Table Of Safety Contents
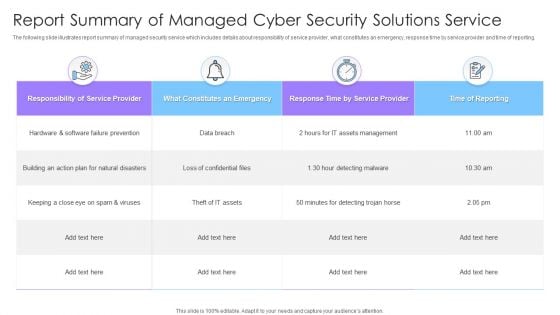
Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides
The following slide illustrates report summary of managed security service which includes details about responsibility of service provider, what constitutes an emergency, response time by service provider and time of reporting. Showcasing this set of slides titled Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides. The topics addressed in these templates are Responsibility Of Service Provider, Time Of Reporting, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
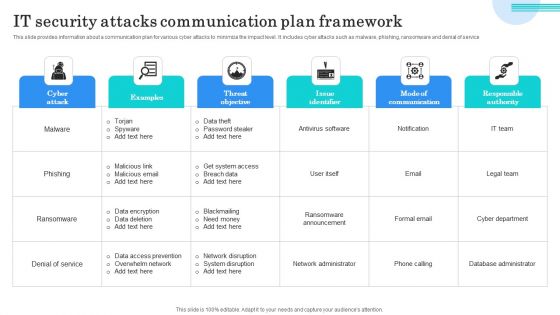
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
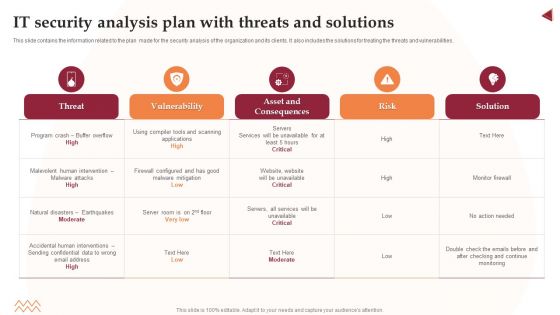
IT Security Analysis Plan With Threats And Solutions Infographics PDF
This slide contains the information related to the plan made for the security analysis of the organization and its clients. It also includes the solutions for treating the threats and vulnerabilities. Showcasing this set of slides titled IT Security Analysis Plan With Threats And Solutions Infographics PDF. The topics addressed in these templates are Risk, Applications, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
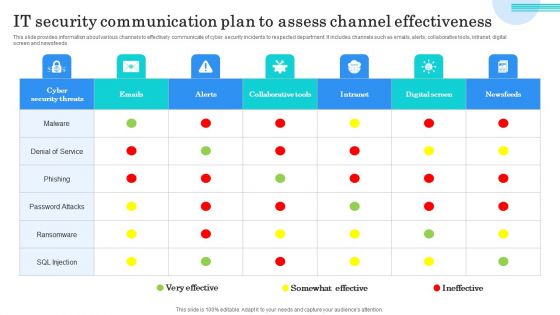
IT Security Communication Plan To Assess Channel Effectiveness Themes PDF
This slide provides information about various channels to effectively communicate of cyber security incidents to respected department. It includes channels such as emails, alerts, collaborative tools, intranet, digitalscreen and newsfeeds. Showcasing this set of slides titled IT Security Communication Plan To Assess Channel Effectiveness Themes PDF. The topics addressed in these templates are Denial Service, Phishing, Password Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
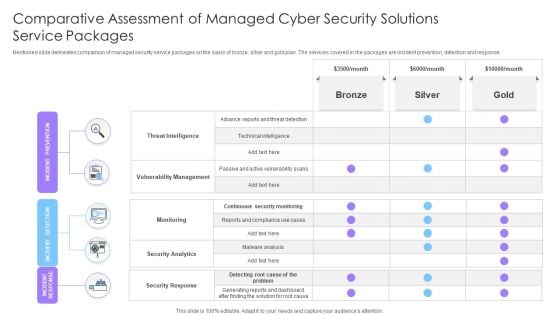
Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Offshore Vs Outsourced Call Center Comparative Analysis Icons Pdf
The following slide highlights points like labor cost, service quality, communication, data security, time zone and customer feedback to show offshore vs onshore call center comparative analysis. It helps organization to make informed decision between offshore and onshore call center outsourcing based on important factors. Pitch your topic with ease and precision using this Offshore Vs Outsourced Call Center Comparative Analysis Icons Pdf. This layout presents information on Service Quality, Communication, Data Security, Customer Feedback. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights points like labor cost, service quality, communication, data security, time zone and customer feedback to show offshore vs onshore call center comparative analysis. It helps organization to make informed decision between offshore and onshore call center outsourcing based on important factors.
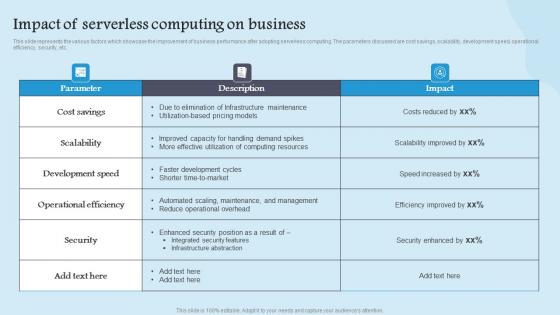
Impact Serverless Computing Role Serverless Computing Modern Technology Information Pdf
This slide represents the various factors which showcase the improvement of business performance after adopting serverless computing. The parameters discussed are cost savings, scalability, development speed, operational efficiency, security, etc. Find a pre designed and impeccable Impact Serverless Computing Role Serverless Computing Modern Technology Information Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the various factors which showcase the improvement of business performance after adopting serverless computing. The parameters discussed are cost savings, scalability, development speed, operational efficiency, security, etc.
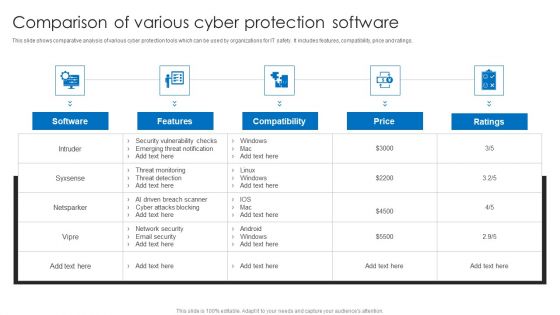
Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
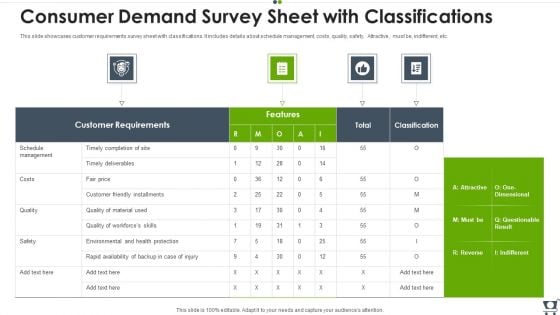
Consumer Demand Survey Sheet With Classifications Topics PDF
This slide showcases customer requirements survey sheet with classifications. It includes details about schedule management, costs, quality, safety, Attractive, must be, indifferent, etc. Pitch your topic with ease and precision using this Consumer Demand Survey Sheet With Classifications Topics PDF. This layout presents information on Customer, Environmental, Quality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
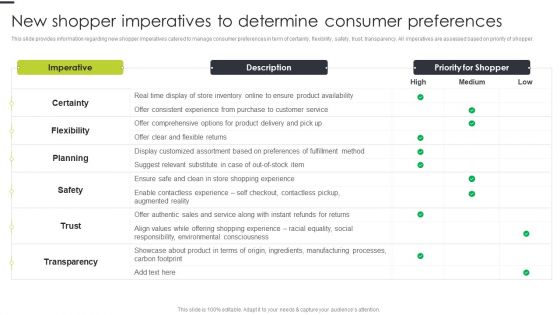
New Shopper Imperatives To Determine Consumer Preferences Template PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver and pitch your topic in the best possible manner with this New Shopper Imperatives To Determine Consumer Preferences Template PDF. Use them to share invaluable insights on Product Availability, Consistent Experience, Store Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
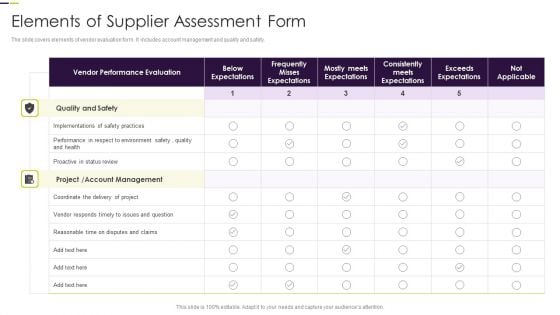
Elements Of Supplier Assessment Form Slides PDF
The slide covers elements of vendor evaluation form. It includes account management and quality and safety.Pitch your topic with ease and precision using this Elements Of Supplier Assessment Form Slides PDF. This layout presents information on Vendor Performance, Below Expectations, Misses Expectations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
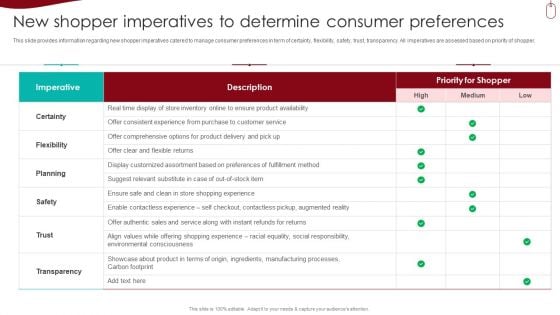
Retail Outlet Experience Optimization Playbook New Shopper Imperatives To Determine Consumer Preferences Brochure PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver an awe inspiring pitch with this creative Retail Outlet Experience Optimization Playbook New Shopper Imperatives To Determine Consumer Preferences Brochure PDF bundle. Topics like Planning, Customer Service, Manufacturing Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
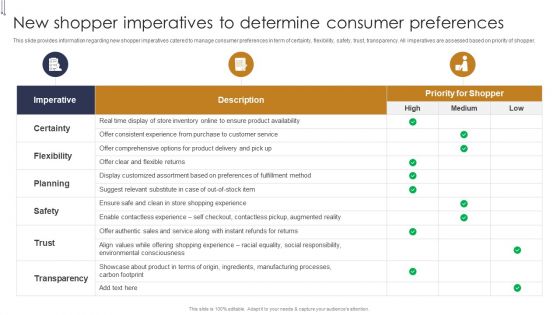
New Shopper Imperatives To Determine Consumer Preferences Buyers Preference Management Playbook Clipart PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver an awe inspiring pitch with this creative New Shopper Imperatives To Determine Consumer Preferences Buyers Preference Management Playbook Clipart PDF bundle. Topics like Fulfillment Method, Environmental Consciousness, Manufacturing Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Evaluation Form With Performance Ratings Ppt PowerPoint Presentation Portfolio File Formats PDF
The slide shows a workforce evaluation form for performance review. It includes employee details, reviewer details, objectives, ratings and additional comments.Pitch your topic with ease and precision using this Workforce Evaluation Form With Performance Ratings Ppt PowerPoint Presentation Portfolio File Formats PDF. This layout presents information on Workforce Safety, Evaluation Checklist Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
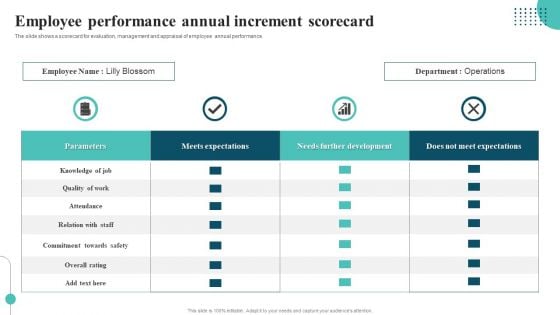
Employee Performance Annual Increment Scorecard Template PDF
The slide shows a scorecard for evaluation, management and appraisal of employee annual performance. Pitch your topic with ease and precision using this Employee Performance Annual Increment Scorecard Template PDF. This layout presents information on Quality Of Work, Development, Commitment Towards Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
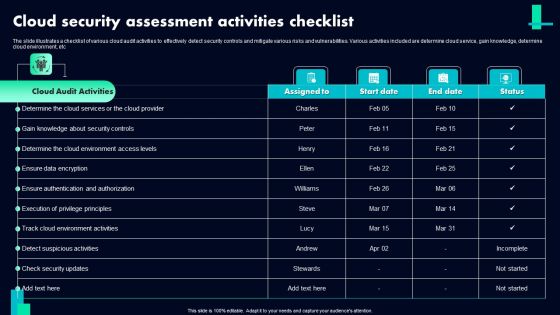
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solutions To Challenges Faced In R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.

Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc.
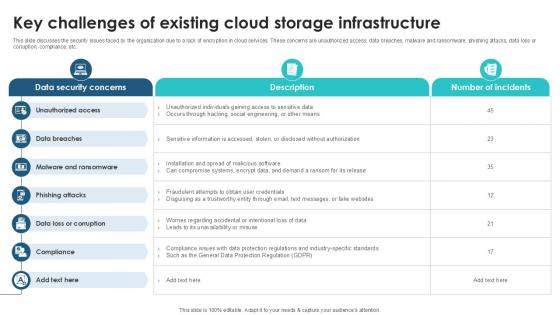
Key Challenges Of Existing Cloud Client Side Encryption PPT Slide
This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. This modern and well-arranged Key Challenges Of Existing Cloud Client Side Encryption PPT Slide provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc.

Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Welcome to our selection of the Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.
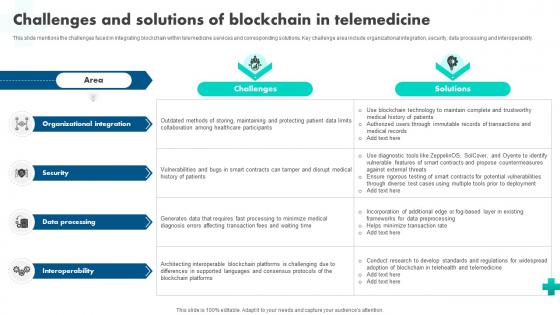
Challenges And Solutions Of Blockchain How Blockchain Is Reshaping Healthcare BCT SS V
This slide mentions the challenges faced in integrating blockchain within telemedicine services and corresponding solutions. Key challenge area include organizational integration, security, data processing and interoperability. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Challenges And Solutions Of Blockchain How Blockchain Is Reshaping Healthcare BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Challenges And Solutions Of Blockchain How Blockchain Is Reshaping Healthcare BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide mentions the challenges faced in integrating blockchain within telemedicine services and corresponding solutions. Key challenge area include organizational integration, security, data processing and interoperability.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

The Digital Project Managers Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. If you are looking for a format to display your unique thoughts, then the professionally designed The Digital Project Managers Deployment Of Cloud Project Management Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download The Digital Project Managers Deployment Of Cloud Project Management Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.
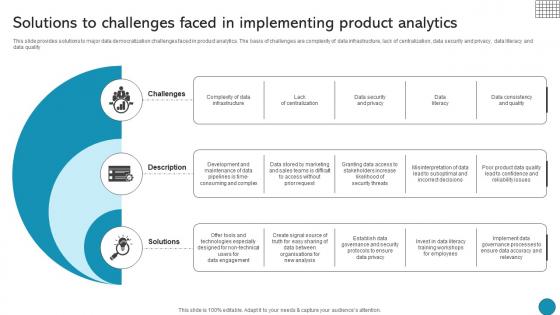
Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality If you are looking for a format to display your unique thoughts, then the professionally designed Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality
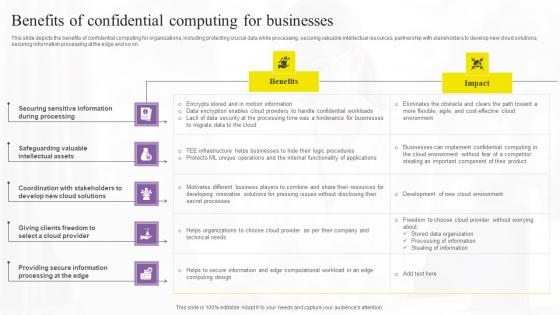
Benefits Of Confidential Computing Confidential Computing Technologies Professional Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing Confidential Computing Technologies Professional Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.

Deployment Of Cloud Project Management Model Strategies For Success In Digital
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deployment Of Cloud Project Management Model Strategies For Success In Digital. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deployment Of Cloud Project Management Model Strategies For Success In Digital today and make your presentation stand out from the rest This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.

Digital Project Management Strategies Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Digital Project Management Strategies Deployment Of Cloud Project Management Model. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Digital Project Management Strategies Deployment Of Cloud Project Management Model today and make your presentation stand out from the rest This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.
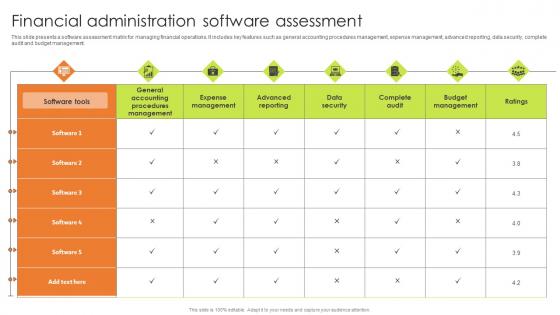
Financial Administration Software Assessment Rules Pdf
This slide presents a software assessment matrix for managing financial operations. It includes key features such as general accounting procedures management, expense management, advanced reporting, data security, complete audit and budget management. Pitch your topic with ease and precision using this Financial Administration Software Assessment Rules Pdf. This layout presents information on Expense Management, Advanced Reporting, Data Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents a software assessment matrix for managing financial operations. It includes key features such as general accounting procedures management, expense management, advanced reporting, data security, complete audit and budget management.
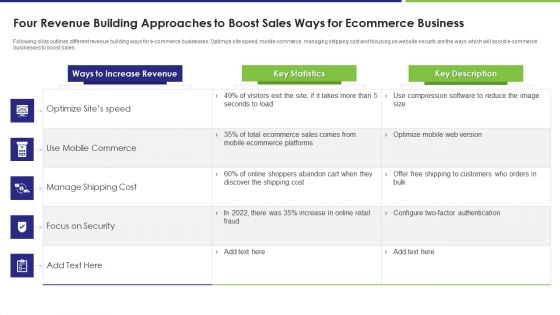
Four Revenue Building Approaches To Boost Sales Ways For Ecommerce Business Elements PDF
Following slide outlines different revenue building ways for e commerce businesses. Optimize site speed, mobile commerce, managing shipping cost and focusing on website security are the ways which will assist e commerce businesses to boost sales. Showcasing this set of slides titled four revenue building approaches to boost sales ways for ecommerce business elements pdf. The topics addressed in these templates are commerce, cost, sales. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Want to ace your presentation in front of a live audience Our Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
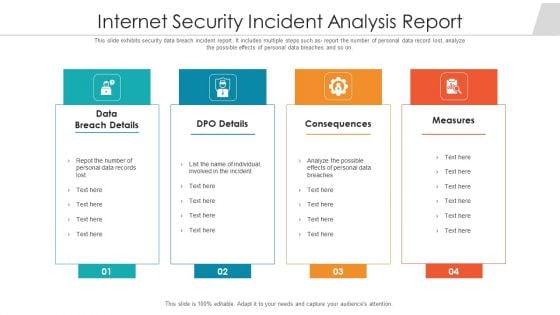
Internet Security Incident Analysis Report Template PDF
This slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Showcasing this set of slides titled internet security incident analysis report template pdf. The topics addressed in these templates are data breach details, consequences, measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. Present like a pro with Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
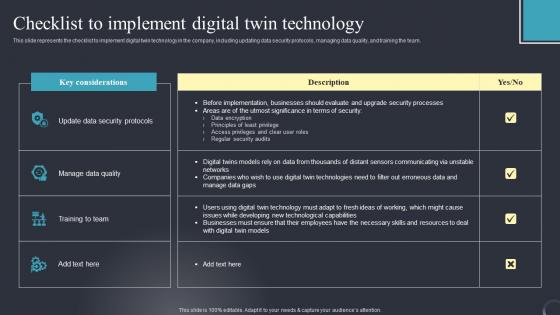
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
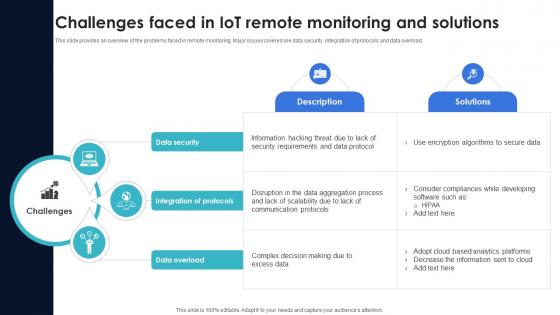
Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V
This slide provides an overview of the problems faced in remote monitoring. Major issues covered are data security, integration of protocols and data overload. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides an overview of the problems faced in remote monitoring. Major issues covered are data security, integration of protocols and data overload.
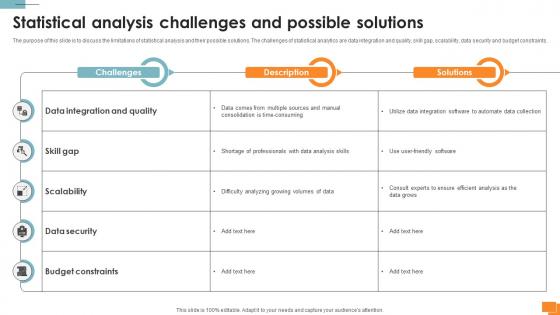
Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Take your projects to the next level with our ultimate collection of Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.
Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.
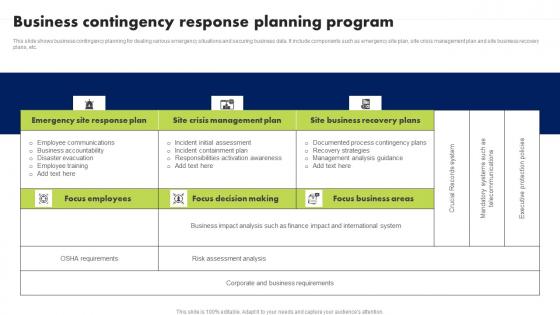
Business Contingency Response Planning Program Formats Pdf
This slide shows business contingency planning for dealing various emergency situations and securing business data. It include components such as emergency site plan, site crisis management plan and site business recovery plans, etc. Pitch your topic with ease and precision using this Business Contingency Response Planning Program Formats Pdf. This layout presents information on Focus Employees, Focus Decision Making. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows business contingency planning for dealing various emergency situations and securing business data. It include components such as emergency site plan, site crisis management plan and site business recovery plans, etc.
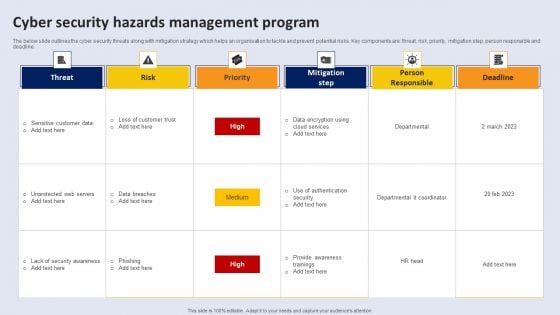
Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
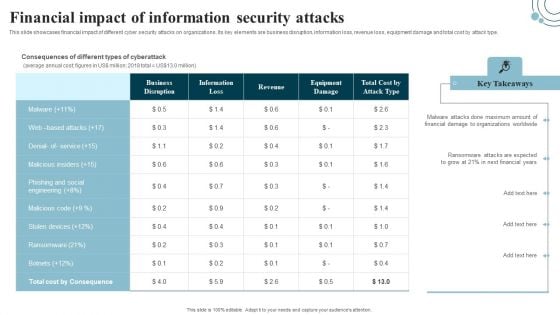
Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
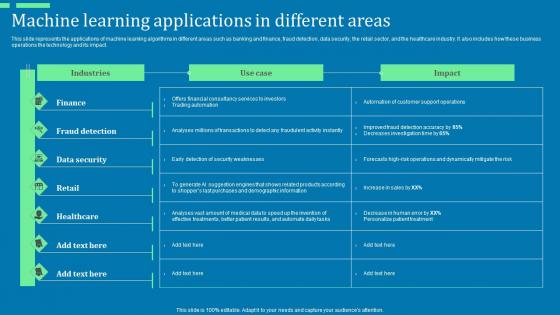
Machine Learning Applications In Different Areas Advanced Tools For Hyperautomation Ppt File Slide Pdf
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact. Find a pre-designed and impeccable Machine Learning Applications In Different Areas Advanced Tools For Hyperautomation Ppt File Slide Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact.
Emerging Technology Trends For Business Growth Icons Pdf
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Do you know about Slidesgeeks Emerging Technology Trends For Business Growth Icons Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security.
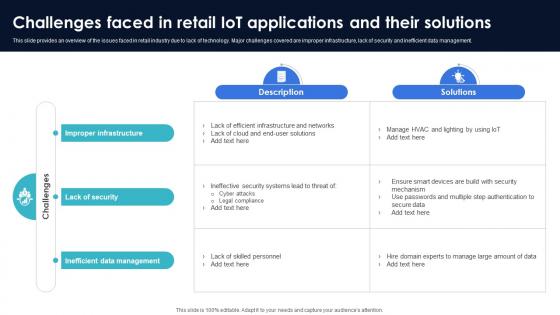
Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V
This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management. Make sure to capture your audiences attention in your business displays with our gratis customizable Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management.
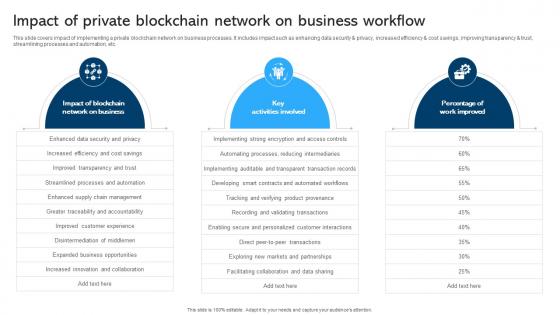
Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V
This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc.

Strategic Plan To Enhance IoT Revolutionizing Production IoT Ppt Example
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Take your projects to the next level with our ultimate collection of Strategic Plan To Enhance IoT Revolutionizing Production IoT Ppt Example. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.

Categories Of Issues In Artificial Intelligence Development PPT Sample SS
This slide presents categories of issues in artificial intelligence AI development and some appropriate solutions, helpful in reducing costs and improving client experience. It includes problems such as bias problem, data security, infrastructure, AI integration and expensive. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Categories Of Issues In Artificial Intelligence Development PPT Sample SS from Slidegeeks and deliver a wonderful presentation. This slide presents categories of issues in artificial intelligence AI development and some appropriate solutions, helpful in reducing costs and improving client experience. It includes problems such as bias problem, data security, infrastructure, AI integration and expensive.
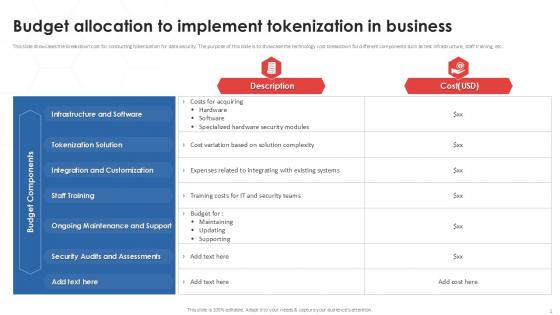
Budget Allocation To Implement Tokenization In Business PPT Example
This slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Find a pre-designed and impeccable Budget Allocation To Implement Tokenization In Business PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc.
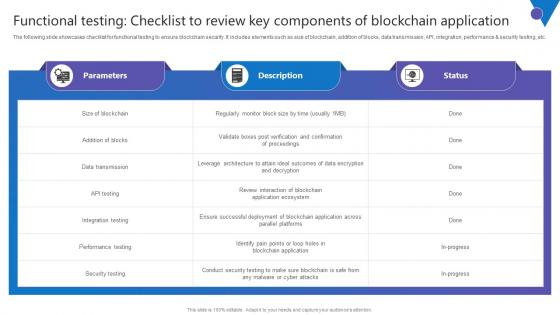
Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf
The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.
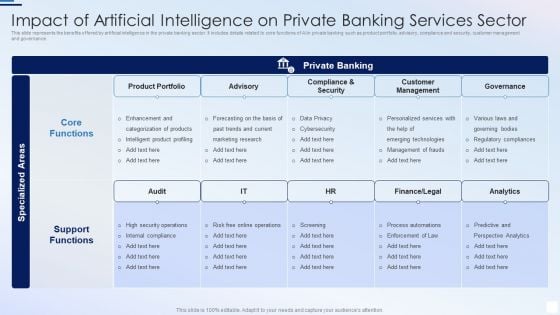
Impact Of Artificial Intelligence On Private Banking Services Sector Pictures PDF
This slide represents the benefits offered by artificial intelligence in the private banking sector. It includes details related to core functions of AI in private banking such as product portfolio, advisory, compliance and security, customer management and governance.Showcasing this set of slides titled Impact Of Artificial Intelligence On Private Banking Services Sector Pictures PDF. The topics addressed in these templates are Categorization Of Products, Security Operations, Emerging Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.
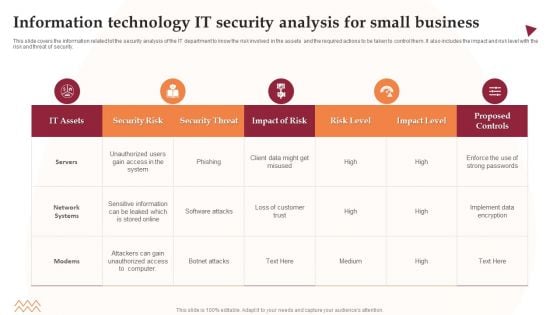
Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
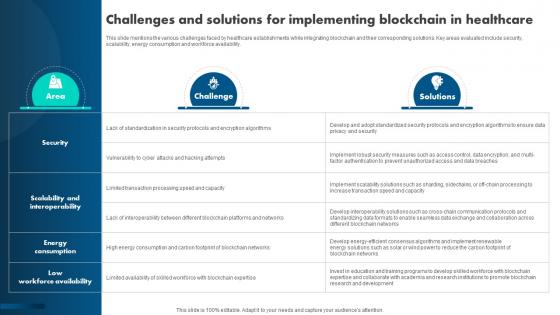
How Blockchain Is Reshaping Challenges And Solutions For Implementing Blockchain BCT SS V
This slide mentions the various challenges faced by healthcare establishments while integrating blockchain and their corresponding solutions. Key areas evaluated include security, scalability, energy consumption and workforce availability. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Blockchain Is Reshaping Challenges And Solutions For Implementing Blockchain BCT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide mentions the various challenges faced by healthcare establishments while integrating blockchain and their corresponding solutions. Key areas evaluated include security, scalability, energy consumption and workforce availability.
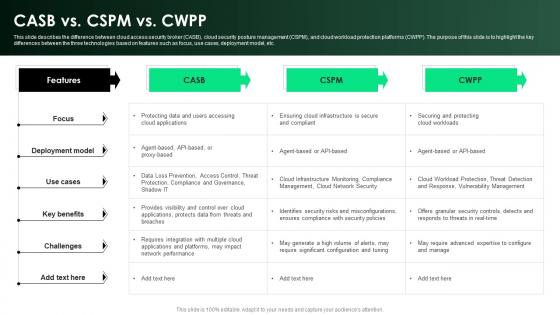
CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts
This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc.
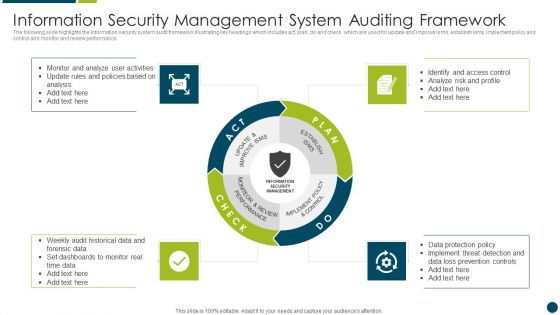
Information Security Management System Auditing Framework Microsoft PDF
The following slide highlights the information security management system audit checklist illustrating matrix consisting of domain, objective, description, identification and audit for information security policies, information security organization and human resource security Showcasing this set of slides titled Information Security Management System Auditing Framework Microsoft PDF. The topics addressed in these templates are Information Security Organization, Information Security Policies, Human Resource Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting


 Continue with Email
Continue with Email

 Home
Home


































