Table Of Safety Contents

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
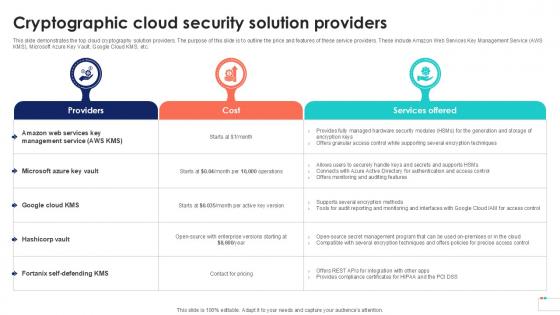
Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.

Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. Boost your pitch with our creative Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.
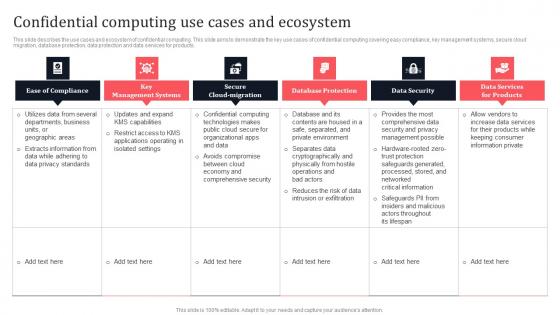
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
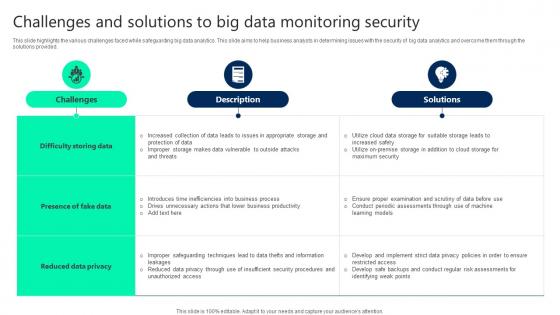
Challenges And Solutions To Big Data Monitoring Security Slides pdf
This slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided. Showcasing this set of slides titled Challenges And Solutions To Big Data Monitoring Security Slides pdf. The topics addressed in these templates are Challenges, Solutions, Difficulty Storing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided.
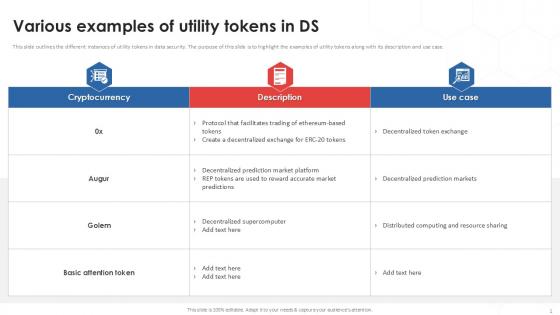
Various Examples Of Tokenization Strategies For Data Security PPT Slides
This slide outlines the different instances of utility tokens in data security. The purpose of this slide is to highlight the examples of utility tokens along with its description and use case. Boost your pitch with our creative Various Examples Of Tokenization Strategies For Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the different instances of utility tokens in data security. The purpose of this slide is to highlight the examples of utility tokens along with its description and use case.
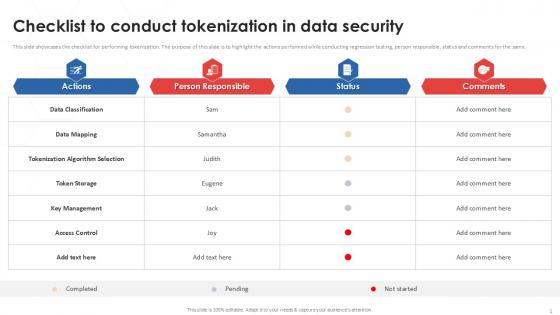
Checklist To Conduct Tokenization In Data Security PPT Presentation
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Boost your pitch with our creative Checklist To Conduct Tokenization In Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same.
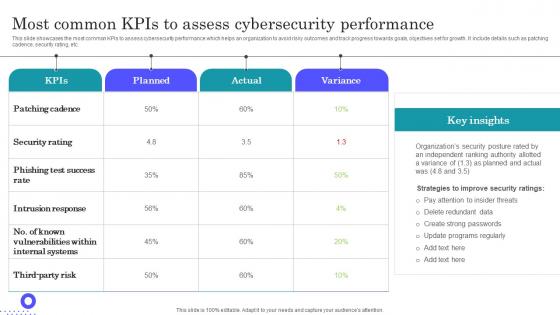
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.
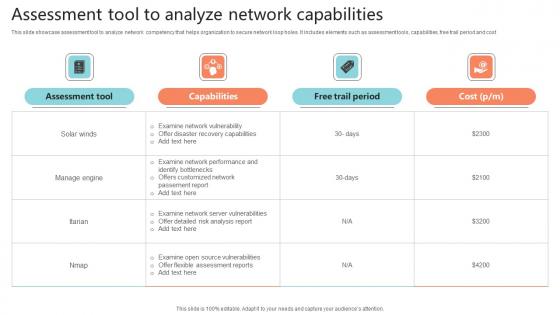
Assessment Tool To Analyze Network Capabilities Pictures Pdf
This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.Showcasing this set of slides titled Assessment Tool To Analyze Network Capabilities Pictures Pdf The topics addressed in these templates are Examine Network, Flexible Assessment, Recovery Capabilities All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.

Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf
Showcasing this set of slides titled Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf The topics addressed in these templates are Organizations Network, Security Assessments, Provides Privileged All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the benefits of using cybersecurity key performance indicators which help an organization to provide a snapshot to its relevant stakeholders, managers. It include details such as removes unknown devices on an organizations network, etc.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.
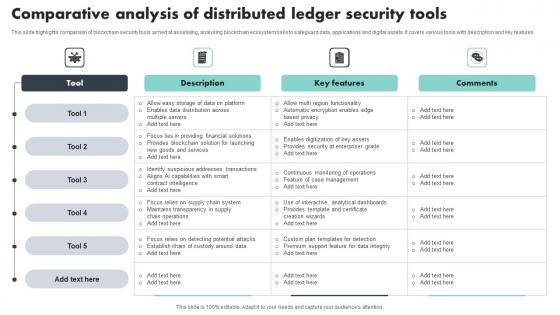
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features
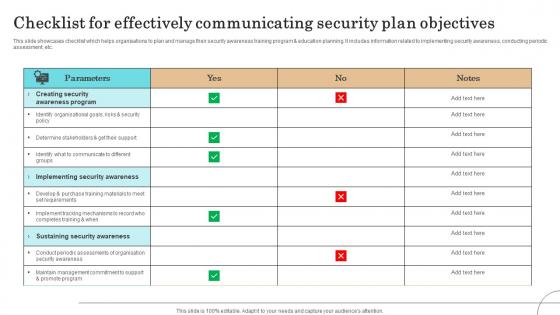
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.

Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.
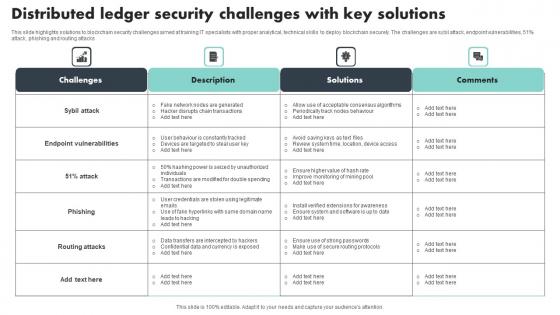
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.
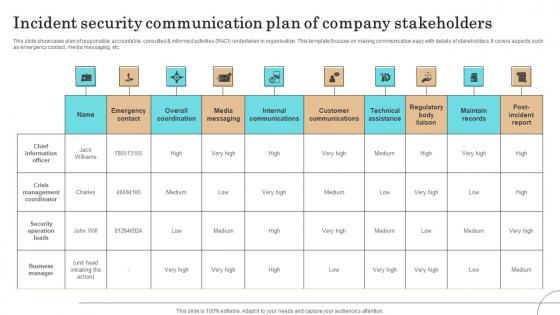
Incident Security Communication Plan Of Company Stakeholders Pictures Pdf
This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.Showcasing this set of slides titled Incident Security Communication Plan Of Company Stakeholders Pictures Pdf The topics addressed in these templates are Crisis Management Coordinator, Security Operation Leads, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc.
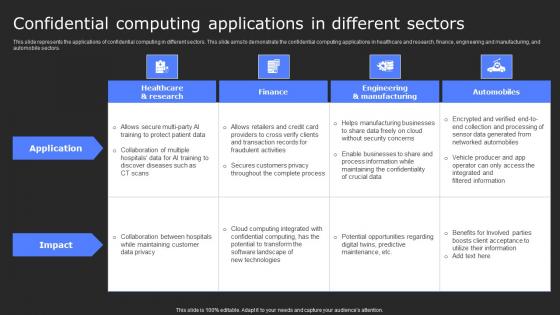
Confidential Computing Applications In Secure Computing Framework Demonstration Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Find highly impressive Confidential Computing Applications In Secure Computing Framework Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Applications In Secure Computing Framework Demonstration Pdffor your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.
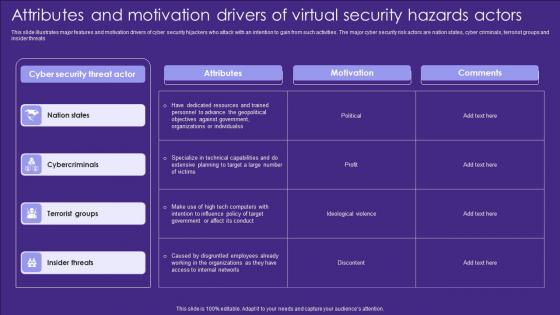
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.
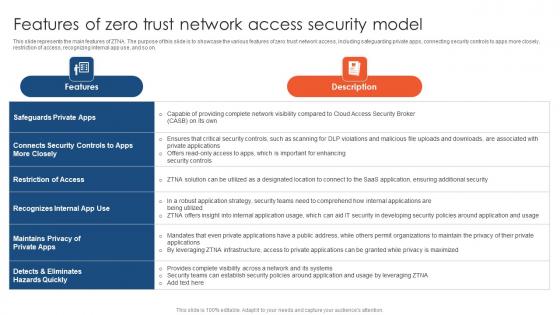
Zero Trust Network Access Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Slidegeeks has constructed Zero Trust Network Access Features Of Zero Trust Network Access Security Model after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
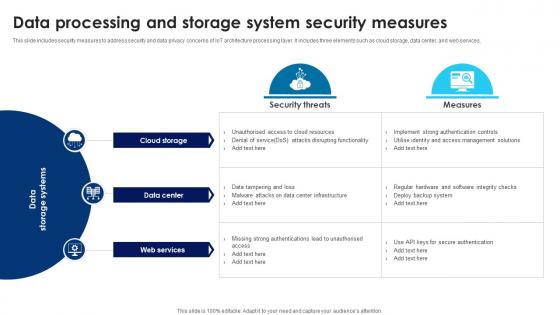
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services.

Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc.
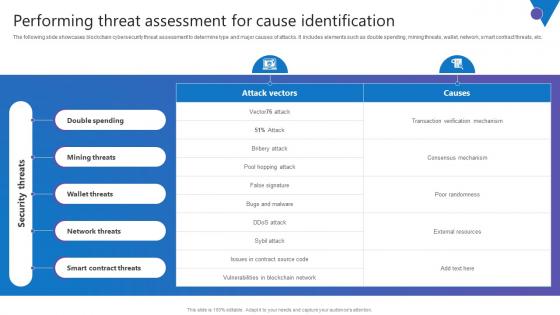
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf. The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
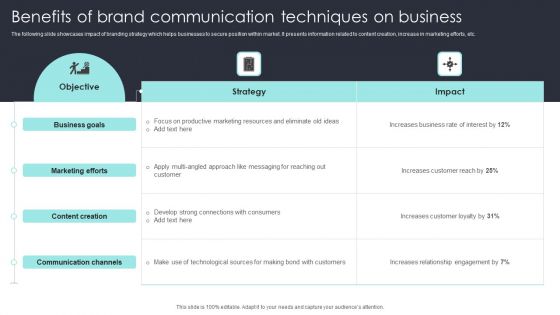
Benefits Of Brand Communication Techniques On Business Demonstration PDF
The following slide showcases impact of branding strategy which helps businesses to secure position within market. It presents information related to content creation, increase in marketing efforts, etc. Showcasing this set of slides titled Benefits Of Brand Communication Techniques On Business Demonstration PDF. The topics addressed in these templates are Marketing Efforts, Business Goals, Content Creation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Adapting To Technological Change Technological Change Management Training Microsoft Pdf
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Adapting To Technological Change Technological Change Management Training Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Adapting To Technological Change Technological Change Management Training Microsoft Pdf. This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc.
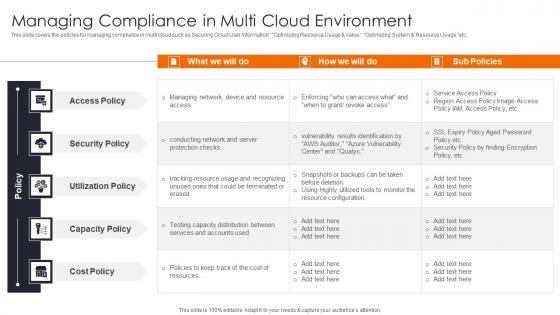
Managing Compliance In Multi Enhancing Workload Efficiency Through Cloud Architecture Download Pdf
This slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage and Value, Optimizing System and Resource Usage etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Managing Compliance In Multi Enhancing Workload Efficiency Through Cloud Architecture Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Managing Compliance In Multi Enhancing Workload Efficiency Through Cloud Architecture Download Pdf. This slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage and Value, Optimizing System and Resource Usage etc.
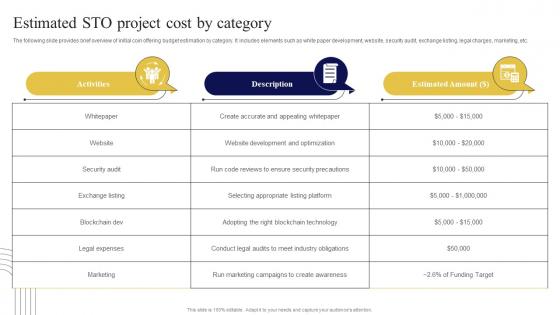
Estimated STO Project Cost By Category Exploring Investment Opportunities Designs Pdf
The following slide provides brief overview of initial coin offering budget estimation by category. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Estimated STO Project Cost By Category Exploring Investment Opportunities Designs Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Estimated Sto Project Cost By Category Exploring Investment Opportunities Designs Pdf The following slide provides brief overview of initial coin offering budget estimation by category. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.
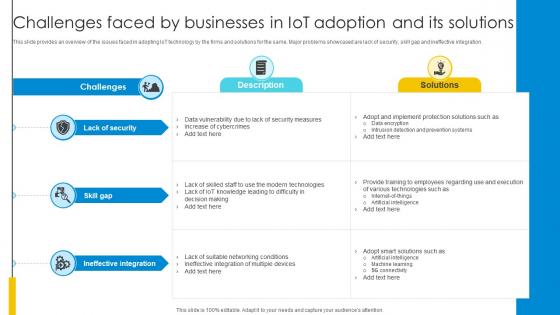
Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V
This slide provides an overview of the issues faced in adopting IoT technology by the firms and solutions for the same. Major problems showcased are lack of security, skill gap and ineffective integration. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V. This slide provides an overview of the issues faced in adopting IoT technology by the firms and solutions for the same. Major problems showcased are lack of security, skill gap and ineffective integration.
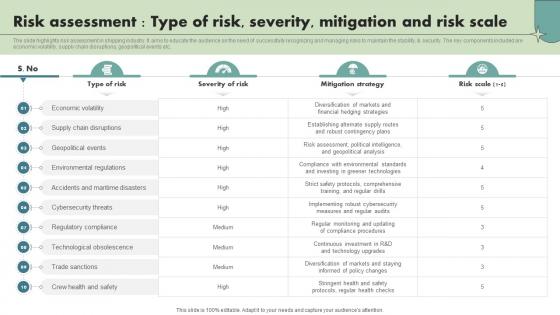
Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V
The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V. The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc.

Credit Risk Management Strategies For Complete Guide On Managing Banking Fin SS V
This slide shows details regarding the key strategies which can be used by commercial banks to mitigate credit risk. It includes strategies such as credit assessment, credit scoring models, collateral and security, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Credit Risk Management Strategies For Complete Guide On Managing Banking Fin SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Credit Risk Management Strategies For Complete Guide On Managing Banking Fin SS V This slide shows details regarding the key strategies which can be used by commercial banks to mitigate credit risk. It includes strategies such as credit assessment, credit scoring models, collateral and security, etc.
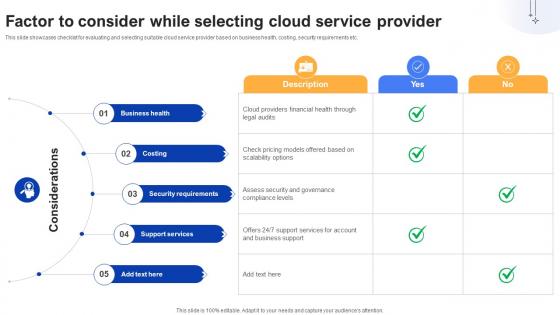
Effective Data Migration Factor To Consider While Selecting Cloud Service
This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Effective Data Migration Factor To Consider While Selecting Cloud Service to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc.
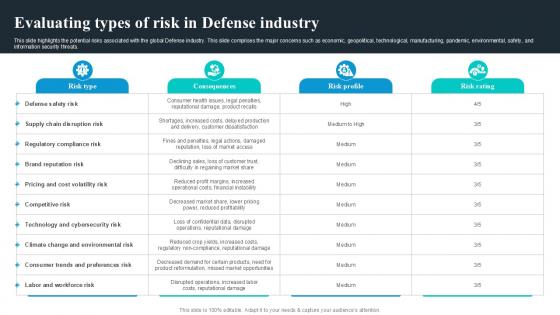
Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V
This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V can be your best option for delivering a presentation. Represent everything in detail using Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats.
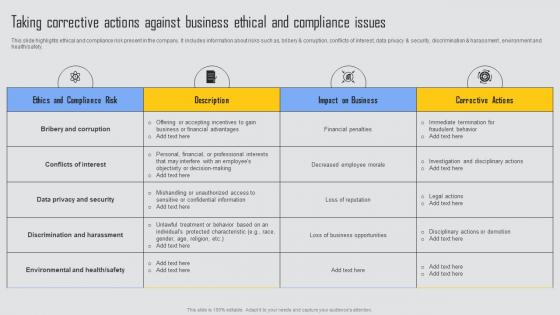
Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf
This slide highlights ethical and compliance risk present in the company. It includes information about risks such as, bribery and corruption, conflicts of interest, data privacy and security, discrimination and harassment , environment and health safety. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf today and make your presentation stand out from the rest This slide highlights ethical and compliance risk present in the company. It includes information about risks such as, bribery and corruption, conflicts of interest, data privacy and security, discrimination and harassment , environment and health safety.
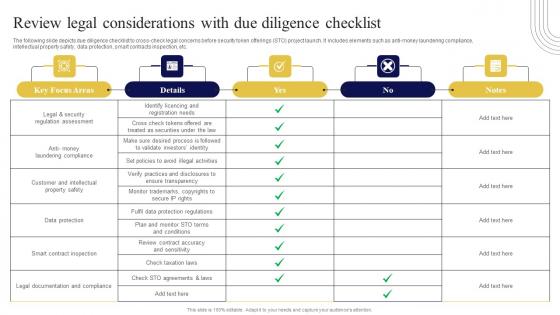
Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf
The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf today and make your presentation stand out from the rest The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
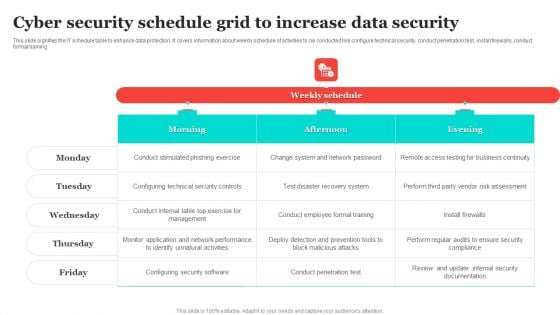
Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
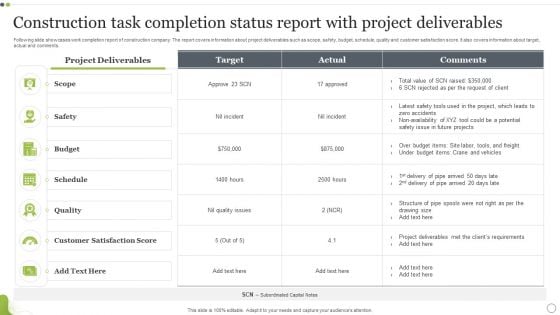
Construction Task Completion Status Report With Project Deliverables Designs PDF
Following slide showcases work completion report of construction company. The report covers information about project deliverables such as scope, safety, budget, schedule, quality and customer satisfaction score. It also covers information about target, actual and comments. Showcasing this set of slides titled Construction Task Completion Status Report With Project Deliverables Designs PDF. The topics addressed in these templates are Quality, Scope, Schedule. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
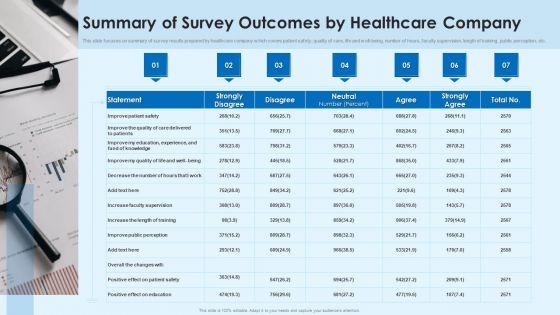
Summary Of Survey Outcomes By Healthcare Company Clipart PDF
This slide focuses on summary of survey results prepared by healthcare company which covers patient safety, quality of care, life and well-being, number of hours, faculty supervision, length of training, public perception, etc.Showcasing this set of slides titled Summary Of Survey Outcomes By Healthcare Company Clipart PDF The topics addressed in these templates are Improve Patient, Faculty Supervision, Length Of Training All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
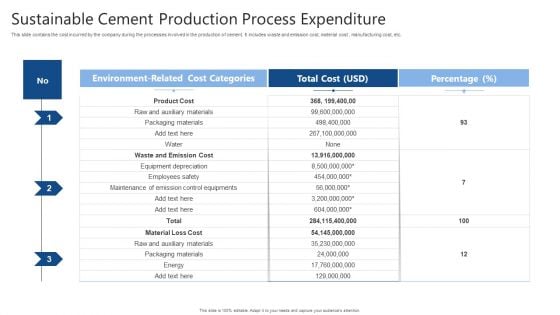
Sustainable Cement Production Process Expenditure Ppt Portfolio Deck PDF
This slide contains the cost incurred by the company during the processes involved in the production of cement. It includes waste and emission cost, material cost , manufacturing cost, etc. Showcasing this set of slides titled Sustainable Cement Production Process Expenditure Ppt Portfolio Deck PDF. The topics addressed in these templates are Product Cost, Equipment Depreciation, Employees Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Application Of Herzbergs Hygiene Theory To Improve Job Satisfaction Infographics PDF
This slide covers dual factors transforming motivation to job satisfaction for employees. It includes elements such as factors, themes and categories as job satisfiers and dissatisfiers based on professional growth, relationship with peers, health and safety, recognition and appreciation, etc. Showcasing this set of slides titled Application Of Herzbergs Hygiene Theory To Improve Job Satisfaction Infographics PDF. The topics addressed in these templates are Motivation Factors, Hygiene Factors, Job Satisfaction. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
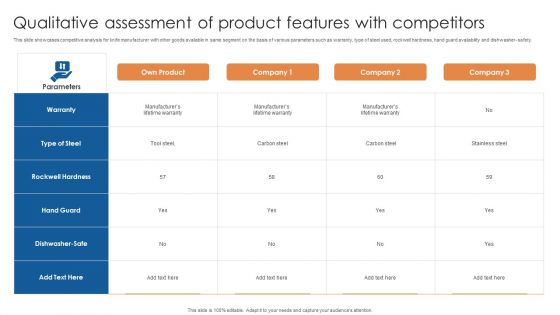
Qualitative Assessment Of Product Features With Competitors Ppt Layouts Styles PDF
This slide showcases competitive analysis for knife manufacturer with other goods available in same segment on the basis of various parameters such as warranty, type of steel used, rockwell hardness, hand guard availability and dishwasher- safety. Showcasing this set of slides titled Qualitative Assessment Of Product Features With Competitors Ppt Layouts Styles PDF. The topics addressed in these templates are Own Product, Parameters, Rockwell Hardness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Complete Beginners Guide Solutions To Protect Bitcoin Against Security Threats Fin SS V
This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc. Boost your pitch with our creative Complete Beginners Guide Solutions To Protect Bitcoin Against Security Threats Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc.

On Premise And Cloud Computing Comparison Data Migration From On Premises
This slide showcases comparative assessment between on premises and cloud storage based on cost, resources, data security, flexibility etc. Explore a selection of the finest On Premise And Cloud Computing Comparison Data Migration From On Premises here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our On Premise And Cloud Computing Comparison Data Migration From On Premises to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases comparative assessment between on premises and cloud storage based on cost, resources, data security, flexibility etc.
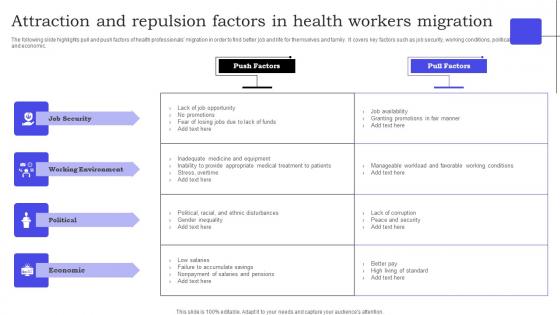
Attraction And Repulsion Factors In Health Workers Migration Information Pdf
The following slide highlights pull and push factors of health professionals migration in order to find better job and life for themselves and family. It covers key factors such as job security, working conditions, political and economic. Showcasing this set of slides titled Attraction And Repulsion Factors In Health Workers Migration Information Pdf. The topics addressed in these templates are Push Factors, Pull Factors, Job Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights pull and push factors of health professionals migration in order to find better job and life for themselves and family. It covers key factors such as job security, working conditions, political and economic.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.
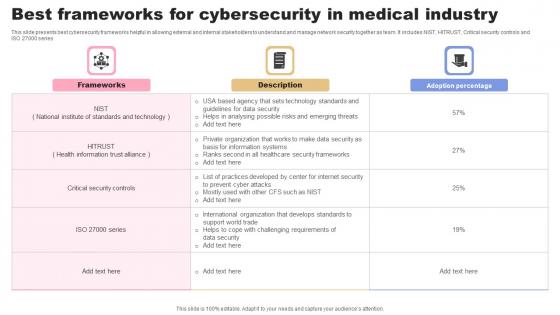
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
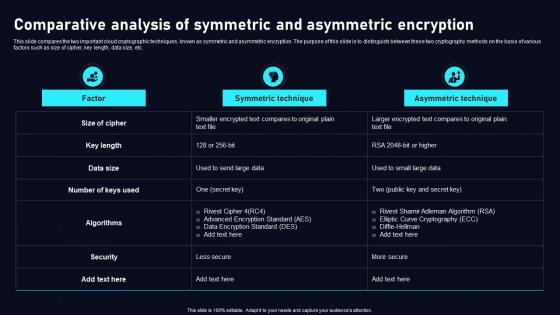
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
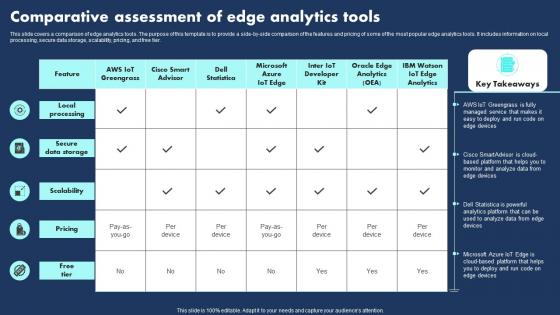
Comparative Assessment Of Edge Analytics Tools Graphics Pdf
This slide covers a comparison of edge analytics tools. The purpose of this template is to provide a side by side comparison of the features and pricing of some of the most popular edge analytics tools. It includes information on local processing, secure data storage, scalability, pricing, and free tier.Showcasing this set of slides titled Comparative Assessment Of Edge Analytics Tools Graphics Pdf The topics addressed in these templates are Local Processing, Secure Data Storage, Scalability All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers a comparison of edge analytics tools. The purpose of this template is to provide a side by side comparison of the features and pricing of some of the most popular edge analytics tools. It includes information on local processing, secure data storage, scalability, pricing, and free tier.

Implementing Robust Cybersecurity Measures To Safeguard Organizational Data DT SS V
This slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence.Boost your pitch with our creative Implementing Robust Cybersecurity Measures To Safeguard Organizational Data DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence.

Types Of Software Testing Techniques Evaluation Ppt Layouts Diagrams Pdf
This slide outlines the various analysis approaches used in software testing. It includes key types such as static testing, dynamic testing, code coverage, test case analysis, defect analysis, performance testing, security testing, test automation and exploratory testing. Showcasing this set of slides titled Types Of Software Testing Techniques Evaluation Ppt Layouts Diagrams Pdf. The topics addressed in these templates are Test Case Analysis, Defect Analysis, Performance Testing, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines the various analysis approaches used in software testing. It includes key types such as static testing,dynamic testing,code coverage,test case analysis,defect analysis,performance testing,security testing,test automation and exploratory testing.

ITIL Authorization Management Key Performance Indicators Infographics Pdf
This slide showcase KPI indicators which helps in identifying areas of improvement and align all parties involved in access management. It include KPIs such as unauthorized access setting, request access number, revoked instances and deviation in defined security policies. Showcasing this set of slides titled ITIL Authorization Management Key Performance Indicators Infographics Pdf The topics addressed in these templates are Unit Of Measures, Defined Security, Access Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase KPI indicators which helps in identifying areas of improvement and align all parties involved in access management. It include KPIs such as unauthorized access setting, request access number, revoked instances and deviation in defined security policies.

Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf
This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc. Showcasing this set of slides titled Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf. The topics addressed in these templates are Readability Checks, Performance Checks, Security Checks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc.
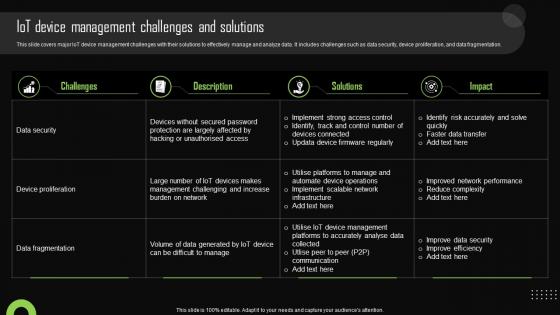
Iot Device Management Challenges And Solutions Iot Device Management Demonstration Pdf
This slide covers major IoT device management challenges with their solutions to effectively manage and analyze data. It includes challenges such as data security, device proliferation, and data fragmentation. Boost your pitch with our creative Iot Device Management Challenges And Solutions Iot Device Management Demonstration Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers major IoT device management challenges with their solutions to effectively manage and analyze data. It includes challenges such as data security, device proliferation, and data fragmentation.
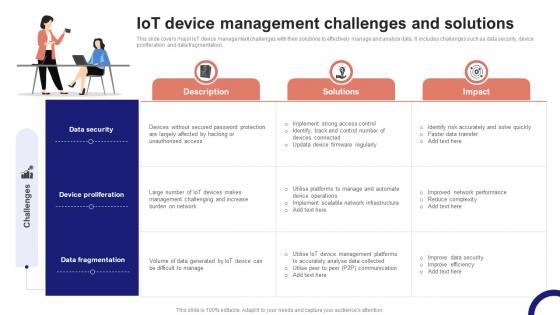
IoT Device Management Fundamentals IoT Device Management Challenges And Solutions IoT Ss V
This slide covers major IoT device management challenges with their solutions to effectively manage and analyze data. It includes challenges such as data security, device proliferation, and data fragmentation. Boost your pitch with our creative IoT Device Management Fundamentals IoT Device Management Challenges And Solutions IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers major IoT device management challenges with their solutions to effectively manage and analyze data. It includes challenges such as data security, device proliferation, and data fragmentation.

Action Steps To Tackle Edge Analytics Challenges Template Pdf
This slide covers the challenges of edge analytics in business formal language. The purpose of this template is to provide a concise overview of the challenges that organizations may face when adopting edge analytics, including data security, data privacy, latency, cost, and fragmentation.Showcasing this set of slides titled Action Steps To Tackle Edge Analytics Challenges Template Pdf The topics addressed in these templates are Processing Power Bandwidth, Integrate Manage, Promote Interoperability All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers the challenges of edge analytics in business formal language. The purpose of this template is to provide a concise overview of the challenges that organizations may face when adopting edge analytics, including data security, data privacy, latency, cost, and fragmentation.

IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V
This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc. Explore a selection of the finest IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc.


 Continue with Email
Continue with Email

 Home
Home


































