Network Security
Integrating Naas Service Model To Enhance Comparison Between Service Models Introduction PDF
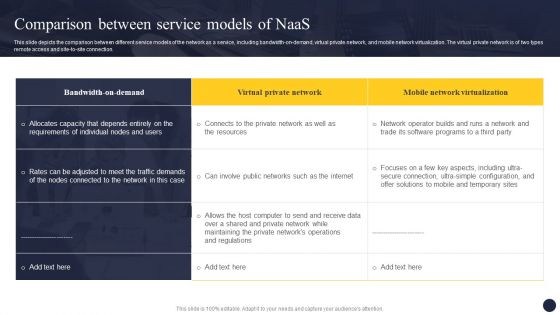
This slide depicts the comparison between different service models of the network as a service, including bandwidth-on-demand, virtual private network, and mobile network virtualization. The virtual private network is of two types remote access and site-to-site connection. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Integrating Naas Service Model To Enhance Comparison Between Service Models Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Integrating Naas Service Model Comparison Between Service Models Of Naas Ppt Styles Graphic Images PDF
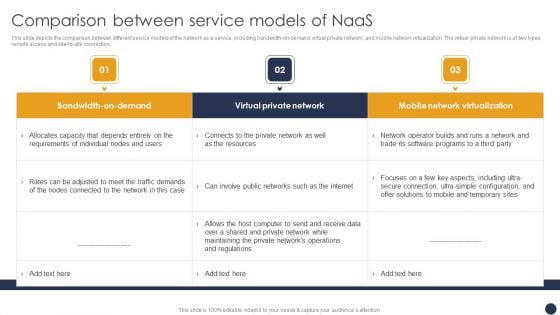
This slide depicts the comparison between different service models of the network as a service, including bandwidth-on-demand, virtual private network, and mobile network virtualization. The virtual private network is of two types remote access and site-to-site connection. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Integrating Naas Service Model Comparison Between Service Models Of Naas Ppt Styles Graphic Images PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Logistics Strategy Planning Process For Smooth Functioning Introduction PDF
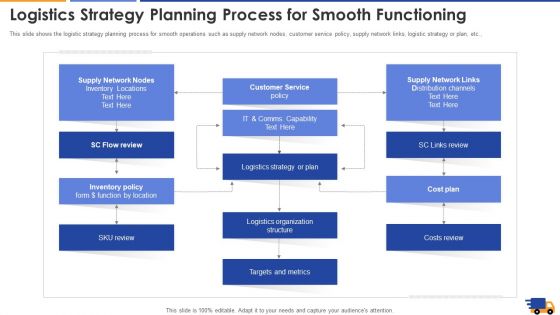
This slide shows the logistic strategy planning process for smooth operations such as supply network nodes, customer service policy, supply network links, logistic strategy or plan, etc. Deliver and pitch your topic in the best possible manner with this logistics strategy planning process for smooth functioning introduction pdf. Use them to share invaluable insights on strategy, plan, supply network, inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Salary And Job Details Rules PDF
This slide covers salary details CCIE certified salary and job details along with certification courses, exam status and scope of certification etc. Deliver an awe inspiring pitch with this creative IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Salary And Job Details Rules PDF bundle. Topics like Network Associate, Networking Technologies, Networking Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Years Plan With Key Activities Ppt PowerPoint Presentation Infographics Topics PDF
Presenting this set of slides with name five years plan with key activities ppt powerpoint presentation infographics topics pdf. The topics discussed in these slides are key activities, network service enabler defined and standardized, availability of products supporting the network service enabler, products available from multiple interoperable sources supporting the network service enabler. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF
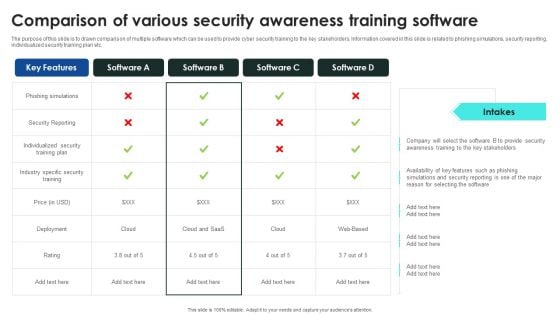
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Components Of Information And Communication Technology Telecommunications Formats Pdf
This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi. There are so many reasons you need a Components Of Information And Communication Technology Telecommunications Formats Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi.
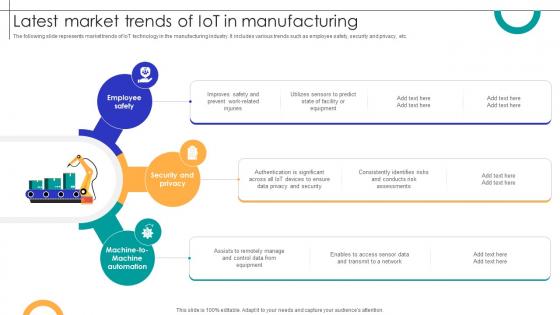
Latest Market Trends Of IOT In Manufacturing Streamlining Production Ppt Powerpoint
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Find a pre-designed and impeccable Latest Market Trends Of IOT In Manufacturing Streamlining Production Ppt Powerpoint The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc.

Incident Response Techniques Deployement Five Phases Of Cybersecurity Incident Management Formats PDF

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
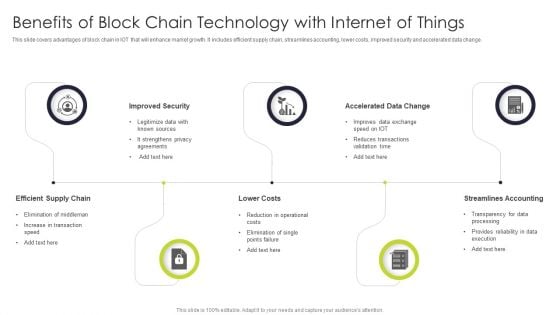
Benefits Of Block Chain Technology With Internet Of Things Introduction PDF
This slide covers advantages of block chain in IOT that will enhance market growth. It includes efficient supply chain, streamlines accounting, lower costs, improved security and accelerated data change.Persuade your audience using this Benefits Of Block Chain Technology With Internet Of Things Introduction PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Streamlines Accounting, Improved Security, Accelerated Data Change Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
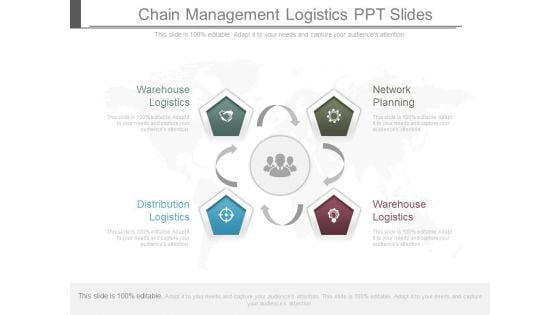
Chain Management Logistics Ppt Slides
This is a chain management logistics ppt slides. This is a four stage process. The stages in this process are network planning, warehouse logistics, distribution logistics, warehouse logistics.
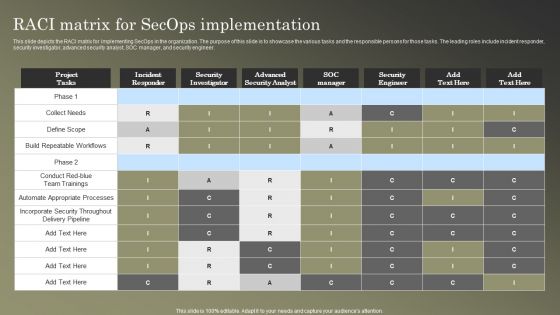
Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF
This slide depicts the RACI matrix for implementing SecOps in the organization. The purpose of this slide is to showcase the various tasks and the responsible persons for those tasks. The leading roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Present like a pro with Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
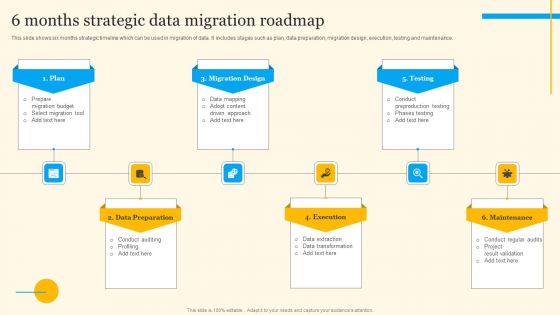
6 Months Strategic Data Migration Roadmap Background PDF
This slide shows timeline which can be used in network migration. It includes various stages such as network selection, network agreement, tech integration, etc. Persuade your audience using this 6 Months Strategic Data Migration Roadmap Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Select Network, Affiliate Communication Plan, Aggressive Affiliate Migration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
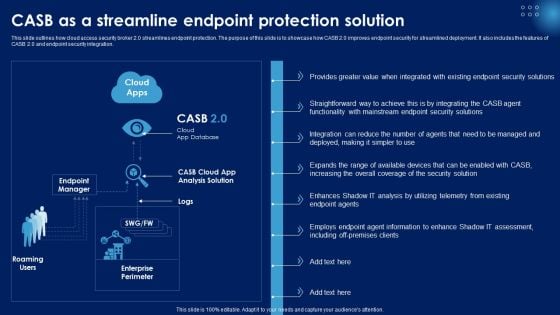
CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Take your projects to the next level with our ultimate collection of CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF
This slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Explore a selection of the finest Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
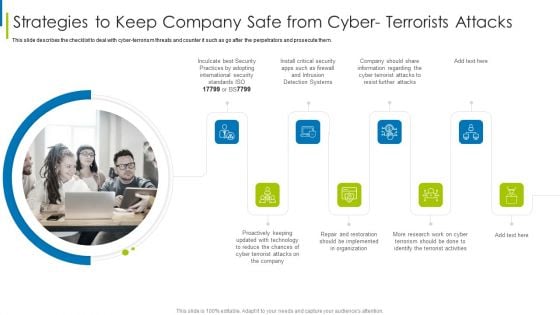
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
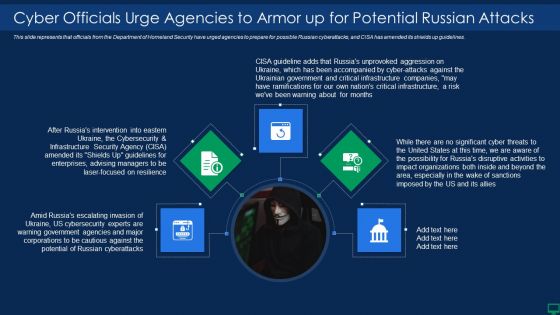
Russian Cyber Attacks On Ukraine IT Cyber Officials Urge Background PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting russian cyber attacks on ukraine it cyber officials urge background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, organizations, risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
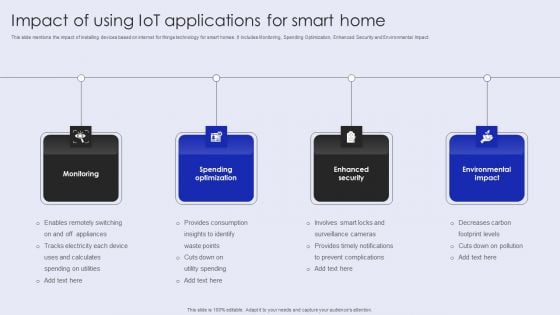
Impact Of Using Iot Applications For Smart Home Template PDF
This slide mentions the impact of installing devices based on internet for things technology for smart homes. It includes Monitoring, Spending Optimization, Enhanced Security and Environmental Impact. Persuade your audience using this Impact Of Using Iot Applications For Smart Home Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Spending Optimization, Enhanced Security, Environmental Impact. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
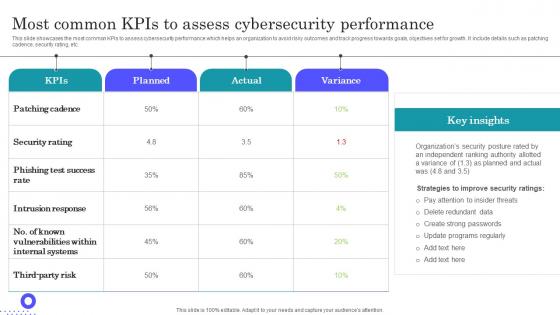
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.
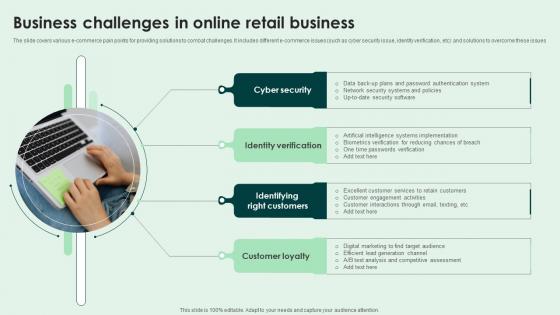
Business Challenges In Online Retail Business Introduction Pdf
The slide covers various e-commerce pain points for providing solutions to combat challenges. It includes different e-commerce issues such as cyber security issue, identity verification, etc and solutions to overcome these issues. Showcasing this set of slides titled Business Challenges In Online Retail Business Introduction Pdf. The topics addressed in these templates are Cyber Security, Identity Verification, Customer Loyalty. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide covers various e-commerce pain points for providing solutions to combat challenges. It includes different e-commerce issues such as cyber security issue, identity verification, etc and solutions to overcome these issues.
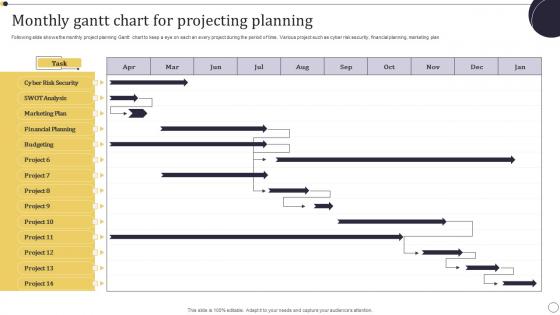
Monthly Gantt Chart For Projecting Planning Information Pdf
Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan Showcasing this set of slides titled Monthly Gantt Chart For Projecting Planning Information Pdf. The topics addressed in these templates are Marketing Plan, Financial Planning, Cyber Risk Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan
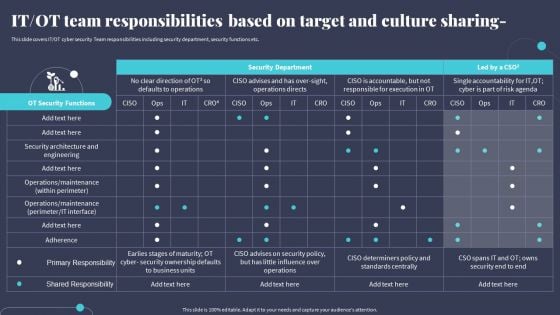
IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF.

Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF
The following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Slidegeeks is here to make your presentations a breeze with Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
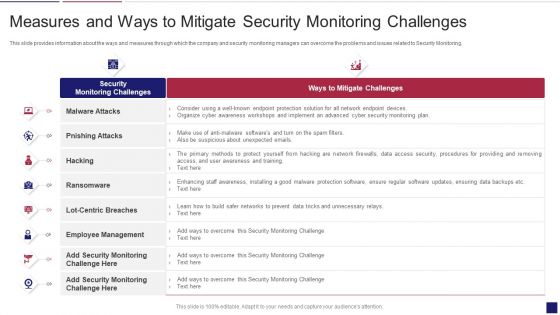
Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
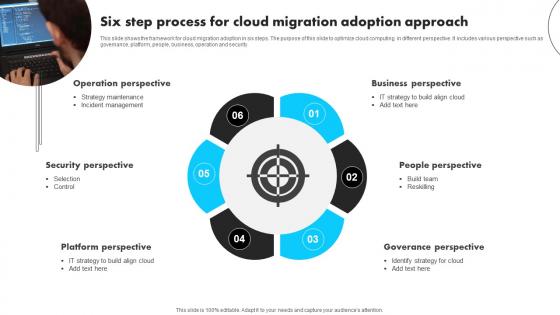
Six Step Process For Cloud Migration Adoption Approach Information Pdf
This slide shows the framework for cloud migration adoption in six steps. The purpose of this slide to optimize cloud computing in different perspective. It includes various perspective such as governance, platform, people, business, operation and security. Pitch your topic with ease and precision using this Six Step Process For Cloud Migration Adoption Approach Information Pdf This layout presents information on Operation Perspective, Security Perspective, People Perspective It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows the framework for cloud migration adoption in six steps. The purpose of this slide to optimize cloud computing in different perspective. It includes various perspective such as governance, platform, people, business, operation and security.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
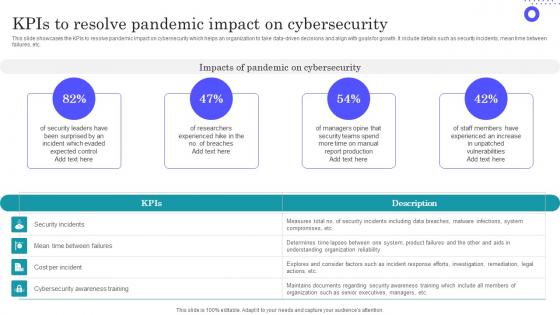
KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf
Pitch your topic with ease and precision using this KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf This layout presents information on Understanding Organization, Security Incidents, Malware Infections It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the KPIs to resolve pandemic impact on cybersecurity which helps an organization to take data driven decisions and align with goals for growth. It include details such as security incidents, mean time between failures, etc.
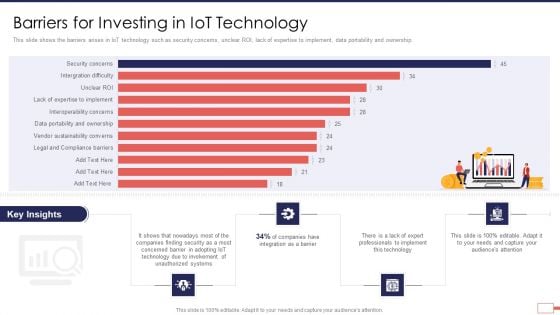
Iot Digital Twin Technology Post Covid Expenditure Management Barriers For Investing In Iot Technology Download PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this iot digital twin technology post covid expenditure management barriers for investing in iot technology download pdf Use them to share invaluable insights on security, companies, involvement, unauthorized, technology, barrier and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
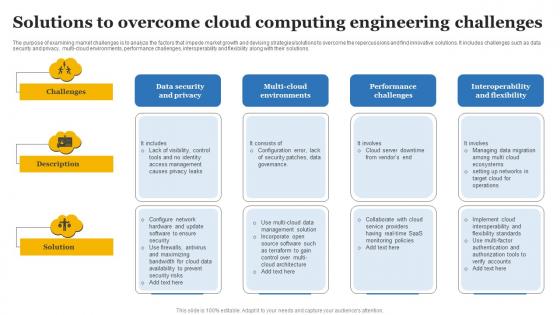
Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf
The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions. Pitch your topic with ease and precision using this Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf This layout presents information on Data Security And Privacy, Multi Cloud Environments It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions.
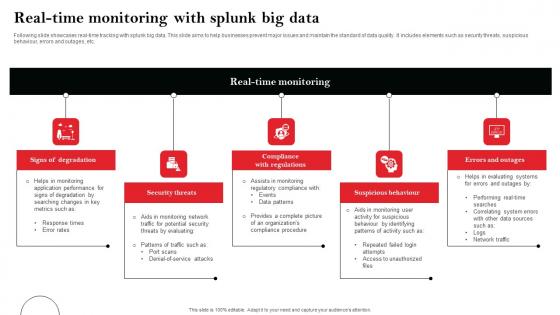
Real Time Monitoring With Splunk Big Data Diagrams Pdf
Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc. Pitch your topic with ease and precision using this Real Time Monitoring With Splunk Big Data Diagrams Pdf This layout presents information on Signs Of Degradation, Security Threats, Errors And Outages It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc.
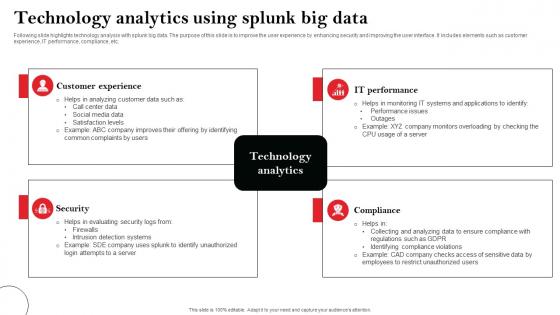
Technology Analytics Using Splunk Big Data Microsoft Pdf
Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc. Pitch your topic with ease and precision using this Technology Analytics Using Splunk Big Data Microsoft Pdf This layout presents information on Customer Experience, Security, Compliance It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc.
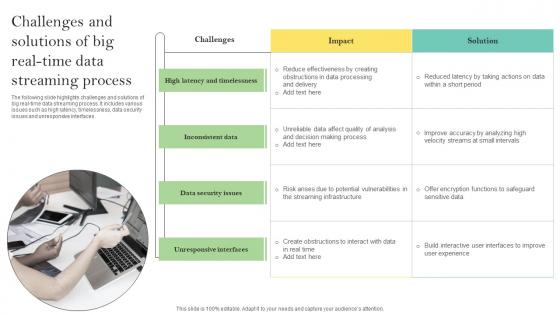
Challenges And Solutions Of Big Real Time Data Streaming Process Ppt File Styles Pdf
The following slide highlights challenges and solutions of big real-time data streaming process. It includes various issues such as high latency, timelessness, data security issues and unresponsive interfaces. Pitch your topic with ease and precision using this Challenges And Solutions Of Big Real Time Data Streaming Process Ppt File Styles Pdf. This layout presents information on High Latency, Timelessness, Data Security Issues. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights challenges and solutions of big real-time data streaming process. It includes various issues such as high latency, timelessness, data security issues and unresponsive interfaces.

Types Of Software Testing Techniques Evaluation Ppt Layouts Diagrams Pdf
This slide outlines the various analysis approaches used in software testing. It includes key types such as static testing, dynamic testing, code coverage, test case analysis, defect analysis, performance testing, security testing, test automation and exploratory testing. Showcasing this set of slides titled Types Of Software Testing Techniques Evaluation Ppt Layouts Diagrams Pdf. The topics addressed in these templates are Test Case Analysis, Defect Analysis, Performance Testing, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines the various analysis approaches used in software testing. It includes key types such as static testing,dynamic testing,code coverage,test case analysis,defect analysis,performance testing,security testing,test automation and exploratory testing.
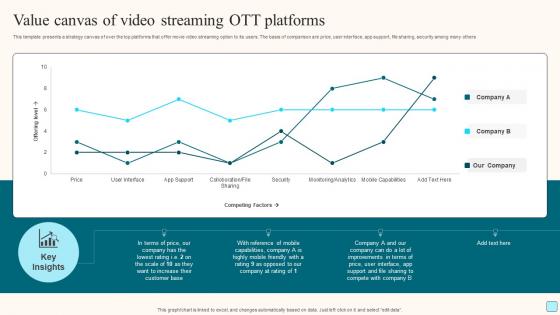
Value Canvas Of Video Streaming Ott Platforms Professional Pdf
This template presents a strategy canvas of over the top platforms that offer movie video streaming option to its users. The basis of comparison are price, user interface, app support, file sharing, security among many others. Pitch your topic with ease and precision using this Value Canvas Of Video Streaming Ott Platforms Professional Pdf. This layout presents information on Value Canvas, Video Streaming, App Support, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This template presents a strategy canvas of over the top platforms that offer movie video streaming option to its users. The basis of comparison are price, user interface, app support, file sharing, security among many others.
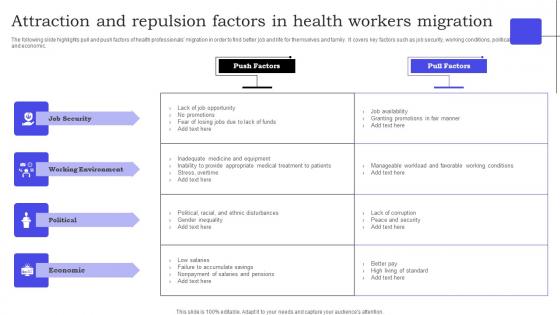
Attraction And Repulsion Factors In Health Workers Migration Information Pdf
The following slide highlights pull and push factors of health professionals migration in order to find better job and life for themselves and family. It covers key factors such as job security, working conditions, political and economic. Showcasing this set of slides titled Attraction And Repulsion Factors In Health Workers Migration Information Pdf. The topics addressed in these templates are Push Factors, Pull Factors, Job Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights pull and push factors of health professionals migration in order to find better job and life for themselves and family. It covers key factors such as job security, working conditions, political and economic.

ITIL Authorization Management Key Performance Indicators Infographics Pdf
This slide showcase KPI indicators which helps in identifying areas of improvement and align all parties involved in access management. It include KPIs such as unauthorized access setting, request access number, revoked instances and deviation in defined security policies. Showcasing this set of slides titled ITIL Authorization Management Key Performance Indicators Infographics Pdf The topics addressed in these templates are Unit Of Measures, Defined Security, Access Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase KPI indicators which helps in identifying areas of improvement and align all parties involved in access management. It include KPIs such as unauthorized access setting, request access number, revoked instances and deviation in defined security policies.

Key Benefits Of Non FHA Home Loan Themes Pdf
The following slide enlists major benefits of conventional loans with transparency, flexibility in regulations and variety specifics to appeal customers. It covers faster underwriting, optional escrow accounts, security and flexibility. Pitch your topic with ease and precision using this Key Benefits Of Non FHA Home Loan Themes Pdf. This layout presents information on Escrow Accounts, Security, Flexibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide enlists major benefits of conventional loans with transparency, flexibility in regulations and variety specifics to appeal customers. It covers faster underwriting, optional escrow accounts, security and flexibility.

Operational Challeneges Of Outsourced Call Center Sample Pdf
The following slide highlights lack of knowledge, lack of control, hidden costs, security concern and language barrier to show challenges of offshore call center outsourcing to show challenges of offshore call center. It helps organizations to identify and mitigate potential challenges. Showcasing this set of slides titled Operational Challeneges Of Outsourced Call Center Sample Pdf. The topics addressed in these templates are Lack Of Company Knowledge, Lack Of Control, Security Concerns, Language Barrier. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights lack of knowledge, lack of control, hidden costs, security concern and language barrier to show challenges of offshore call center outsourcing to show challenges of offshore call center. It helps organizations to identify and mitigate potential challenges.

Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf
This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc. Showcasing this set of slides titled Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf. The topics addressed in these templates are Readability Checks, Performance Checks, Security Checks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc.
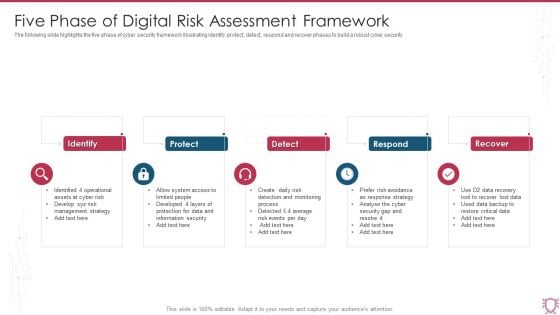
Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF
The following slide highlights the five phase of cyber security framework illustrating identify, protect, detect, respond and recover phases to build a robust cyber security. Persuade your audience using this Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Protect, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
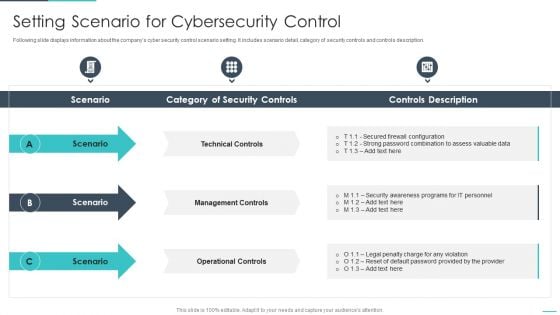
Handling Cyber Threats Digital Era Setting Scenario For Cybersecurity Control Ppt Infographics Brochure PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting handling cyber threats digital era setting scenario for cybersecurity control ppt infographics brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

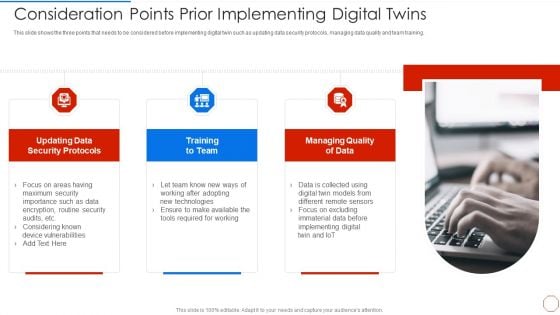
Iot Digital Twin Technology Post Covid Expenditure Management Consideration Points Prior Implementing Digital Twins Rules PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. Presenting iot digital twin technology post covid expenditure management consideration points prior implementing digital twins rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, protocols, data, training, managing, quality . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Minimizing Operational Cost Through Iot Virtual Twins Implementation Consideration Points Prior Clipart PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. Presenting minimizing operational cost through iot virtual twins implementation consideration points prior clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like required, technologies, implementing, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF
The following slide showcases various courses associated with cyber security training to aware workforce with latest security threats. It includes elements such as course name, features, cost, duration etc. Presenting Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Introduction To Cybersecurity, Cyber Online, IT And Cybersecurity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
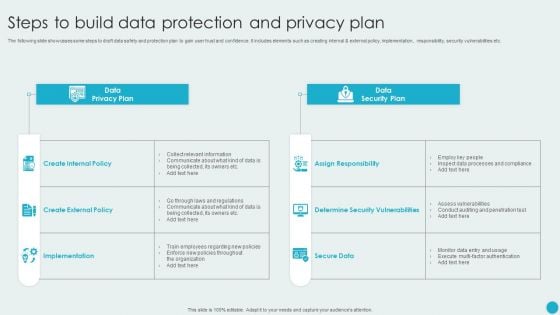
Steps To Build Data Protection And Privacy Plan Diagrams PDF
The following slide showcases some steps to draft data safety and protection plan to gain user trust and confidence. It includes elements such as creating internal and external policy, implementation, responsibility, security vulnerabilities etc. Showcasing this set of slides titled Steps To Build Data Protection And Privacy Plan Diagrams PDF. The topics addressed in these templates are Data Privacy Plan, Data Security Plan, Implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
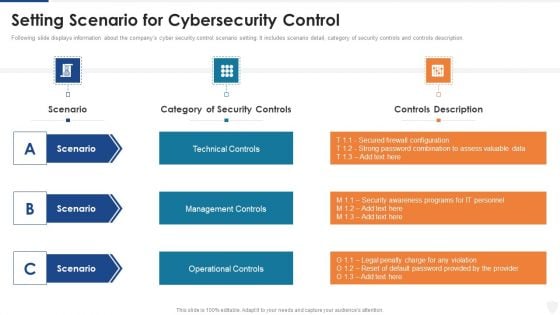
Setting Scenario For Cybersecurity Control Ppt Pictures Graphics Tutorials PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting setting scenario for cybersecurity control ppt pictures graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management controls, technical controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot And Digital Twin To Reduce Costs Post Covid Consideration Points Prior Implementing Digital Twins Brochure PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. Presenting iot and digital twin to reduce costs post covid consideration points prior implementing digital twins brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like data security protocols, training to team, managing quality of data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
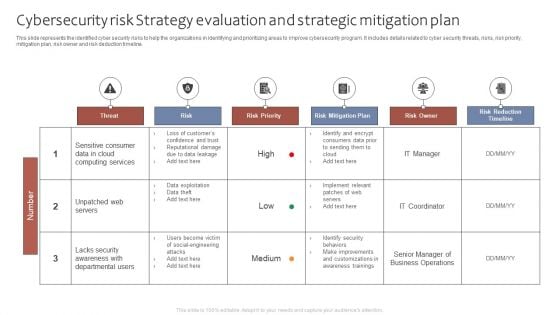
Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF
This slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Showcasing this set of slides titled Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF. The topics addressed in these templates are Threat, Risk, Risk Priority, Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Scorecard To Check Cybersecurity And Digital Risk Preparedness Ppt Layouts Brochure PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this scorecard to check cybersecurity and digital risk preparedness ppt layouts brochure pdf. Use them to share invaluable insights on organization, management, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
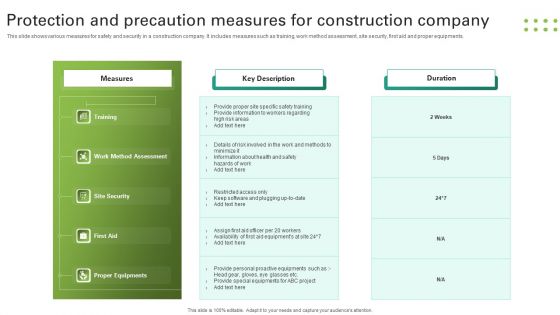
Protection And Precaution Measures For Construction Company Portrait PDF
This slide shows various measures for safety and security in a construction company. It includes measures such as training, work method assessment, site security, first aid and proper equipments. Pitch your topic with ease and precision using this Protection And Precaution Measures For Construction Company Portrait PDF. This layout presents information on Measures, Key Description, Duration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Retail Businesses Internal Strategy With Icons Ppt Ideas Slide Download PDF
This slide covers retail operational processes and its work flow. It includes following problems such as Security related, maintenance and safety related, merchandise related and HR process. Presenting retail businesses internal strategy with icons ppt ideas slide download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security related problems, maintenance and safety, merchandise related problems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
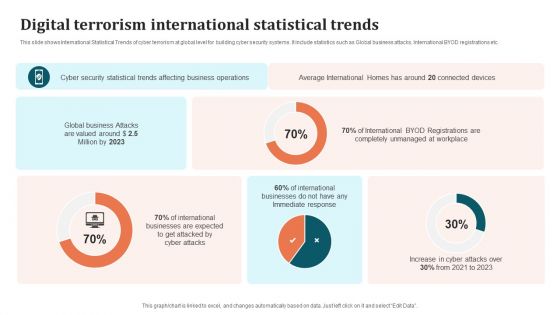
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Safety Awareness Program Services Platform Ppt Show Information PDF
This slide covers platform for providing security awareness training services to clients. It includes elements such as platforms comprising of security awareness training content, phishing case studies, quarterly cyber awareness training, human based testing, monthly incident reporting, etc. Showcasing this set of slides titled Cyber Safety Awareness Program Services Platform Ppt Show Information PDF. The topics addressed in these templates are Platforms, Development, Core Self Managed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
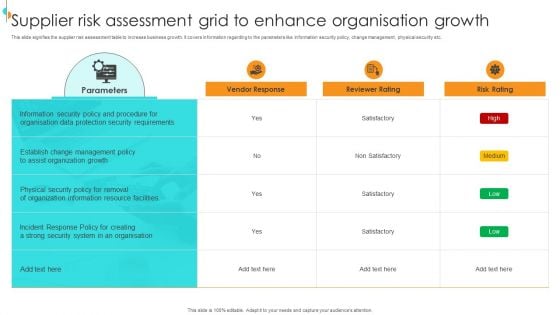
Supplier Risk Assessment Grid To Enhance Organisation Growth Download PDF
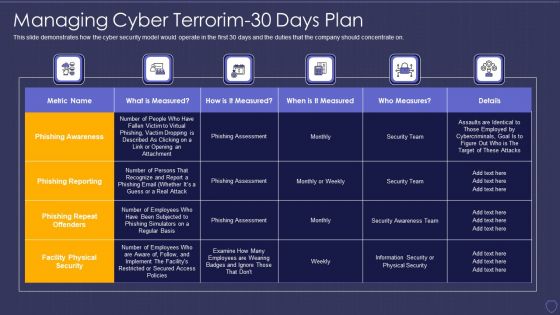
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorim 30 Days Plan Information PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it managing cyber terrorim 30 days plan information pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Web App Firewall Services IT Features Of WAF Protection Against The OWASP Vulnerabilities Graphics PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a web app firewall services it features of waf protection against the owasp vulnerabilities graphics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, data exposure, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
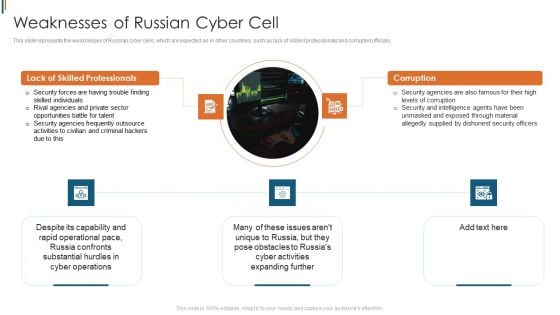
Ukraine Cyberwarfare Weaknesses Of Russian Cyber Cell Brochure Pdf
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Presenting ukraine cyberwarfare weaknesses of russian cyber cell brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security forces are having trouble finding skilled individuals, rival agencies and private sector opportunities battle for talent, security agencies frequently outsource activities to civilian and criminal hackers due to this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhanced Protection Corporate Event Administration How Firm Handle Insider Threats Structure PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a enhanced protection corporate event administration how firm handle insider threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































