Password Security

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
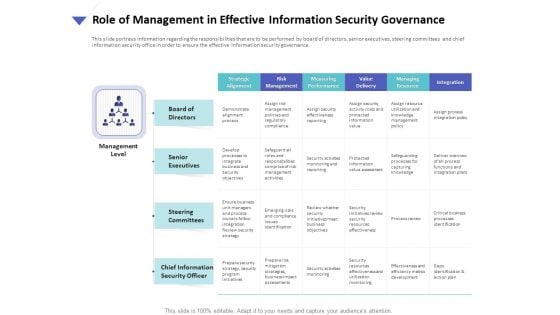
Strategies To Mitigate Cyber Security Risks Role Of Management In Effective Information Security Governance Ppt Model File Formats PDF
Presenting this set of slides with name strategies to mitigate cyber security risks role of management in effective information security governance ppt model file formats pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Hacking Prevention Awareness Training For IT Security Icons Slide Hacking Prevention Awareness Training For IT Security Information PDF
Introducing our well designed hacking prevention awareness training for it security icons slide hacking prevention awareness training for it security information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Table Of Content Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Elements PDF
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Icons Slide For Real Time Assessment Of Security Threats Sample PDF
Presenting our innovatively structured real time assessment of security threats icons slide for real time assessment of security threats sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
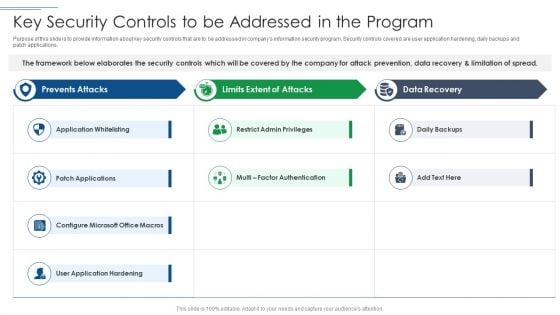
IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
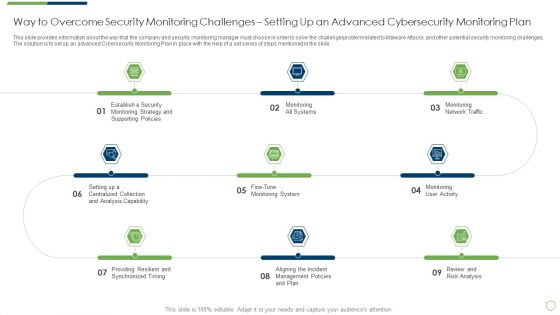
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
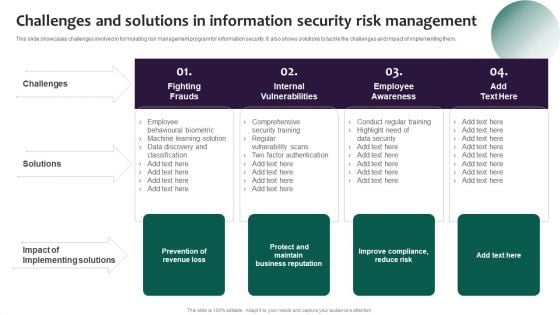
Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF
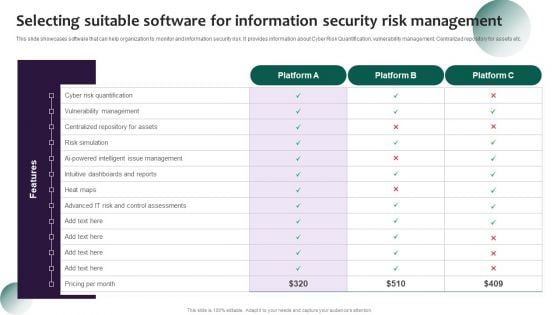
Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
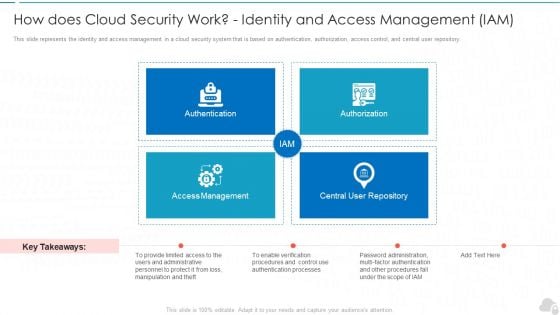
How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
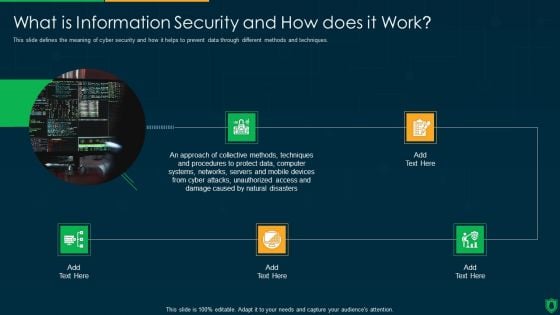
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Impact On Organization After Implementing Information Technology Security Strategy And Training Ppt Slides Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this it security impact on organization after implementing information technology security strategy and training ppt slides deck pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

30 60 90 Days Plan To Implement Cloud Security In Business Cloud Computing Security IT Ppt Gallery Master Slide PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 days plan to implement cloud security in business cloud computing security it ppt gallery master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performed, analyze, cloud services, data access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
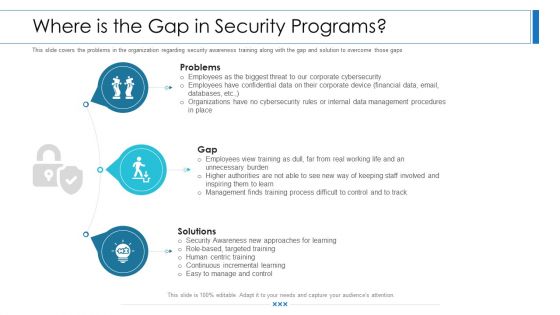
Workforce Security Realization Coaching Plan Where Is The Gap In Security Programs Ppt Show Master Slide PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a workforce security realization coaching plan where is the gap in security programs ppt show master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
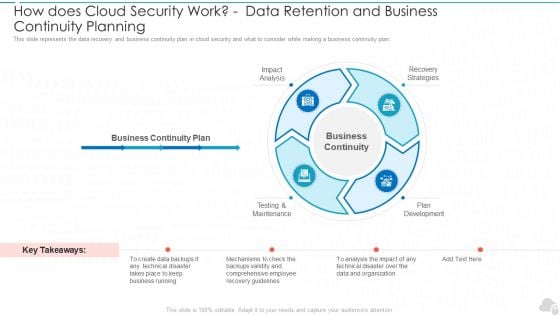
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers.
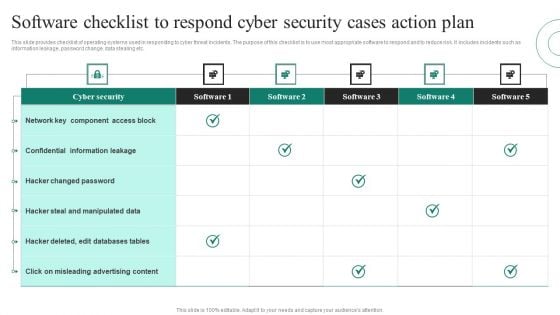
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
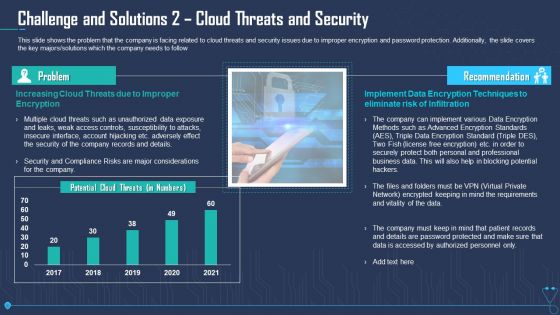
Challenge And Solutions 2 Cloud Threats And Security Ppt Gallery Images PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt gallery images pdf bundle. Topics like challenge and solutions 2 cloud threats and security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 2 Cloud Threats And Security Ppt Inspiration Slideshow PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver and pitch your topic in the best possible manner with this challenge and solutions 2 cloud threats and security ppt inspiration slideshow pdf. Use them to share invaluable insights on security, risks, encryption methods, echniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Challenge And Solutions 2 Cloud Threats And Security Ppt Styles Graphics PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt styles graphics pdf bundle. Topics like problem, recommendation, potential cloud threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
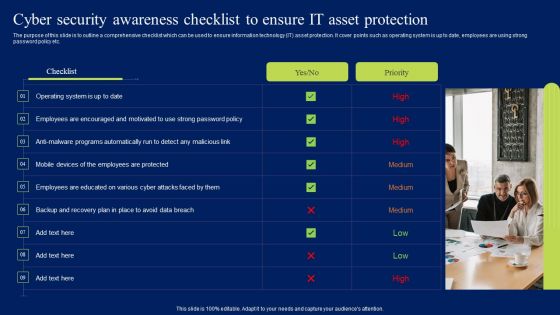
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
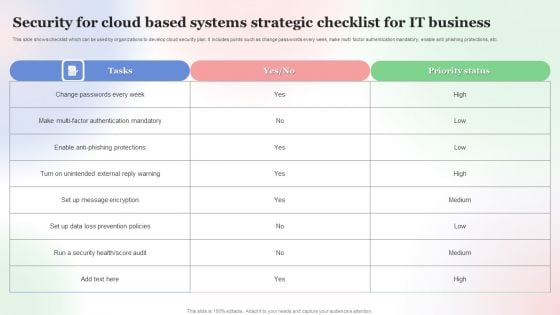
Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Internet PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Computer PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to The data is secure, security, business, technology, internet, computer. The prominent colors used in the PowerPoint template are Black, Gray, Yellow. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our internet PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Customers tell us our business PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. People tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. With our Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113 you will feel free. They drastically cut down the burden on you.
Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF
Persuade your audience using this Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Security Computer, System Interface Securing, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
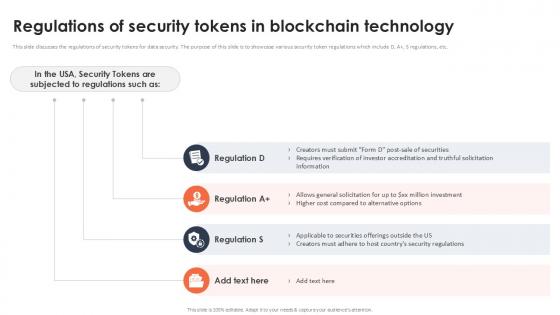
Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.

Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Explore a selection of the finest Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.
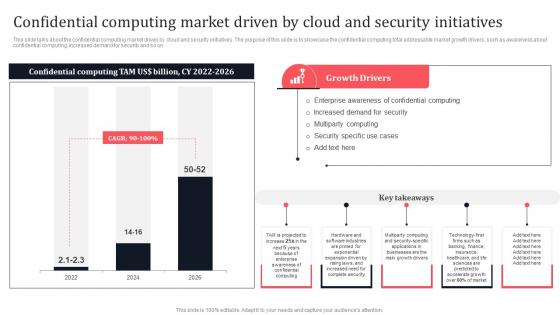
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
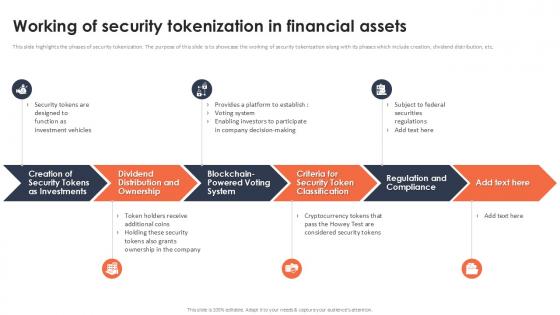
Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.
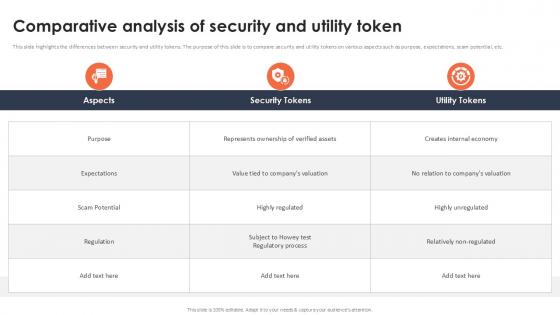
Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
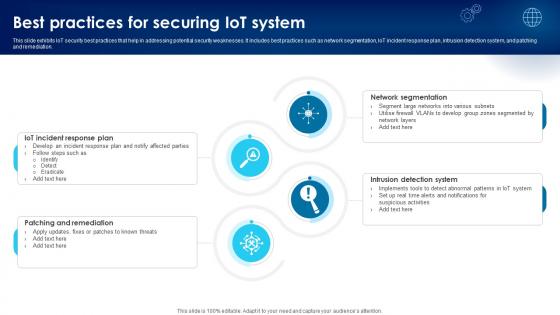
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.
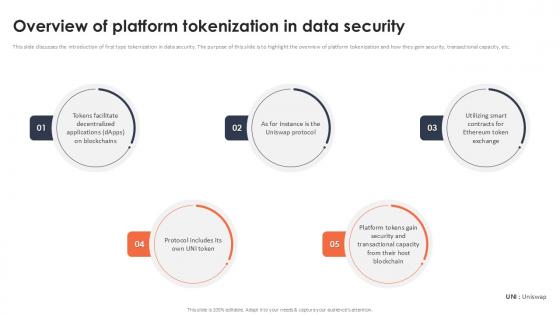
Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.

Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides
This slide discusses the two types of secure code review in application security which are automated code review and manual code review. This Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses the two types of secure code review in application security which are automated code review and manual code review.
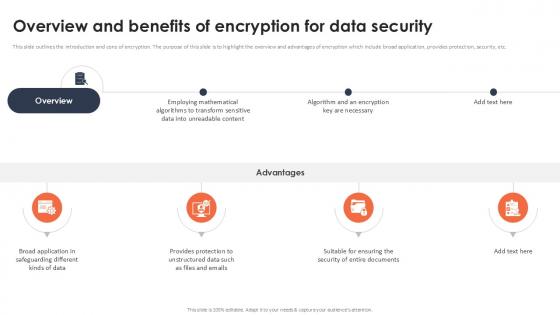
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.
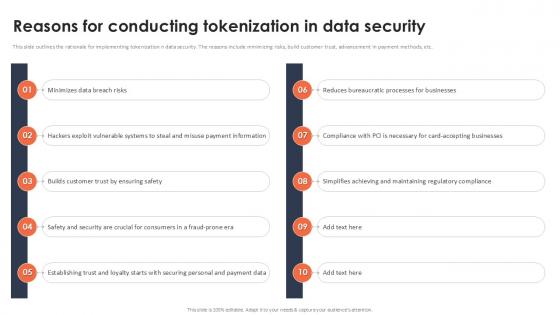
Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
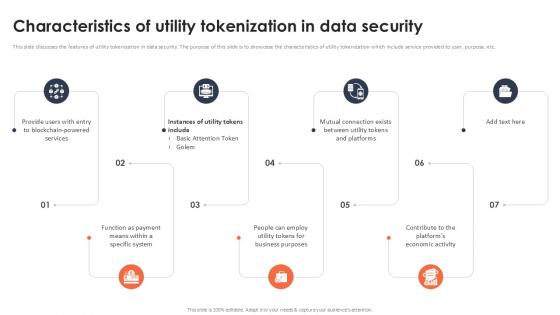
Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.
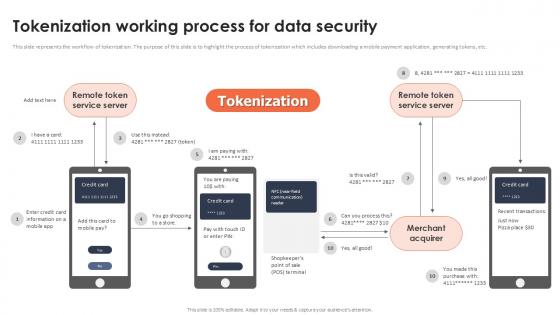
Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.

Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Slidegeeks is here to make your presentations a breeze with Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.
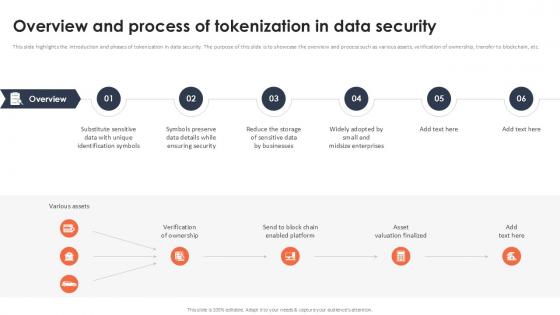
Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
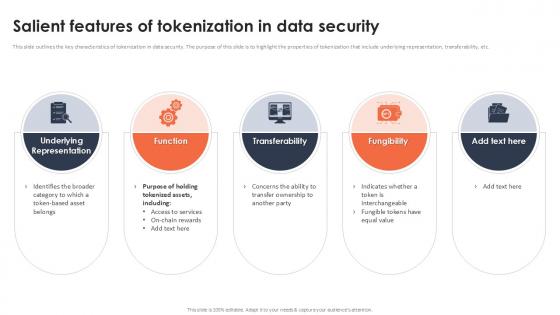
Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc.
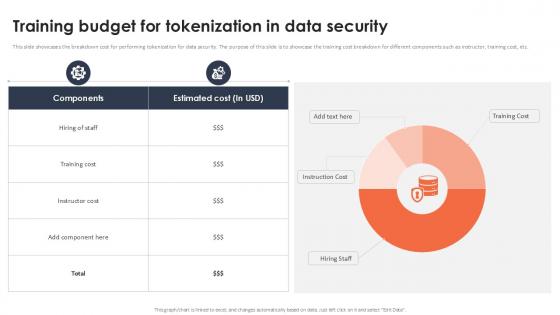
Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.
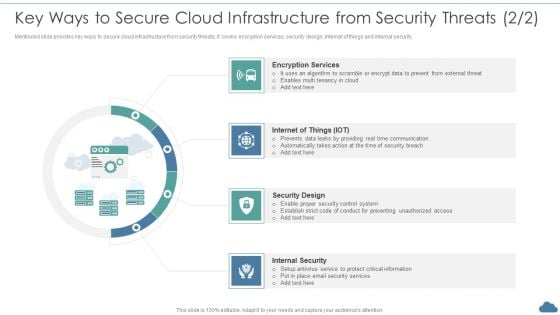
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
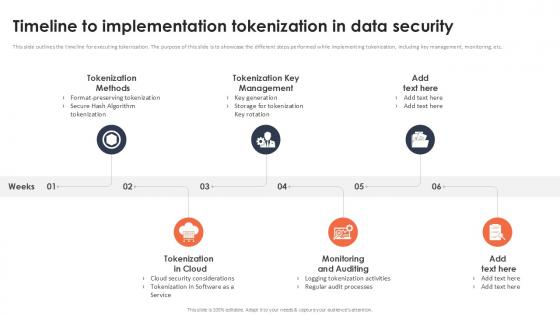
Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Get a simple yet stunning designed Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface.
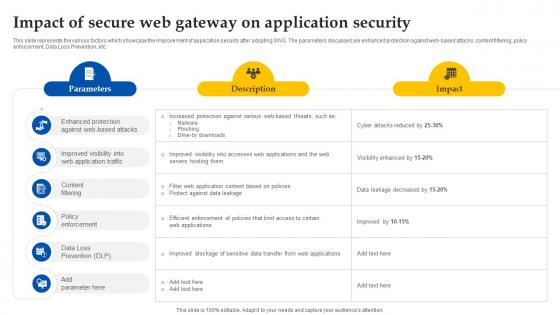
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
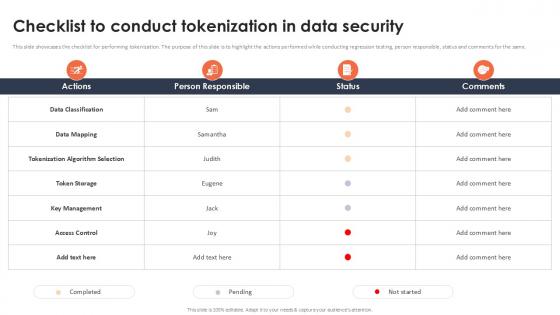
Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present like a pro with Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.
Securing Windows With Network Security System Ppt PowerPoint Presentation File Slides PDF
Presenting this set of slides with name securing windows with network security system ppt powerpoint presentation file slides pdf. The topics discussed in these slide is securing windows with network security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































