Survey Slide

Sustainable Industrial Efforts And Restrictions Of Green Computing
This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiatives related to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Sustainable Industrial Efforts And Restrictions Of Green Computing for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiatives related to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development.
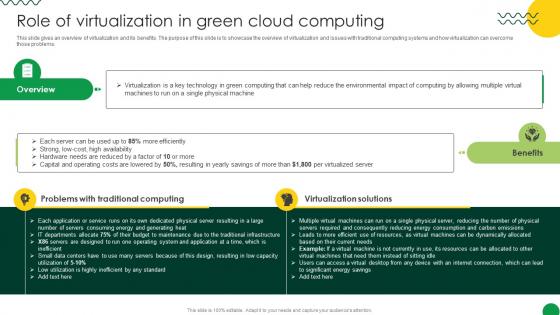
Sustainable Role Of Virtualization In Green Cloud Computing
This slide gives an overview of virtualization and its benefits. The purpose of this slide is to showcase the overview of virtualization and issues with traditional computing systems and how virtualization can overcome those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Sustainable Role Of Virtualization In Green Cloud Computing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of virtualization and its benefits. The purpose of this slide is to showcase the overview of virtualization and issues with traditional computing systems and how virtualization can overcome those problems.

External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
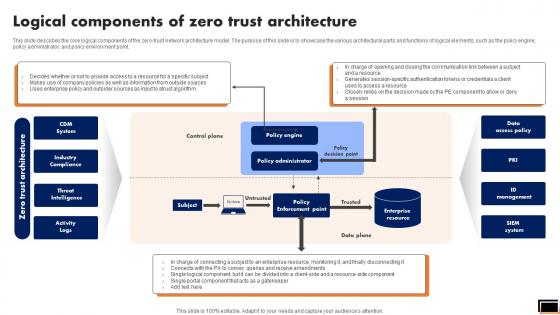
Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
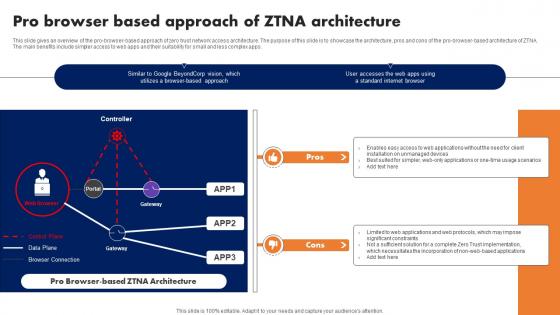
Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.

Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
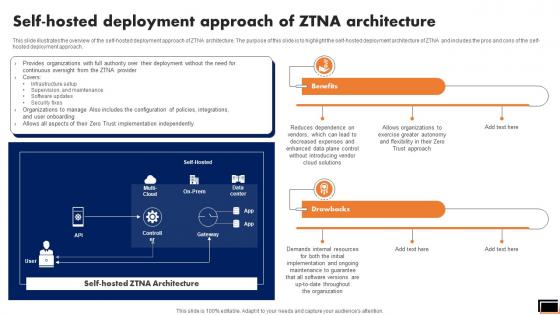
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
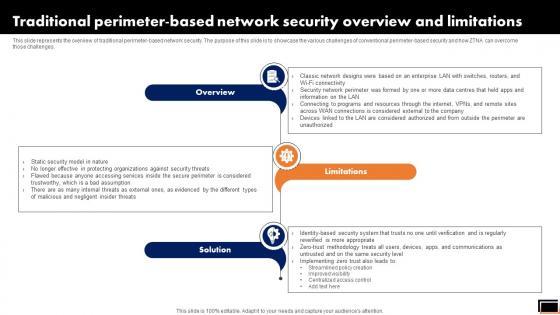
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
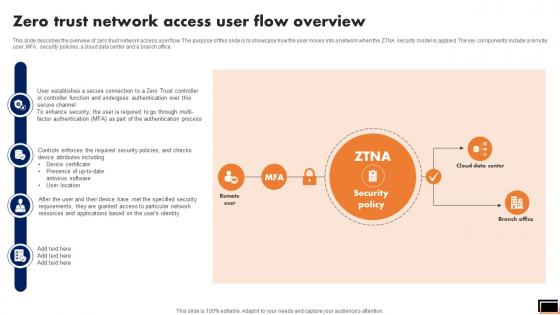
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
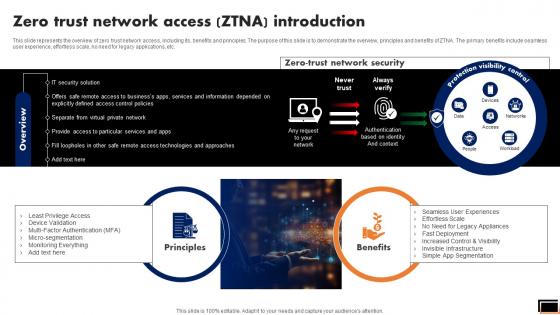
Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Restaurant Marketing Team Responsibilities Raci Matrix Create An Effective Restaurant
This slide shows the responsibility matrix. The purpose of this slide is to frame in advance who is responsible for which task to meet the marketing objective on time. It includes such as product manager, marketing strategies, advertising, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Restaurant Marketing Team Responsibilities RACI Matrix Create An Effective Restaurant a try. Our experts have put a lot of knowledge and effort into creating this impeccable Restaurant Marketing Team Responsibilities Raci Matrix Create An Effective Restaurant. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide shows the responsibility matrix. The purpose of this slide is to frame in advance who is responsible for which task to meet the marketing objective on time. It includes such as product manager, marketing strategies, advertising, etc.
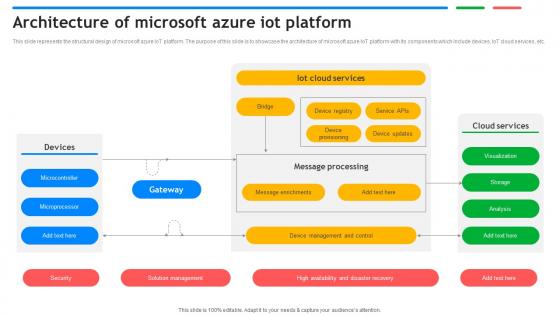
Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform
This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform a try. Our experts have put a lot of knowledge and effort into creating this impeccable Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc.
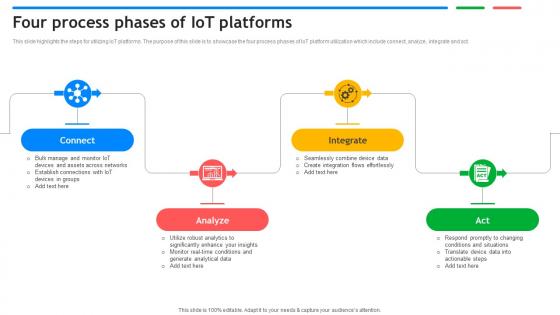
Four Process Phases Of IoT Platforms Exploring Google Cloud IoT Platform
This slide highlights the steps for utilizing IoT platforms. The purpose of this slide is to showcase the four process phases of IoT platform utilization which include connect, analyze, integrate and act. If you are looking for a format to display your unique thoughts, then the professionally designed Four Process Phases Of IoT Platforms Exploring Google Cloud IoT Platform is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Four Process Phases Of IoT Platforms Exploring Google Cloud IoT Platform and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the steps for utilizing IoT platforms. The purpose of this slide is to showcase the four process phases of IoT platform utilization which include connect, analyze, integrate and act.

Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present like a pro with Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment.

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.

Mental Health Awareness Activities Planned Building A Winning Community Outreach Strategy SS V
This slide covers key activities that are expected to be performed by community health organizations under various schemes launched. The purpose of this template is to provide an overview on calendar defining activities scheduled along with dates for new financial year. The Mental Health Awareness Activities Planned Building A Winning Community Outreach Strategy SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers key activities that are expected to be performed by community health organizations under various schemes launched. The purpose of this template is to provide an overview on calendar defining activities scheduled along with dates for new financial year.

Facebook Marketing Plan Humorous Content Example To Boost Organic Strategy SS V
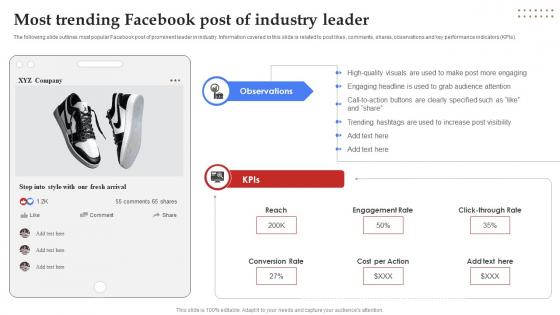
Facebook Marketing Plan Most Trending Facebook Post Of Industry Leader Strategy SS V

Salient Features Of Pictory Generative AI How Generative AI Tools Work AI SS V
This slide provides information regarding salient features of Pictory platform that include AI slide development, extensive template library, customization options, collaboration features, generate video highlight reel, access to stock clips, realistic AI voice, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Salient Features Of Pictory Generative AI How Generative AI Tools Work AI SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide provides information regarding salient features of Pictory platform that include AI slide development, extensive template library, customization options, collaboration features, generate video highlight reel, access to stock clips, realistic AI voice, etc.
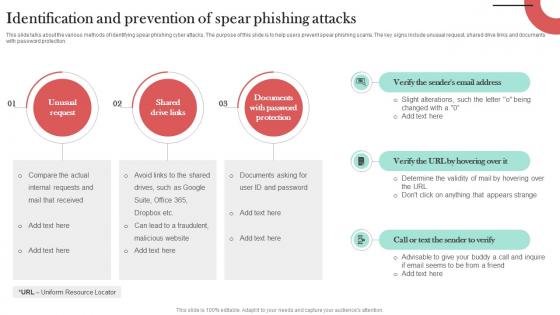
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection.
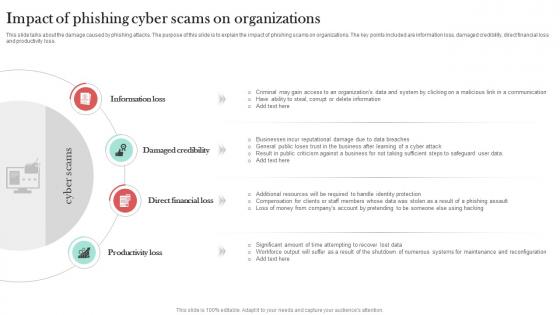
Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT. This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.
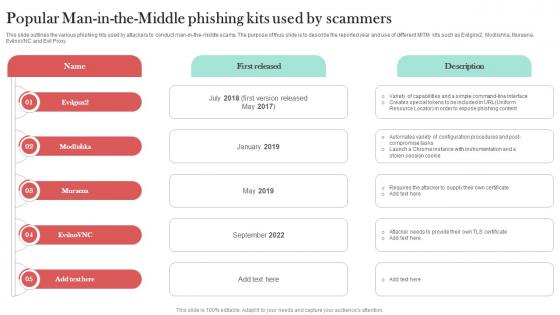
Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT
This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy.
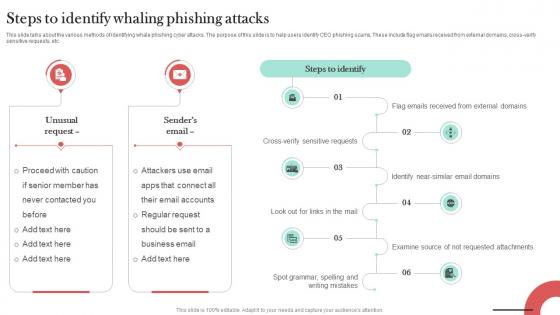
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
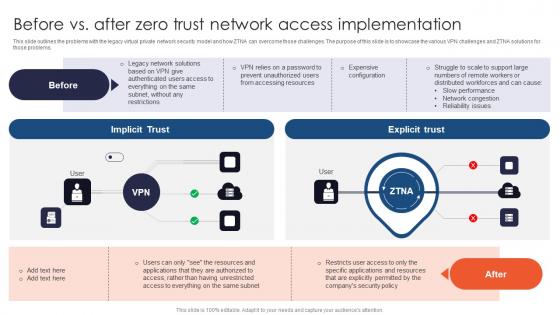
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
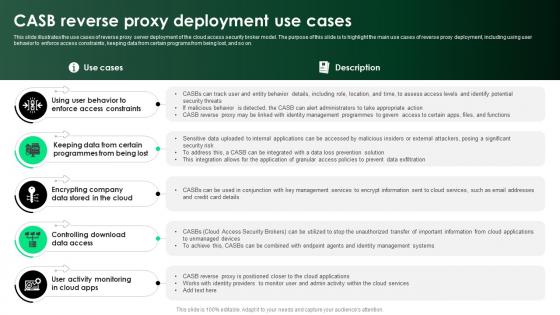
CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases
This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on.
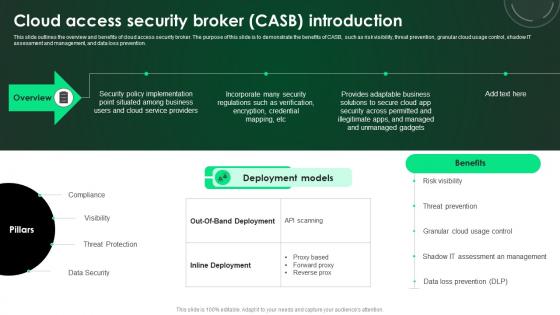
CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention.
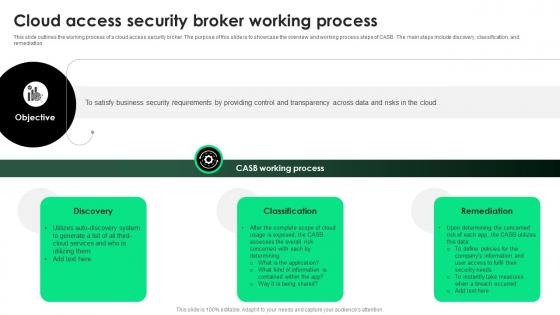
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.

Create A Restaurant Marketing Introduction Of Marketing Plan To Determine
This slide shows the complete overview of the marketing plan. This slide aims to make the target audience aware by creating an effective or successful marketing plan. It includes parameters such as marketing focus, elements, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Create A Restaurant Marketing Introduction Of Marketing Plan To Determine is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Create A Restaurant Marketing Introduction Of Marketing Plan To Determine and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows the complete overview of the marketing plan. This slide aims to make the target audience aware by creating an effective or successful marketing plan. It includes parameters such as marketing focus, elements, etc.

Create A Restaurant Marketing Plan Email Marketing Plan For Restaurant
This slide shows various email promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are sending welcome emails, weekly specials offers, etc. Presenting this PowerPoint presentation, titled Create A Restaurant Marketing Plan Email Marketing Plan For Restaurant, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Create A Restaurant Marketing Plan Email Marketing Plan For Restaurant. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Create A Restaurant Marketing Plan Email Marketing Plan For Restaurant that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide shows various email promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are sending welcome emails, weekly specials offers, etc.

Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain
This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.If you are looking for a format to display your unique thoughts, then the professionally designed Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.

Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain
This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.Presenting this PowerPoint presentation, titled Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.

Applications Of Data Integration In Various Sectors Data Integration Strategies For Business
This slide discusses the application of data integration in the real world. The purpose of this slide is to highlight the various fields such as retail, marketing, finance, healthcare, and IoT where data integration plays a significant role. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Applications Of Data Integration In Various Sectors Data Integration Strategies For Business a try. Our experts have put a lot of knowledge and effort into creating this impeccable Applications Of Data Integration In Various Sectors Data Integration Strategies For Business. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the application of data integration in the real world. The purpose of this slide is to highlight the various fields such as retail, marketing, finance, healthcare, and IoT where data integration plays a significant role.
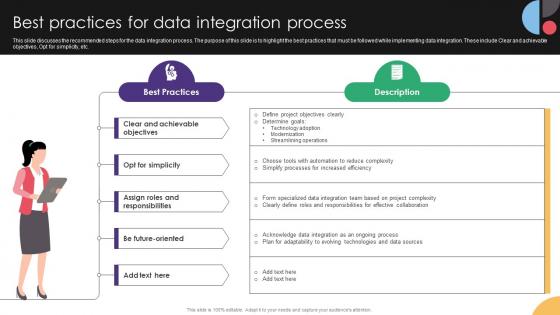
Best Practices For Data Integration Process Data Integration Strategies For Business
This slide discusses the recommended steps for the data integration process. The purpose of this slide is to highlight the best practices that must be followed while implementing data integration. These include Clear and achievable objectives, Opt for simplicity, etc. Present like a pro with Best Practices For Data Integration Process Data Integration Strategies For Business. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses the recommended steps for the data integration process. The purpose of this slide is to highlight the best practices that must be followed while implementing data integration. These include Clear and achievable objectives, Opt for simplicity, etc.

Different Approaches To Execute Data Integration Data Integration Strategies For Business
This slide highlights the approaches and techniques to implement data integration. The purpose of this slide is to discuss the different integration methods to facilitate an automated data integration process for connecting and routing data from a source system to a target system. This Different Approaches To Execute Data Integration Data Integration Strategies For Business is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Different Approaches To Execute Data Integration Data Integration Strategies For Business features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights the approaches and techniques to implement data integration. The purpose of this slide is to discuss the different integration methods to facilitate an automated data integration process for connecting and routing data from a source system to a target system.
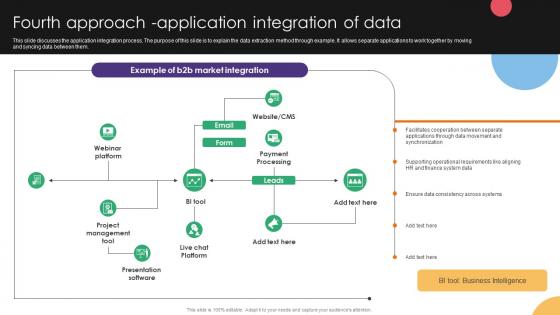
Fourth Approach Application Integration Of Data Integration Strategies For Business
This slide discusses the application integration process. The purpose of this slide is to explain the data extraction method through example. It allows separate applications to work together by moving and syncing data between them. Presenting this PowerPoint presentation, titled Fourth Approach Application Integration Of Data Integration Strategies For Business, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Fourth Approach Application Integration Of Data Integration Strategies For Business. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Fourth Approach Application Integration Of Data Integration Strategies For Business that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the application integration process. The purpose of this slide is to explain the data extraction method through example. It allows separate applications to work together by moving and syncing data between them.

Generic Architecture Of Data Integration Process Data Integration Strategies For Business
This slide showcases the architectural structure of data integration. The purpose of this slide is to give an overview of the architecture of data integration with their component, like online applications, external data sources, mobile, cloud, and transaction logs. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Generic Architecture Of Data Integration Process Data Integration Strategies For Business to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Generic Architecture Of Data Integration Process Data Integration Strategies For Business. This slide showcases the architectural structure of data integration. The purpose of this slide is to give an overview of the architecture of data integration with their component, like online applications, external data sources, mobile, cloud, and transaction logs.

Impact Of Data Integration Process On Organizations Data Integration Strategies For Business
This slide discusses the effects of the data integration process in an organization. The purpose of this slide is to explain the impact of data integration in terms of decision-making, cost efficiency, time-saving, increasing productivity, customer satisfaction, and competitive advancement. Do you know about Slidesgeeks Impact Of Data Integration Process On Organizations Data Integration Strategies For Business These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide discusses the effects of the data integration process in an organization. The purpose of this slide is to explain the impact of data integration in terms of decision-making, cost efficiency, time-saving, increasing productivity, customer satisfaction, and competitive advancement.

Issue Associated With Data Integration Process Data Integration Strategies For Business
This slide discusses the basic issues that need to be considered during data integration. The purpose of this slide is to explain the issues of data integration that are schema integration, redundancy detection, and resolution of data value conflicts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Issue Associated With Data Integration Process Data Integration Strategies For Business a try. Our experts have put a lot of knowledge and effort into creating this impeccable Issue Associated With Data Integration Process Data Integration Strategies For Business. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the basic issues that need to be considered during data integration. The purpose of this slide is to explain the issues of data integration that are schema integration, redundancy detection, and resolution of data value conflicts.

Types Of Data Integration Data Consolidation Data Integration Strategies For Business
This slide discusses data consolidation, a type of data integration. The purpose of this slide is to explain the functioning of data consolidation, which involves eliminating redundancies, correcting errors, storing in a centralized repository, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Types Of Data Integration Data Consolidation Data Integration Strategies For Business and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide discusses data consolidation, a type of data integration. The purpose of this slide is to explain the functioning of data consolidation, which involves eliminating redundancies, correcting errors, storing in a centralized repository, etc.

Various Benefits Of Data Integration Process Data Integration Strategies For Business
This slide highlights the various benefits of data integration. The purpose of this slide is to discuss the various advantages of data integration to businesses. These include high-quality data, reduced data silos, enhanced data user efficiency, etc. This Various Benefits Of Data Integration Process Data Integration Strategies For Business is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Various Benefits Of Data Integration Process Data Integration Strategies For Business features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights the various benefits of data integration. The purpose of this slide is to discuss the various advantages of data integration to businesses. These include high-quality data, reduced data silos, enhanced data user efficiency, etc.
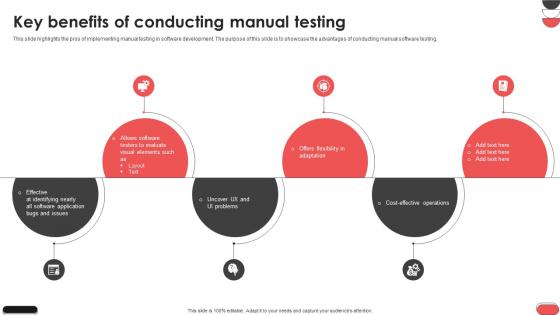
Key Benefits Of Conducting Manual Testing Gray Box Testing Best Practices
This slide highlights the pros of implementing manual testing in software development. The purpose of this slide is to showcase the advantages of conducting manual software testing. If you are looking for a format to display your unique thoughts, then the professionally designed Key Benefits Of Conducting Manual Testing Gray Box Testing Best Practices is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Benefits Of Conducting Manual Testing Gray Box Testing Best Practices and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the pros of implementing manual testing in software development. The purpose of this slide is to showcase the advantages of conducting manual software testing.

Google Ads Categories Steps To Use GKP Tool For Keyword Searching Related To Business MKT SS V
This slide covers process to use keyword planner tool to help users to find most search words on Google to improve campaign performance. The purpose of this template is provide a guide to users to leverage Google keyword planner to improve search volumes. It includes steps starting from opening keyword planner, setting up account, etc. The Google Ads Categories Steps To Use GKP Tool For Keyword Searching Related To Business MKT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers process to use keyword planner tool to help users to find most search words on Google to improve campaign performance. The purpose of this template is provide a guide to users to leverage Google keyword planner to improve search volumes. It includes steps starting from opening keyword planner, setting up account, etc.
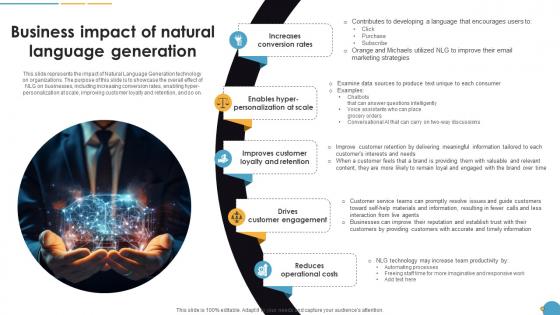
Business Impact Of Natural Language Generation Natural Language Automation
This slide represents the impact of Natural Language Generation technology on organizations. The purpose of this slide is to showcase the overall effect of NLG on businesses, including increasing conversion rates, enabling hyper-personalization at scale, improving customer loyalty and retention, and so on. Present like a pro with Business Impact Of Natural Language Generation Natural Language Automation. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the impact of Natural Language Generation technology on organizations. The purpose of this slide is to showcase the overall effect of NLG on businesses, including increasing conversion rates, enabling hyper-personalization at scale, improving customer loyalty and retention, and so on.
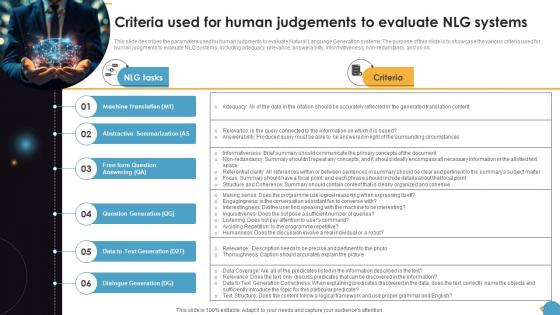
Criteria Used For Human Judgements To Evaluate NLG Systems Natural Language Automation
This slide describes the parameters used for human judgments to evaluate Natural Language Generation systems. The purpose of this slide is to showcase the various criteria used for human judgments to evaluate NLG systems, including adequacy, relevance, answerability, informativeness, non-redundancy, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Criteria Used For Human Judgements To Evaluate NLG Systems Natural Language Automation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Criteria Used For Human Judgements To Evaluate NLG Systems Natural Language Automation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide describes the parameters used for human judgments to evaluate Natural Language Generation systems. The purpose of this slide is to showcase the various criteria used for human judgments to evaluate NLG systems, including adequacy, relevance, answerability, informativeness, non-redundancy, and so on.
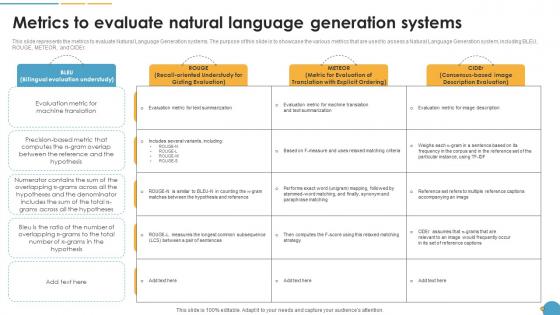
Metrics To Evaluate Natural Language Generation Systems Natural Language Automation
This slide represents the metrics to evaluate Natural Language Generation systems. The purpose of this slide is to showcase the various metrics that are used to assess a Natural Language Generation system, including BLEU, ROUGE, METEOR, and CIDEr Presenting this PowerPoint presentation, titled Metrics To Evaluate Natural Language Generation Systems Natural Language Automation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Metrics To Evaluate Natural Language Generation Systems Natural Language Automation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Metrics To Evaluate Natural Language Generation Systems Natural Language Automation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the metrics to evaluate Natural Language Generation systems. The purpose of this slide is to showcase the various metrics that are used to assess a Natural Language Generation system, including BLEU, ROUGE, METEOR, and CIDEr.
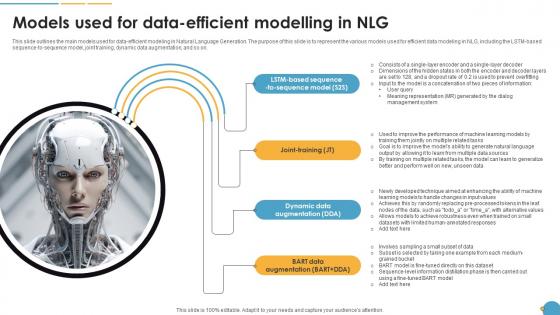
Models Used For DAT Efficient Modelling In NLG Natural Language Automation
This slide outlines the main models used for data-efficient modeling in Natural Language Generation. The purpose of this slide is to represent the various models used for efficient data modeling in NLG, including the LSTM-based sequence-to-sequence model, joint training, dynamic data augmentation, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Models Used For DAT Efficient Modelling In NLG Natural Language Automation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Models Used For DAT Efficient Modelling In NLG Natural Language Automation. This slide outlines the main models used for data-efficient modeling in Natural Language Generation. The purpose of this slide is to represent the various models used for efficient data modeling in NLG, including the LSTM-based sequence-to-sequence model, joint training, dynamic data augmentation, and so on.

Primary Transformer Models In Natural Language Generation Natural Language Automation
This slide represents the primary models of transformers used in Natural Language Generation. The purpose of this slide is to showcase the various transformer models, including generative pre-trained transformers, bidirectional encoder representations from transformers, and XLNet. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Primary Transformer Models In Natural Language Generation Natural Language Automation a try. Our experts have put a lot of knowledge and effort into creating this impeccable Primary Transformer Models In Natural Language Generation Natural Language Automation. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the primary models of transformers used in Natural Language Generation. The purpose of this slide is to showcase the various transformer models, including generative pre-trained transformers, bidirectional encoder representations from transformers, and XLNet.
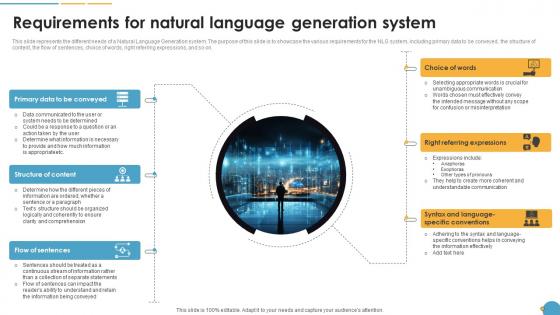
Requirements For Natural Language Generation System Natural Language Automation
This slide represents the different needs of a Natural Language Generation system. The purpose of this slide is to showcase the various requirements for the NLG system, including primary data to be conveyed, the structure of content, the flow of sentences, choice of words, right referring expressions, and so on. Present like a pro with Requirements For Natural Language Generation System Natural Language Automation. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the different needs of a Natural Language Generation system. The purpose of this slide is to showcase the various requirements for the NLG system, including primary data to be conveyed, the structure of content, the flow of sentences, choice of words, right referring expressions, and so on.
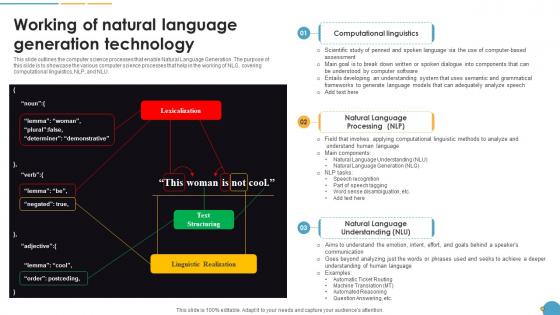
Working Of Natural Language Generation Technology Natural Language Automation
This slide outlines the computer science processes that enable Natural Language Generation. The purpose of this slide is to showcase the various computer science processes that help in the working of NLG, covering computational linguistics, NLP, and NLU. If you are looking for a format to display your unique thoughts, then the professionally designed Working Of Natural Language Generation Technology Natural Language Automation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Working Of Natural Language Generation Technology Natural Language Automation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the computer science processes that enable Natural Language Generation. The purpose of this slide is to showcase the various computer science processes that help in the working of NLG, covering computational linguistics, NLP, and NLU.

IoT Automation System Architecture Working Utilizing Smart Appliances IoT SS V
This slide provides an overview of the working of an IOT-based automation system. The slide includes basic setup, cloud connection, real-time monitoring, IIFTT integration and home sensors. If you are looking for a format to display your unique thoughts, then the professionally designed IoT Automation System Architecture Working Utilizing Smart Appliances IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IoT Automation System Architecture Working Utilizing Smart Appliances IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides an overview of the working of an IOT-based automation system. The slide includes basic setup, cloud connection, real-time monitoring, IIFTT integration and home sensors.
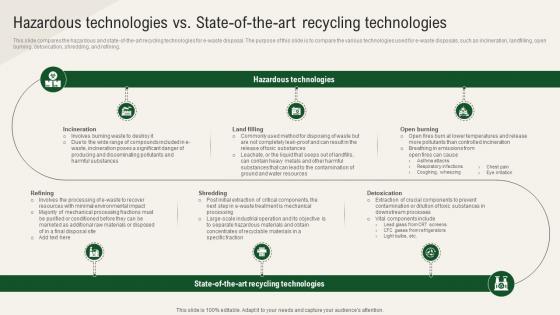
Solar Computing IT Hazardous Technologies Vs State Of The Art Recycling Technologies
This slide compares the hazardous and state-of-the-art recycling technologies for e-waste disposal. The purpose of this slide is to compare the various technologies used for e-waste disposals, such as incineration, landfilling, open burning, detoxication, shredding, and refining. This Solar Computing IT Hazardous Technologies Vs State Of The Art Recycling Technologies is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Solar Computing IT Hazardous Technologies Vs State Of The Art Recycling Technologies features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide compares the hazardous and state-of-the-art recycling technologies for e-waste disposal. The purpose of this slide is to compare the various technologies used for e-waste disposals, such as incineration, landfilling, open burning, detoxication, shredding, and refining.

Solar Computing IT Industrial Efforts And Restrictions Of Green Computing
This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiatives related to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development. Retrieve professionally designed Solar Computing IT Industrial Efforts And Restrictions Of Green Computing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiatives related to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development.

Customizing The Salon Experience Financial Highlights And Marketing Mix Of Salon Business Strategy SS V
This slide presents key monetary results of the organization with a detailed description of services provided by the organization. It includes information about company revenue, net income, per session cost, gross profit margin, resource allocation, cost of services, cost of goods sold. The Customizing The Salon Experience Financial Highlights And Marketing Mix Of Salon Business Strategy SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents key monetary results of the organization with a detailed description of services provided by the organization. It includes information about company revenue, net income, per session cost, gross profit margin, resource allocation, cost of services, cost of goods sold.
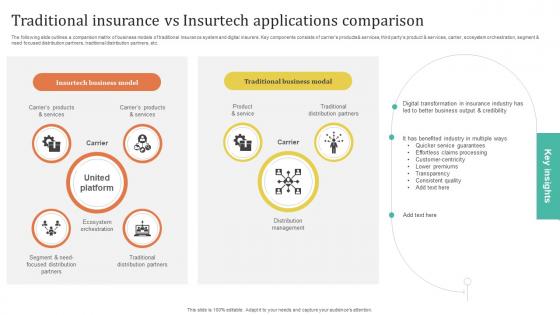
Improving Customer Satisfaction Traditional Insurance Vs Insurtech Applications Comparison
The following slide outlines a comparison matrix of business models of traditional insurance system and digital insurers. Key components consists of carriers products and services, third partys product and services, carrier, ecosystem orchestration, segment and need focused distribution partners, traditional distribution partners, etc. The Improving Customer Satisfaction Traditional Insurance Vs Insurtech Applications Comparison is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide outlines a comparison matrix of business models of traditional insurance system and digital insurers. Key components consists of carriers products and services, third partys product and services, carrier, ecosystem orchestration, segment and need focused distribution partners, traditional distribution partners, etc.

Marketing Growth Strategy Need To Implement Business Growth Strategies Strategy SS V
The following slide outlines the major reasons to introduce business growth strategies. Higher sales, increased market share, diversifying product or service offerings, and strengthening brand awareness are the major reasons that are outlined in slide. Retrieve professionally designed Marketing Growth Strategy Need To Implement Business Growth Strategies Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide outlines the major reasons to introduce business growth strategies. Higher sales, increased market share, diversifying product or service offerings, and strengthening brand awareness are the major reasons that are outlined in slide.
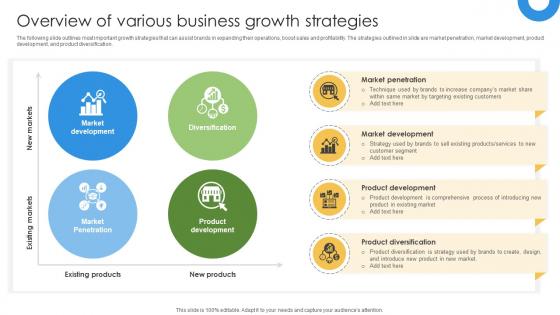
Marketing Growth Strategy Overview Of Various Business Growth Strategies Strategy SS V
The following slide outlines most important growth strategies that can assist brands in expanding their operations, boost sales and profitability. The strategies outlined in slide are market penetration, market development, product development, and product diversification. Presenting this PowerPoint presentation, titled Marketing Growth Strategy Overview Of Various Business Growth Strategies Strategy SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Marketing Growth Strategy Overview Of Various Business Growth Strategies Strategy SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Marketing Growth Strategy Overview Of Various Business Growth Strategies Strategy SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide outlines most important growth strategies that can assist brands in expanding their operations, boost sales and profitability. The strategies outlined in slide are market penetration, market development, product development, and product diversification.

Marketing Growth Strategy Social Media Giveaway Campaign To Increase Customer Strategy SS V
The following slide outlines social media contest that can assist organizations in increasing engagement rate and boosting sales. Information covered in this slide is related to techniques such as product exclusivity, offering multiple prizes, promoting competition, optimizing entry process, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Marketing Growth Strategy Social Media Giveaway Campaign To Increase Customer Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Marketing Growth Strategy Social Media Giveaway Campaign To Increase Customer Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines social media contest that can assist organizations in increasing engagement rate and boosting sales. Information covered in this slide is related to techniques such as product exclusivity, offering multiple prizes, promoting competition, optimizing entry process, etc.
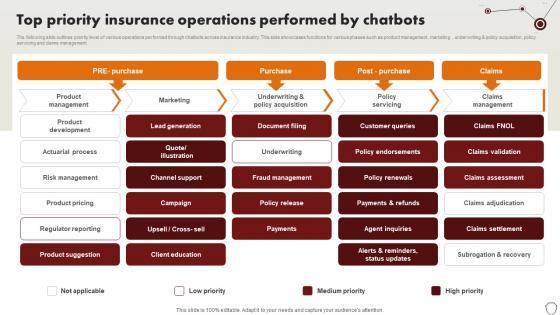
Technology Trends In Online Insurance Top Priority Insurance Operations Performed By Chatbots
The following slide outlines priority level of various operations performed through chatbots across insurance industry. This slide showcases functions for various phases such as product management, marketing , underwriting and policy acquisition, policy servicing and claims management. Retrieve professionally designed Technology Trends In Online Insurance Top Priority Insurance Operations Performed By Chatbots to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide outlines priority level of various operations performed through chatbots across insurance industry. This slide showcases functions for various phases such as product management, marketing , underwriting and policy acquisition, policy servicing and claims management.


 Continue with Email
Continue with Email

 Home
Home


































