Network Security

Major Distribution Strategies For Agriculture Business Plan Go To Market Strategy Topics Pdf
This slide highlights the top sales strategies for agriculture business which includes build distribution network, establish a cold chain, develop digital platform, leverage local network and build direct to consumer strategy. The Major Distribution Strategies For Agriculture Business Plan Go To Market Strategy Topics Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the top sales strategies for agriculture business which includes build distribution network, establish a cold chain, develop digital platform, leverage local network and build direct to consumer strategy.

Supply Planning Powerpoint Presentation Templates
This is a supply planning powerpoint presentation templates. This is a six stage process. The stages in this process are inventory planning, demand planning, supply planning, supply chain analytics, manufacturing planning, supply chain network design.

IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.
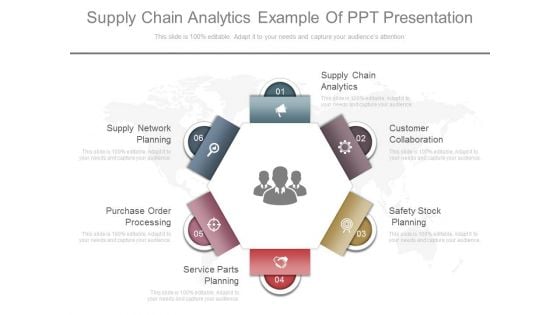
Supply Chain Analytics Example Of Ppt Presentation
This is a supply chain analytics example of ppt presentation. This is a six stage process. The stages in this process are supply chain analytics, customer collaboration, safety stock planning, purchase order processing, supply network planning, safety stock planning.

5G Technology Development For Digital Transformation Addressing Cost Determination Framework For 5G Pictures PDF
This slide provides details regarding cost determination framework for 5G network including network capacity, network coverage, energy efficient network, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download 5G Technology Development For Digital Transformation Addressing Cost Determination Framework For 5G Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
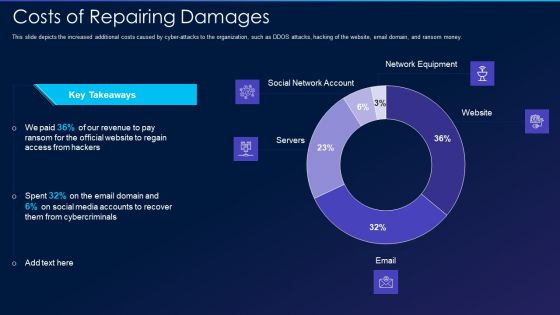
Cyber Exploitation IT Costs Of Repairing Damages Themes PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money. Deliver an awe inspiring pitch with this creative cyber exploitation it costs of repairing damages themes pdf bundle. Topics like social network account, servers, network equipment, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
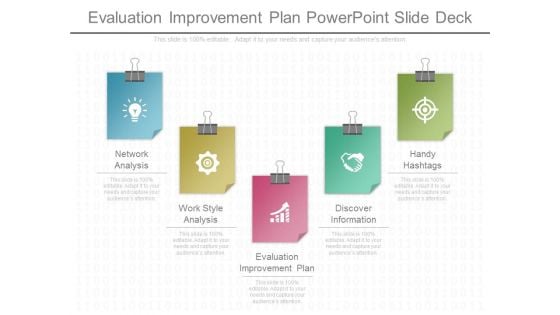
Evaluation Improvement Plan Powerpoint Slide Deck
This is an evaluation improvement plan powerpoint slide deck. This is a five stage process. The stages in this process are network analysis, work style analysis, evaluation improvement plan, discover information, handy hashtags.\n\n
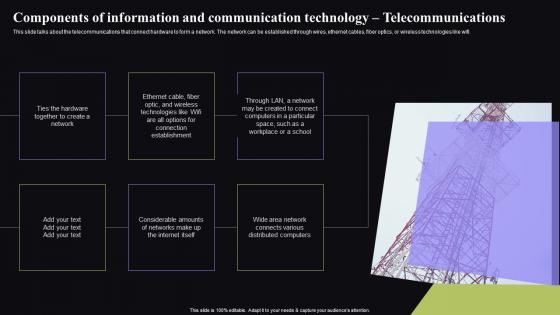
Y3 Video Conferencing In Corporate Components Of Information And Communication Microsoft Pdf
This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi. Present like a pro with Y3 Video Conferencing In Corporate Components Of Information And Communication Microsoft Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi.

Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection. This modern and well-arranged Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection.

Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Present like a pro with Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.
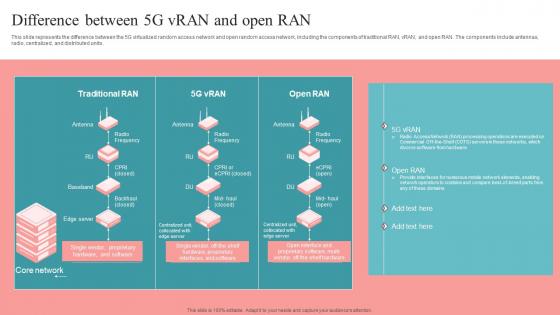
Difference Between 5G Vran And Open Ran Unlocking The Potential Of Open Ran Themes Pdf
This slide represents the difference between the 5G virtualized random access network and open random access network, including the components of traditional RAN, vRAN, and open RAN. The components include antennas, radio, centralized, and distributed units. There are so many reasons you need a Difference Between 5G Vran And Open Ran Unlocking The Potential Of Open Ran Themes Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the difference between the 5G virtualized random access network and open random access network, including the components of traditional RAN, vRAN, and open RAN. The components include antennas, radio, centralized, and distributed units.
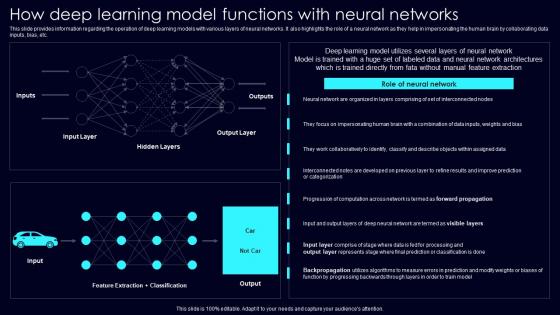
How Deep Learning Model Exploring Rise Of Generative AI In Artificial Intelligence Introduction Pdf
This slide provides information regarding the operation of deep learning models with various layers of neural networks. It also highlights the role of a neural network as they help in impersonating the human brain by collaborating data inputs, bias, etc. Boost your pitch with our creative How Deep Learning Model Exploring Rise Of Generative AI In Artificial Intelligence Introduction Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide provides information regarding the operation of deep learning models with various layers of neural networks. It also highlights the role of a neural network as they help in impersonating the human brain by collaborating data inputs, bias, etc.

Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Endpoint Initiated Vs Service Initiated Software Defined Perimeter SDP
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.
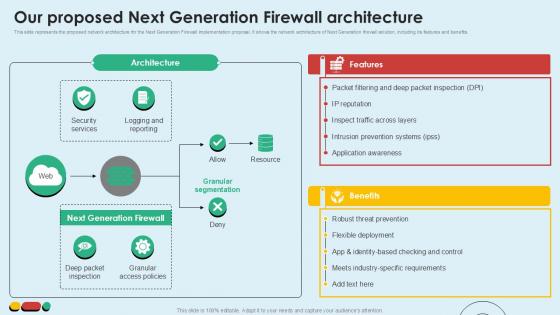
Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation
This slide represents the proposed network architecture for the Next Generation Firewall implementation proposal. It shows the network architecture of Next Generation firewall solution, including its features and benefits.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Our Proposed Next Generation Intelligent Intrusion Prevention System Ppt Presentation today and make your presentation stand out from the rest This slide represents the proposed network architecture for the Next Generation Firewall implementation proposal. It shows the network architecture of Next Generation firewall solution, including its features and benefits.
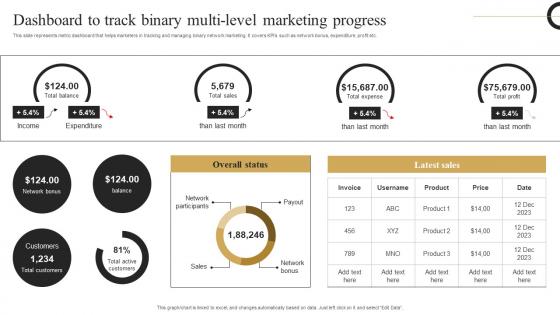
Dashboard Track Binary Multi Strategic Plan Develop Multi Level Marketing Microsoft Pdf
This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Dashboard Track Binary Multi Strategic Plan Develop Multi Level Marketing Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc.
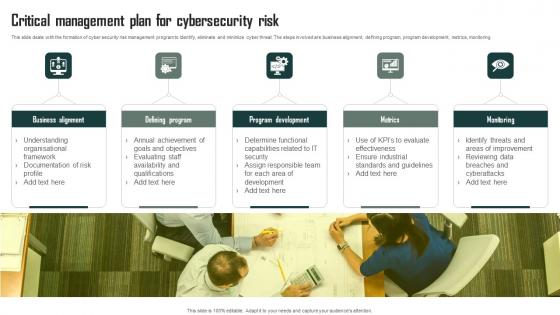
Critical Management Plan For Cybersecurity Risk Demonstration Pdf
This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring Pitch your topic with ease and precision using this Critical Management Plan For Cybersecurity Risk Demonstration Pdf This layout presents information on Business Alignment, Defining Program, Program Development It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring
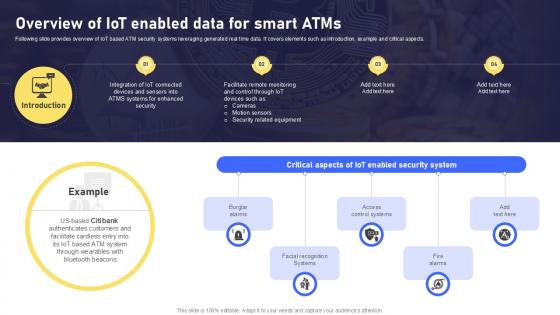
Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Are you searching for a Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V from Slidegeeks today. Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects.
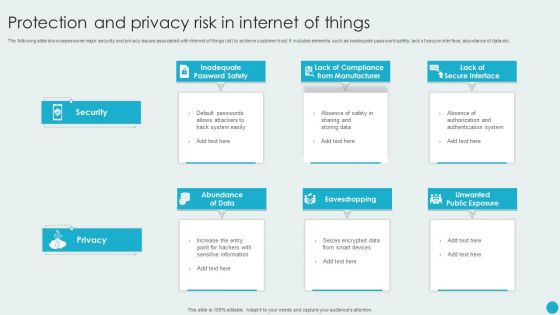
Protection And Privacy Risk In Internet Of Things Topics PDF
The following slide showcases some major security and privacy issues associated with internet of things iot to achieve customer trust. It includes elements such as inadequate password safety, lack of secure interface, abundance of data etc. Presenting Protection And Privacy Risk In Internet Of Things Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Abundance Of Data, Eavesdropping, Unwanted Public Exposure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
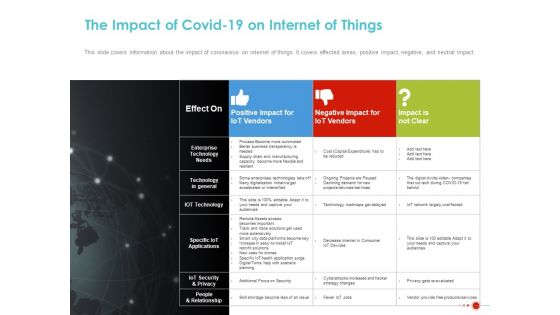
COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Internet Of Things Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on internet of things brochure pdf. The topics discussed in these slides are positive impact, iot vendors, negative impact iot vendors, impact not clear, enterprise technology needs, technology general, iot technology, specific iot applications, iot security and privacy, people and relationship. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V
This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights. This modern and well-arranged Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights.

Blockchain Technology Used IoT Fleet Monitoring Ppt Example IoT SS V
This slide provides an overview of the blockchain technology used in logistics for monitoring and communication . It also includes the benefits that it allows device communication, enhances security and provides authorization access. There are so many reasons you need a Blockchain Technology Used IoT Fleet Monitoring Ppt Example IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the blockchain technology used in logistics for monitoring and communication . It also includes the benefits that it allows device communication, enhances security and provides authorization access.
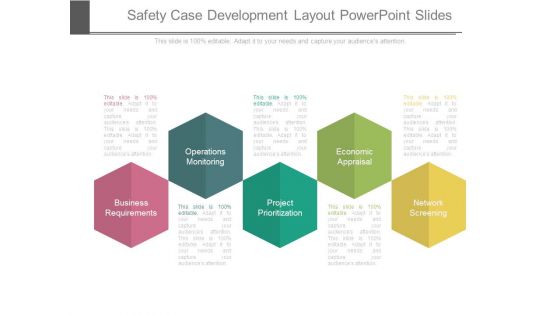
Safety Case Development Layout Powerpoint Slides
This is a safety case development layout powerpoint slides. This is a five stage process. The stages in this process are business requirements, operations monitoring, project prioritization, economic appraisal, network screening.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
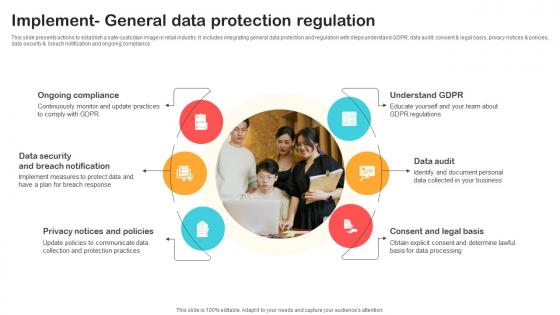
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
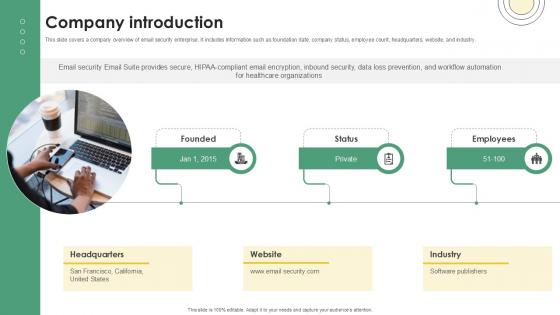
Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example
This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry.

Fact Safety Management Strategy Layout Ppt Sample Download
This is a fact safety management strategy layout ppt sample download. This is a eight stage process. The stages in this process are project prioritization, economic appraisal, diagnosis, counter measuring selection, equipment, people, environment, network screening.
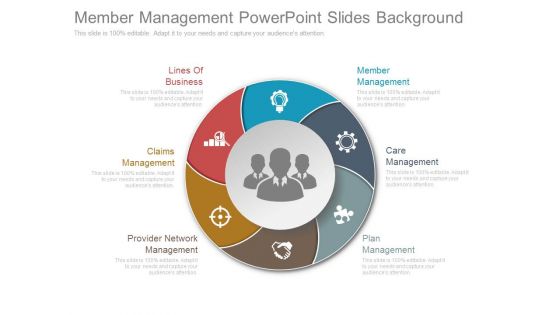
Member Management Powerpoint Slides Background
This is a member management powerpoint slides background. This is a six stage process. The stages in this process are lines of business, claims management, provider network management, member management, care management, plan management.
Business Objects Model Powerpoint Ideas

Critical Success Factors Powerpoint Presentation Examples
This is a critical success factors powerpoint presentation examples. This is a four stage process. The stages in this process are critical success factors, network architecture plan, business objects model, business activity modelling.
User Support Ppt Samples Download
This is a user support ppt samples download. This is a four stage process. The stages in this process are contact use support, query investigation, project planning network meeting, delivery and ongoing support.
Six Steps For Capacity Shortage Analysis Diagram Powerpoint Show
This is a six steps for capacity shortage analysis diagram powerpoint show. This is a six stage process. The stages in this process are network analysis, procurement, tactical forecast, causal analysis, execution and compliance, dynamic planning.
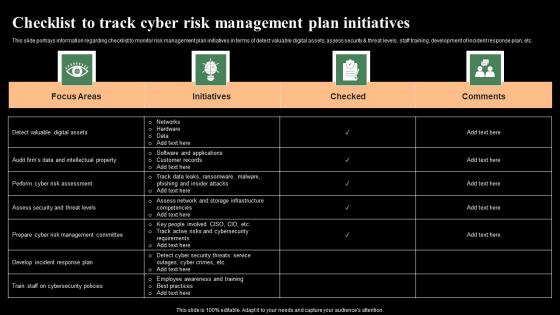
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc.

Relationship Between Open RAN And Private Unlocking The Potential Of Open RAN Download Pdf
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. Welcome to our selection of the Relationship Between Open RAN And Private Unlocking The Potential Of Open RAN Download Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs.

Iot Device Updates And Maintenance Overview Iot Device Management Guidelines Pdf
This slide exhibits IoT device updates management overview and benefits in order to improve device performance. It includes benefits such as a reduction in security threats, fewer bugs, enhance user experience and an increase in performance. Find a pre-designed and impeccable Iot Device Updates And Maintenance Overview Iot Device Management Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide exhibits IoT device updates management overview and benefits in order to improve device performance. It includes benefits such as a reduction in security threats, fewer bugs, enhance user experience and an increase in performance.
Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF
The slide showcases the interconnected functions of a framework used to guide the organizations security measures. It covers identify, protect, detect, respond and recover. Presenting Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify, Protect, Detect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
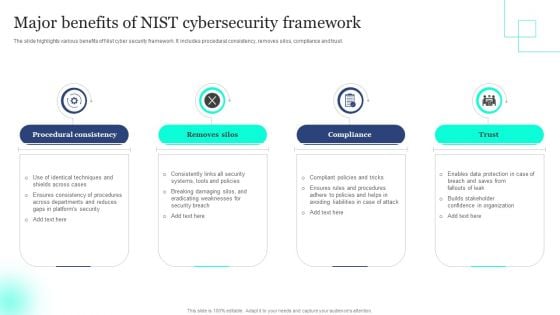
Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Boost your pitch with our creative Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams.
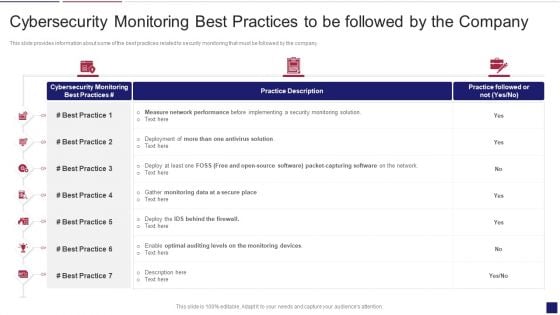
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Best Mockup PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring best mockup pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
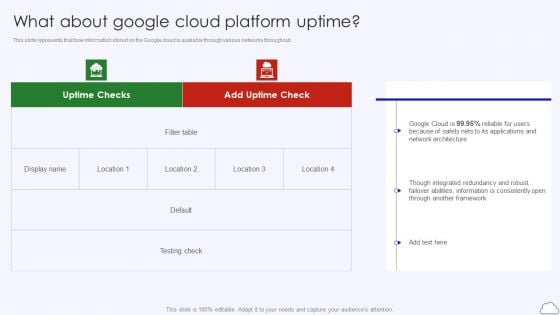
What About Google Cloud Platform Uptime Google Cloud Computing System Designs PDF
This slide represents that how information stored on the Google cloud is available through various networks throughout. Deliver an awe inspiring pitch with this creative What About Google Cloud Platform Uptime Google Cloud Computing System Designs PDF bundle. Topics like Network Architecture, Because Safety, Though Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
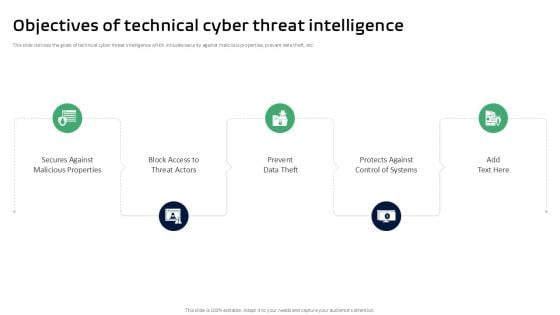
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
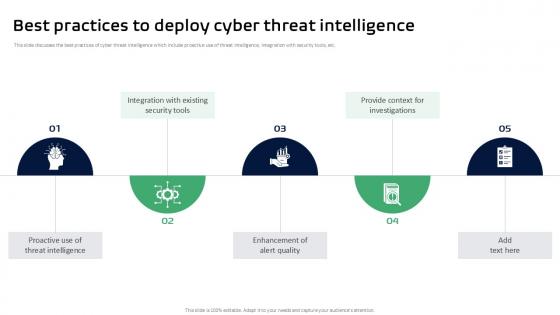
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.
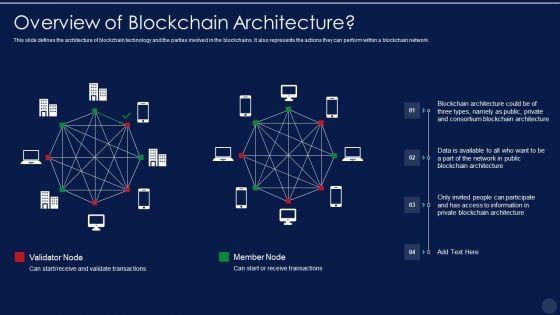
Blockchain Technology Framework IT Overview Of Blockchain Architecture Demonstration PDF
This slide defines the architecture of blockchain technology and the parties involved in the blockchains. It also represents the actions they can perform within a blockchain network. Deliver an awe inspiring pitch with this creative blockchain technology framework it overview of blockchain architecture demonstration pdf bundle. Topics like information, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
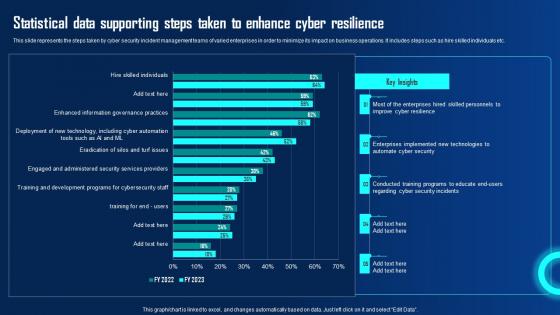
Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc.
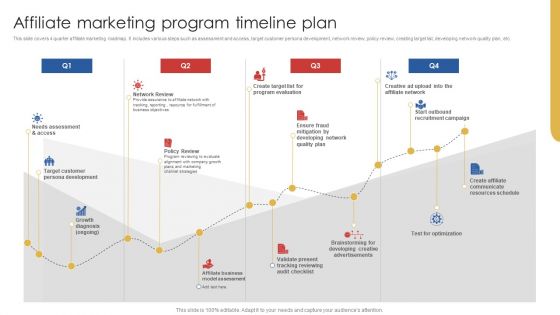
Affiliate Marketing Program Timeline Plan Structure PDF
This slide covers 4 quarter affiliate marketing roadmap. It includes various steps such as assessment and access, target customer persona development, network review, policy review, creating target list, developing network quality plan, etc. There are so many reasons you need a Affiliate Marketing Program Timeline Plan Structure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
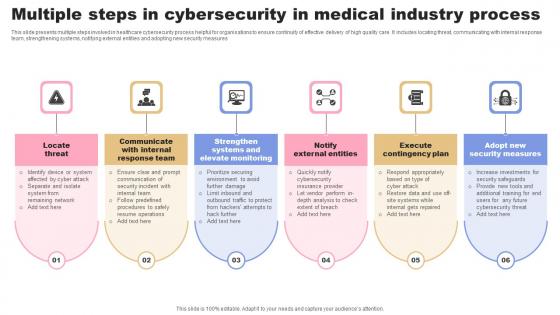
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures
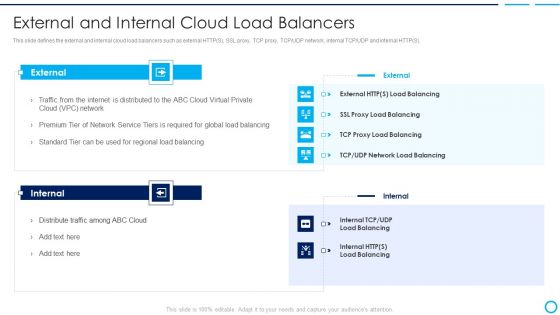
Categories Of Load Balancer External And Internal Cloud Load Balancers Ideas PDF
This slide defines the external and internal cloud load balancers such as external HTTPS, SSL proxy, TCP proxy, TCP UDP network, internal TCP UDP and internal HTTPS. Deliver an awe inspiring pitch with this creative categories of load balancer external and internal cloud load balancers ideas pdf bundle. Topics like proxy load balancing, network load balancing, global load balancing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Proactive Method For 5G Deployment By Telecom Companies Value Enabler 2 Horizontal Apis And Its Importance Clipart PDF
This slide provides details regarding value enabler for operator as horizontal APIs including its importance. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Value Enabler 2 Horizontal Apis And Its Importance Clipart PDF bundle. Topics like Industry Verticals, Network Interfaces, Network Exposure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Supply Chain Approaches Different Variables Of Supply Chain Model Graphics PDF
This slide shows the different variables of supply chain model such as location, allocation, network structuring, number of facilities and equipment, service sequence, volume and inventory level.Deliver an awe inspiring pitch with this creative Supply Chain Approaches Different Variables Of Supply Chain Model Graphics PDF bundle. Topics like Network Structuring, Service Sequence, Inventory Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
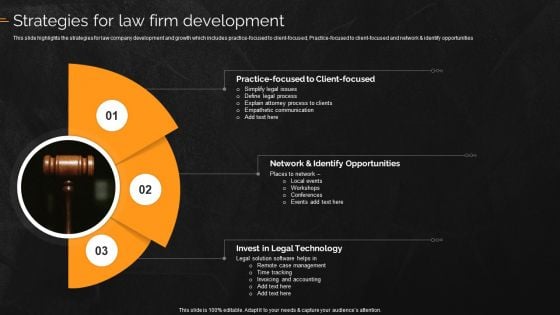
Law And Enforcement Company Profile Strategies For Law Firm Development Introduction PDF
This slide highlights the strategies for law company development and growth which includes practice-focused to client focused, Practice-focused to client focused and network and identify opportunities. Deliver an awe inspiring pitch with this creative Law And Enforcement Company Profile Strategies For Law Firm Development Introduction bundle. Topics like Identify Opportunities, Invest In Legal Technology, Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Transforming Telecom Industry Using Android Automation Topics PDF
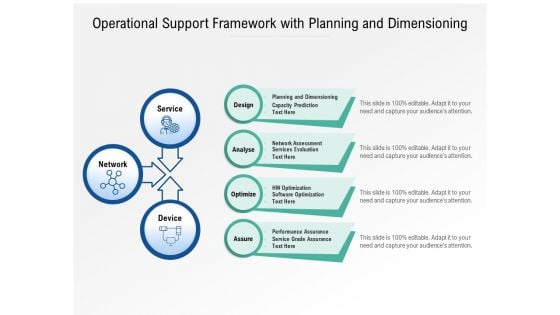
Operational Support Framework With Planning And Dimensioning Ppt PowerPoint Presentation Infographics Images PDF
Presenting this set of slides with name operational support framework with planning and dimensioning ppt powerpoint presentation infographics images pdf. This is a three stage process. The stages in this process are planning and dimensioning, capacity prediction, network assessment, hw optimization, software optimization, performance assurance, service grade assurance, design, analyse, optimize, assure, service, network, device. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
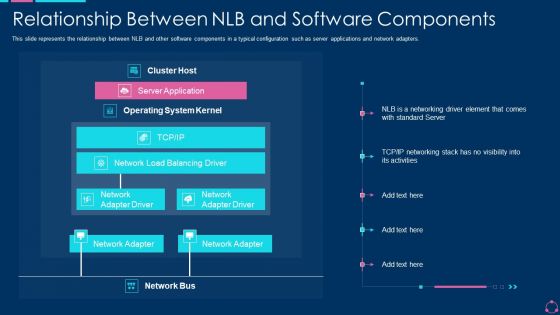
Relationship Between NLB And Software Components Ppt Outline Template PDF
This slide represents the relationship between NLB and other software components in a typical configuration such as server applications and network adapters. Deliver an awe inspiring pitch with this creative relationship between nlb and software components ppt outline template pdf bundle. Topics like operating system, server application, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
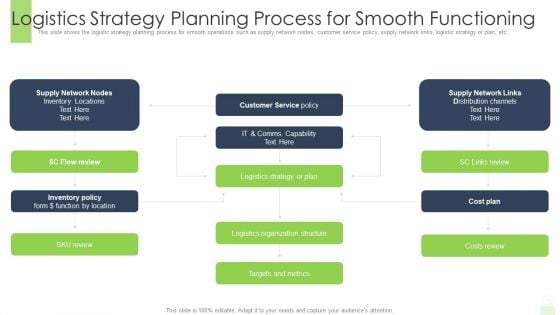
Logistics Strategy Planning Process For Smooth Functioning Ppt File Layouts PDF
This slide shows the logistic strategy planning process for smooth operations such as supply network nodes, customer service policy, supply network links, logistic strategy or plan, etc., Deliver and pitch your topic in the best possible manner with this logistics strategy planning process for smooth functioning ppt file layouts pdf. Use them to share invaluable insights on logistics organization structure, cost plan, customer service and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
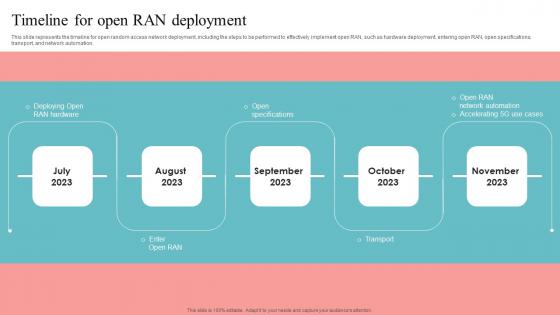
Timeline For Open RAN Deployment Unlocking The Potential Of Open RAN Ideas Pdf
This slide represents the timeline for open random access network deployment, including the steps to be performed to effectively implement open RAN, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. This Timeline For Open RAN Deployment Unlocking The Potential Of Open RAN Ideas Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the timeline for open random access network deployment, including the steps to be performed to effectively implement open RAN, such as hardware deployment, entering open RAN, open specifications, transport, and network automation.
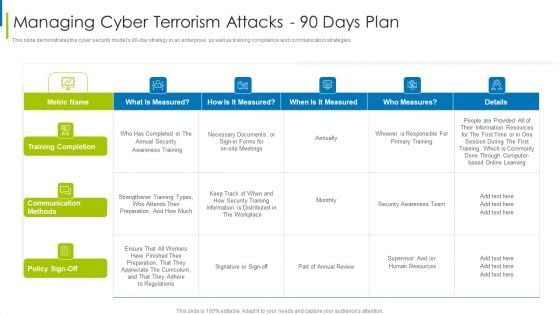
Cyber Terrorism Assault Managing Cyber Terrorism Attacks 90 Days Plan Formats PDF
This slide demonstrates the cyber security models 90 to day strategy in an enterprise, as well as training compliance and communication strategies.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism attacks 90 days plan formats pdf Use them to share invaluable insights on training completion, communication methods, information is distributed and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.

Common Smart Packaging Application Types Optimizing Inventory Management IoT SS V
This slide provides an overview of the common packaging applications. Major types covered are freshness, reusable, connected, security self-life extension, tracking and tracing packaging. Welcome to our selection of the Common Smart Packaging Application Types Optimizing Inventory Management IoT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide provides an overview of the common packaging applications. Major types covered are freshness, reusable, connected, security self-life extension, tracking and tracing packaging.
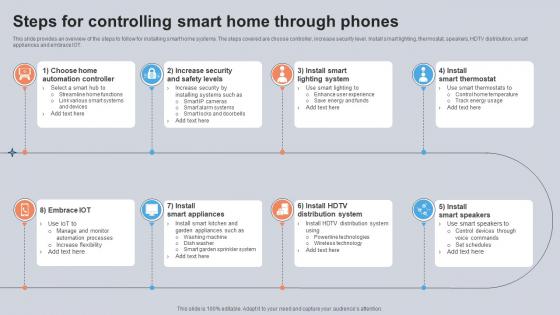
Steps For Controlling Smart Home Through Phones Utilizing Smart Appliances IoT SS V
This slide provides an overview of the steps to follow for installing smart home systems. The steps covered are choose controller, increase security level. Install smart lighting, thermostat, speakers, HDTV distribution, smart appliances and embrace IOT. Boost your pitch with our creative Steps For Controlling Smart Home Through Phones Utilizing Smart Appliances IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide provides an overview of the steps to follow for installing smart home systems. The steps covered are choose controller, increase security level. Install smart lighting, thermostat, speakers, HDTV distribution, smart appliances and embrace IOT.
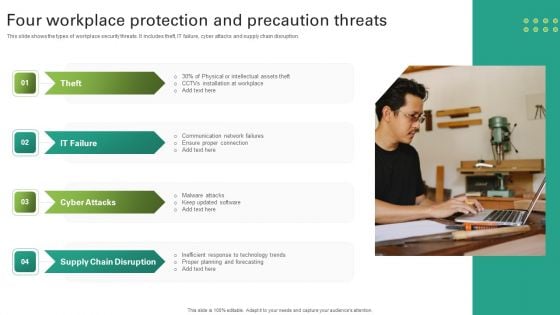
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































