Password Security

Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
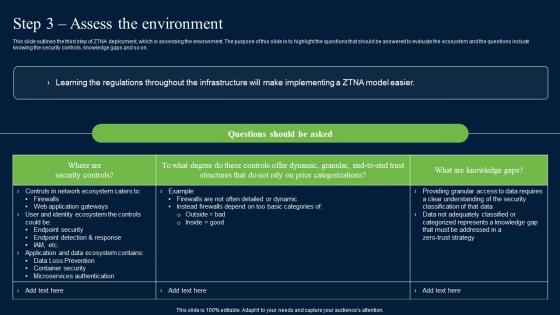
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.
Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. Our Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now. Our Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
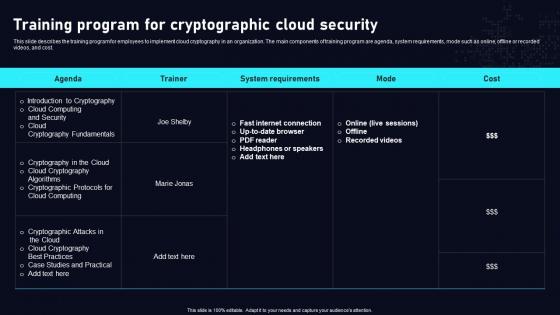
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck
Take advantage of this well-researched and professionally-designed Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty one-slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below. Our Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business.

Table Of Contents Global Data Security Industry Report IR SS V
Slidegeeks has constructed Table Of Contents Global Data Security Industry Report IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
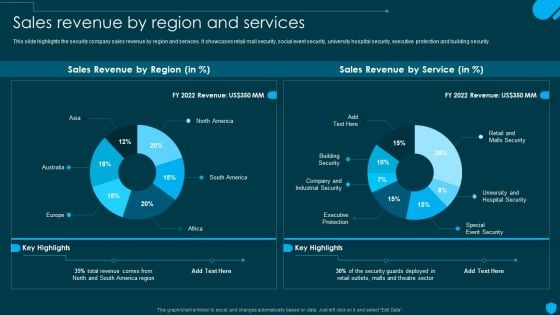
Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF. Use them to share invaluable insights on Sales Revenue, Region And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. The Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
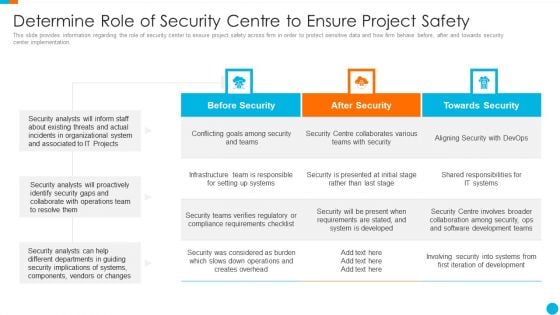
Upgrading Total Project Safety IT Determine Role Of Security Centre To Ensure Project Safety Download PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative upgrading total project safety it determine role of security centre to ensure project safety download pdf bundle. Topics like before security, after security, towards security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
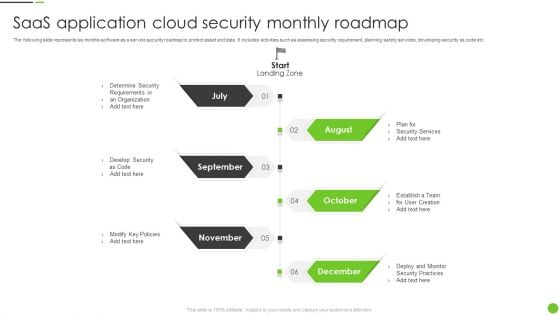
Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF
The following slide represents six months software as a service security roadmap to protect asset and data. It includes activities such as assessing security requirement, planning safety services, developing security as code etc. Presenting Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Determine Security, Develop Security, Modify Key Policies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
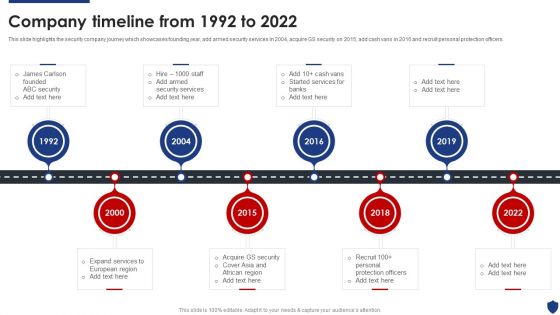
Security Officer Service Company Profile Company Timeline From 1992 To 2022 Themes PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Security Officer Service Company Profile Company Timeline From 1992 To 2022 Themes PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Expand Services, Acquire GS Security, Security Services, 1992 To 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
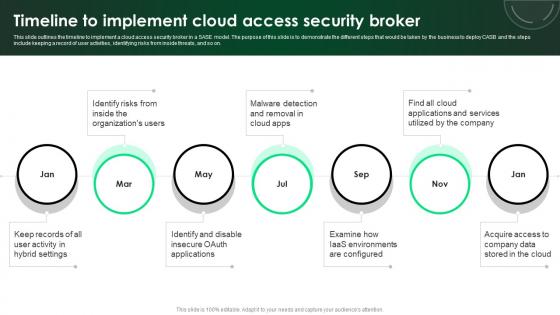
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.
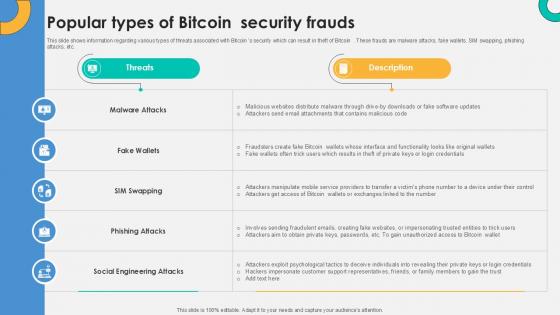
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
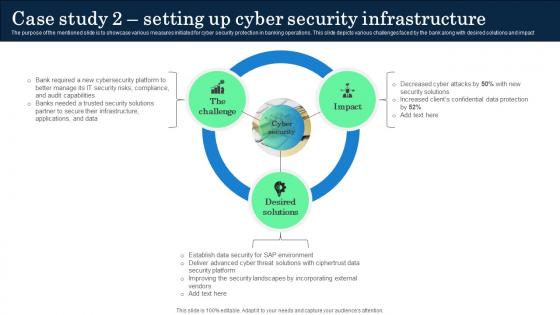
Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact. Present like a pro with Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact
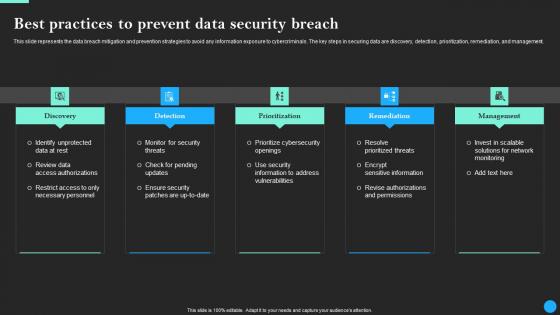
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
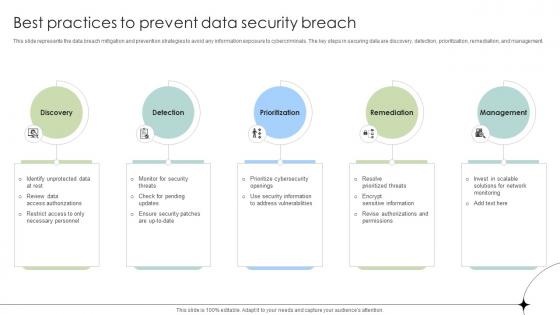
Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.

Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Explore a selection of the finest Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc.
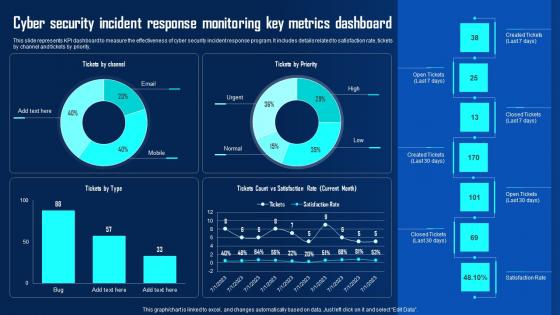
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.
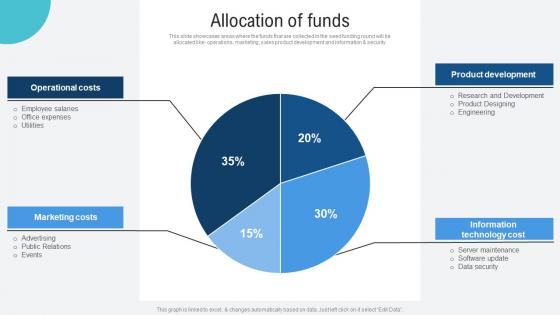
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
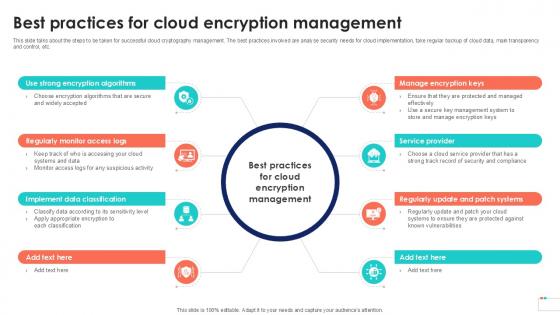
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
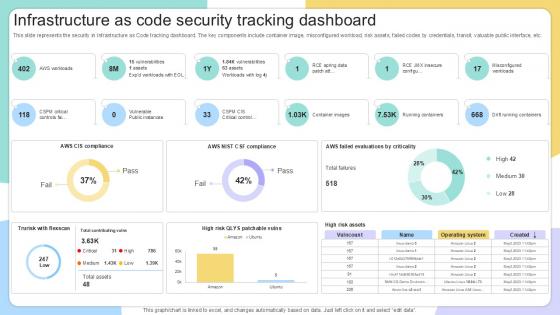
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.
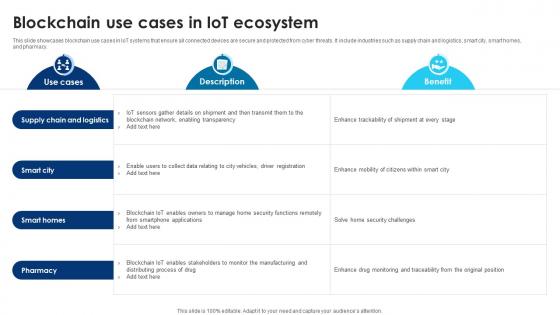
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy.
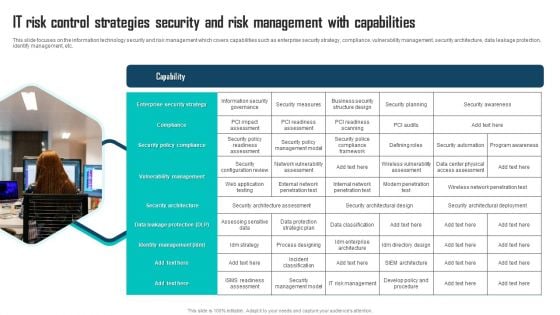
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
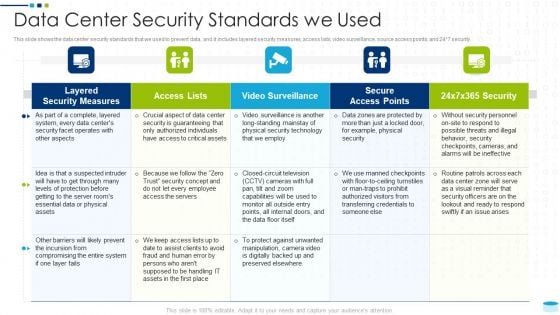
Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
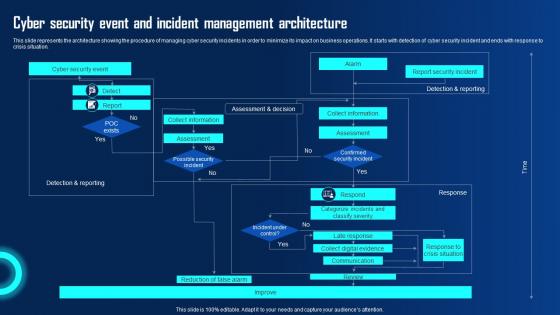
Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf
This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.
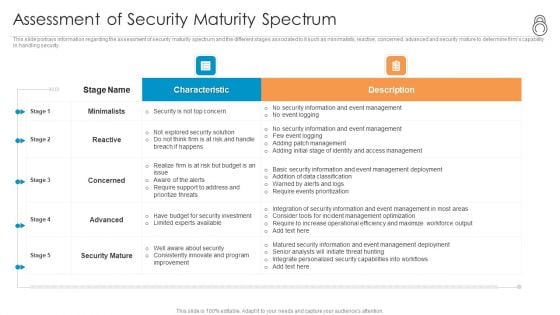
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Welcome to our selection of the Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc.

Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V
This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access. Find a pre-designed and impeccable Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access.
Google Cloud Console IT Google Cloud Services Identity And Security Ppt Icon Graphics Design PDF
This slide describes the identity and security service of Google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a google cloud console it google cloud services identity and security ppt icon graphics design pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud resource manager, cloud platform security, cloud security scanner, cloud iam. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
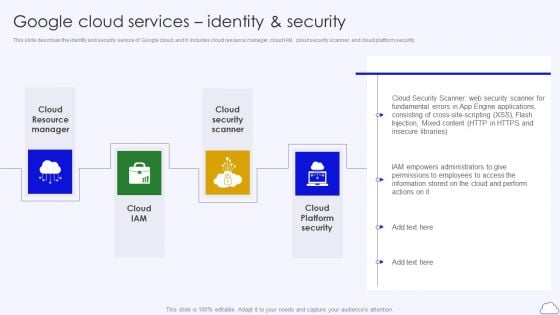
Google Cloud Services Identity And Security Google Cloud Computing System Themes PDF
This slide describes the identity and security service of Google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security.Presenting Google Cloud Services Identity And Security Google Cloud Computing System Themes PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Resource Manager, Security Scanner, Platform Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
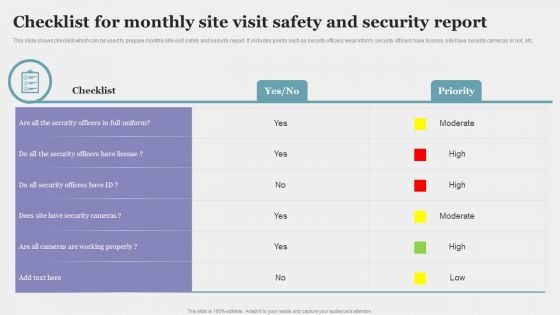
Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF
This slide shows checklist which can be used to prepare monthly site visit safety and security report. It includes points such as security officers wear inform, security officers have license, site have security cameras or not, etc. Showcasing this set of slides titled Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF. The topics addressed in these templates are Security Officers, Monthly Site, Visit Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V
This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc. Present like a pro with Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc.
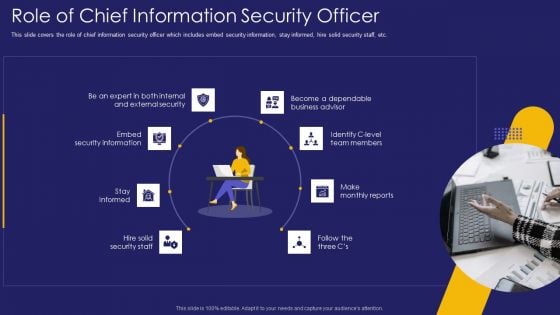
Role IT Team Digital Transformation Role Of Chief Information Security Officer Summary PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting role it team digital transformation role of chief information security officer summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like security information, security staff, monthly reports. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
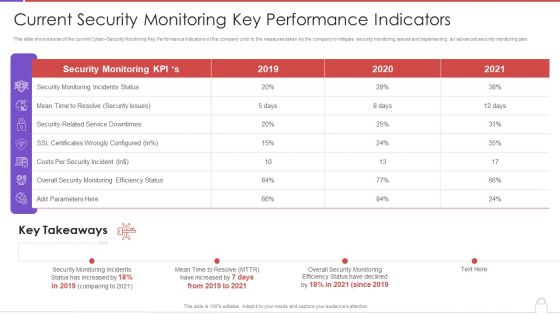
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
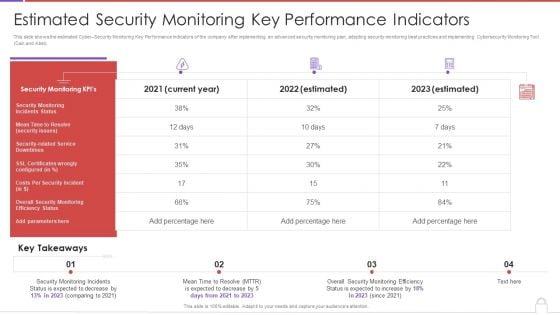
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
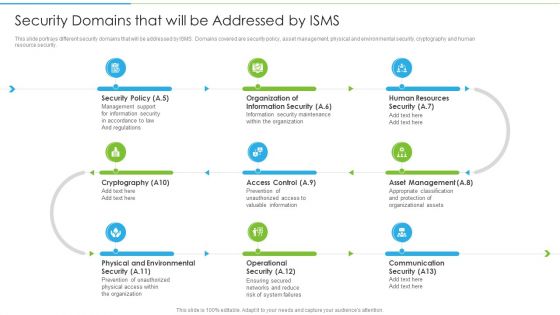
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
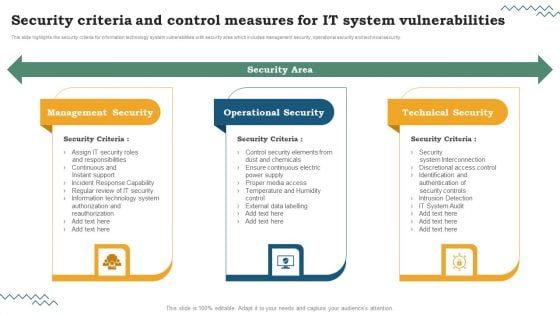
Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc. There are so many reasons you need a Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.
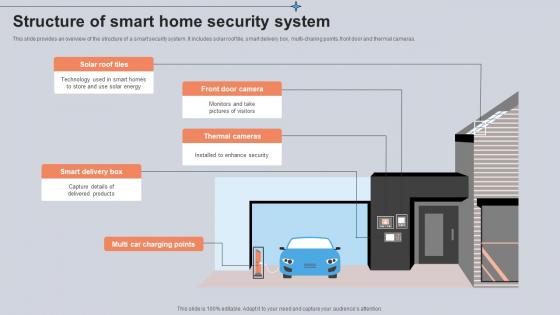
Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V
This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras.

Overview Need For Implementing Data Security Across Retail DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Make sure to capture your audiences attention in your business displays with our gratis customizable Overview Need For Implementing Data Security Across Retail DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
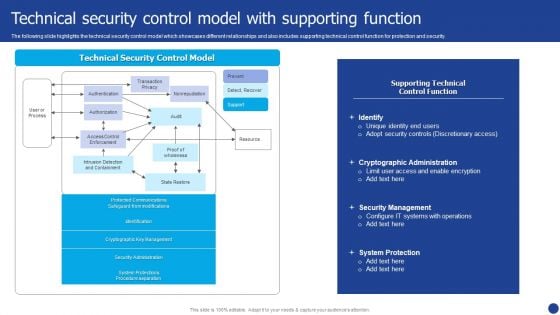
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc.
Online Security Threat And Computer Virus Vector Icon Ppt PowerPoint Presentation Styles Vector PDF
Presenting online security threat and computer virus vector icon ppt powerpoint presentation styles vector pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including online security threat and computer virus vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































