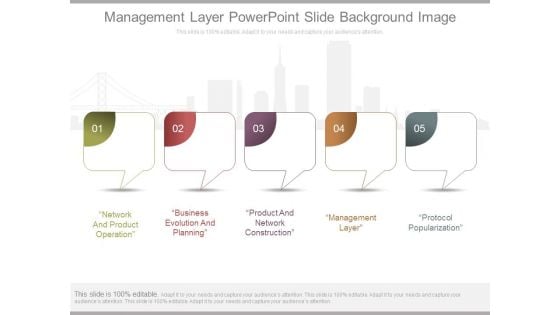
Management Layer Powerpoint Slide Background Image
This is a management layer powerpoint slide background image. This is a five stage process. The stages in this process are network and product operation, business evolution and planning, product and network construction, management layer, protocol popularization.
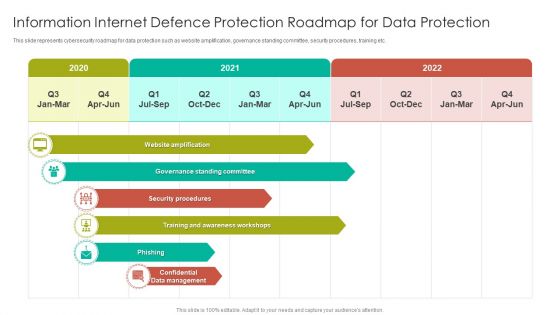
Information Internet Defence Protection Roadmap For Data Protection Topics PDF
This slide represents cybersecurity roadmap for data protection such as website amplification, governance standing committee, security procedures, training etc. Showcasing this set of slides titled Information Internet Defence Protection Roadmap For Data Protection Topics PDF. The topics addressed in these templates are Governance Standing, Security Procedures, Awareness Workshops. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
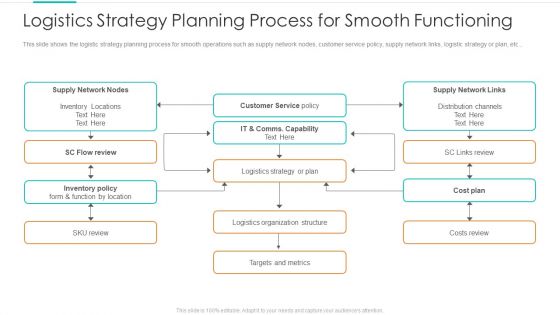
Logistics Strategy Planning Process For Smooth Functioning Mockup PDF
This slide shows the logistic strategy planning process for smooth operations such as supply network nodes, customer service policy, supply network links, logistic strategy or plan, etc. Deliver an awe-inspiring pitch with this creative logistics strategy planning process for smooth functioning mockup pdf bundle. Topics like supply network nodes, customer service, supply network links can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Market Overview Fitness Industry Digital Marketing Strategy Customer Acquisition Strategy Template PDF
This is our customer acquisition strategy via AdWords which includes search network adds and display network ads from which we can get 23 plus clicks and 2K impressions. Deliver an awe-inspiring pitch with this creative market overview fitness industry digital marketing strategy customer acquisition strategy template pdf bundle. Topics like potential reach search, search network, display network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
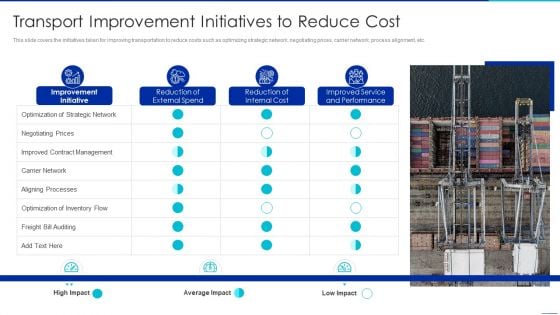
Optimizing Logistics Management Process Transport Improvement Initiatives To Reduce Cost Background PDF
This slide covers the initiatives taken for improving transportation to reduce costs such as optimizing strategic network, negotiating prices, carrier network, process alignment, etc. Deliver an awe inspiring pitch with this creative optimizing logistics management process transport improvement initiatives to reduce cost background pdf bundle. Topics like carrier network, improved contract management, negotiating prices, optimization of strategic network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
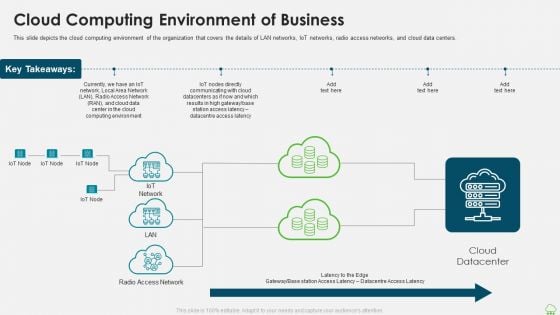
Distributed Computing IT Cloud Computing Environment Of Business Inspiration PDF
This slide depicts the cloud computing environment of the organization that covers the details of LAN networks, IoT networks, radio access networks, and cloud data centers. Deliver an awe inspiring pitch with this creative distributed computing it cloud computing environment of business inspiration pdf bundle. Topics like communicating, computing environment, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
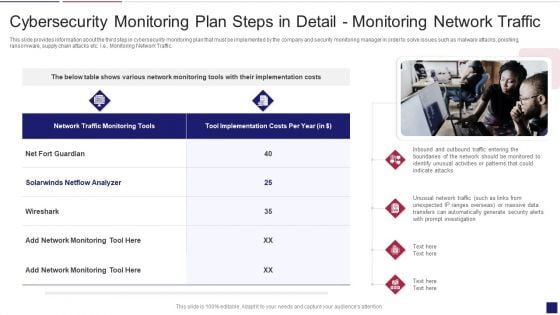
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
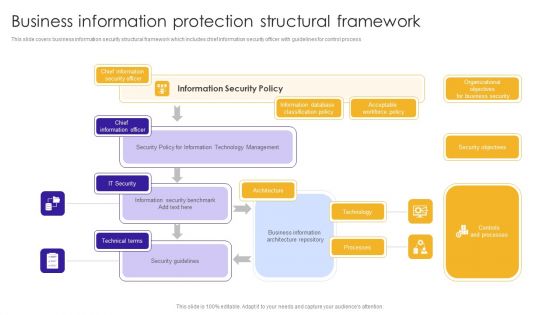
Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Our Services Ppt PowerPoint Presentation Model Grid
This is a our services ppt powerpoint presentation model grid. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics , security maintenance.
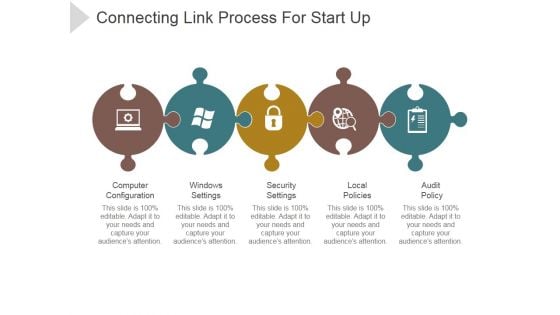
Connecting Link Process For Start Up Ppt PowerPoint Presentation Summary
This is a connecting link process for start up ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.
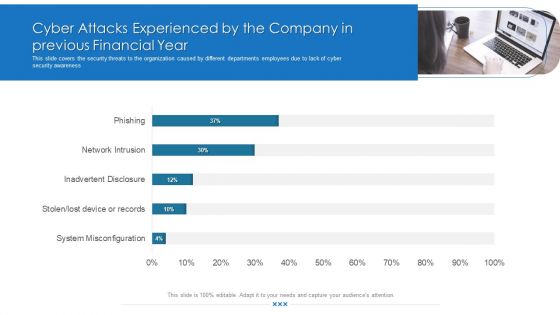
Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
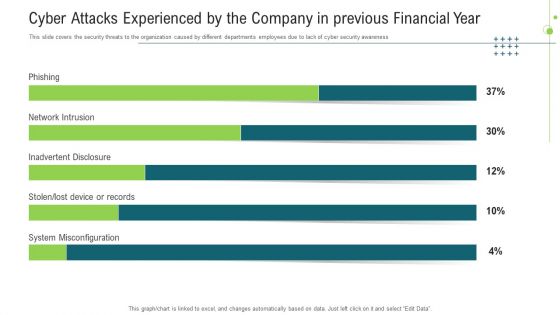
Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
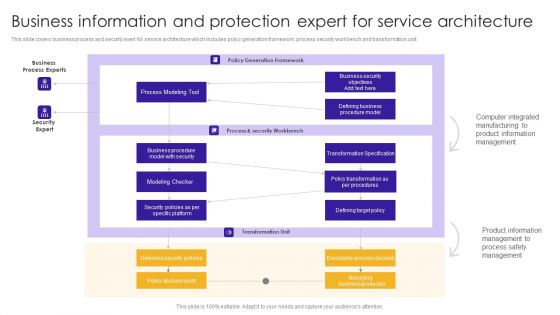
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Management Template Presentation Background Images
This is a cyber management template presentation background images. This is a six stage process. The stages in this process are risk review, policy, audit, cyber security life cycle, implementation, administration.
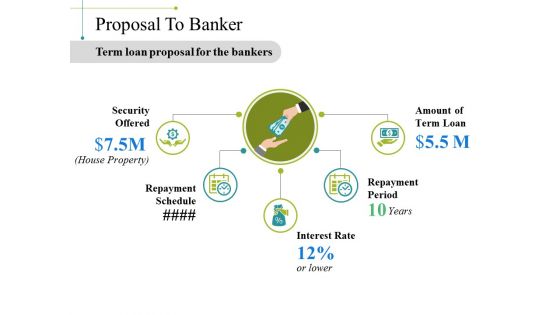
Proposal To Banker Ppt PowerPoint Presentation Outline Grid
This is a proposal to banker ppt powerpoint presentation outline grid. This is a five stage process. The stages in this process are security offered, repayment schedule, interest rate, repayment period, amount of term loan.
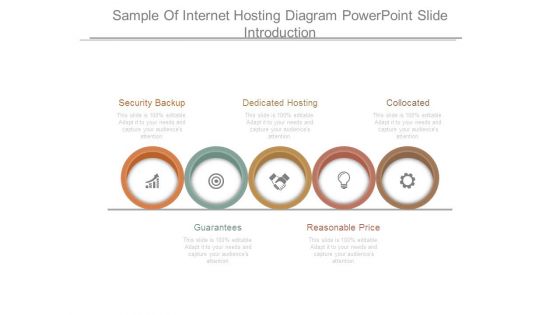
Sample Of Internet Hosting Diagram Powerpoint Slide Introduction
This is a sample of internet hosting diagram powerpoint slide introduction. This is a five stage process. The stages in this process are security backup, dedicated hosting, collocated, guarantees, reasonable price.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Business Framework Entry Barrier 1 PowerPoint Presentation
This business framework PPT diagram has been designed with graphic of traffic cones and barrier. This PPT diagram contains the concept of security and construction. Use this PPT diagram for your road safety and traffic rules related presentations.
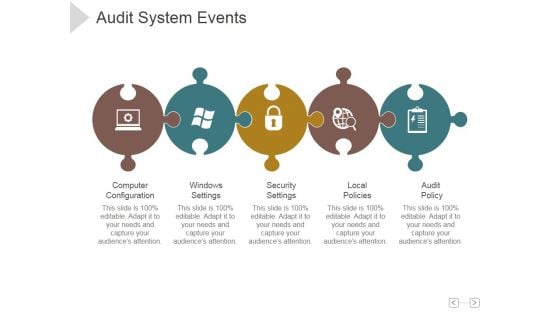
Audit System Events Ppt PowerPoint Presentation Model
This is a audit system events ppt powerpoint presentation model. This is a five stage process. The stages in this process are computer configuration, windows settings , security settings , local policies, audit policy.
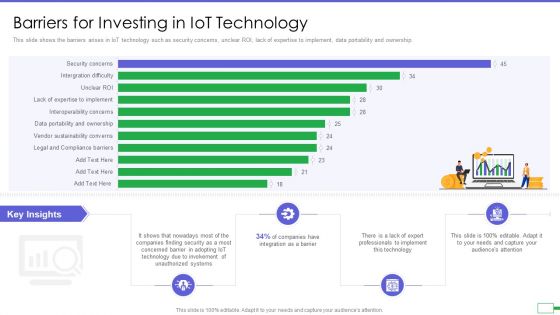
Iot And Digital Twin To Reduce Costs Post Covid Barriers For Investing In Iot Technology Sample PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this iot and digital twin to reduce costs post covid barriers for investing in iot technology sample pdf. Use them to share invaluable insights on security, technology, integration, implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration.

Stock Photo Key With Red Heart Shaped Lock PowerPoint Slide
This image slide has been designed with key and red heart shaped lock. Use this image to define concepts like lock, security heart protection. Make amazing presentations with this image.
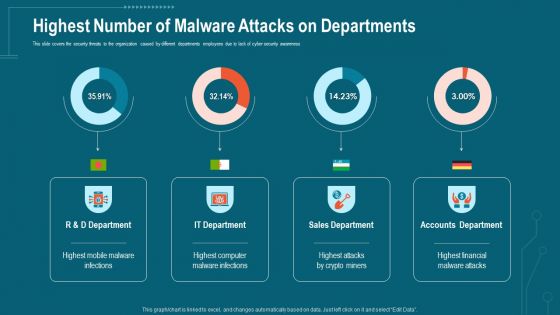
Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Needs Wants And Demands Ppt PowerPoint Presentation Samples
This is a customer needs wants and demands ppt powerpoint presentation samples. This is a five stage process. The stages in this process are need, wants, demands, safety needs security protection, physiological needs, hunger thirst.

Customer Needs Wants And Demands Ppt PowerPoint Presentation Portfolio Layout
This is a customer needs wants and demands ppt powerpoint presentation portfolio layout. This is a five stage process. The stages in this process are need, wants, demands, safety needs security protection.
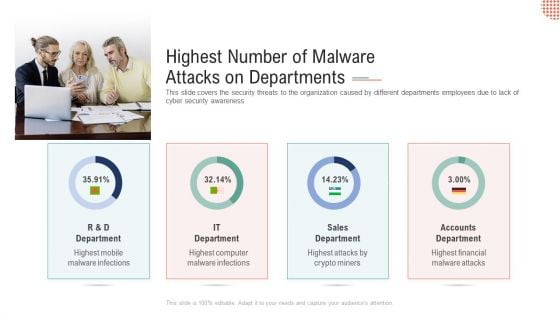
Highest Number Of Malware Attacks On Departments Ppt Inspiration Deck PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver an awe-inspiring pitch with this creative highest number of malware attacks on departments ppt inspiration deck pdf. bundle. Topics like r ans d department, sales department, accounts department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
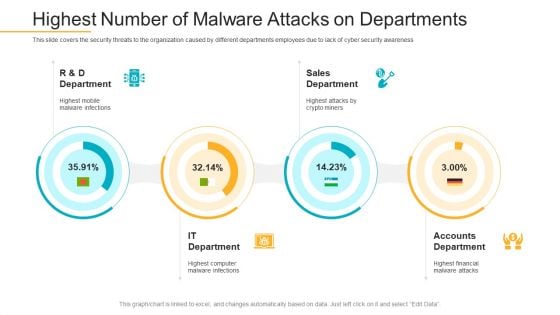
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
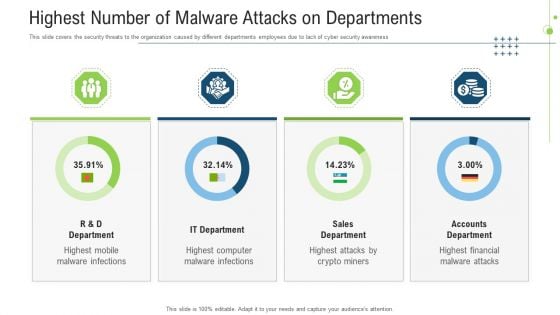
Highest Number Of Malware Attacks On Departments Ppt Gallery Ideas PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative highest number of malware attacks on departments ppt gallery ideas pdf bundle. Topics like accounts department, sales department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
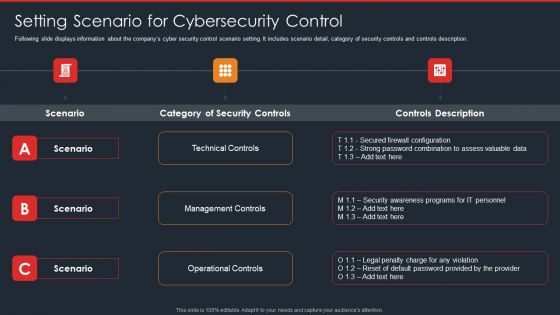
Data Safety Initiatives Setting Scenario For Cybersecurity Control Inspiration PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative data safety initiatives setting scenario for cybersecurity control inspiration pdf bundle. Topics like scenario, technical controls, management controls, operational controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
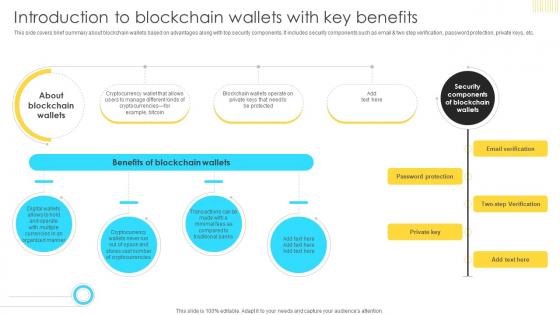
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc
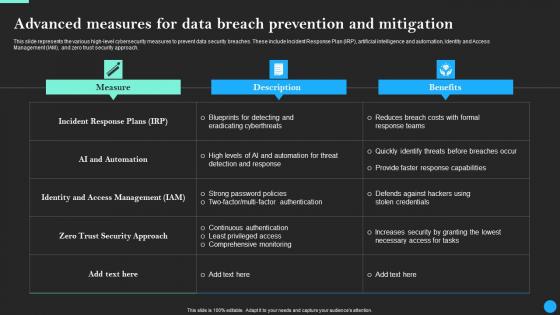
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
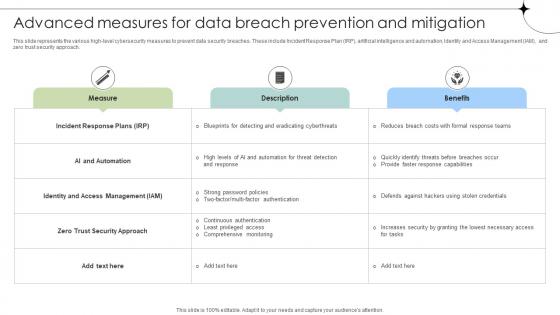
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
Evolving BI Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Demonstration PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver an awe inspiring pitch with this creative evolving bi infrastructure tracking intelligence infrastructure activities dashboard demonstration pdf bundle. Topics like application delivery, business analytics, internet of things, it operations, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Context For Firewall Migration Proposal
This slide highlights the project context for the firewall migration proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as advanced security features, security ecosystem components, etc.Unleash your creativity with our Project Context For Firewall Migration Proposal single-slide PPT template. Whether you are a seasoned presenter or a newbie, our editable and visually-stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience. This slide highlights the project context for the firewall migration proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as advanced security features, security ecosystem components, etc.

Stock Photo Dollar Bundles Safe With Lock And Chain Image Graphics For PowerPoint Slide
This image slide displays dollar bundle locked with chain. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.

Stock Photo Blue Colored Pen Drive With Combination Lock PowerPoint Slide
Graphic of blue colored pen drive and combination lock has been used to design this power point template. This PPT contains the concept of data security and data technology. Use this PPT for your business and marketing related presentations.
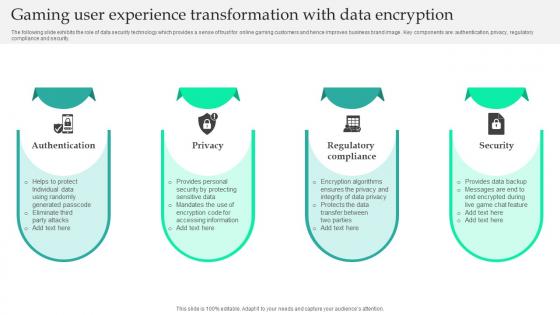
Gaming User Experience Transformation With Data Encryption Portrait Pdf
The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security. Pitch your topic with ease and precision using this Gaming User Experience Transformation With Data Encryption Portrait Pdf. This layout presents information on Authentication, Privacy, Regulatory Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security.

Our Services Template 2 Ppt PowerPoint Presentation Styles Introduction
This is a our services template 2 ppt powerpoint presentation styles introduction. This is a four stage process. The stages in this process are business, digital advertising, digital care package, security maintenance, marketing and analytics .

Stock Photo 3d Key And Keyhole For Safety Image Graphics For PowerPoint Slide
This image slide has been designed with graphics of golden key with key hole. This professional slide contains golden key to displays security and safety concepts. This unique image provides impressive background for your presentations.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
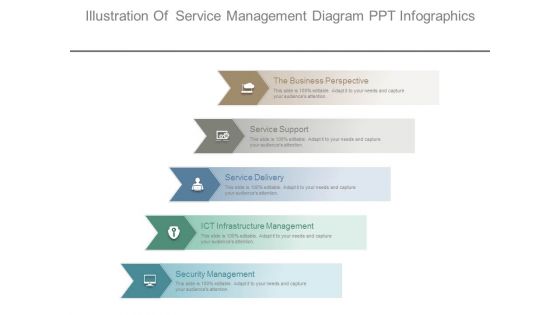
Illustration Of Service Management Diagram Ppt Infographics
This is a illustration of service management diagram ppt infographics. This is a five stage process. The stages in this process are the business perspective, service support, service delivery, ict infrastructure management, security management.

Our Services Ppt PowerPoint Presentation Gallery Model
This is a our services ppt powerpoint presentation gallery model. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.

Our Services Ppt PowerPoint Presentation Professional Ideas
This is a our services ppt powerpoint presentation professional ideas. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.
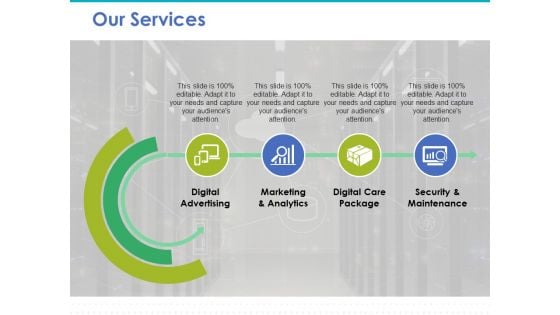
Our Services Ppt PowerPoint Presentation Inspiration Brochure
This is a our services ppt powerpoint presentation inspiration brochure. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.
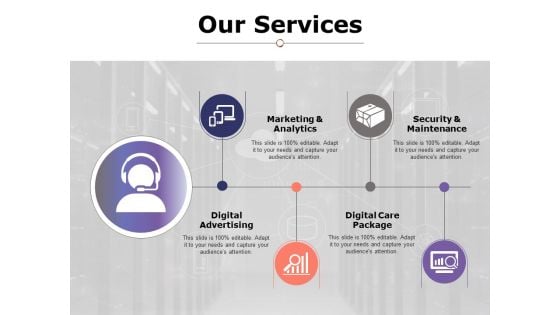
Our Services Ppt PowerPoint Presentation Layouts Shapes
This is a our services ppt powerpoint presentation pictures display. This is a four stage process. The stages in this process are marketing and analytics, security and maintenance, digital advertising, digital care package.
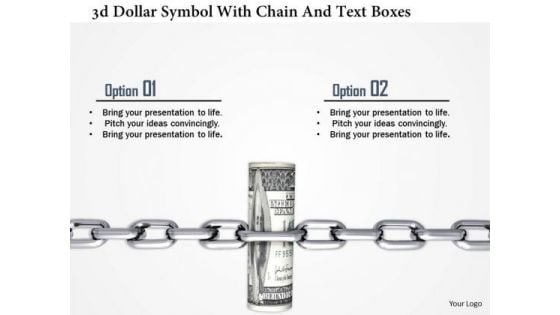
Stock Photo 3d Dollar Symbol With Chain And Text Boxes PowerPoint Slide
This image slide has been designed with graphic of dollar notes locked with chain. This slide depicts concept of financial security and investment. Use this editable slide for your wealth and finance related topics.

Our Services Template 2 Ppt PowerPoint Presentation Show Design Inspiration
This is a our services template 2 ppt powerpoint presentation show design inspiration. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.
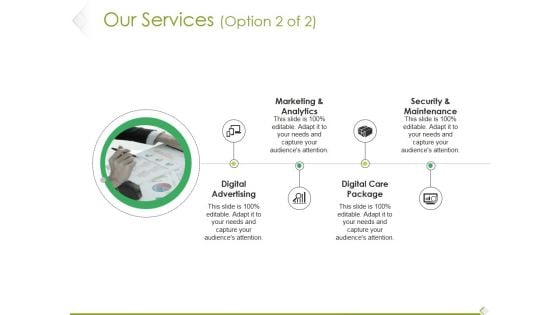
Our Services Template 2 Ppt PowerPoint Presentation Model Background Images
This is a our services template 2 ppt powerpoint presentation model background images. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics, security and maintenance.

Our Services Template 1 Ppt PowerPoint Presentation Model Picture
This is a our services template 1 ppt powerpoint presentation model picture. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.


 Continue with Email
Continue with Email

 Home
Home


































