Table Of Safety Contents

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc.
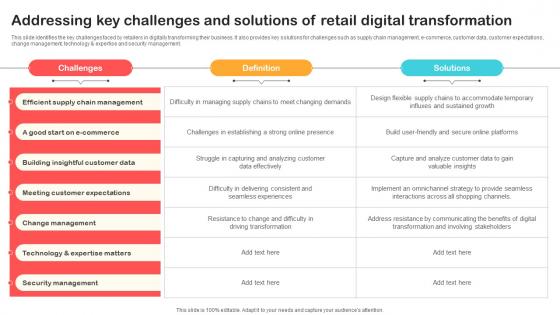
Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.
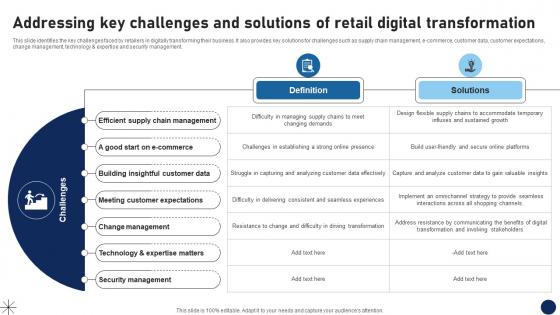
Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.

Allocation Of Funds For Finance Startup Strategy For Launching A Financial Strategy SS V
This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc. Boost your pitch with our creative Allocation Of Funds For Finance Startup Strategy For Launching A Financial Strategy SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc.
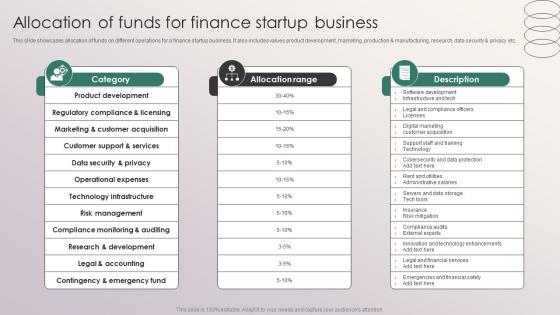
Allocation Of Funds For Finance Startup Business Penetrating Markets With Financial Strategy SS V
This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc. Boost your pitch with our creative Allocation Of Funds For Finance Startup Business Penetrating Markets With Financial Strategy SS V. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc.
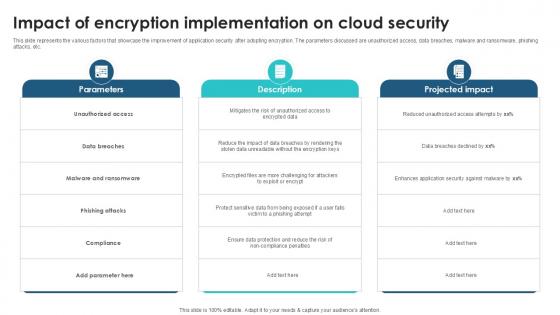
Impact Of Encryption Implementation Client Side Encryption PPT Presentation
This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Impact Of Encryption Implementation Client Side Encryption PPT Presentation to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc.
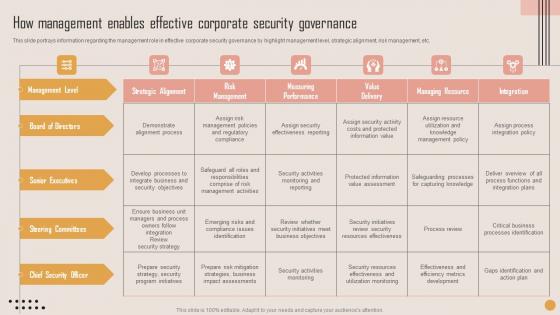
How Management Enables Effective Playbook For Strategic Actions To Improve IT Performance Topics Pdf
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created How Management Enables Effective Playbook For Strategic Actions To Improve IT Performance Topics Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc.

Emergency Response Management Action Plan With Communication Channels Elements Pdf
This slide provide information about incident management action plan to communicate it to key stakeholder. It includes elements such as IT security manager, business manger, senior management, functional head and business unit Showcasing this set of slides titled Emergency Response Management Action Plan With Communication Channels Elements Pdf The topics addressed in these templates are Incident Management Action Plan, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about incident management action plan to communicate it to key stakeholder. It includes elements such as IT security manager, business manger, senior management, functional head and business unit

Monthly Restaurant Initial Funds Estimate Professional Pdf
The following slide exhibits startup budget for restaurant which include several cost such as security deposit, licence fee, renovation, rent, salary, marketing, etc. The slide also cover one time cost, recurring costs, low estimate, and high estimates. Showcasing this set of slides titled Monthly Restaurant Initial Funds Estimate Professional Pdf. The topics addressed in these templates are Expenses, Low Estimate, High Estimate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide exhibits startup budget for restaurant which include several cost such as security deposit, licence fee, renovation, rent, salary, marketing, etc. The slide also cover one time cost, recurring costs, low estimate, and high estimates.
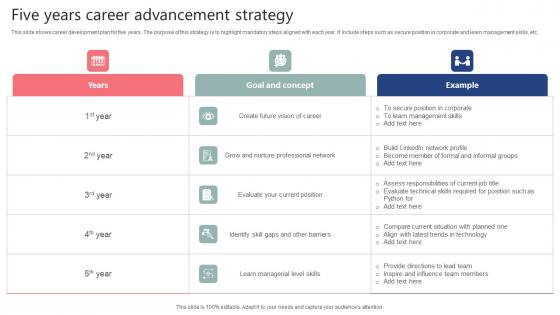
Five Years Career Advancement Strategy Diagrams Pdf
This slide shows career development plan for five years. The purpose of this strategy is to highlight mandatory steps aligned with each year. It include steps such as secure position in corporate and learn management skills, etc. Showcasing this set of slides titled Five Years Career Advancement Strategy Diagrams Pdf. The topics addressed in these templates are Years, Goal And Concept, Example. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows career development plan for five years. The purpose of this strategy is to highlight mandatory steps aligned with each year. It include steps such as secure position in corporate and learn management skills, etc.
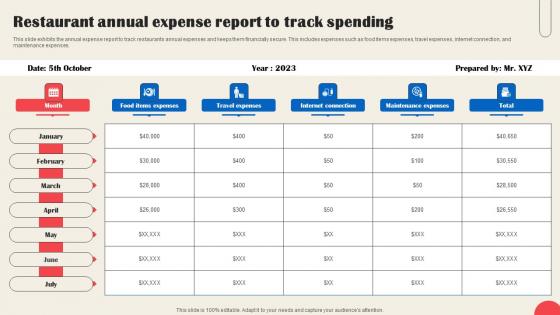
Restaurant Annual Expense Report To Track Spending Professional Pdf
This slide exhibits the annual expense report to track restaurants annual expenses and keeps them financially secure. This includes expenses such as food items expenses, travel expenses, internet connection, and maintenance expenses. Showcasing this set of slides titled Restaurant Annual Expense Report To Track Spending Professional Pdf The topics addressed in these templates are Travel Expenses, Internet Connection, Maintenance Expenses All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide exhibits the annual expense report to track restaurants annual expenses and keeps them financially secure. This includes expenses such as food items expenses, travel expenses, internet connection, and maintenance expenses.

Difference Between Hot And Cold Wallets Cryptocurrency Management With Blockchain
This slide highlights the comparison between hot and cold wallets. These are the ways to make transactions in cryptocurrency. The comparison is made on the basis of private key, security, convenience, types, suitability, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Difference Between Hot And Cold Wallets Cryptocurrency Management With Blockchain to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the comparison between hot and cold wallets. These are the ways to make transactions in cryptocurrency. The comparison is made on the basis of private key, security, convenience, types, suitability, etc.
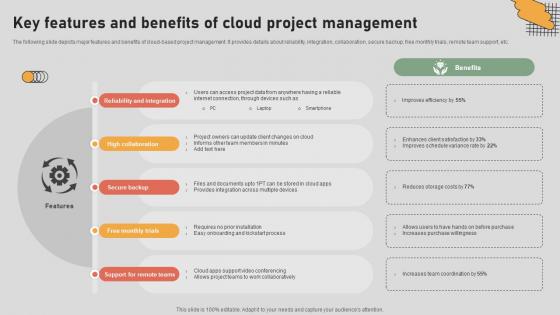
The Digital Project Managers Key Features And Benefits Of Cloud Project Management
The following slide depicts major features and benefits of cloud-based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc. Explore a selection of the finest The Digital Project Managers Key Features And Benefits Of Cloud Project Management here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our The Digital Project Managers Key Features And Benefits Of Cloud Project Management to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide depicts major features and benefits of cloud-based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc.

Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

Categories Of Issues And Risks In Cloud Computing PPT Slide SS
This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Categories Of Issues And Risks In Cloud Computing PPT Slide SS to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance.
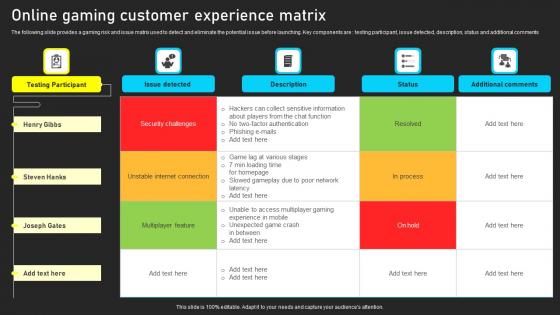
Online Gaming Customer Experience Matrix Guidelines Pdf
The following slide provides a gaming risk and issue matrix used to detect and eliminate the potential issue before launching. Key components are testing participant, issue detected, description, status and additional comments Showcasing this set of slides titled Online Gaming Customer Experience Matrix Guidelines Pdf. The topics addressed in these templates are Security Challenges, Unstable Internet Connection, Multiplayer Feature. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides a gaming risk and issue matrix used to detect and eliminate the potential issue before launching. Key components are testing participant, issue detected, description, status and additional comments
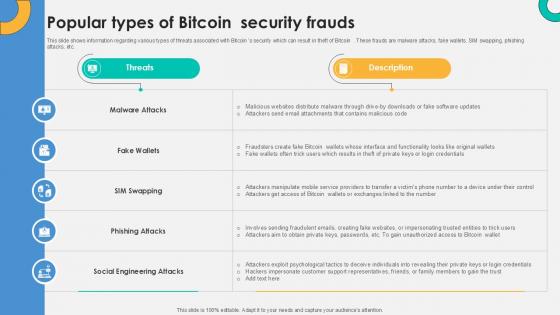
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
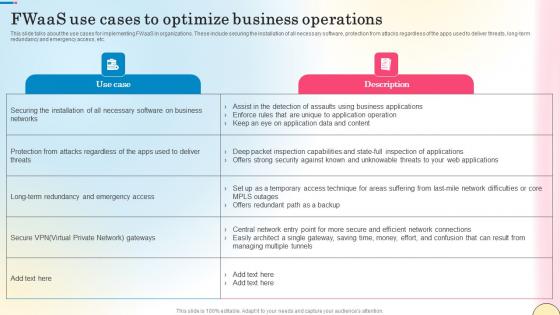
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.
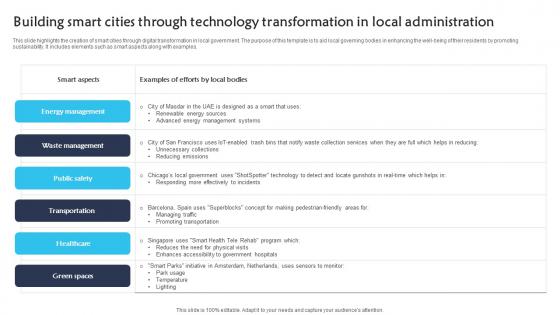
Building Smart Cities Through Technology Transformation In Local Administration Themes pdf
This slide highlights the creation of smart cities through digital transformation in local government. The purpose of this template is to aid local governing bodies in enhancing the well-being of their residents by promoting sustainability. It includes elements such as smart aspects along with examples. Pitch your topic with ease and precision using this Building Smart Cities Through Technology Transformation In Local Administration Themes pdf. This layout presents information on Energy Management, Waste Management, Public Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the creation of smart cities through digital transformation in local government. The purpose of this template is to aid local governing bodies in enhancing the well-being of their residents by promoting sustainability. It includes elements such as smart aspects along with examples.
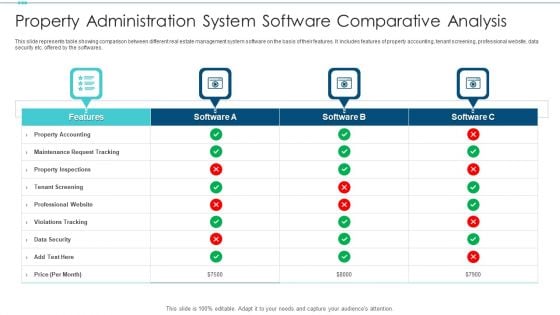
Property Administration System Software Comparative Analysis Formats PDF
This slide represents table showing comparison between different real estate management system software on the basis of their features. It includes features of property accounting, tenant screening, professional website, data security etc. offered by the softwares. Pitch your topic with ease and precision using this property administration system software comparative analysis formats pdf. This layout presents information on property accounting, data security, tenant screening. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
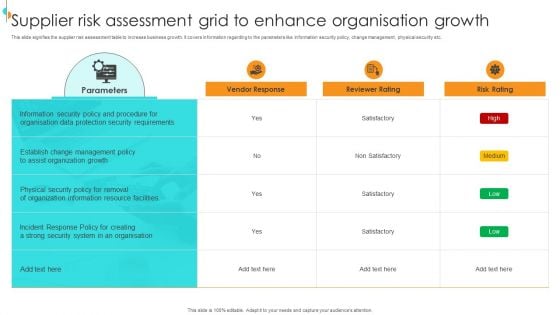
Supplier Risk Assessment Grid To Enhance Organisation Growth Download PDF
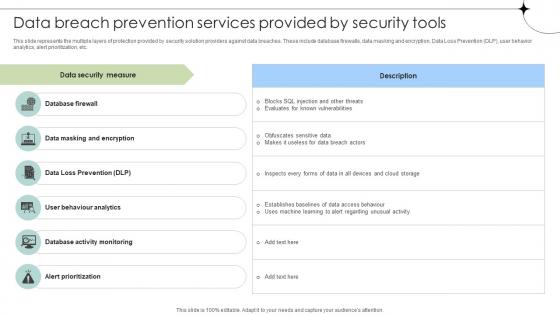
Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.

Zero Trust Model Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Boost your pitch with our creative Zero Trust Model Role Of ZTNA To Improve Business Operations And Security. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.

Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Boost your pitch with our creative Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.
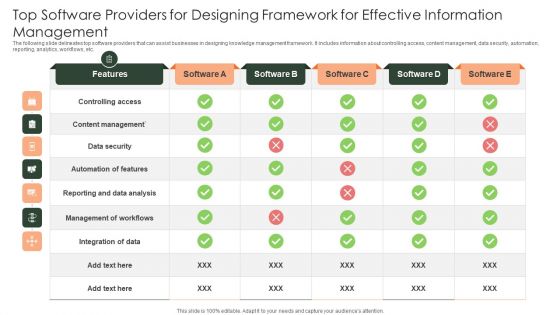
Top Software Providers For Designing Framework For Effective Information Management Slides PDF
The following slide delineates top software providers that can assist businesses in designing knowledge management framework. It includes information about controlling access, content management, data security, automation, reporting, analytics, workflows, etc. Showcasing this set of slides titled Top Software Providers For Designing Framework For Effective Information Management Slides PDF. The topics addressed in these templates are Content Management, Data Security, Controlling Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide.
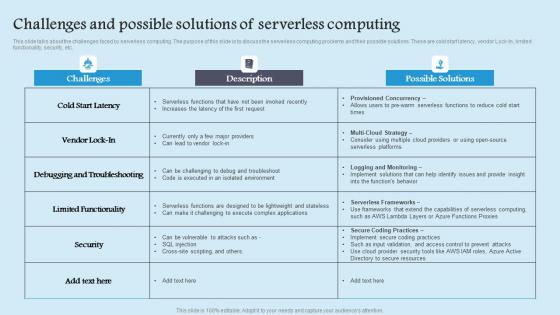
Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf
This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc.
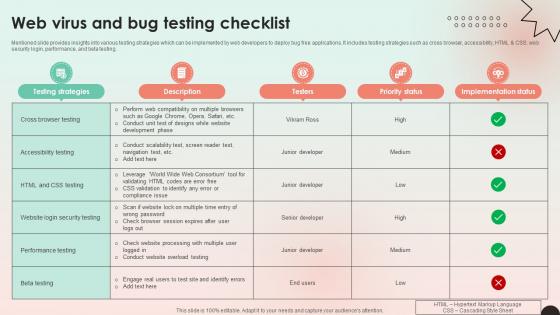
Web Consulting Business Web Virus And Bug Testing Checklist
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. Explore a selection of the finest Web Consulting Business Web Virus And Bug Testing Checklist here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Consulting Business Web Virus And Bug Testing Checklist to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing.

Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V
This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges. Find highly impressive Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges.
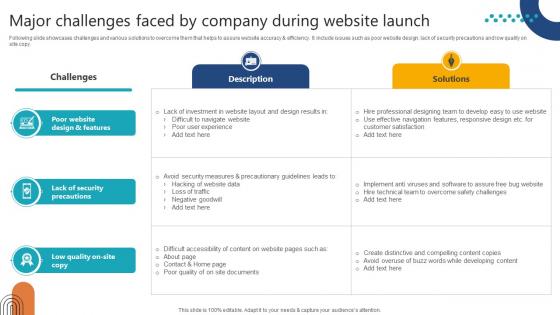
Complete Guide To Launch Major Challenges Faced By Company During Website
Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy. Explore a selection of the finest Complete Guide To Launch Major Challenges Faced By Company During Website here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Complete Guide To Launch Major Challenges Faced By Company During Website to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy.

Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V
This slide covers issues highlighting common challenges associated with software wallets. The purpose of this template is to potential solutions to enhance their efficiency for risks such as security risks, user error and loss, compatibility issues along with description and solutions. Find highly impressive Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Mastering Blockchain Wallets Challenges With Solutions For Improving Efficiency BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers issues highlighting common challenges associated with software wallets. The purpose of this template is to potential solutions to enhance their efficiency for risks such as security risks, user error and loss, compatibility issues along with description and solutions.
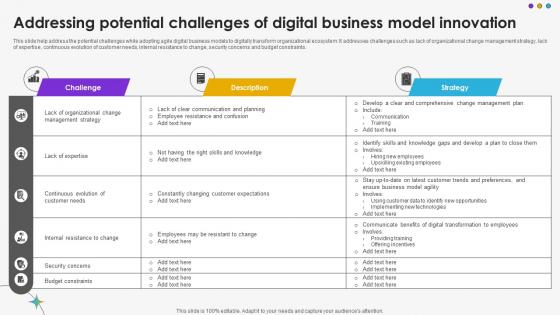
Addressing Potential Challenges Of Digital Business Model Innovation DT SS V
This slide help address the potential challenges while adopting agile digital business models to digitally transform organizational ecosystem. It addresses challenges such as lack of organizational change management strategy, lack of expertise, continuous evolution of customer needs, internal resistance to change, security concerns and budget constraints.Boost your pitch with our creative Addressing Potential Challenges Of Digital Business Model Innovation DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide help address the potential challenges while adopting agile digital business models to digitally transform organizational ecosystem. It addresses challenges such as lack of organizational change management strategy, lack of expertise, continuous evolution of customer needs, internal resistance to change, security concerns and budget constraints.
Weekly Workforce Productivity Tracking Report Structure PDF
The following slide depicts the insights of marketing work stream to monitor its progress. It includes elements such as activities, due date, reported person, planned and actual hours etc. Showcasing this set of slides titled Weekly Workforce Productivity Tracking Report Structure PDF. The topics addressed in these templates areDesign Marketing Campaign, Securing Database, Evaluate Campaign Results. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
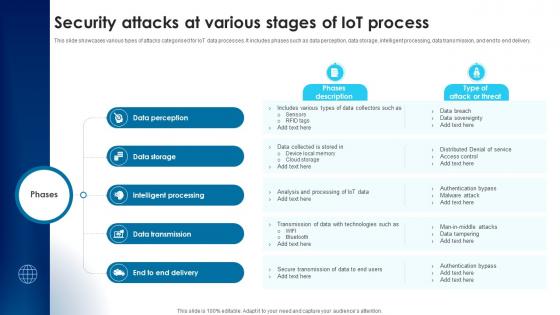
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc.
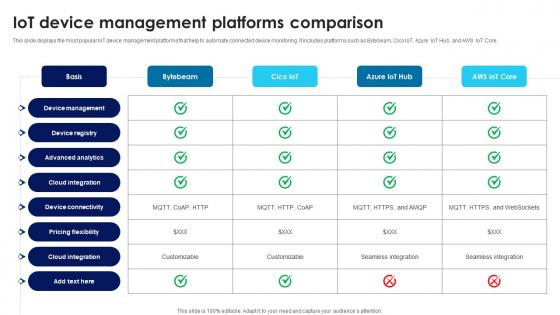
Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V
This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core. The Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core.
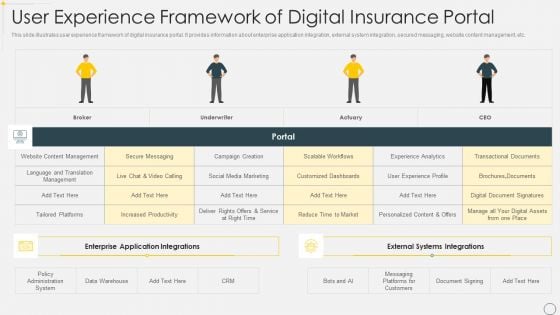
User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Essential Trainings To Employees Increased Superiority For Food Products Information PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees increased superiority for food products information pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Multi Unit Residential Building Facility Management Services Sample PDF
This slide showcases the facility services at muti unit residential building which includes service area of energy, health and wellbeing, access and egress, security, safety, water services and HVAC. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Multi Unit Residential Building Facility Management Services Sample PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
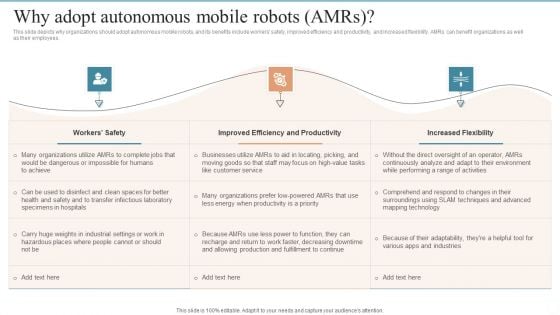
AMR Robot Why Adopt Autonomous Mobile Robots Amrs Ppt PowerPoint Presentation File Styles PDF
This slide depicts why organizations should adopt autonomous mobile robots, and its benefits include workers safety, improved efficiency and productivity, and increased flexibility. AMRs can benefit organizations as well as their employees. Find highly impressive AMR Robot Why Adopt Autonomous Mobile Robots Amrs Ppt PowerPoint Presentation File Styles PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download AMR Robot Why Adopt Autonomous Mobile Robots Amrs Ppt PowerPoint Presentation File Styles PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Why Adopt Autonomous Mobile Robots Amrs Template PDF
This slide depicts why organizations should adopt autonomous mobile robots, and its benefits include workers safety, improved efficiency and productivity, and increased flexibility. AMRs can benefit organizations as well as their employees. Find highly impressive Why Adopt Autonomous Mobile Robots Amrs Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Why Adopt Autonomous Mobile Robots Amrs Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses
This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Present like a pro with Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc.
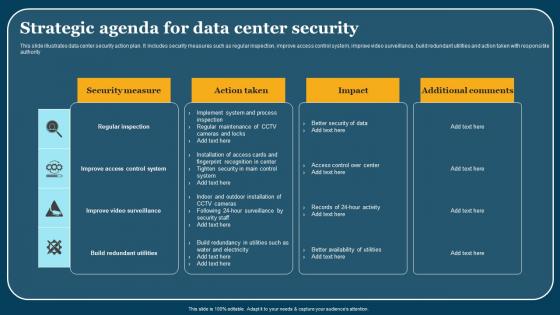
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
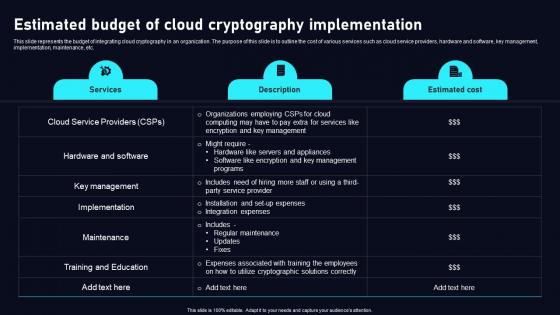
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
Essential Trainings To Employees Food Security Excellence Ppt Professional Icons PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees food security excellence ppt professional icons pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Trainings To Employees Application Of Quality Management For Food Processing Companies Ideas PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees application of quality management for food processing companies ideas pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Trainings To Employees Assuring Food Quality And Hygiene Template PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees assuring food quality and hygiene template pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Trainings To Employees Uplift Food Production Company Quality Standards Pictures PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees uplift food production company quality standards pictures pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
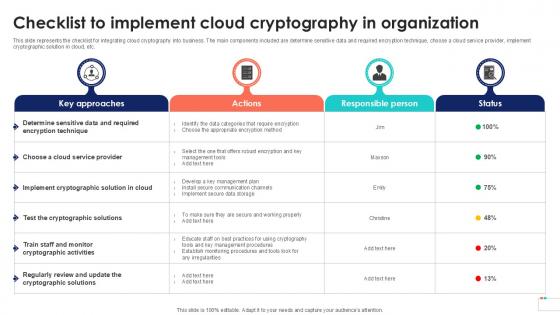
Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
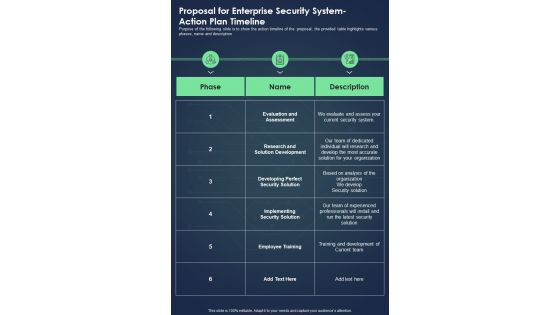
Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document
Purpose of the following slide is to show the action timeline of the proposal, the provided table highlights various phases, name and description Presenting you an exemplary Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Action Plan Timeline One Pager Sample Example Document brilliant piece now.
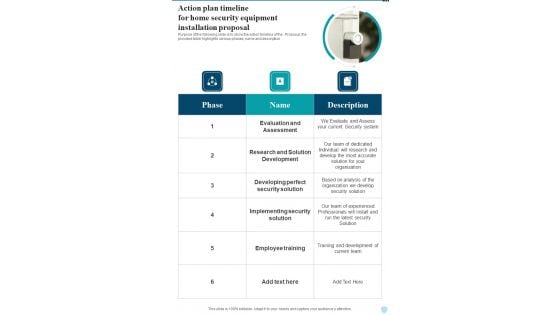
Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document
Purpose of the following slide is to show the action timeline of the Proposal, the provided table highlights various phases, name and description. Presenting you an exemplary Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Find highly impressive Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.


 Continue with Email
Continue with Email

 Home
Home


































