System Security
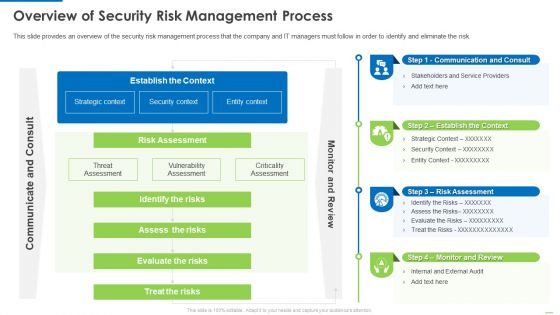
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Strategic Planning Process For CPS Ppt Slides Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver and pitch your topic in the best possible manner with this Security Strategic Planning Process For CPS Ppt Slides Icons PDF. Use them to share invaluable insights on Business Strategy, Technology Roadmap, Environmental Trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
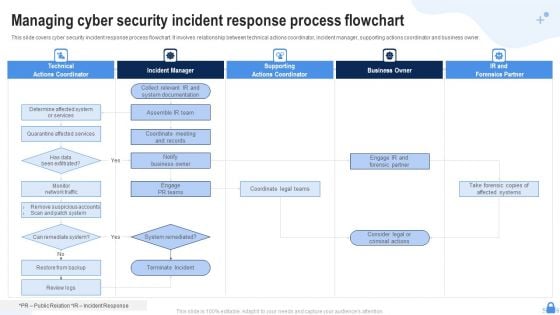
Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF
This slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Presenting Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Technical Actions Coordinator, Incident Manager, Supporting Actions Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
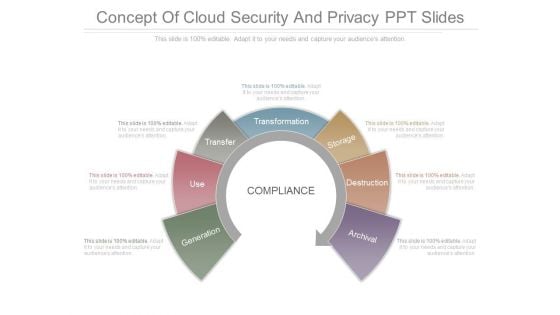
Concept Of Cloud Security And Privacy Ppt Slides
This is a concept of cloud security and privacy ppt slides. This is a seven stage process. The stages in this process are generation, use, transfer, transformation, storage, destruction, archival, compliance.
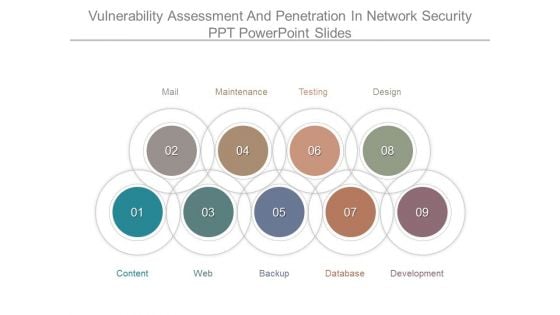
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
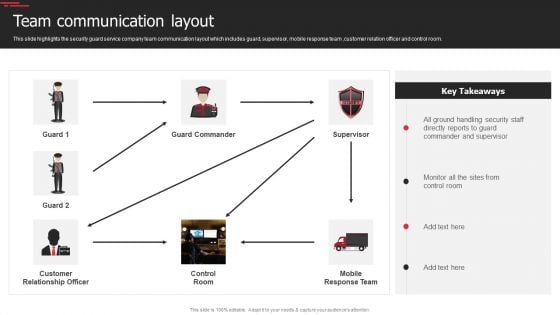
Security Agency Business Profile Team Communication Layout Topics PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team ,customer relation officer and control room. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Team Communication Layout Topics PDF. Use them to share invaluable insights on Customer Relationship Officer, Mobile Response Team, Supervisor and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Manpower Corporate Security Business Profile Team Communication Layout Icons PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team , customer relation officer and control room. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Team Communication Layout Icons PDF bundle. Topics like Customer Relationship Officer, Supervisor, Mobile Response Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.
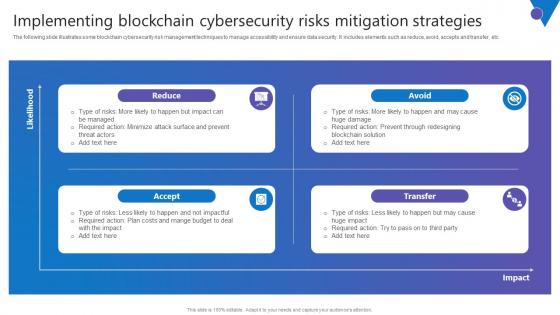
Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc.
Security Patch Management Best Practices Ppt PowerPoint Presentation Pictures Infographics
This is a security patch management best practices ppt powerpoint presentation pictures infographics. This is a three stage process. The stages in this process are patch management process, patch management procedure, patch management approach.
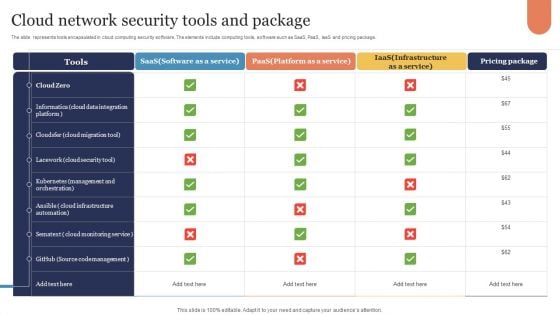
Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
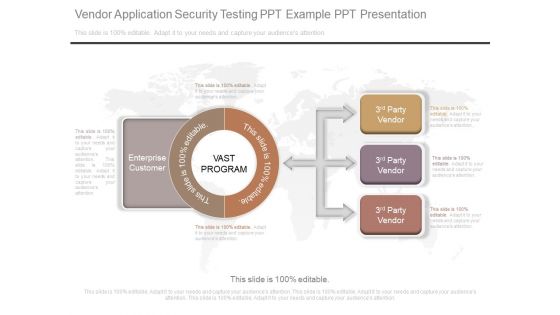
Vendor Application Security Testing Ppt Example Ppt Presentation
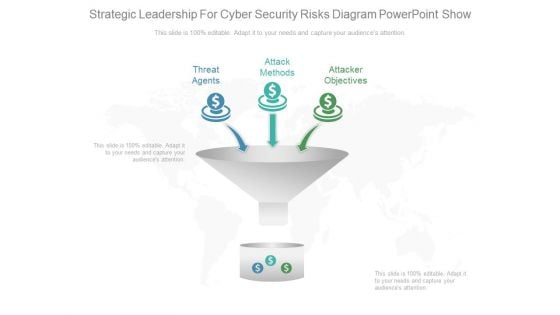
Strategic Leadership For Cyber Security Risks Diagram Powerpoint Show
This is a strategic leadership for cyber security risks diagram powerpoint show. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
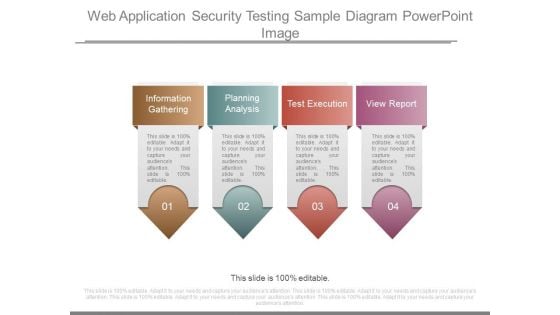
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.
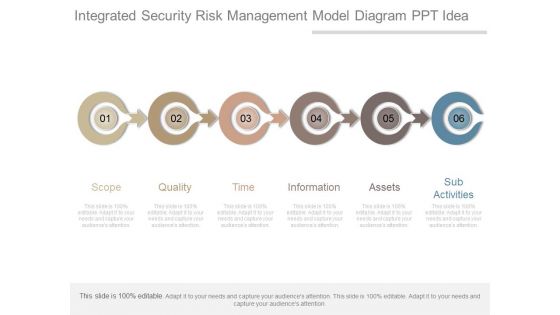
Integrated Security Risk Management Model Diagram Ppt Idea
This is a integrated security risk management model diagram ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.
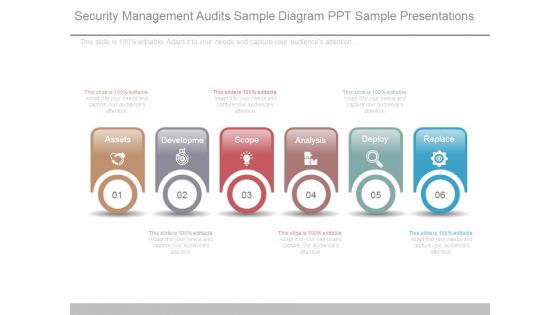
Security Management Audits Sample Diagram Ppt Sample Presentations
This is a security management audits sample diagram ppt sample presentations. This is a six stage process. The stages in this process are assets, development, scope, analysis, deploy, replace.

Security Incident Response Plan Template Ppt Design Templates
This is a security incident response plan template ppt design templates. This is a three stage process. The stages in this process are prepare, detection and analysis, post incident activity.
Security Governance Icon Ppt PowerPoint Presentation Layouts Rules
This is a security governance icon ppt powerpoint presentation layouts rules. This is a four stage process. The stages in this process are risk management icon, governance icon, compliance icon.
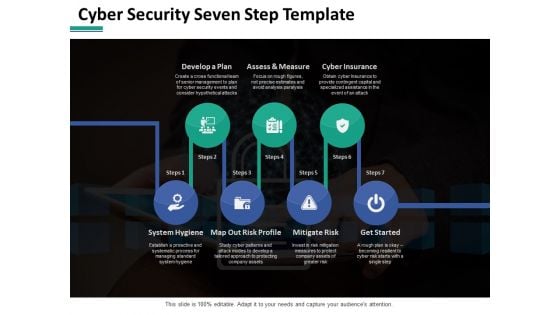
Cyber Security Seven Step Ppt PowerPoint Presentation Infographic Template Maker
This is a cyber security seven step ppt powerpoint presentation infographic template maker. This is a seven stage process. The stages in this process are business, management, planning, strategy, marketing.
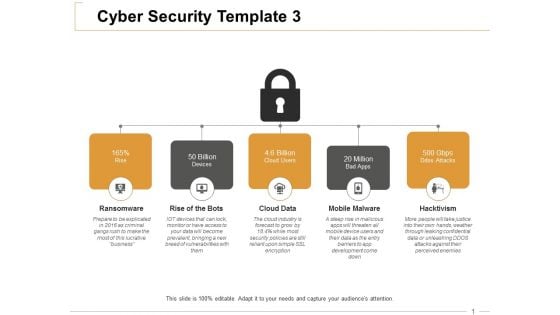
Cyber Security Ransomware Ppt PowerPoint Presentation Summary Graphics Design
This is a cyber security ransomware ppt powerpoint presentation summary graphics design. This is a five stage process. The stages in this process are business, management, planning, strategy, marketing.
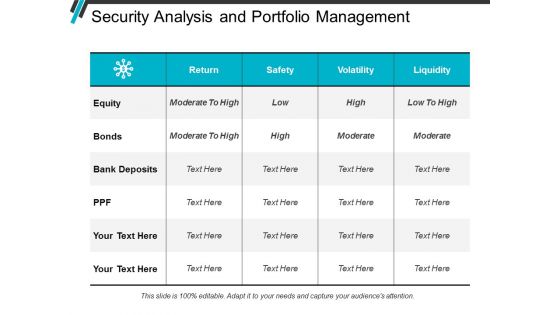
Security Analysis And Portfolio Management Ppt PowerPoint Presentation Styles Outfit
This is a security analysis and portfolio management ppt powerpoint presentation styles outfit. This is a four stage process. The stages in this process are mutual funds, funds to buy, investment slide.

Global Peace And Security Ppt PowerPoint Presentation Pictures Structure
This is a global peace and security ppt powerpoint presentation pictures structure. This is a three stage process. The stages in this process are world peace, peace on earth, peaceful environment.

No Entry Security Gate Ppt PowerPoint Presentation Gallery Graphics Tutorials
This is a no entry security gate ppt powerpoint presentation gallery graphics tutorials. This is a four stage process. The stages in this process are Restriction, Barrier To Entry, No Entry.
Security Fence Entry Gate Ppt PowerPoint Presentation Summary Sample
This is a security fence entry gate ppt powerpoint presentation summary sample. This is a four stage process. The stages in this process are Restriction, Barrier To Entry, No Entry.

International Security Market Highlights Ppt PowerPoint Presentation File Graphics Example
This is a international security market highlights ppt powerpoint presentation file graphics example. This is a three stage process. The stages in this process are location, information, geography, management, strategy.
Security Alert Vector Icon Ppt PowerPoint Presentation Summary Gallery
This is a security alert vector icon ppt powerpoint presentation summary gallery. This is a five stage process. The stages in this process are risk management, governance icon, compliance icon.

International Security Market Highlights Ppt PowerPoint Presentation Professional Model
This is a international security market highlights ppt powerpoint presentation professional model. This is a three stage process. The stages in this process are location, information, geography, management, strategy.
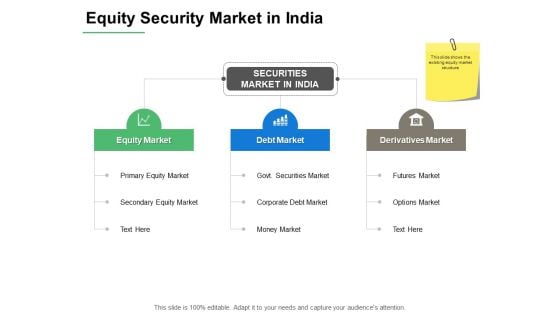
Equity Security Market In India Ppt PowerPoint Presentation Pictures Infographics
This is a equity security market in india ppt powerpoint presentation pictures infographics. This is a three stage process. The stages in this process are marketing, business, management, planning, strategy.
Roadmap For Security Camera Services One Pager Sample Example Document
Presenting you an exemplary Roadmap For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Roadmap For Security Camera Services One Pager Sample Example Document brilliant piece now.
Security Camera Services About Us One Pager Sample Example Document
Presenting you an exemplary Security Camera Services About Us One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Security Camera Services About Us One Pager Sample Example Document brilliant piece now.
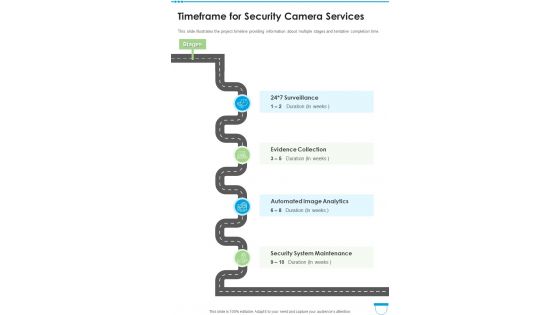
Timeframe For Security Camera Services One Pager Sample Example Document
This slide illustrates the project timeline providing information about multiple stages and tentative completion time. Presenting you an exemplary Timeframe For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeframe For Security Camera Services One Pager Sample Example Document brilliant piece now.
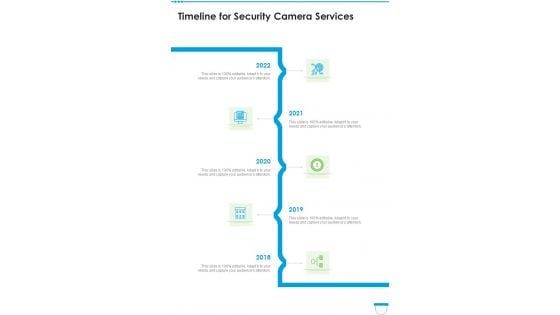
Timeline For Security Camera Services One Pager Sample Example Document
Presenting you an exemplary Timeline For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Security Camera Services One Pager Sample Example Document brilliant piece now.
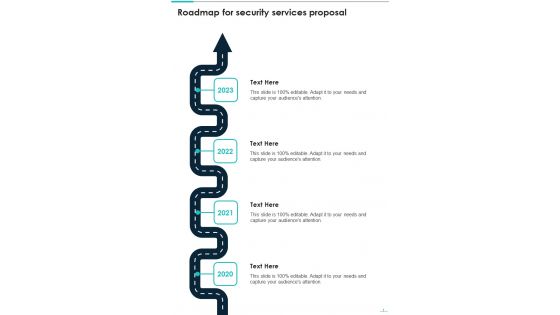
Roadmap For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Roadmap For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Roadmap For Security Services Proposal One Pager Sample Example Document brilliant piece now.
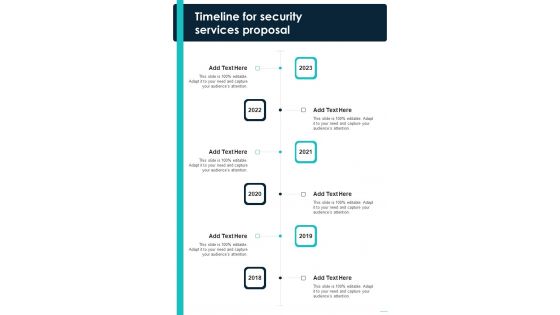
Timeline For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Security Services Proposal One Pager Sample Example Document brilliant piece now.
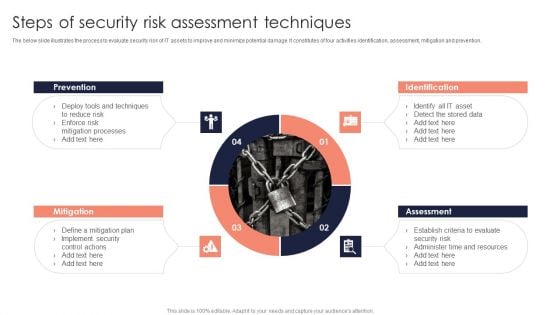
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Programs Ppt PowerPoint Presentation Ideas Design Inspiration Cpb
Presenting this set of slides with name information security programs ppt powerpoint presentation ideas design inspiration cpb. This is an editable Powerpoint eleven stages graphic that deals with topics like information security programs to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Project Security Administration IT Diagrams PDF
This is a agenda for project security administration it diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, management, implemented, security center, improvement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
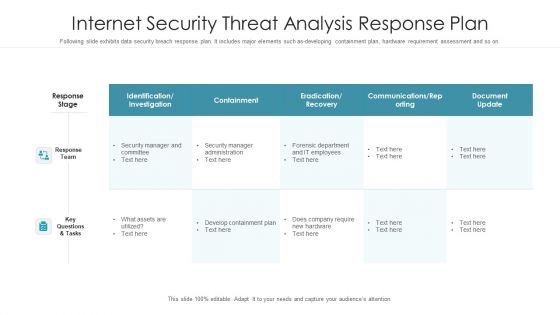
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

One Page Internet Security Management Sheet PDF Document PPT Template
Presenting you an exemplary One Page Internet Security Management Sheet PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Internet Security Management Sheet PDF Document PPT Template Download now.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
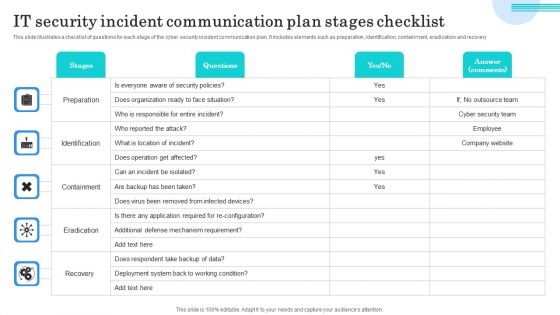
IT Security Incident Communication Plan Stages Checklist Topics PDF
This slide illustrates a checklist of questions for each stage of the cyber security incident communication plan. It includes elements such as preparation, identification, containment, eradication and recovery. Showcasing this set of slides titled IT Security Incident Communication Plan Stages Checklist Topics PDF. The topics addressed in these templates are Preparation, Identification, Containment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
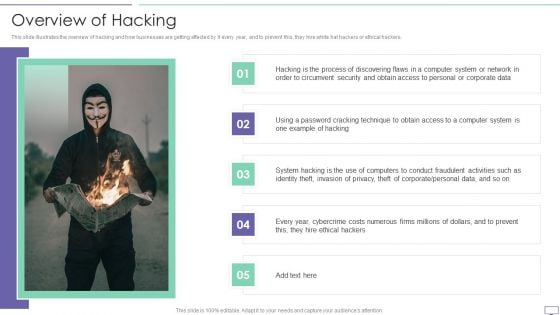
IT Security Hacker Overview Of Hacking Sample PDF
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers.Deliver an awe inspiring pitch with this creative IT Security Hacker Overview Of Hacking Sample PDF bundle. Topics like Process Of Discovering, Circumvent Security, Example Of Hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
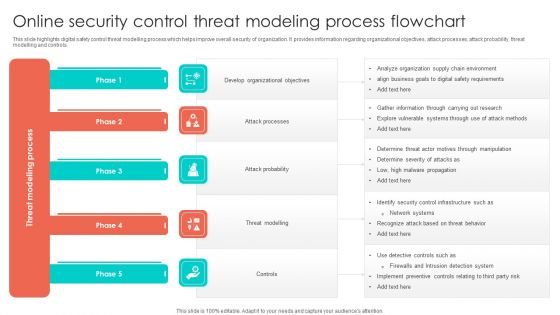
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
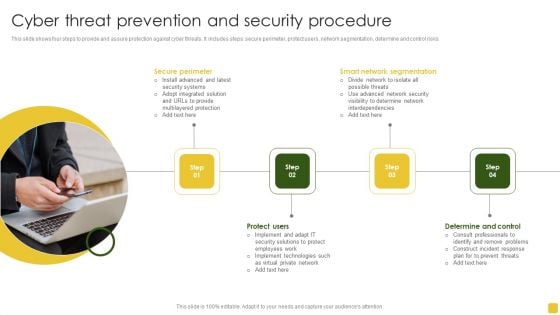
Cyber Threat Prevention And Security Procedure Elements PDF
This slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Presenting Cyber Threat Prevention And Security Procedure Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Control, Smart Network Segmentation, Secure Perimeter. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
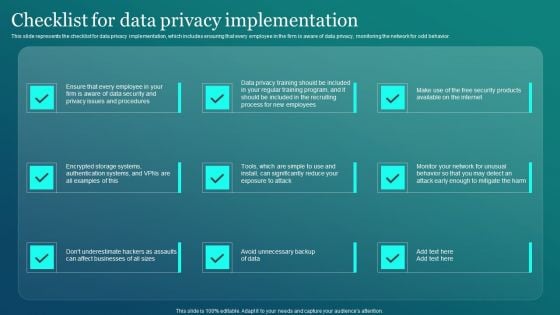
Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
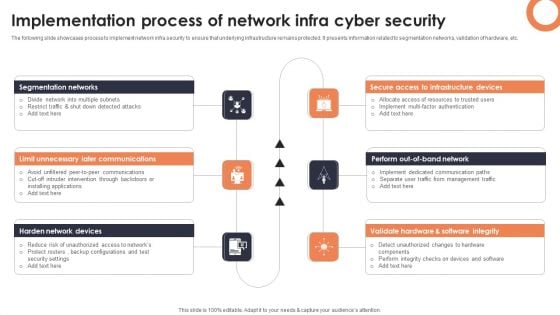
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
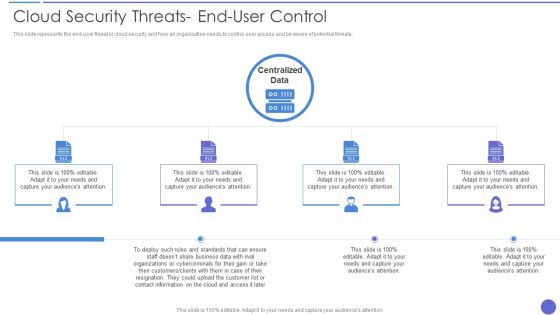
Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
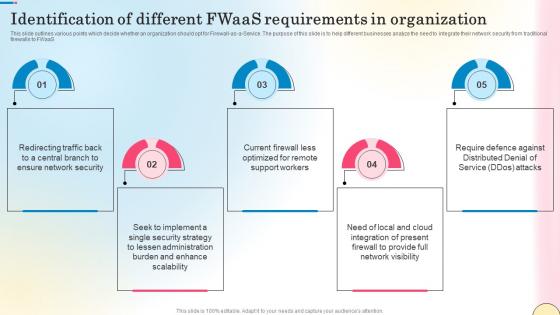
Identification Of Different Fwaas Requirements In Network Security Template Pdf
This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Identification Of Different Fwaas Requirements In Network Security Template Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS.
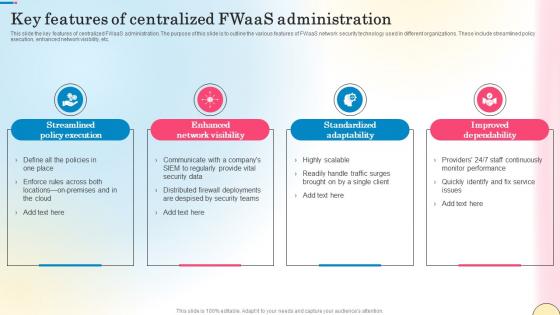
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc.
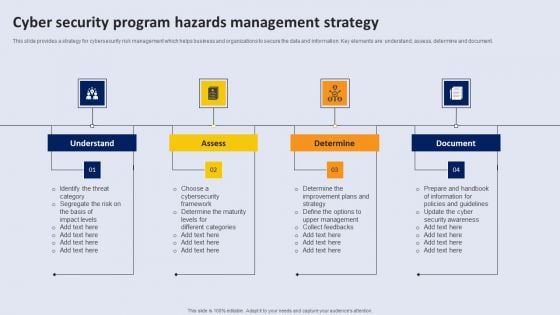
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
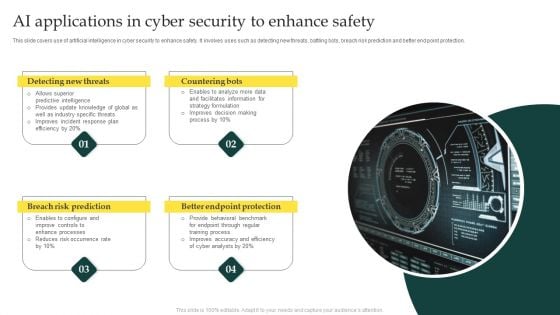
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
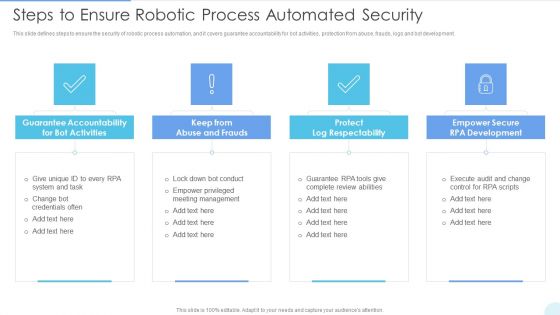
Steps To Ensure Robotic Process Automated Security Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
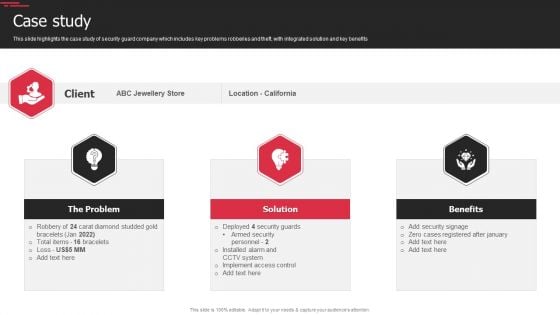
Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
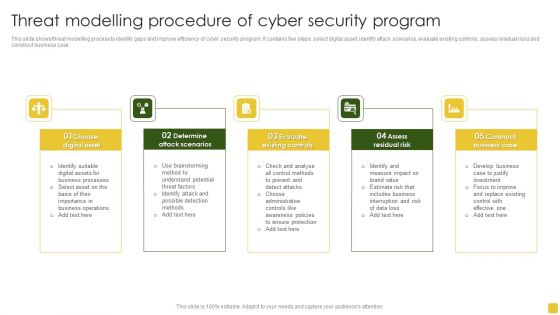
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
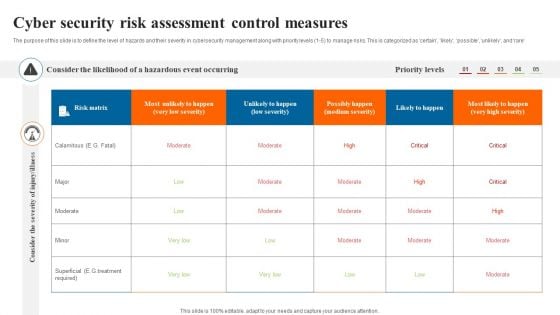
Cyber Security Risk Assessment Control Measures Slides PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain likely possible unlikely and rare. Showcasing this set of slides titled Cyber Security Risk Assessment Control Measures Slides PDF. The topics addressed in these templates are Cyber Security Risk, Assessment Control Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
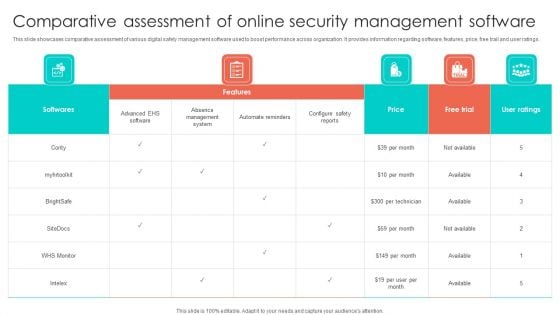
Comparative Assessment Of Online Security Management Software Summary PDF
This slide showcases comparative assessment of various digital safety management software used to boost performance across organization. It provides information regarding software, features, price, free trail and user ratings. Pitch your topic with ease and precision using this Comparative Assessment Of Online Security Management Software Summary PDF. This layout presents information on Price, Absence Management System, Softwares. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
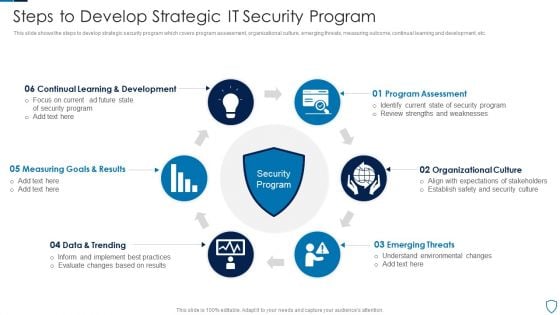
Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































