Table Of Safety Contents
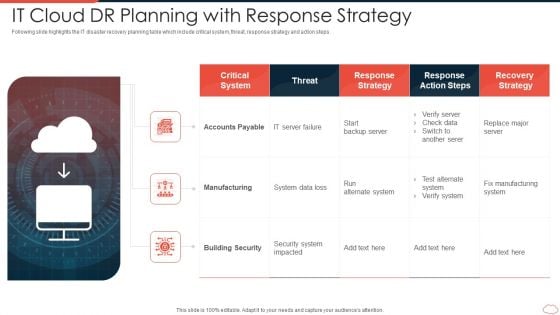
IT Cloud DR Planning With Response Strategy Template PDF
Following slide highlights the IT disaster recovery planning table which include critical system, threat, response strategy and action steps. Showcasing this set of slides titled it cloud dr planning with response strategy template pdf. The topics addressed in these templates are accounts payable, manufacturing, building security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
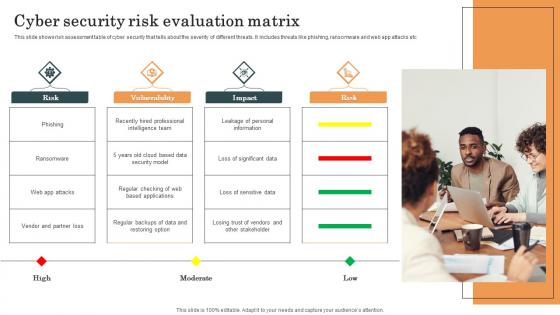
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.
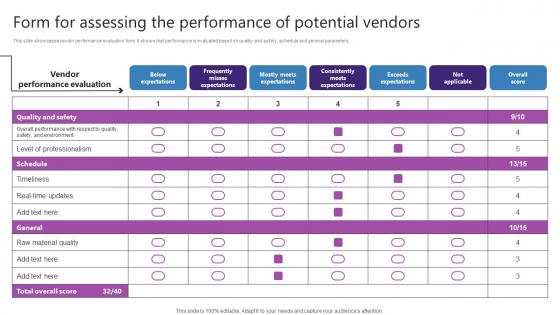
Form For Assessing The Performance Of Potential Vendors Strategic Plan For Enhancing Portrait Pdf
This slide showcases vendor performance evaluation form. It shows that performance is evaluated based on quality and safety, schedule and general parameters. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Form For Assessing The Performance Of Potential Vendors Strategic Plan For Enhancing Portrait Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Form For Assessing The Performance Of Potential Vendors Strategic Plan For Enhancing Portrait Pdf This slide showcases vendor performance evaluation form. It shows that performance is evaluated based on quality and safety, schedule and general parameters.
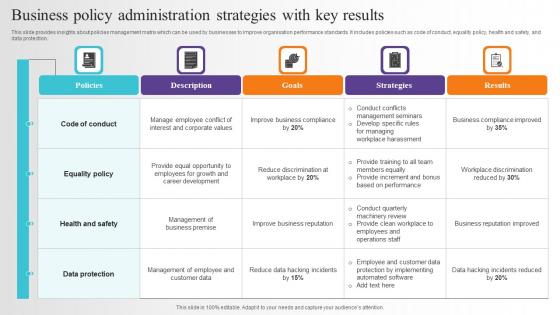
Business Policy Administration Strategies With Key Results Download Pdf
This slide provides insights about policies management matrix which can be used by businesses to improve organisation performance standards. It includes policies such as code of conduct, equality policy, health and safety, and data protection. Showcasing this set of slides titled Business Policy Administration Strategies With Key Results Download Pdf. The topics addressed in these templates are Code Conduct, Equality Policy, Health And Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides insights about policies management matrix which can be used by businesses to improve organisation performance standards. It includes policies such as code of conduct, equality policy, health and safety, and data protection.

Analysis Current Scenario Healthcare Information Tech To Enhance Medical Facilities Designs Pdf
This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction. Boost your pitch with our creative Analysis Current Scenario Healthcare Information Tech To Enhance Medical Facilities Designs Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction.
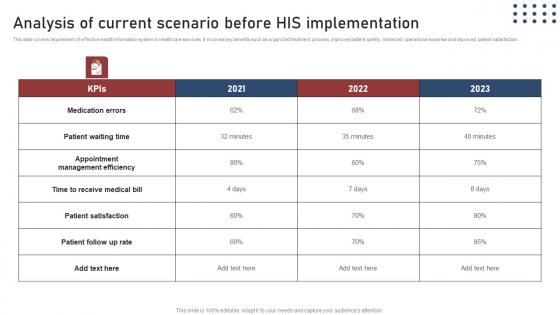
Analysis Current Scenario Transforming Medical Workflows Via His Integration Rules Pdf
This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction. Boost your pitch with our creative Analysis Current Scenario Transforming Medical Workflows Via His Integration Rules Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction.
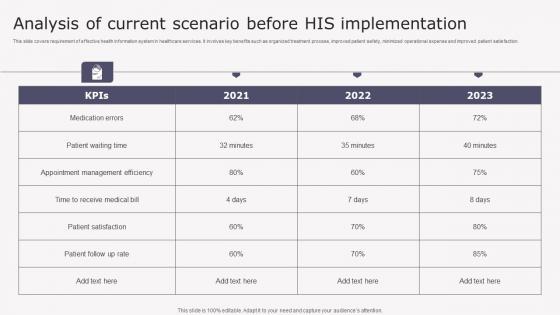
Analysis Current Scenario Transforming Medicare Services Using Health Demonstration Pdf
This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction. Boost your pitch with our creative Analysis Current Scenario Transforming Medicare Services Using Health Demonstration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction.
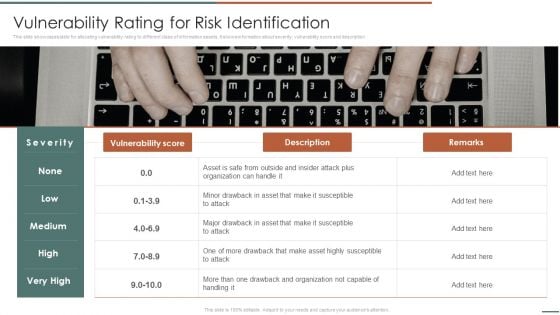
Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF
This slide shows various stakeholders expectations from the mobile financial service ecosystem. Stakeholders covered in the table are consumer, employees, mobile network operators, micro finance institutions, agents and regulator. This is a Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Security, Commission Transactions, Reduce Money. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
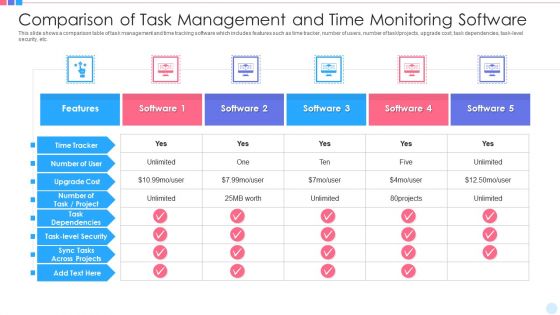
Comparison Of Task Management And Time Monitoring Software Professional PDF
This slide shows a comparison table of task management and time tracking software which includes features such as time tracker, number of users, number of task or projects, upgrade cost, task dependencies, task level security, etc. Showcasing this set of slides titled comparison of task management and time monitoring software professional pdf. The topics addressed in these templates are upgrade cost, projects, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
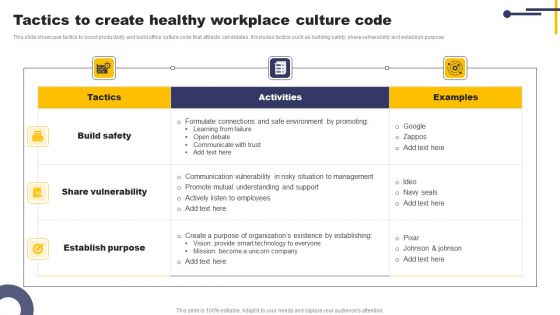
Tactics To Create Healthy Workplace Culture Code Diagrams PDF
This slide showcase tactics to boost productivity and build office culture code that attracts candidates. It includes tactics such as building safety, share vulnerability and establish purpose. Showcasing this set of slides titled Tactics To Create Healthy Workplace Culture Code Diagrams PDF. The topics addressed in these templates are Build Safety, Share Vulnerability, Establish Purpose. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
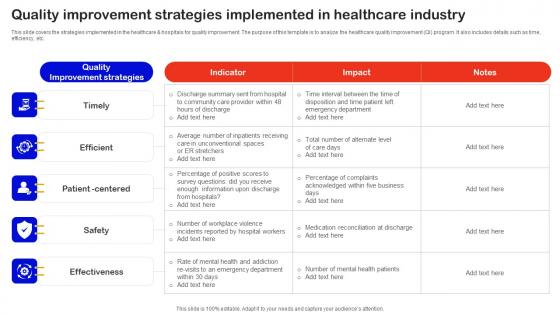
Quality Improvement Strategies Implemented In Healthcare Industry Sample Pdf
This slide covers the strategies implemented in the healthcare and hospitals for quality improvement. The purpose of this template is to analyze the healthcare quality improvement QI program. It also includes details such as time, efficiency, etc. Showcasing this set of slides titled Quality Improvement Strategies Implemented In Healthcare Industry Sample Pdf. The topics addressed in these templates are Timely, Efficient, Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers the strategies implemented in the healthcare and hospitals for quality improvement. The purpose of this template is to analyze the healthcare quality improvement QI program. It also includes details such as time, efficiency, etc.
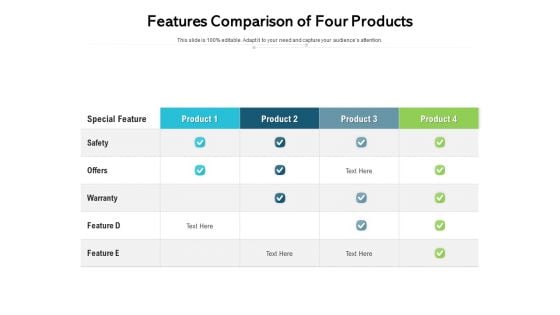
Features Comparison Of Four Products Ppt PowerPoint Presentation Gallery Designs Download PDF
Showcasing this set of slides titled features comparison of four products ppt powerpoint presentation gallery designs download pdf. The topics addressed in these templates are safety, offers, warranty. All the content presented in this PPT design is completely editable. Download it and make adjustments in colour, background, font etc. as per your unique business setting.
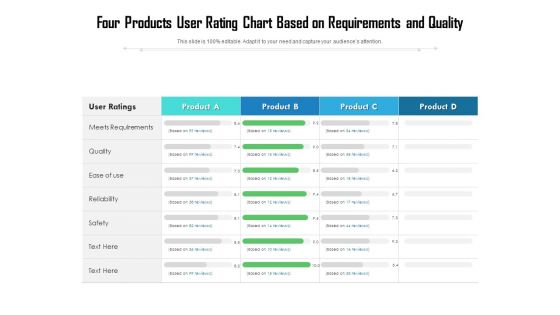
Four Products User Rating Chart Based On Requirements And Quality Ppt PowerPoint Presentation Gallery Slide Download PDF
Showcasing this set of slides titled four products user rating chart based on requirements and quality ppt powerpoint presentation gallery slide download pdf. The topics addressed in these templates are reliability, safety, quality. All the content presented in this PPT design is completely editable. Download it and make adjustments in colour, background, font etc. as per your unique business setting.
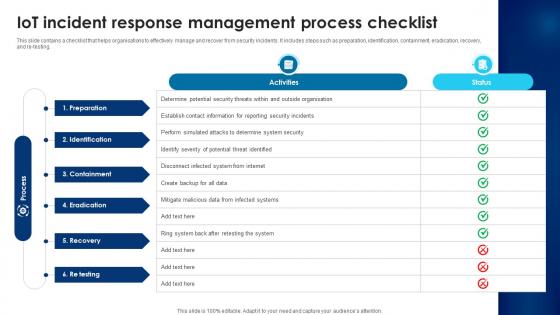
Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V
This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V. This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing.

Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V
This slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN. Explore a selection of the finest Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN.

Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal
This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.Take your presentations to the next level with our Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.
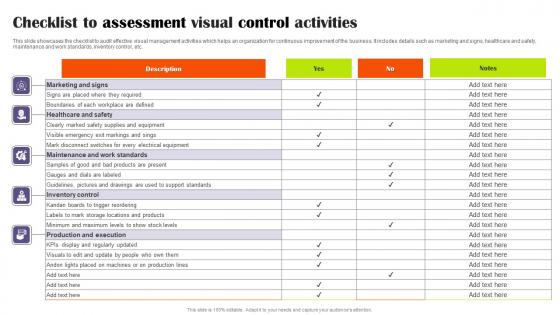
Checklist To Assessment Visual Control Activities Slides Pdf
This slide showcases the checklist to audit effective visual management activities which helps an organization for continuous improvement of the business. It includes details such as marketing and signs, healthcare and safety, maintenance and work standards, inventory control, etc. Pitch your topic with ease and precision using this Checklist To Assessment Visual Control Activities Slides Pdf This layout presents information on Marketing And Signs, Healthcare And Safety, Production And Execution It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the checklist to audit effective visual management activities which helps an organization for continuous improvement of the business. It includes details such as marketing and signs, healthcare and safety, maintenance and work standards, inventory control, etc.
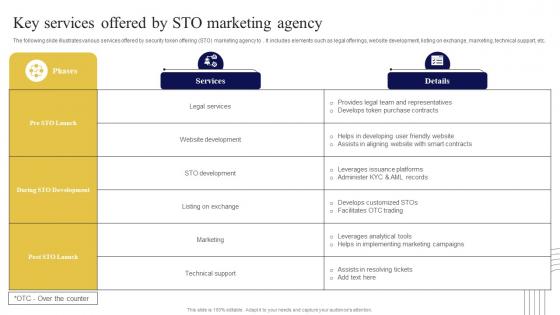
Key Services Offered By STO Exploring Investment Opportunities Topics Pdf
The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc. Slidegeeks has constructed Key Services Offered By STO Exploring Investment Opportunities Topics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc.
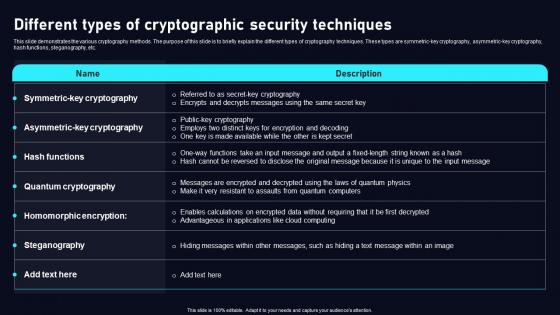
Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc. Slidegeeks has constructed Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc.
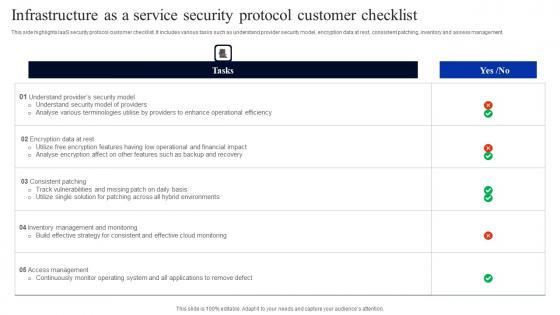
Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management.
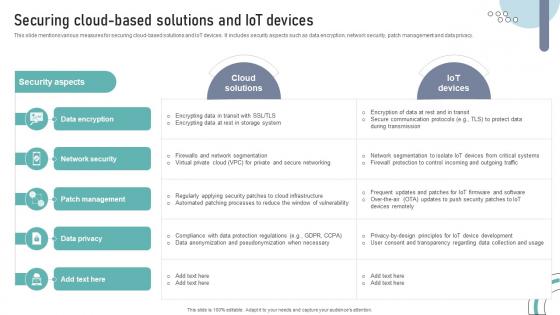
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
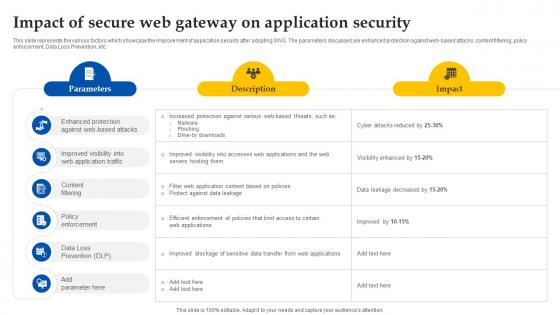
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
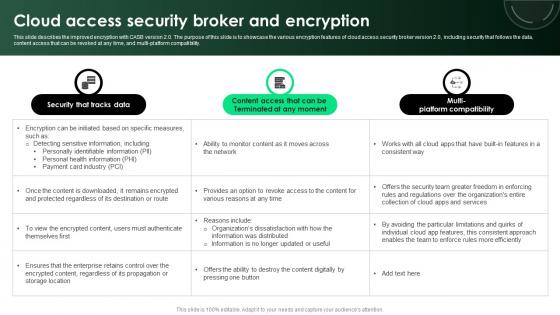
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility.
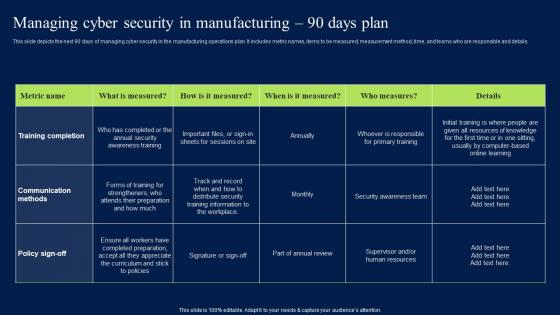
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
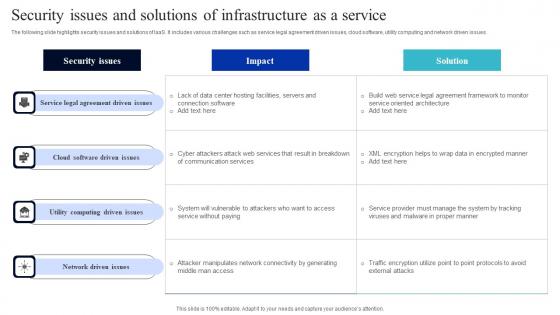
Security Issues And Solutions Of Infrastructure As A Service Summary Pdf
The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues. Showcasing this set of slides titled Security Issues And Solutions Of Infrastructure As A Service Summary Pdf. The topics addressed in these templates are Cloud Software, Utility Computing, Network Driven Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.

Effective Compliance Training For Human Resource Administration Template PDF
The purpose of this slide is to highlight compliance training for HR management. Information covered in this slide is related to workplace safety, violence and hiring and recruiting that will assist the management to create a culture of respect at workplace. Showcasing this set of slides titled Effective Compliance Training For Human Resource Administration Template PDF. The topics addressed in these templates are Workplace Safety, Workplace Violence, Hiring And Recruiting. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist For New Hires Orientation Training Program Ppt PowerPoint Presentation Gallery Backgrounds PDF
This slide will help HR in making checklist for new employee induction training program. It includes company introduction, about job, health and safety, terms and conditions of employment and equal opportunities. Showcasing this set of slides titled checklist for new hires orientation training program ppt powerpoint presentation gallery backgrounds pdf. The topics addressed in these templates are employment, terms and conditions, health and safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
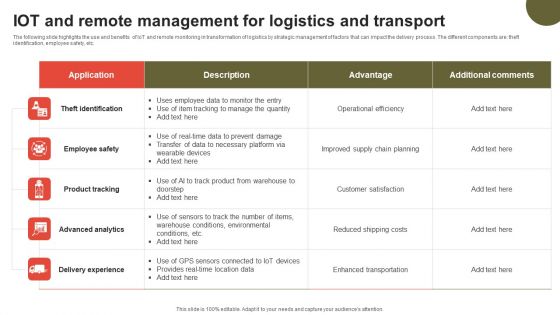
IOT And Remote Management For Logistics And Transport Topics PDF
The following slide highlights the use and benefits of IoT and remote monitoring in transformation of logistics by strategic management of factors that can impact the delivery process. The different components are theft identification, employee safety, etc. Showcasing this set of slides titled IOT And Remote Management For Logistics And Transport Topics PDF. The topics addressed in these templates are Theft Identification, Employee Safety, Product Tracking . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
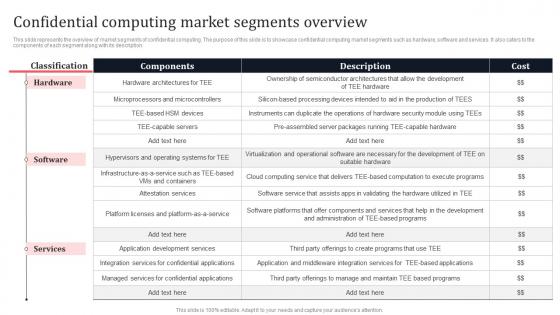
Confidential Computing Market Segments Overview Secure Multi Party Background Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Market Segments Overview Secure Multi Party Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Market Segments Overview Secure Multi Party Background Pdf This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.

Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V
This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters. Find highly impressive Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters.

Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Slidegeeks has constructed Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.
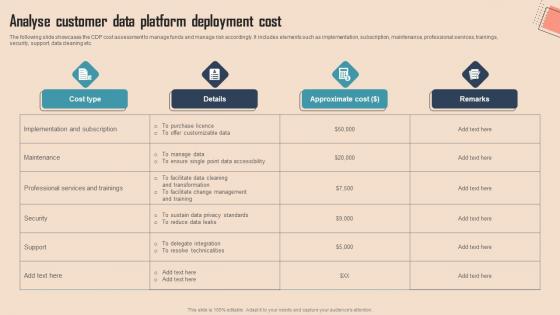
Analyse Customer Data Platform Comprehensive CDP Guide For Promoters Download Pdf
The following slide showcases the CDP cost assessment to manage funds and manage risk accordingly. It includes elements such as implementation, subscription, maintenance, professional services, trainings, security, support, data cleaning etc.Slidegeeks has constructed Analyse Customer Data Platform Comprehensive CDP Guide For Promoters Download Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide showcases the CDP cost assessment to manage funds and manage risk accordingly. It includes elements such as implementation, subscription, maintenance, professional services, trainings, security, support, data cleaning etc.

Disaster Risk Management Checklist For Recognizing And Reporting Workplace Incident Background PDF
This slide represents disaster response checklist illustrating on-scene evaluation, immediate actions and performing risk assessment for ensuring workplace safety. Showcasing this set of slides titled disaster risk management checklist for recognizing and reporting workplace incident background pdf. The topics addressed in these templates are performing risk assessment, procedure and operations, risk evaluation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

DRR Checklist For Recognizing And Reporting Workplace Incident Ppt Model Show PDF
This slide represents disaster response checklist illustrating on-scene evaluation, immediate actions and performing risk assessment for ensuring workplace safety. Showcasing this set of slides titled drr checklist for recognizing and reporting workplace incident ppt model show pdf. The topics addressed in these templates are immediate actions, performing risk assessment, building safe zone, risk evaluation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Employees Skills Training Program For Departmental Operations Icons PDF
This slide covers employees skills training program for different department operations. It includes departments such as sales, purchasing, inventory, production, inspection, HR, marketing, etc. Showcasing this set of slides titled Employees Skills Training Program For Departmental Operations Icons PDF. The topics addressed in these templates are Safety, Employee, Sales SOPs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
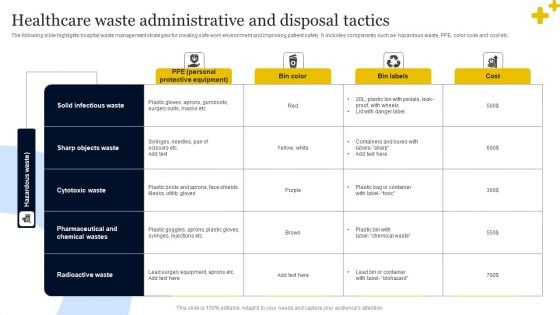
Healthcare Waste Administrative And Disposal Tactics Infographics PDF
The following slide highlights hospital waste management strategies for creating safe work environment and improving patient safety. It includes components such as- hazardous waste, PPE, color code and cost etc.. Showcasing this set of slides titled Healthcare Waste Administrative And Disposal Tactics Infographics PDF. The topics addressed in these templates are Hazardous Waste, Labels, Tactics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
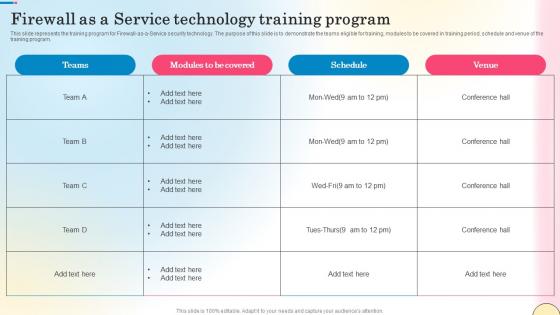
Firewall As A Service Technology Training Program Network Security Brochure Pdf
This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Firewall As A Service Technology Training Program Network Security Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Firewall As A Service Technology Training Program Network Security Brochure Pdf This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program.
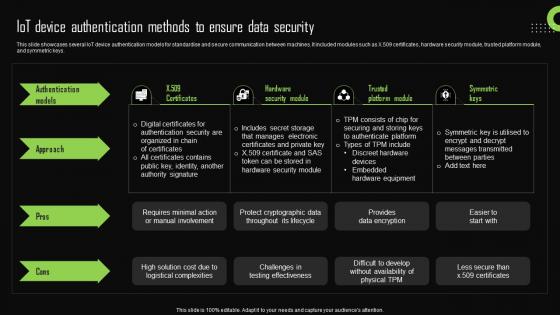
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
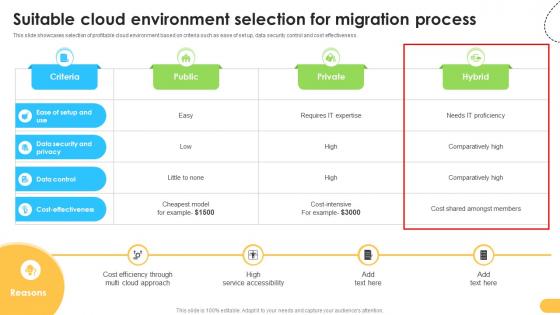
Suitable Cloud Environment Selection For Data Migration From On Premises
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Suitable Cloud Environment Selection For Data Migration From On Premises to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Suitable Cloud Environment Selection For Data Migration From On Premises. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.
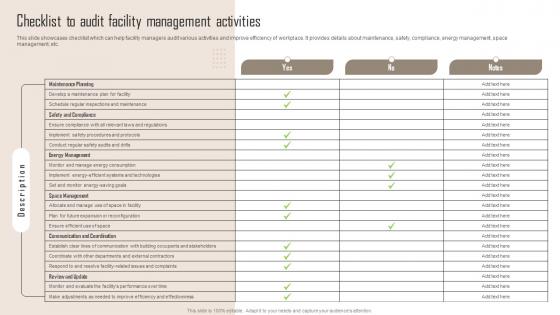
Checklist To Audit Facility Comprehensive Guide For Building Management Information Pdf
This slide showcases checklist which can help facility managers audit various activities and improve efficiency of workplace. It provides details about maintenance, safety, compliance, energy management, space management, etc. Get a simple yet stunning designed Checklist To Audit Facility Comprehensive Guide For Building Management Information Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Audit Facility Comprehensive Guide For Building Management Information Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases checklist which can help facility managers audit various activities and improve efficiency of workplace. It provides details about maintenance, safety, compliance, energy management, space management, etc.

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
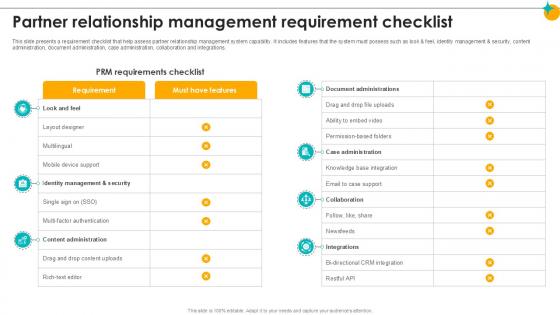
Partner Relationship Management Requirement Checklist Partner Relationship Ppt Template
This slide presents a requirement checklist that help assess partner relationship management system capability. It includes features that the system must possess such as look and feel, identity management and security, content administration, document administration, case administration, collaboration and integrations. Create an editable Partner Relationship Management Requirement Checklist Partner Relationship Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Partner Relationship Management Requirement Checklist Partner Relationship Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide presents a requirement checklist that help assess partner relationship management system capability. It includes features that the system must possess such as look and feel, identity management and security, content administration, document administration, case administration, collaboration and integrations.
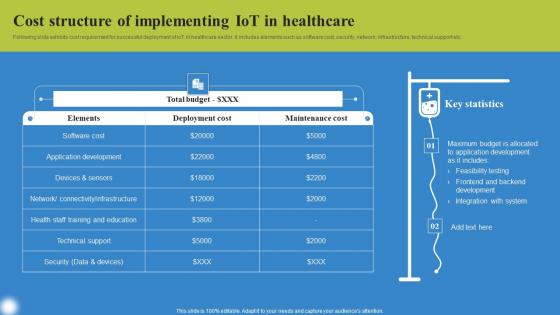
Cost Structure Of Implementing Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf
Following slide exhibits cost requirement for successful deployment of IoT in healthcare sector. It includes elements such as software cost, security, network, infrastructure, technical support etc. Slidegeeks has constructed Cost Structure Of Implementing Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. Following slide exhibits cost requirement for successful deployment of IoT in healthcare sector. It includes elements such as software cost, security, network, infrastructure, technical support etc.
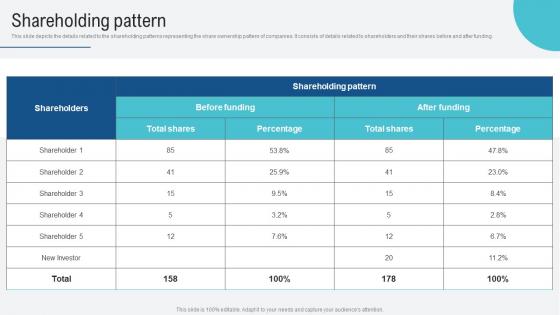
Shareholding Pattern Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem. Boost your pitch with our creative Shareholding Pattern Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem.
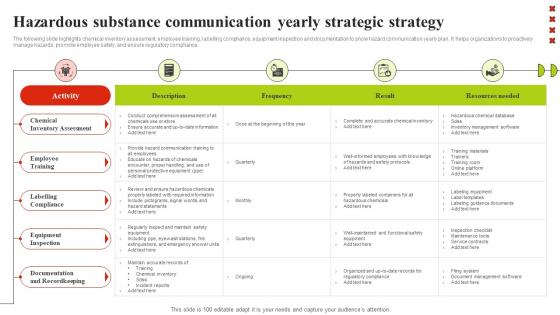
Hazardous Substance Communication Yearly Strategic Strategy Themes Pdf
The following slide highlights chemical inventory assessment, employee training, labelling compliance, equipment inspection and documentation to show hazard communication yearly plan. It helps organizations to proactively manage hazards, promote employee safety, and ensure regulatory compliance. Pitch your topic with ease and precision using this Hazardous Substance Communication Yearly Strategic Strategy Themes Pdf This layout presents information on Chemical Inventory Assessment, Employee Training It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights chemical inventory assessment, employee training, labelling compliance, equipment inspection and documentation to show hazard communication yearly plan. It helps organizations to proactively manage hazards, promote employee safety, and ensure regulatory compliance.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks.
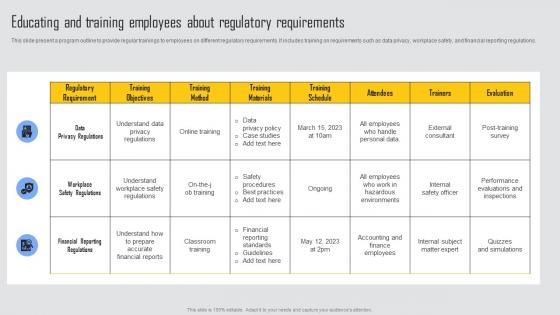
Educating And Training Employees Managing Risks And Establishing Trust Through Efficient Guidelines Pdf
This slide present a program outline to provide regular trainings to employees on different regulatory requirements. It includes training on requirements such as data privacy, workplace safety, and financial reporting regulations. Do you know about Slidesgeeks Educating And Training Employees Managing Risks And Establishing Trust Through Efficient Guidelines Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide present a program outline to provide regular trainings to employees on different regulatory requirements. It includes training on requirements such as data privacy, workplace safety, and financial reporting regulations.
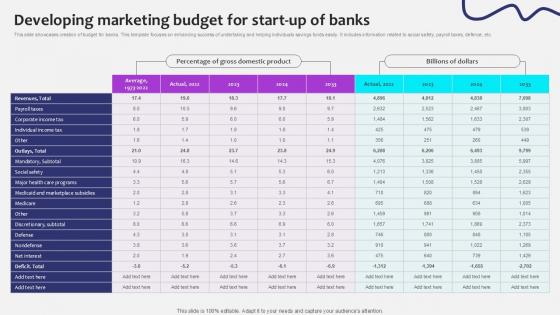
Developing Marketing Budget Initiating Globalization Of Banking Ppt Sample
This slide showcases creation of budget for banks. This template focuses on enhancing success of undertaking and helping individuals savings funds easily. It includes information related to social safety, payroll taxes, defence, etc. Slidegeeks is here to make your presentations a breeze with Developing Marketing Budget Initiating Globalization Of Banking Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases creation of budget for banks. This template focuses on enhancing success of undertaking and helping individuals savings funds easily. It includes information related to social safety, payroll taxes, defence, etc.
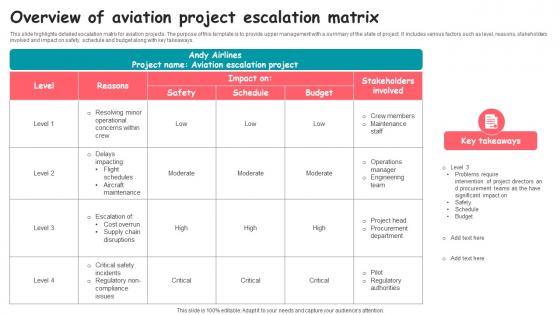
Overview Of Aviation Project Escalation Matrix Graphics pdf
This slide highlights detailed escalation matrix for aviation projects. The purpose of this template is to provide upper management with a summary of the state of project. It includes various factors such as level, reasons, stakeholders involved and impact on safety, schedule and budget along with key takeaways. Pitch your topic with ease and precision using this Overview Of Aviation Project Escalation Matrix Graphics pdf. This layout presents information on Crew Members, Maintenance Staff, Problems Require. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights detailed escalation matrix for aviation projects. The purpose of this template is to provide upper management with a summary of the state of project. It includes various factors such as level, reasons, stakeholders involved and impact on safety, schedule and budget along with key takeaways.

Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf. This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc.

Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
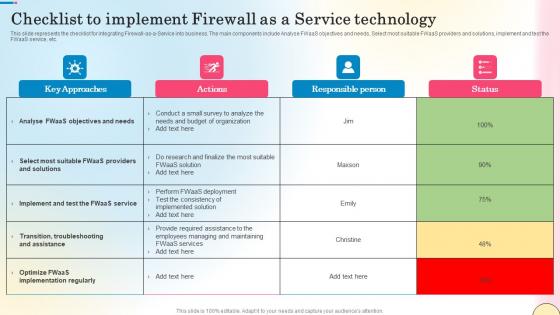
Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf
This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Find highly impressive Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc.
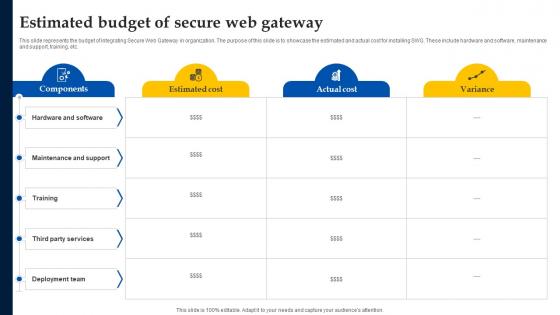
Web Access Control Solution Estimated Budget Of Secure Web Gateway
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Web Access Control Solution Estimated Budget Of Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Web Access Control Solution Estimated Budget Of Secure Web Gateway. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.
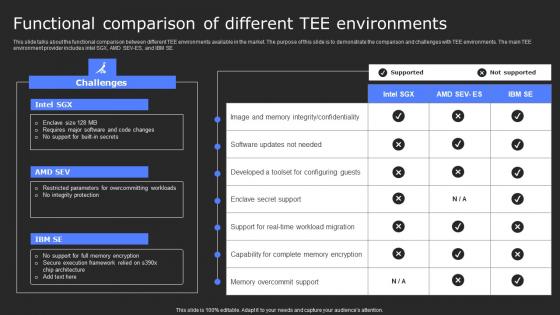
Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE. Slidegeeks has constructed Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE.

CASB 2 0 IT Training Program For Cloud Access Security Broker
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Training Program For Cloud Access Security Broker was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Training Program For Cloud Access Security Broker. This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training.
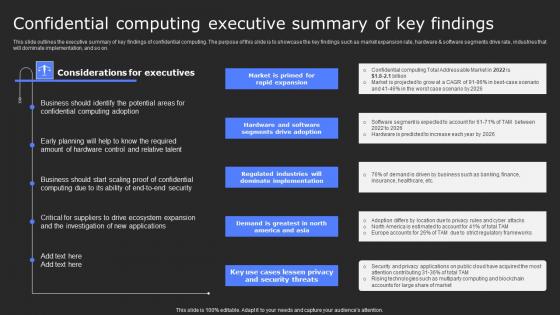
Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.


 Continue with Email
Continue with Email

 Home
Home


































