System Security
Server Security Checklist In Powerpoint And Google Slides Cpb
Introducing our well designed Server Security Checklist In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Server Security Checklist. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Server Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Security Metrics In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Application Security Metrics In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Security Metrics that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Security Metrics In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Bracketing Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Bracketing Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Bracketing Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Bracketing Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Company In Powerpoint And Google Slides Cpb
Introducing our well designed Security Company In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Security Company Profile Presentation As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Company In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Company Profile Presentation In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Company Profile Presentation In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Security Company that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Company Profile Presentation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Knowledge Framework In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Knowledge Framework In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Knowledge Framework that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Knowledge Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Monitoring Dashboard In Powerpoint And Google Slides Cpb
Introducing our well designed Security Monitoring Dashboard In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Monitoring Dashboard. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Monitoring Dashboard In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Test Plan Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Test Plan Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Test Plan Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Test Plan Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Sphere Security In Powerpoint And Google Slides Cpb
Introducing our well designed Sphere Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Sphere Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Sphere Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Pick Lines In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Pick Lines In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Pick Lines. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Pick Lines In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Pyramid Application Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Pyramid Application Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Pyramid Application Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Pyramid Application Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Pattern Documents In Powerpoint And Google Slides Cpb
Introducing our well designed Security Pattern Documents In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Pattern Documents. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Pattern Documents In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Customer Engagement Data Security In Powerpoint And Google Slides Cpb
Introducing our well designed Customer Engagement Data Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Customer Engagement Data Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Customer Engagement Data Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Advisory Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Advisory Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Advisory Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Advisory Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cybersecurity Security Incident Investigation that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Devsecops Security Checklist In Powerpoint And Google Slides Cpb
Introducing our well designed Devsecops Security Checklist In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Devsecops Security Checklist. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Devsecops Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wireless Security Presentation In Powerpoint And Google Slides Cpb
Introducing our well designed Wireless Security Presentation In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Wireless Security Presentation. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Wireless Security Presentation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Wlan Security Ppt In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Wlan Security Ppt In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wlan Security Ppt that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wlan Security Ppt In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Introduction Application Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Introduction Application Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Introduction Application Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Introduction Application Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Chip Security Flaw In Powerpoint And Google Slides Cpb
Introducing our well-designed Chip Security Flaw In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Chip Security Flaw. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Chip Security Flaw In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Computer Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Computer Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Computer Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Policy In Powerpoint And Google Slides Cpb
Introducing our well designed Information Security Policy In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Policy. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Policy In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Facial Recognition Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Facial Recognition Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Facial Recognition Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Facial Recognition Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Website Safe Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Website Safe Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Website Safe Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Website Safe Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Budget Security Robot Technology In Powerpoint And Google Slides Cpb
Introducing our well-designed Budget Security Robot Technology In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Budget Security Robot Technology. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Budget Security Robot Technology In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Best Cyber Security World In Powerpoint And Google Slides Cpb
Introducing our well designed Best Cyber Security World In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Cyber Security World. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Cyber Security World In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Software Security Testing Harnessing The World Of Ethical Ppt Example
This slide highlights the challenges faced during the implementation of security testing such as the velocity of software development, weaknesses in the code, etc. Retrieve professionally designed Software Security Testing Harnessing The World Of Ethical Ppt Example to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the challenges faced during the implementation of security testing such as the velocity of software development, weaknesses in the code, etc.

Best Practices For Tokenization In Data Security PPT Slides
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Boost your pitch with our creative Best Practices For Tokenization In Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
Main Features For Robust Application Security Testing Ppt Powerpoint Icons
This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Are you searching for a Main Features For Robust Application Security Testing Ppt Powerpoint Icons that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Features For Robust Application Security Testing Ppt Powerpoint Icons from Slidegeeks today. This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Agenda Global Security Industry Report PPT PowerPoint IR SS V
Find a pre-designed and impeccable Agenda Global Security Industry Report PPT PowerPoint IR SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Global Security Industry Report PPT PowerPoint IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
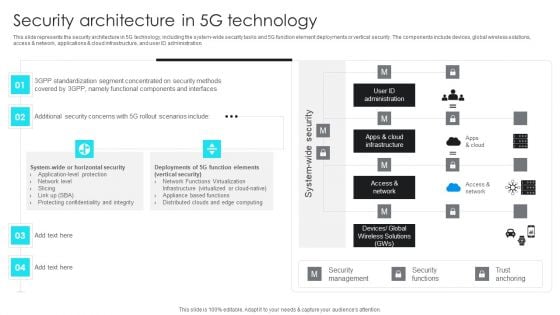
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
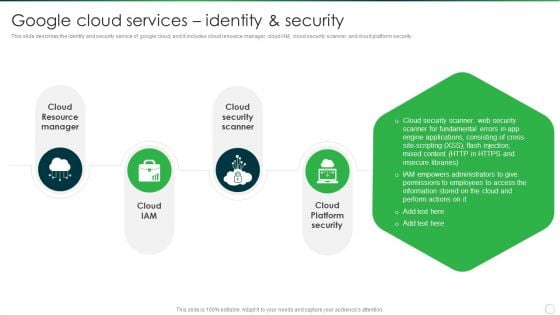
Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
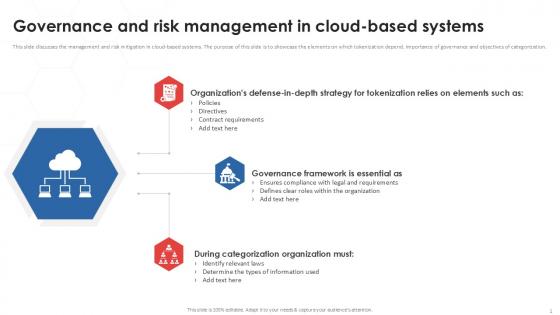
Governance And Risk Tokenization Strategies For Data Security PPT Sample
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Boost your pitch with our creative Governance And Risk Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.
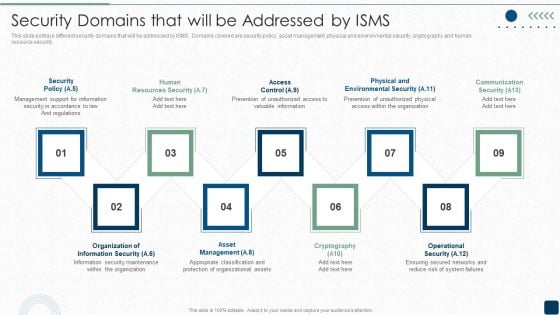
Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
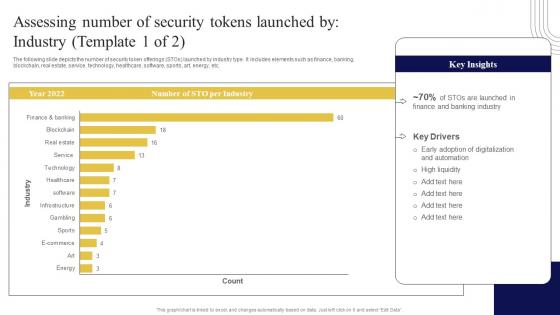
Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf
The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Want to ace your presentation in front of a live audience Our Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
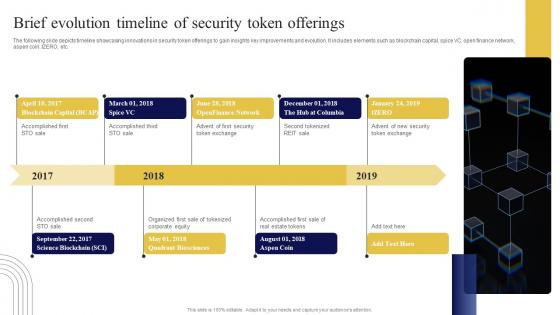
Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf
The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc.
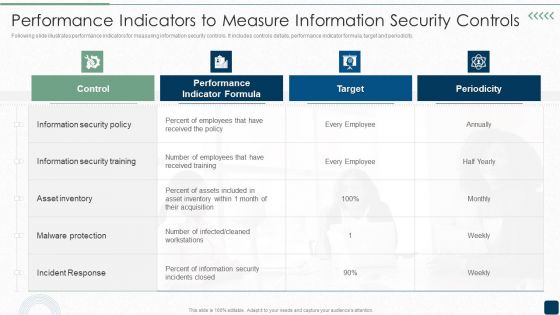
Performance Indicators To Measure Information Security Controls Brochure PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Brochure PDF bundle. Topics like Information Security, Security Training, Malware Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
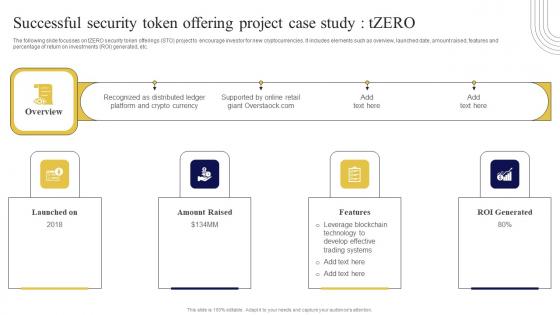
Successful Security Token Offering Exploring Investment Opportunities Background Pdf
The following slide focusses on tZERO security token offerings STO project to encourage investor for new cryptocurrencies. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Successful Security Token Offering Exploring Investment Opportunities Background Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Successful Security Token Offering Exploring Investment Opportunities Background Pdf. The following slide focusses on tZERO security token offerings STO project to encourage investor for new cryptocurrencies. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
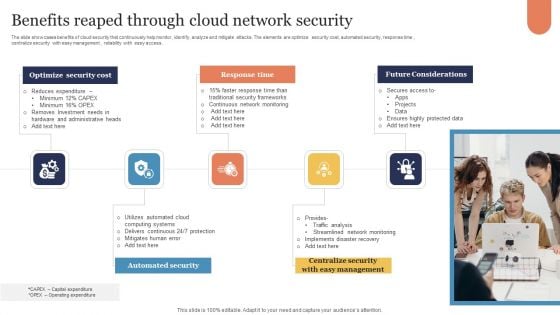
Benefits Reaped Through Cloud Network Security Sample PDF
The slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting Benefits Reaped Through Cloud Network Security Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Optimize Security Cost, Response Time, Future Considerations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
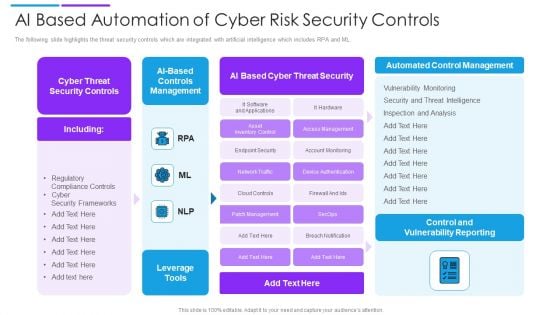
AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
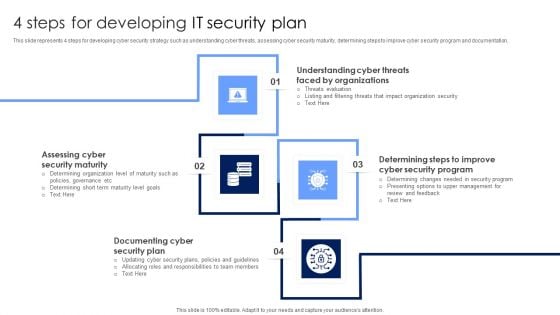
4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
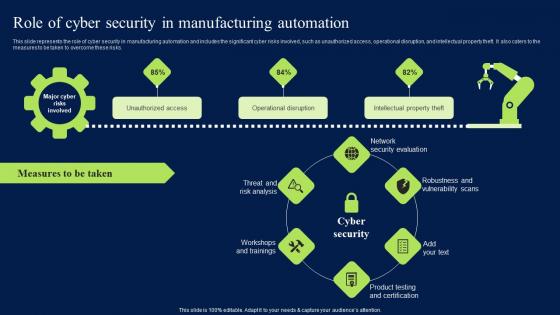
Role Of Cyber Security In Manufacturing Automation Clipart PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks.
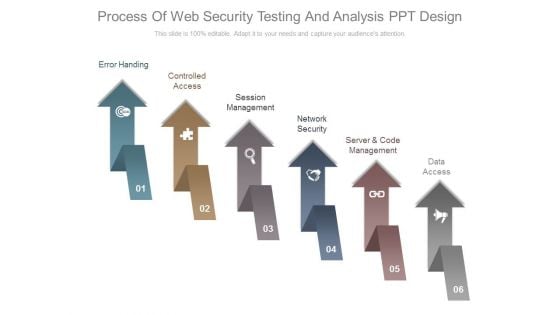
Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.

It Security Risk Management Ppt Powerpoint Presentation Outline Guidelines Cpb
This is a it security risk management ppt powerpoint presentation outline guidelines cpb. This is a five stage process. The stages in this process are it security risk management.

Table Of Contents For Application Security Testing Ppt Powerpoint Designs
The Table Of Contents For Application Security Testing Ppt Powerpoint Designs is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Our Table Of Contents For Application Security Testing Ppt Powerpoint Designs are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
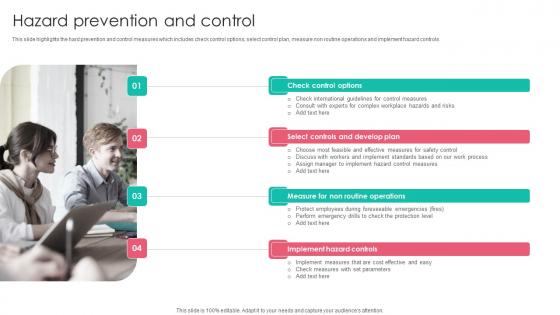
Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls. This Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls.
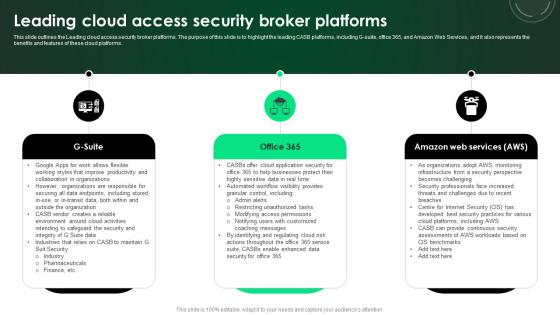
CASB 2 0 IT Leading Cloud Access Security Broker Platforms
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. There are so many reasons you need a CASB 2 0 IT Leading Cloud Access Security Broker Platforms. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms.
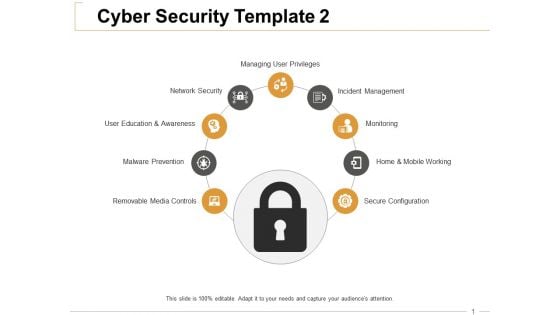
Cyber Security Monitoring Ppt PowerPoint Presentation Inspiration Objects
This is a cyber security monitoring ppt powerpoint presentation inspiration objects. This is a nine stage process. The stages in this process are network security, malware prevention, monitoring, incident management, managing user privileges.
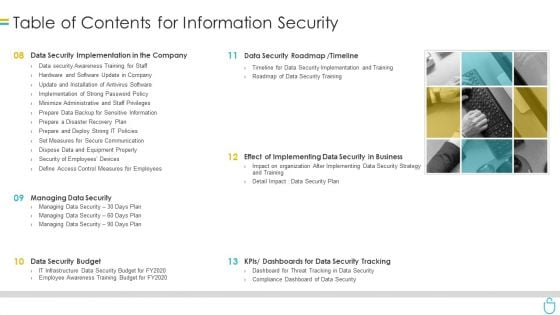
Table Of Contents For Information Security Ppt Styles Outline PDF
Presenting table of contents for information security ppt styles outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security implementation, data security roadmap, data security budget, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
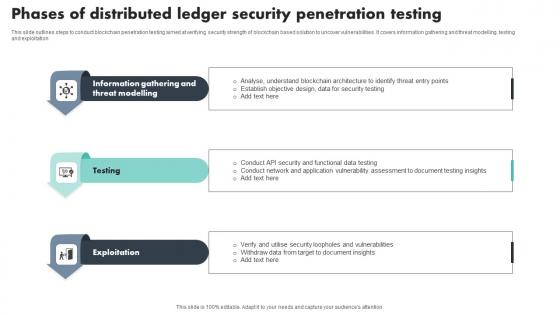
Phases Of Distributed Ledger Security Penetration Testing Download Pdf
This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation Showcasing this set of slides titled Phases Of Distributed Ledger Security Penetration Testing Download Pdf The topics addressed in these templates are Information Gathering, Threat Modelling, Exploitation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation

Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
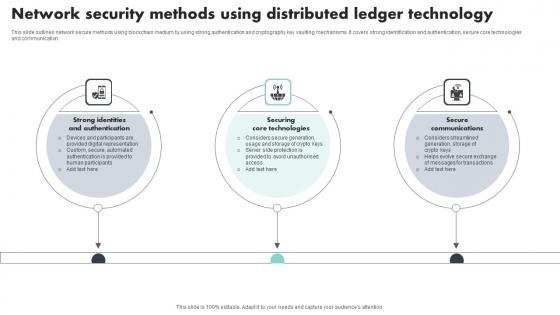
Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication
6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Essential Elements Of Security Monitoring Plan Background PDF
Deliver an awe inspiring pitch with this creative essential elements of security monitoring plan background pdf bundle. Topics like critical infrastructure, application security, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Milestones In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Milestones In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Milestones that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Milestones In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































