Safety Management
Develop Secure Database Ppt PowerPoint Presentation Outline Graphic Tips Cpb
Presenting this set of slides with name develop secure database ppt powerpoint presentation outline graphic tips cpb. This is an editable Powerpoint four stages graphic that deals with topics like develop secure database to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
E Security Web Technology Ppt PowerPoint Presentation File Display Cpb
Presenting this set of slides with name e security web technology ppt powerpoint presentation file display cpb. This is an editable Powerpoint six stages graphic that deals with topics like e security web technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Operations Analytics Reporting Ppt PowerPoint Presentation Outline Templates Cpb
Presenting this set of slides with name security operations analytics reporting ppt powerpoint presentation outline templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like security operations analytics reporting to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Orchestration Automated Response Ppt PowerPoint Presentation Show Examples Cpb
Presenting this set of slides with name security orchestration automated response ppt powerpoint presentation show examples cpb. This is an editable Powerpoint four stages graphic that deals with topics like security orchestration automated response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Implementing Security E Commerce Ppt PowerPoint Presentation Icon Microsoft Cpb
Presenting this set of slides with name implementing security e commerce ppt powerpoint presentation icon microsoft cpb. This is an editable Powerpoint six stages graphic that deals with topics like implementing security e commerce to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Multi Cloud Security Architecture Ppt PowerPoint Presentation Pictures Maker Cpb
Presenting this set of slides with name multi cloud security architecture ppt powerpoint presentation pictures maker cpb. This is an editable Powerpoint five stages graphic that deals with topics like multi cloud security architecture to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Authentication Information Security Ppt PowerPoint Presentation Ideas Guide Cpb Pdf
Presenting this set of slides with name authentication information security ppt powerpoint presentation ideas guide cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like authentication information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Corporate Security Tool Ppt PowerPoint Presentation Outline Sample Cpb Pdf
Presenting this set of slides with name corporate security tool ppt powerpoint presentation outline sample cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like corporate security tool to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Applications Cyber Security Ppt PowerPoint Presentation Infographics Brochure Cpb Pdf
Presenting this set of slides with name applications cyber security ppt powerpoint presentation infographics brochure cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like applications cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Medical Data Security Ppt PowerPoint Presentation Show Cpb Pdf
Presenting this set of slides with name medical data security ppt powerpoint presentation show cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like medical data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Dashboard Examples Ppt PowerPoint Presentation Infographics Background Cpb Pdf
Presenting this set of slides with name security dashboard examples ppt powerpoint presentation infographics background cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security dashboard examples to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Enterprise Security Review Ppt PowerPoint Presentation File Visuals Cpb Pdf
Presenting this set of slides with name enterprise security review ppt powerpoint presentation file visuals cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like enterprise security review to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Assessment Ppt PowerPoint Presentation File Infographics Cpb
Presenting this set of slides with name security assessment ppt powerpoint presentation file infographics cpb. This is an editable Powerpoint six stages graphic that deals with topics like security assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Company Security Policies Ppt PowerPoint Presentation Summary Portrait Cpb Pdf
Presenting this set of slides with name company security policies ppt powerpoint presentation summary portrait cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like company security policies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Assessment Checklist Ppt PowerPoint Presentation Model Rules Cpb Pdf
Presenting this set of slides with name security assessment checklist ppt powerpoint presentation model rules cpb pdf. This is an editable Powerpoint nine stages graphic that deals with topics like security assessment checklist to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Privileged Account Security Tools Ppt PowerPoint Presentation Styles Cpb Pdf
Presenting this set of slides with name privileged account security tools ppt powerpoint presentation styles cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like privileged account security tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
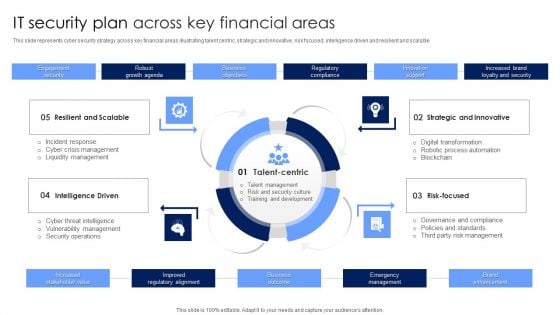
IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
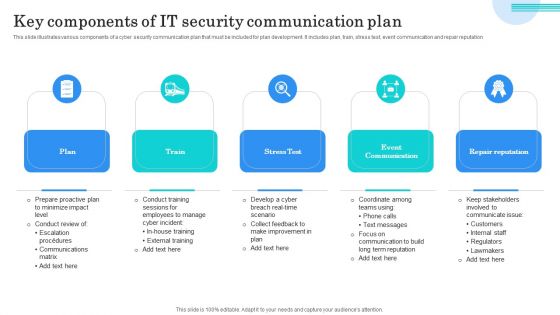
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example
This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc.
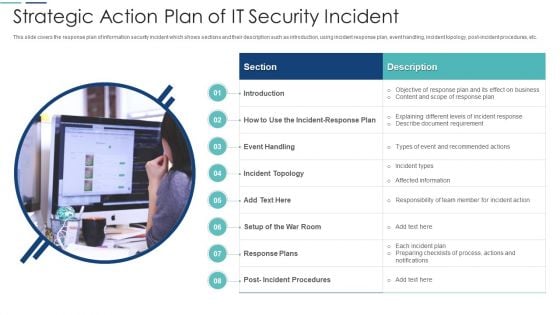
Strategic Action Plan Of It Security Incident Ideas PDF
This slide covers the response plan of information security incident which shows sections and their description such as introduction, using incident response plan, event handling, incident topology, post-incident procedures, etc. Persuade your audience using this strategic action plan of it security incident ideas pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including strategic action plan of it security incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
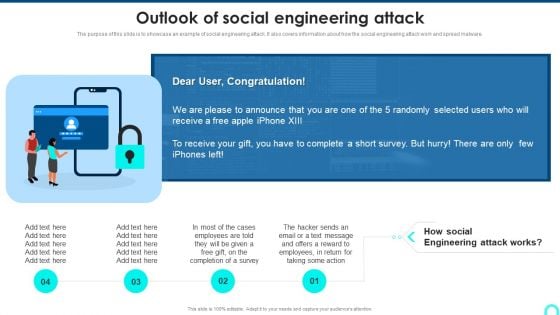
Outlook Of Social Engineering Attack Brochure PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. This is a Outlook Of Social Engineering Attack Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Engineering Attack, Employees Return, Randomly Selected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Risk Assessment Framework Demonstration PDF
The following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting Information Technology Security Risk Assessment Framework Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
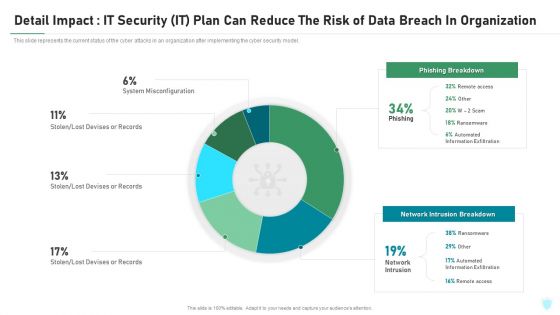
Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
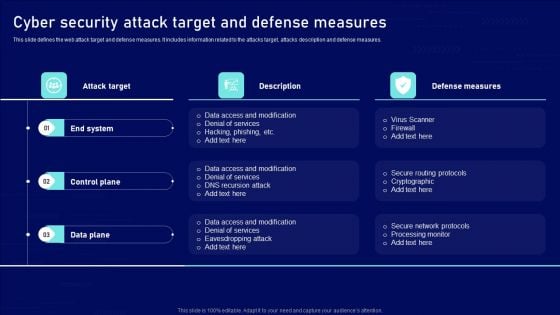
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
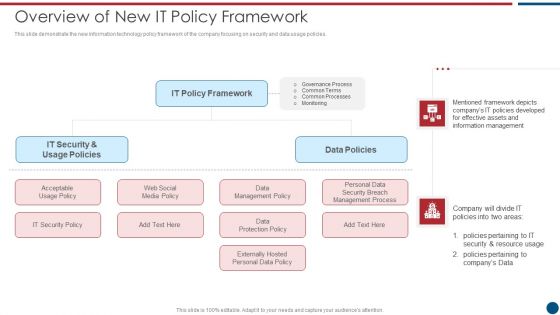
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
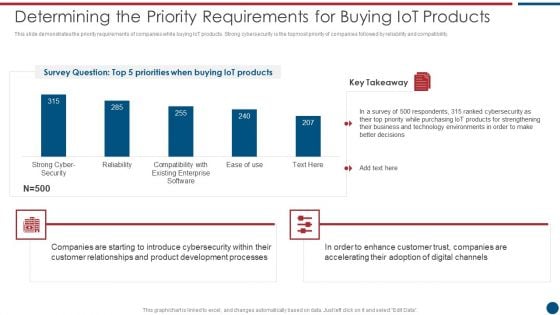
Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
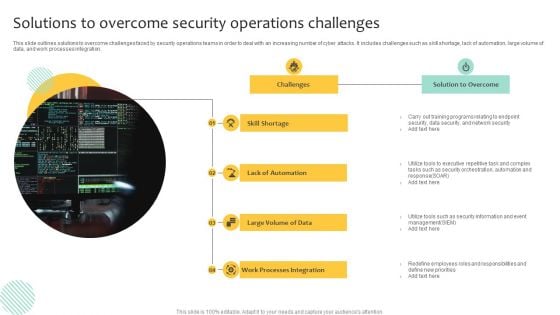
Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
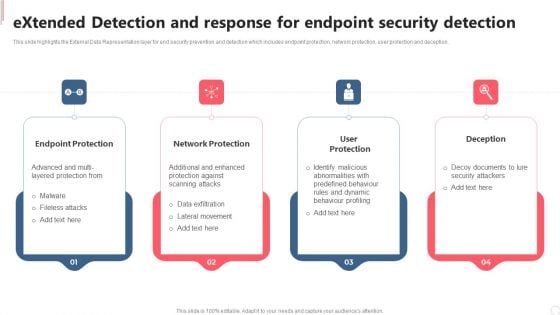
Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Possible Solutions Key Design Ppt Slides
This is a possible solutions key design ppt slides. This is a seven stage process. The stages in this process are business, puzzles or jigsaws, success.\n\n\n\n

Organizational Design Methodologies Powerpoint Guide
This is a organizational design methodologies powerpoint guide. This is a five stage process. The stages in this process are requirements, design, implementation, verification, maintenance.
Possible Solutions Ppt PowerPoint Presentation Portfolio
This is a possible solutions ppt powerpoint presentation portfolio. This is a five stage process. The stages in this process are business, strategy, marketing, success, puzzle, key lock.
Event Promotion Business Ppt Powerpoint Presentation Infographics Portrait Cpb
This is a event promotion business ppt powerpoint presentation infographics portrait cpb. This is a four stage process. The stages in this process are event promotion business.
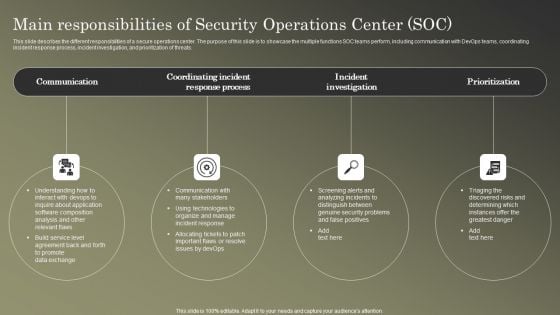
Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF
This slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. There are so many reasons you need a Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
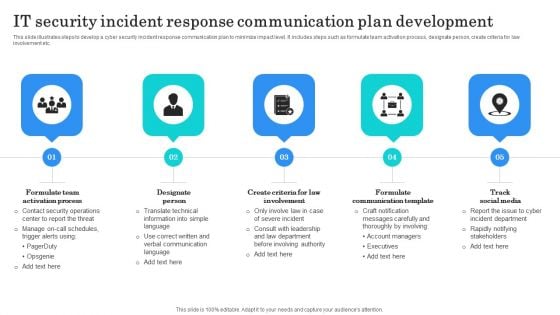
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
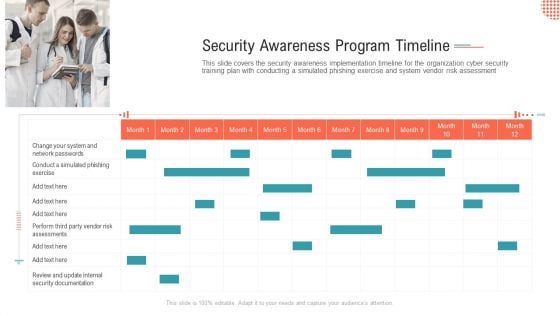
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
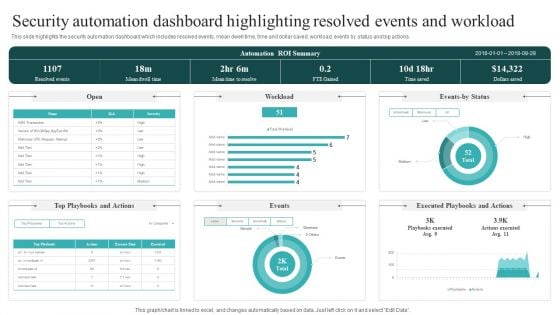
Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. This Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
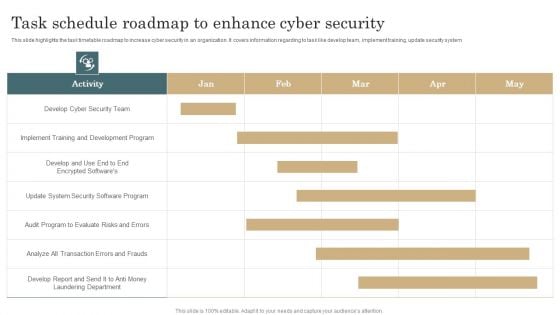
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Security Gap Analysis With Risk Level Information PDF
The following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Pitch your topic with ease and precision using this Information Technology Security Gap Analysis With Risk Level Information PDF. This layout presents information on Organize Security, Regularly Analyze, Gap Assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
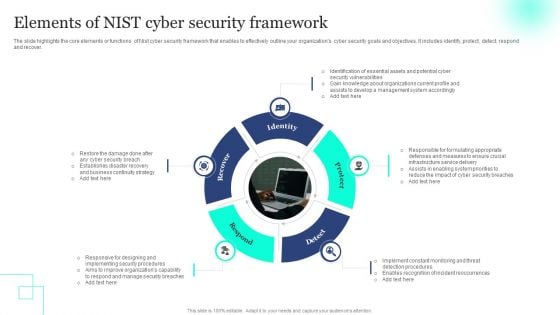
Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
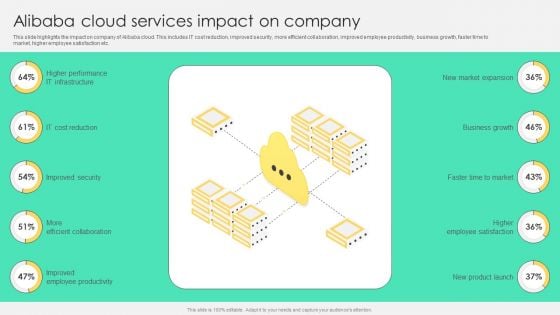
Alibaba Cloud Services Impact On Company Background PDF
This slide highlights the impact on company of Alibaba cloud. This includes IT cost reduction, improved security, more efficient collaboration, improved employee productivity, business growth, faster time to market, higher employee satisfaction etc. This Alibaba Cloud Services Impact On Company Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Alibaba Cloud Services Impact On Company Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
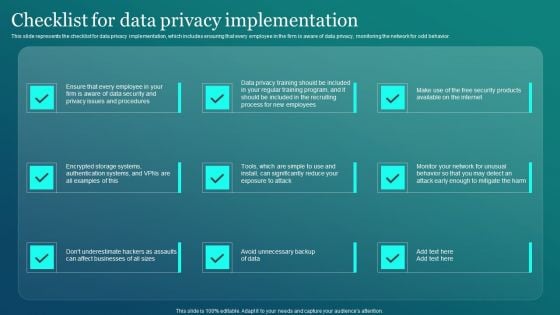
Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
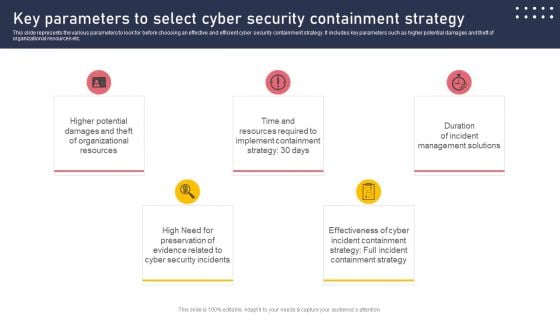
Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
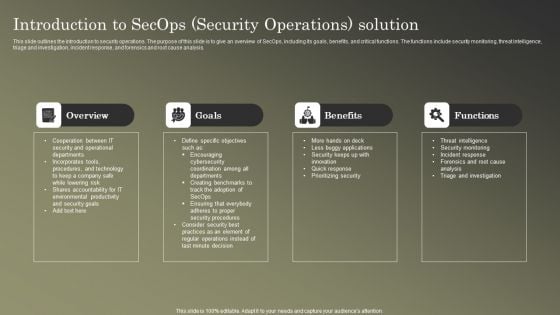
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cybersecurity Security Framework In Cloud Computing Ppt Portfolio Grid PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a cybersecurity security framework in cloud computing ppt portfolio grid pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, identify, protect, detect, respond. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
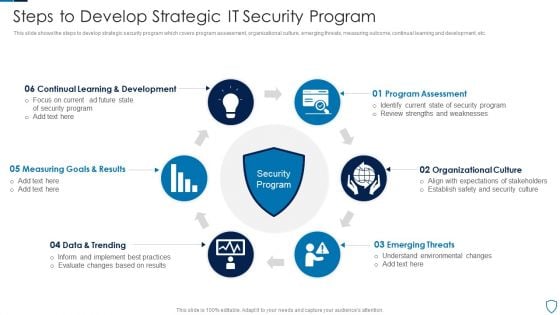
Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
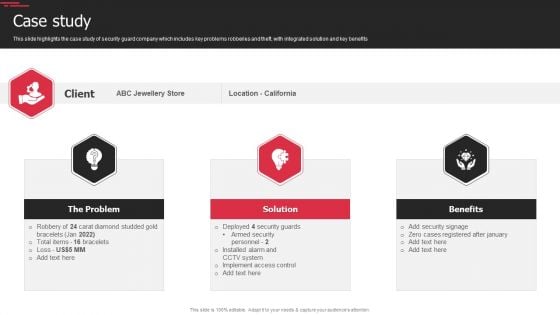
Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Case Study Mockup PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. This is a Manpower Corporate Security Business Profile Case Study Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solution, Benefits, The Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
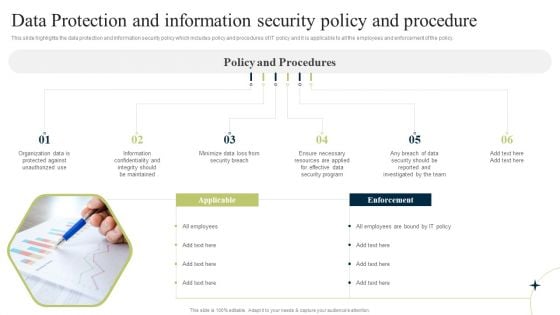
New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Want to ace your presentation in front of a live audience Our New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Information And Technology Security Operations Circular Inspiration PDF
This is a information and technology security operations circular inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like circular. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Functioning Centre Circular Diagram Ppt Portfolio Diagrams PDF
This is a security functioning centre circular diagram ppt portfolio diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like circular diagram. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Circular Diagram IT Security IT Ppt Layouts Tips PDF
Presenting circular diagram it security it ppt layouts tips pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like circular diagram. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
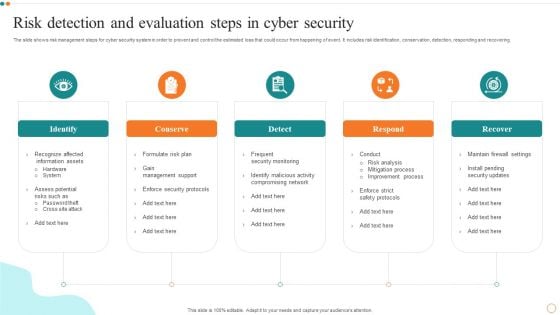
Risk Detection And Evaluation Steps In Cyber Security Designs PDF
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
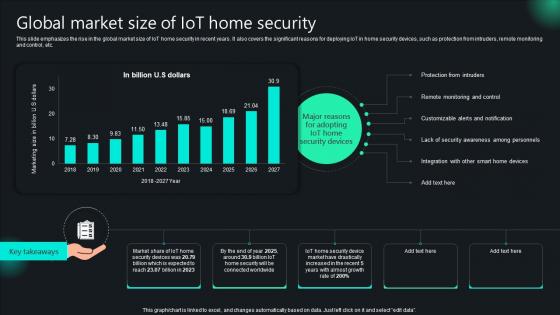
Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V
This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc. The Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc.


 Continue with Email
Continue with Email

 Home
Home


































