System Security
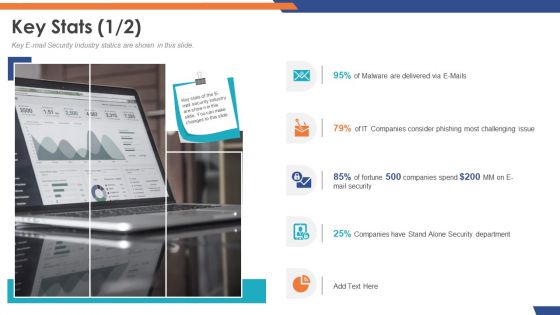
Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Table Of Contents Topics PDF
Presenting this set of slides with name email security market research report table of contents topics pdf. This is a eight stage process. The stages in this process are market introduction, market dynamics, market by segments, market competition analysis, market forecasting and projections, issues faced by companies, porter 5 force model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
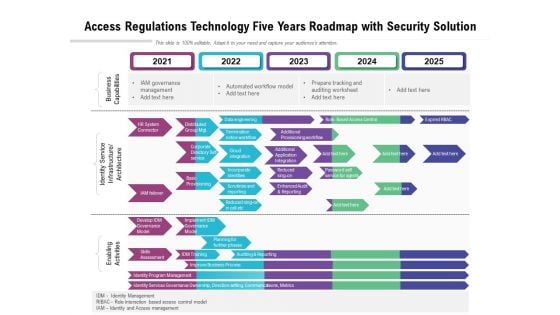
Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Five Year Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured five year data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
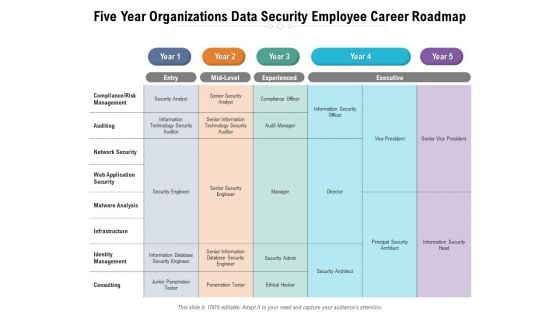
Five Year Organizations Data Security Employee Career Roadmap Inspiration
Presenting our jaw-dropping five year organizations data security employee career roadmap inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
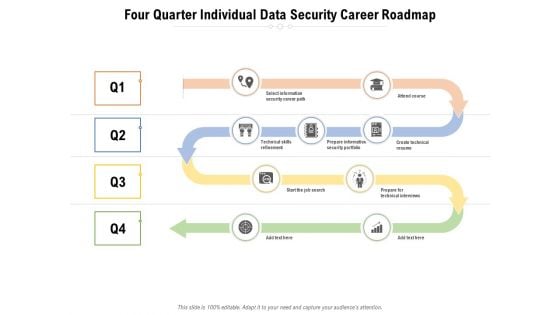
Four Quarter Individual Data Security Career Roadmap Sample
Presenting our innovatively-structured four quarter individual data security career roadmap sample Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly Data Encryption For Security Career Roadmap Structure
Presenting our jaw-dropping half yearly data encryption for security career roadmap structure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
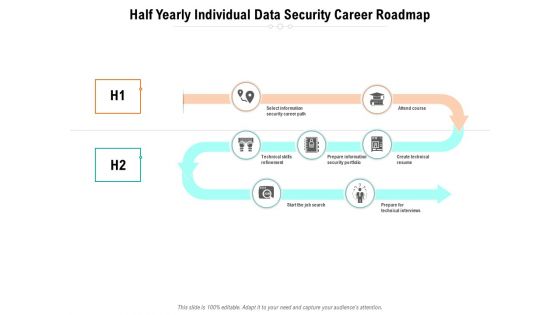
Half Yearly Individual Data Security Career Roadmap Slides
Presenting our innovatively-structured half yearly individual data security career roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
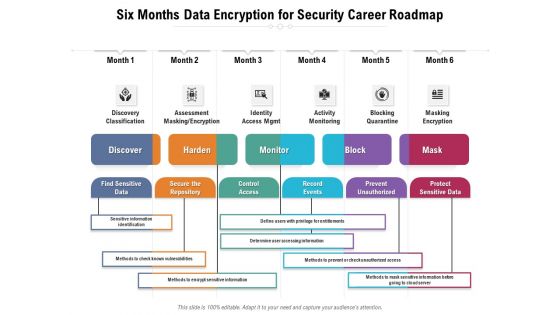
Six Months Data Encryption For Security Career Roadmap Structure
Presenting our innovatively-structured six months data encryption for security career roadmap structure Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
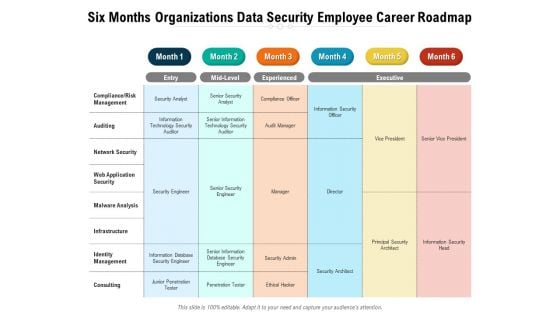
Six Months Organizations Data Security Employee Career Roadmap Ideas
Presenting our jaw-dropping six months organizations data security employee career roadmap ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
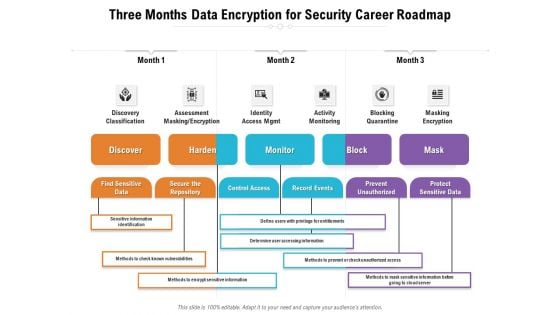
Three Months Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured three months data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
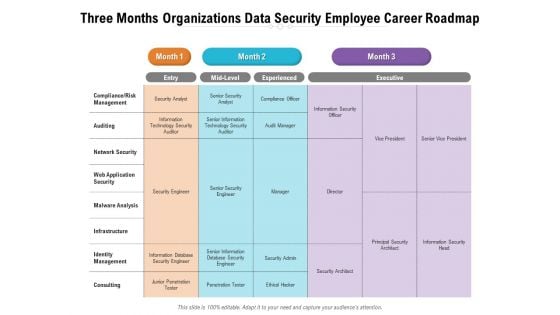
Three Months Organizations Data Security Employee Career Roadmap Background
Presenting our jaw-dropping three months organizations data security employee career roadmap background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Five Years Security Business Growth Assessment Roadmap Icons
Presenting our jaw-dropping five years security business growth assessment roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
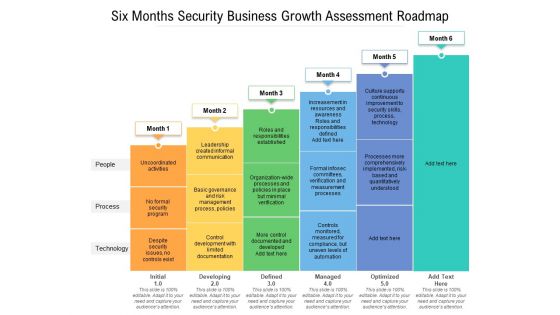
Six Months Security Business Growth Assessment Roadmap Topics
Presenting our jaw-dropping six months security business growth assessment roadmap topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
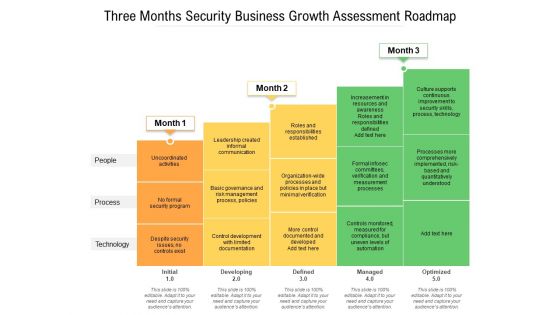
Three Months Security Business Growth Assessment Roadmap Formats
Presenting our jaw-dropping three months security business growth assessment roadmap formats. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
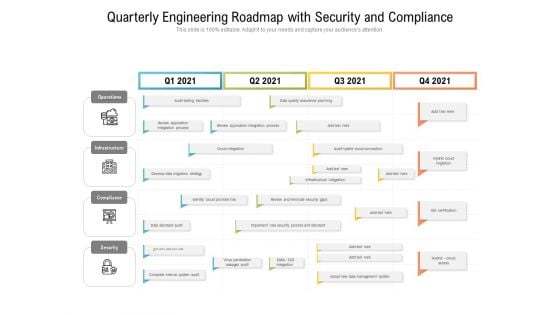
Quarterly Engineering Roadmap With Security And Compliance Template
Presenting our innovatively structured quarterly engineering roadmap with security and compliance template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Workforce Half Yearly Work Roadmap Operations And Security Ideas
Presenting our innovatively structured workforce half yearly work roadmap operations and security ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Workforce Three Months Work Roadmap Operations And Security Ideas
Presenting our jaw dropping workforce three months work roadmap operations and security ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Half Yearly Engineering Roadmap With Security And Compliance Topics
Presenting our jaw-dropping half yearly engineering roadmap with security and compliance topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Cloud Computing Security Half Yearly Roadmap With Deployment Plan Guidelines
Presenting our innovatively structured cloud computing security half yearly roadmap with deployment plan guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Computing Security Plan Quarterly Roadmap For IT Project Slides
Presenting our innovatively structured cloud computing security plan quarterly roadmap for it project slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Five Years IT Security Recognition Program Roadmap Introduction
Presenting our innovatively-structured five years it security recognition program roadmap introduction Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
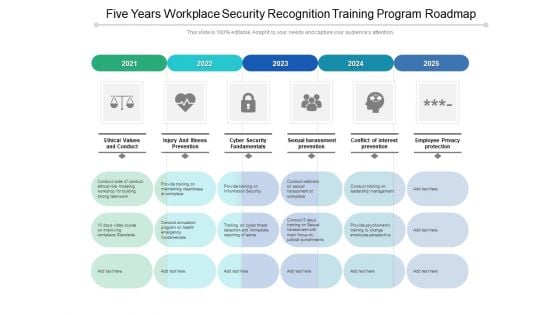
Five Years Workplace Security Recognition Training Program Roadmap Diagrams
Presenting our jaw-dropping five years workplace security recognition training program roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
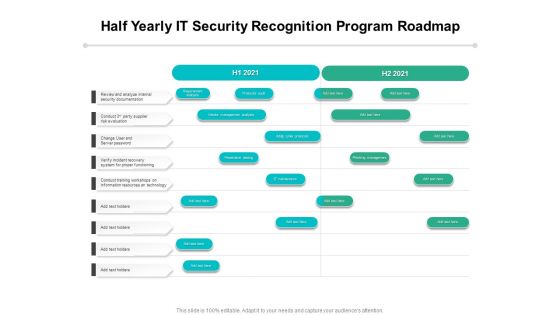
Half Yearly IT Security Recognition Program Roadmap Designs
Presenting our innovatively-structured half yearly it security recognition program roadmap designs Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
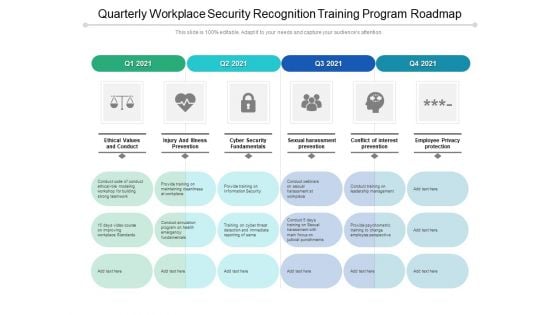
Quarterly Workplace Security Recognition Training Program Roadmap Mockup
Presenting our jaw-dropping quarterly workplace security recognition training program roadmap mockup. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
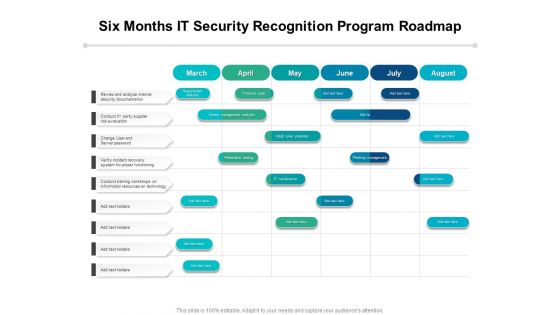
Six Months IT Security Recognition Program Roadmap Diagrams
Presenting our innovatively-structured six months it security recognition program roadmap diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Six Months Workplace Security Recognition Training Program Roadmap Slides
Presenting our jaw-dropping six months workplace security recognition training program roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Three Months IT Security Recognition Program Roadmap Topics
Presenting our innovatively-structured three months it security recognition program roadmap topics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Three Months Workplace Security Recognition Training Program Roadmap Microsoft
Presenting our jaw-dropping three months workplace security recognition training program roadmap microsoft. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Effective Digital Security Three Months Strategic Timeline Download
Presenting our jaw dropping effective digital security three months strategic timeline download. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Quarterly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping quarterly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
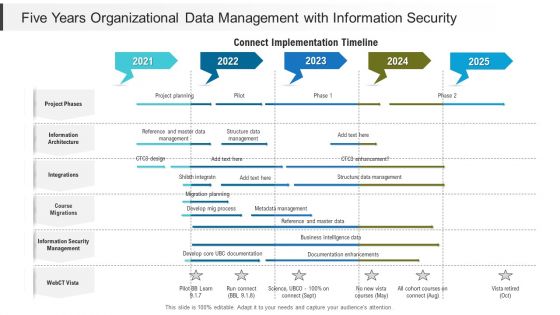
Five Years Organizational Data Management With Information Security Information
Presenting our jaw dropping five years organizational data management with information security information. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
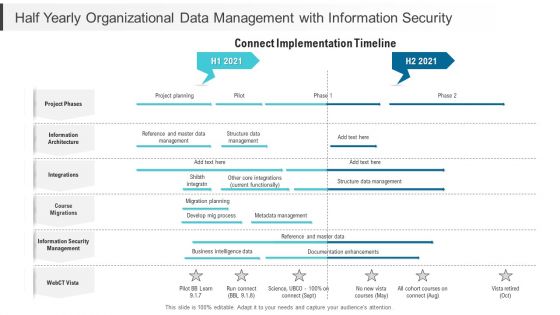
Half Yearly Organizational Data Management With Information Security Designs
Presenting our jaw dropping half yearly organizational data management with information security designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
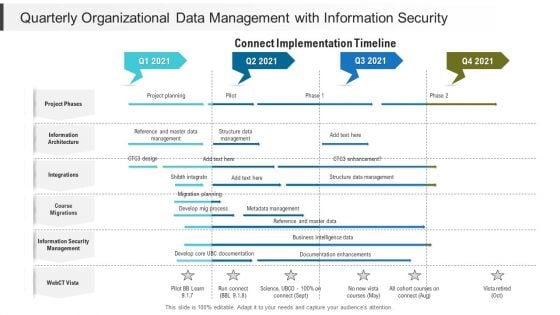
Quarterly Organizational Data Management With Information Security Ideas
Presenting our jaw dropping quarterly organizational data management with information security ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
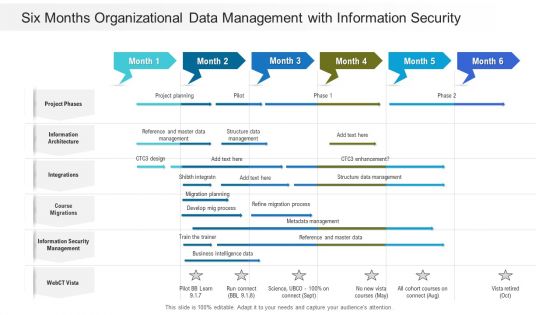
Six Months Organizational Data Management With Information Security Sample
Presenting our jaw dropping six months organizational data management with information security sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
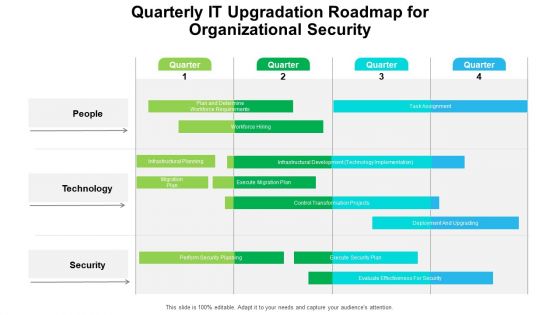
Quarterly IT Upgradation Roadmap For Organizational Security Professional
Presenting our innovatively structured quarterly it upgradation roadmap for organizational security professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
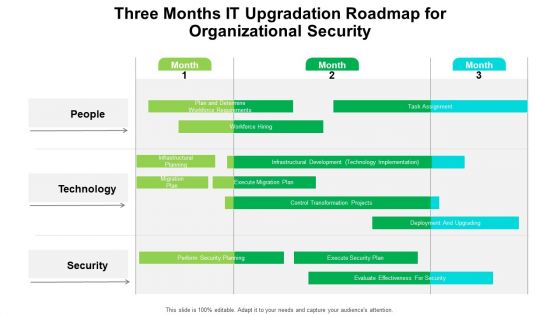
Three Months IT Upgradation Roadmap For Organizational Security Brochure
Presenting our jaw dropping three months it upgradation roadmap for organizational security brochure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
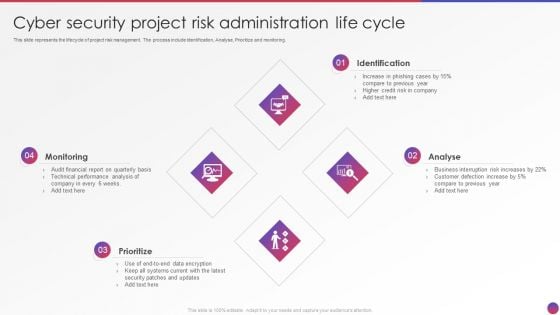
Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
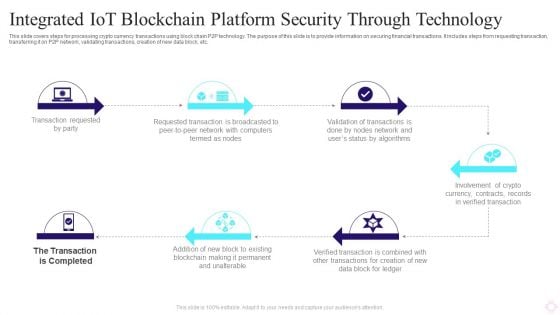
Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
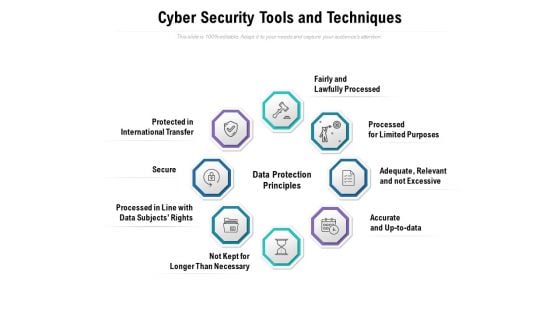
Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Vector
Presenting this set of slides with name cyber security tools and techniques ppt powerpoint presentation styles vector. This is a eight stage process. The stages in this process are fairly and lawfully processed, processed for limited purposes, adequate, relevant and not excessive, accurate and up to data, not kept for longer than necessary, processed in line with data subjects rights, secure, protected in international transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
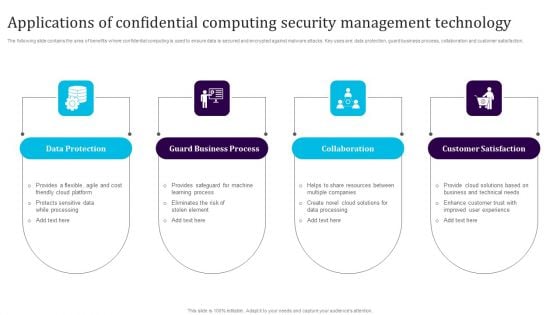
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
7 Stages Of Functional Information Security Business Plan PowerPoint Slides
We present our 7 stages of functional information security business plan PowerPoint Slides .Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Flow Charts PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to Abstract, arrows, balance, business, chart, company, concept, data, diagram, document, finance, financial, report, graph, market, marketing, price, profit, report, statistics, stock, success, trade, work. The prominent colors used in the PowerPoint template are Purple, White, Gray. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by professionals Customers tell us our business PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our 7 stages of functional information security business plan PowerPoint Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our concept PowerPoint templates and PPT Slides will impress their bosses and teams. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by a team of presentation professionals. People tell us our balance PowerPoint templates and PPT Slides will save the presenter time. Ask any favour of our 7 Stages Of Functional Information Security Business Plan PowerPoint Slides. You will find them truly accomodating.
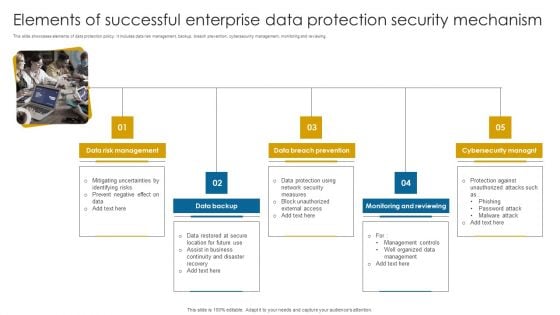
Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF
This slide showcases elements of data protection policy. It includes data risk management, backup, breach prevention, cybersecurity management, monitoring and reviewing.Persuade your audience using this Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Breach Prevention, Monitoring Reviewing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
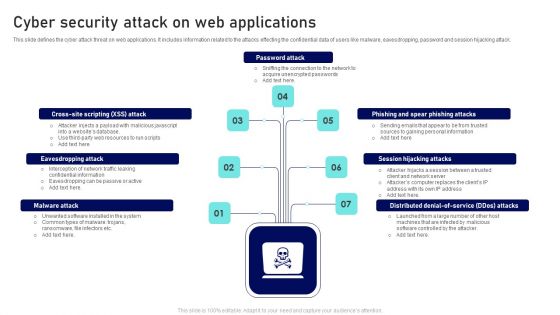
Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phases Of Information IT Security Awareness Training Program Mockup PDF
This slide covers phases of information cybersecurity awareness training program. It involves four phases such as design, development, execution and continual improvement. Persuade your audience using this Phases Of Information IT Security Awareness Training Program Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Design, Development, Execution, Continual Improvement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
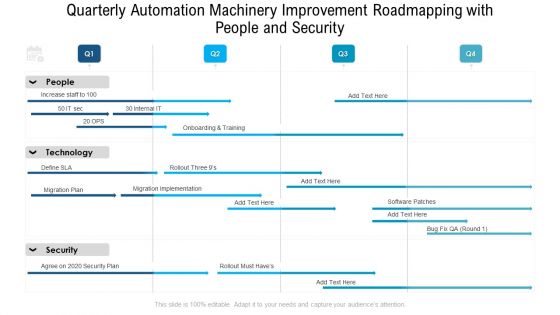
Quarterly Automation Machinery Improvement Roadmapping With People And Security Themes
Presenting our jaw dropping quarterly automation machinery improvement roadmapping with people and security themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
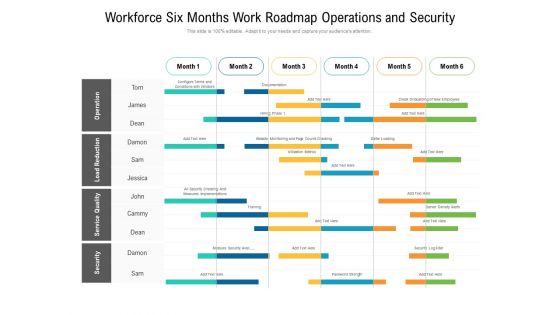
Workforce Six Months Work Roadmap Operations And Security Elements
Presenting the workforce six months work roadmap operations and security elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
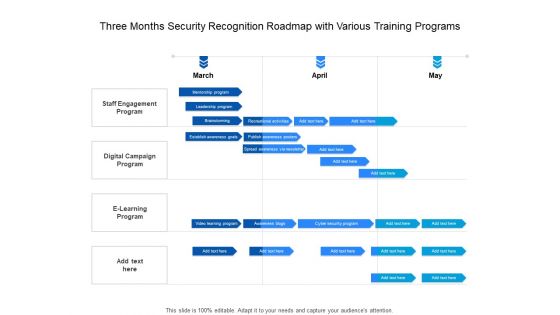
Three Months Security Recognition Roadmap With Various Training Programs Elements
Presenting the three months security recognition roadmap with various training programs elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
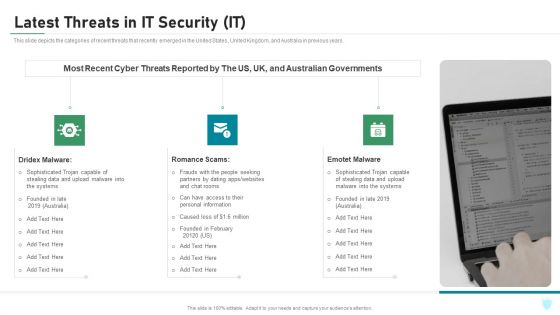
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
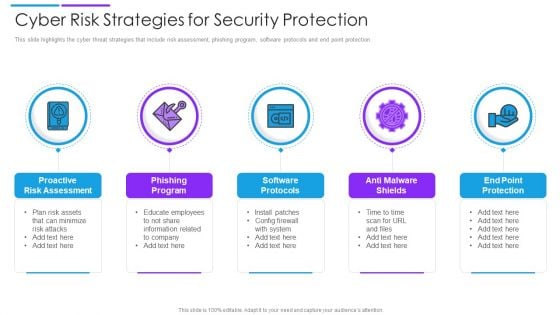
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
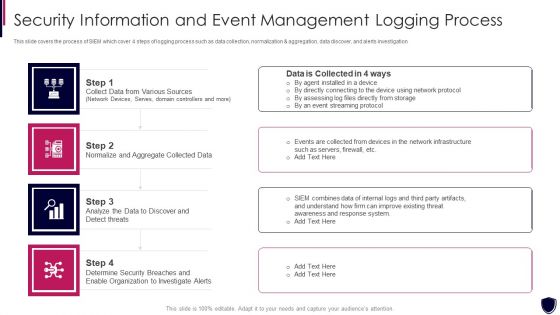
Security Information And Event Management Logging Process Diagrams PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collect data from various sources, normalize and aggregate collected data, organization to investigate alerts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
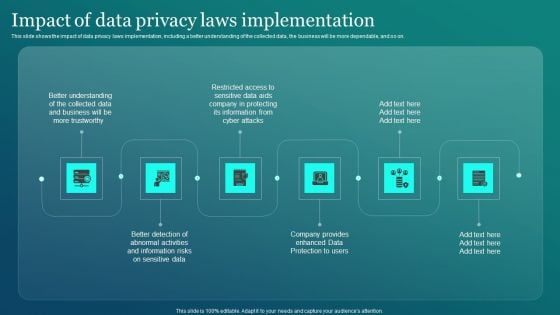
Information Security Impact Of Data Privacy Laws Implementation Slides PDF
This slide shows the impact of data privacy laws implementation, including a better understanding of the collected data, the business will be more dependable, and so on. Take your projects to the next level with our ultimate collection of Information Security Impact Of Data Privacy Laws Implementation Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
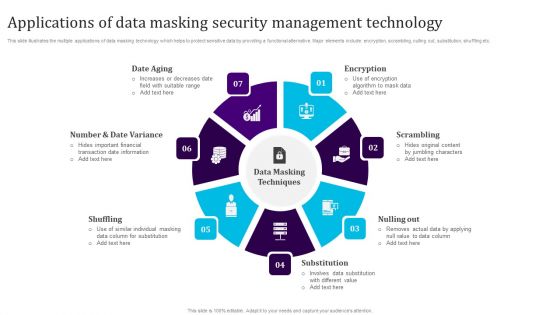
Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
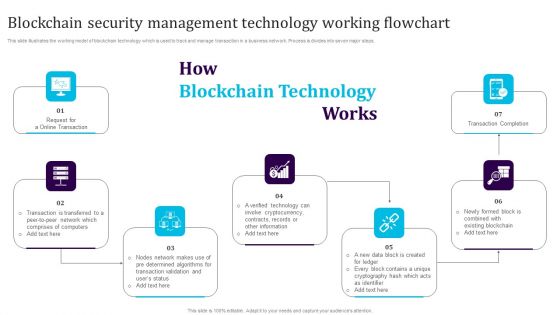
Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Blockchain Security Technology For Healthcare Industry Icons PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification.Persuade your audience using this Blockchain Security Technology For Healthcare Industry Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authenticity Medicine, Electronic Health, Ensures Only Trusted. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
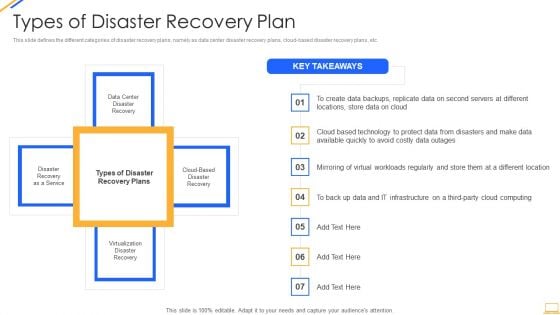
Desktop Security Management Types Of Disaster Recovery Plan Topics PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a desktop security management types of disaster recovery plan topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, locations, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
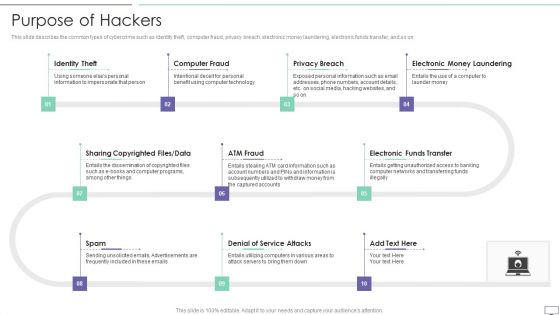
IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
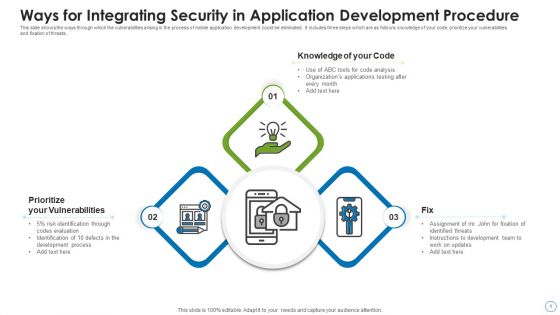
Ways For Integrating Security In Application Development Procedure Structure PDF
This slide shows the ways through which the vulnerabilities arising in the process of mobile application development could be eliminated. It includes three steps which are as follows knowledge of your code, prioritize your vulnerabilities and fixation of threats. Persuade your audience using this ways for integrating security in application development procedure structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including prioritize your vulnerabilities, knowledge of your code, fix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































