Table

Rebalancing Approaches To Optimize Asset Allocation Strategic Investment Plan For Optimizing Risk SS V
This slide presents various types of rebalancing approaches to adjusting a portfolios changed asset allocation to match an original allocation defined by an investors risk and reward profile. It includes types such as smart beta, constant-mix, constant proportion and calendar rebalancing.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Rebalancing Approaches To Optimize Asset Allocation Strategic Investment Plan For Optimizing Risk SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Rebalancing Approaches To Optimize Asset Allocation Strategic Investment Plan For Optimizing Risk SS V today and make your presentation stand out from the rest This slide presents various types of rebalancing approaches to adjusting a portfolios changed asset allocation to match an original allocation defined by an investors risk and reward profile. It includes types such as smart beta, constant-mix, constant proportion and calendar rebalancing.
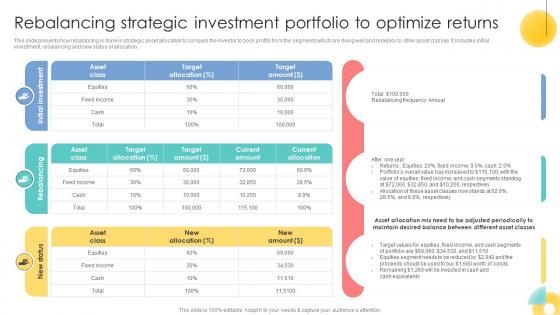
Rebalancing Strategic Investment Portfolio To Strategic Investment Plan For Optimizing Risk SS V
This slide presents how rebalancing is done in strategic asset allocation to compels the investor to book profits from the segments which are doing well and redeploy to other asset classes. It includes initial investment, rebalancing and new status of allocation.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Rebalancing Strategic Investment Portfolio To Strategic Investment Plan For Optimizing Risk SS V can be your best option for delivering a presentation. Represent everything in detail using Rebalancing Strategic Investment Portfolio To Strategic Investment Plan For Optimizing Risk SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents how rebalancing is done in strategic asset allocation to compels the investor to book profits from the segments which are doing well and redeploy to other asset classes. It includes initial investment, rebalancing and new status of allocation.
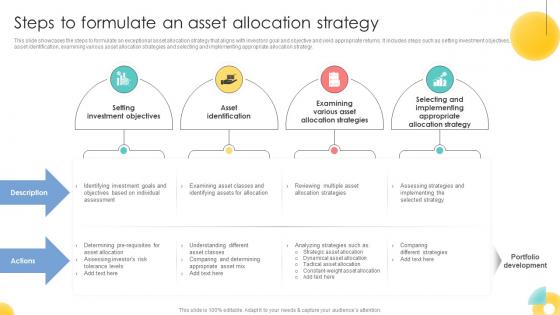
Steps To Formulate An Asset Allocation Strategy Strategic Investment Plan For Optimizing Risk SS V
This slide showcases the steps to formulate an exceptional asset allocation strategy that aligns with investors goal and objective and yield appropriate returns. It includes steps such as setting investment objectives,asset identification, examining various asset allocation strategies and selecting and implementing appropriate allocation strategy.Find highly impressive Steps To Formulate An Asset Allocation Strategy Strategic Investment Plan For Optimizing Risk SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Formulate An Asset Allocation Strategy Strategic Investment Plan For Optimizing Risk SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the steps to formulate an exceptional asset allocation strategy that aligns with investors goal and objective and yield appropriate returns. It includes steps such as setting investment objectives,asset identification, examining various asset allocation strategies and selecting and implementing appropriate allocation strategy.

Steps To Implement Integrated Asset Allocation Strategic Investment Plan For Optimizing Risk SS V
This slide showcases the steps involved in the integrated asset allocation process. It examines projected net worth assets minus obligations and the standard deviation of future net worth, assuming that the investor is prepared to accept further net worth risk in order to improve expected net worth.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Integrated Asset Allocation Strategic Investment Plan For Optimizing Risk SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the steps involved in the integrated asset allocation process. It examines projected net worth assets minus obligations and the standard deviation of future net worth, assuming that the investor is prepared to accept further net worth risk in order to improve expected net worth.
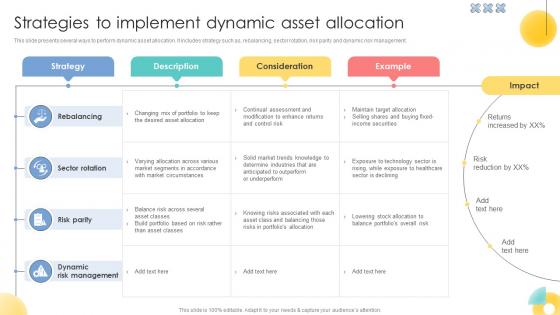
Strategies To Implement Dynamic Asset Allocation Strategic Investment Plan For Optimizing Risk SS V
This slide presents several ways to perform dynamic asset allocation. It includes strategy such as, rebalancing, sector rotation, risk parity and dynamic risk management.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies To Implement Dynamic Asset Allocation Strategic Investment Plan For Optimizing Risk SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies To Implement Dynamic Asset Allocation Strategic Investment Plan For Optimizing Risk SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide presents several ways to perform dynamic asset allocation. It includes strategy such as, rebalancing, sector rotation, risk parity and dynamic risk management.
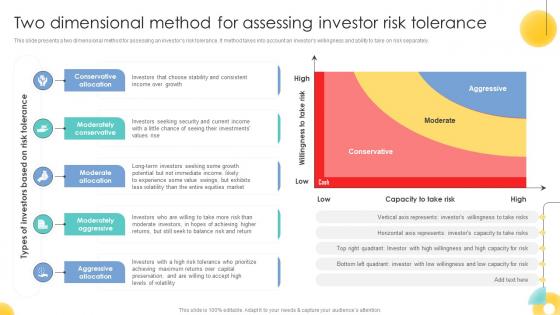
Two Dimensional Method For Assessing Investor Risk Tolerance Strategic Investment Plan For Optimizing Risk SS V
This slide presents a two dimensional method for assessing an investors risk tolerance. It method takes into account an investors willingness and ability to take on risk separately. This modern and well-arranged Two Dimensional Method For Assessing Investor Risk Tolerance Strategic Investment Plan For Optimizing Risk SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide presents a two dimensional method for assessing an investors risk tolerance. It method takes into account an investors willingness and ability to take on risk separately.

A51 Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Want to ace your presentation in front of a live audience Our A51 Zero Trust Network Access Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on

Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Get a simple yet stunning designed Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Zero Trust Exchange Overview And Benefits Zero Trust Network Access
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Exchange Overview And Benefits Zero Trust Network Access and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.

Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions. This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Explore a selection of the finest Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.

Zero Trust Network Access Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Difference Between ZTNA And Software Defined Perimeter from Slidegeeks and deliver a wonderful presentation. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
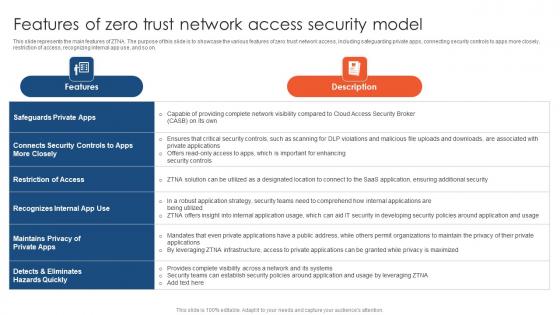
Zero Trust Network Access Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Slidegeeks has constructed Zero Trust Network Access Features Of Zero Trust Network Access Security Model after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Network Access Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Do you know about Slidesgeeks Zero Trust Network Access Main Pillars Of Zero Network Trust Access These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
Zero Trust Network Access Performance Tracking Dashboard
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Performance Tracking Dashboard can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges today and make your presentation stand out from the rest This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
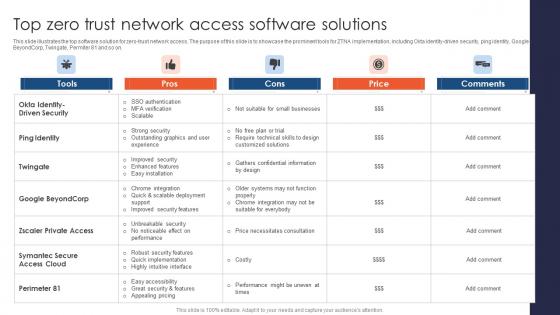
Zero Trust Network Access Top Zero Trust Network Access Software Solutions
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. This modern and well-arranged Zero Trust Network Access Top Zero Trust Network Access Software Solutions provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Welcome to our selection of the Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Retrieve professionally designed Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
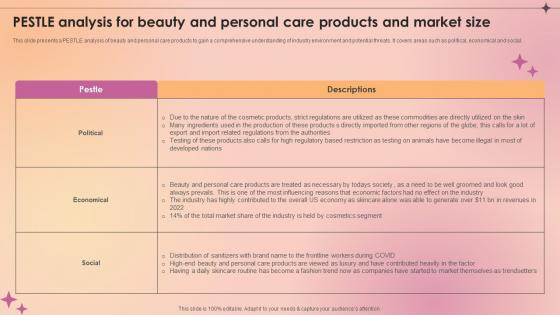
Pestle Analysis For Beauty And Personal Care Products Makeup And Skincare Market IR SS V
This slide presents a PESTLE analysis of beauty and personal care products to gain a comprehensive understanding of industry environment and potential threats. It covers areas such as political, economical and social. This Pestle Analysis For Beauty And Personal Care Products Makeup And Skincare Market IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Pestle Analysis For Beauty And Personal Care Products Makeup And Skincare Market IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide presents a PESTLE analysis of beauty and personal care products to gain a comprehensive understanding of industry environment and potential threats. It covers areas such as political, economical and social.
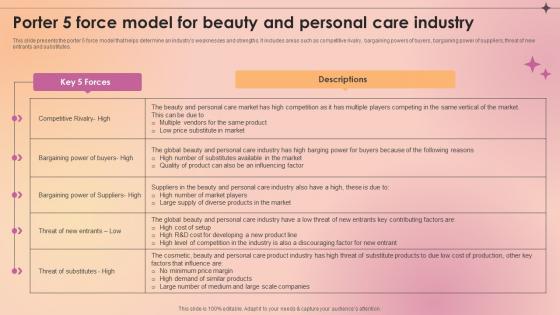
Porter 5 Force Model For Beauty And Personal Care Industry Makeup And Skincare Market IR SS V
This slide presents the porter 5 force model that helps determine an industrys weaknesses and strengths. It includes areas such as competitive rivalry, bargaining powers of buyers, bargaining power of suppliers, threat of new entrants and substitutes. Welcome to our selection of the Porter 5 Force Model For Beauty And Personal Care Industry Makeup And Skincare Market IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide presents the porter 5 force model that helps determine an industrys weaknesses and strengths. It includes areas such as competitive rivalry, bargaining powers of buyers, bargaining power of suppliers, threat of new entrants and substitutes.

CASB 2 0 IT API Based Use Cases Of CASB Deployment
This slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT API Based Use Cases Of CASB Deployment for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on.
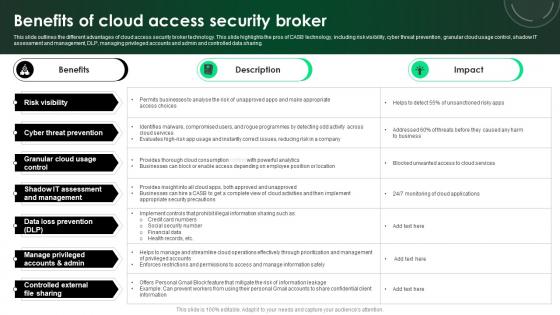
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing.

CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Get a simple yet stunning designed CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.
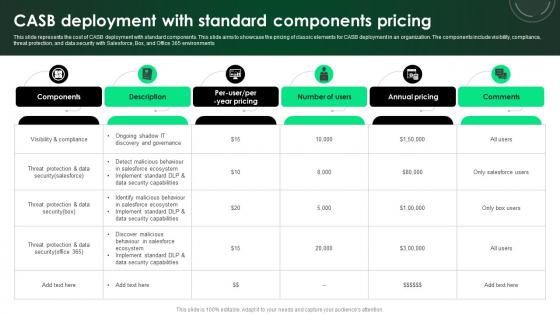
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
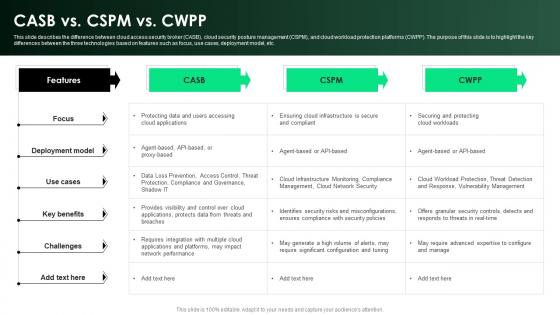
CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts
This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc.
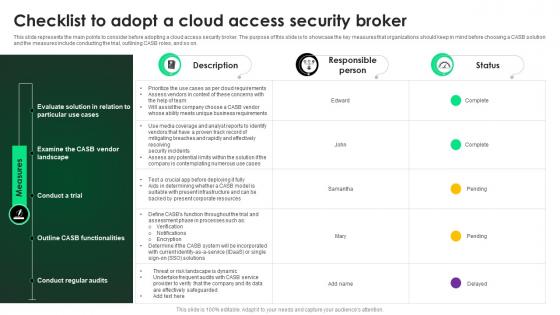
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.
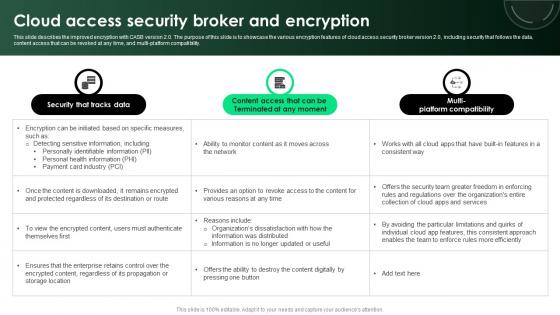
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility.

CASB 2 0 IT Cloud Access Security Broker Architectural Components
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. This modern and well-arranged CASB 2 0 IT Cloud Access Security Broker Architectural Components provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on.

CASB 2 0 IT Cloud Security Standards And Control Frameworks
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. This CASB 2 0 IT Cloud Security Standards And Control Frameworks from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA.
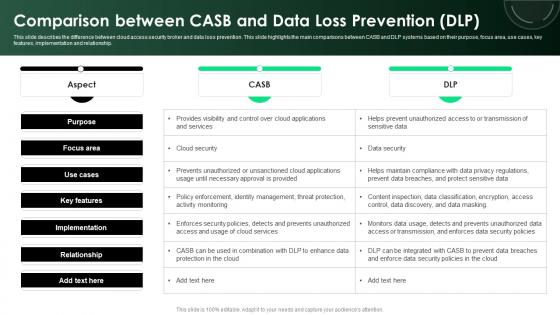
CASB 2 0 IT Comparison Between CASB And Data Loss Prevention DLP
This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. Take your projects to the next level with our ultimate collection of CASB 2 0 IT Comparison Between CASB And Data Loss Prevention DLP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship.
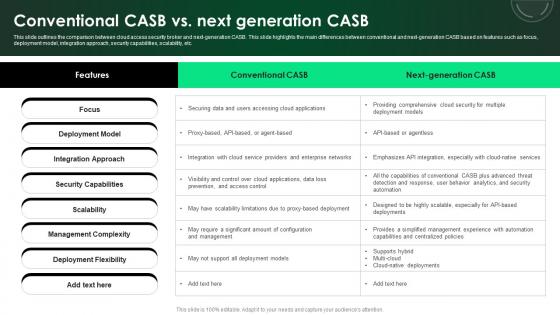
CASB 2 0 IT Conventional CASB Vs Next Generation CASB
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Find a pre-designed and impeccable CASB 2 0 IT Conventional CASB Vs Next Generation CASB. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.

CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model
This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Want to ace your presentation in front of a live audience Our CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc.

CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc.
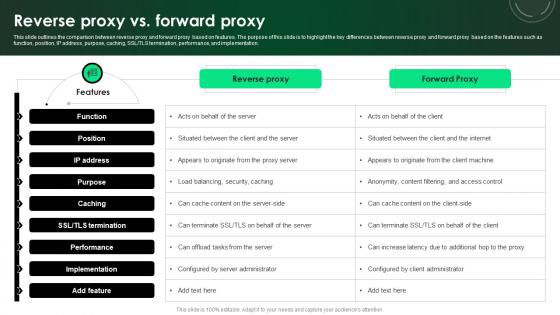
CASB 2 0 IT Reverse Proxy Vs Forward Proxy
This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT Reverse Proxy Vs Forward Proxy is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT Reverse Proxy Vs Forward Proxy and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.

CASB 2 0 IT Training Program For Cloud Access Security Broker
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Training Program For Cloud Access Security Broker was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Training Program For Cloud Access Security Broker. This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training.

CASB 2 0 IT Why CASB Is Important For Businesses
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. This CASB 2 0 IT Why CASB Is Important For Businesses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Why CASB Is Important For Businesses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management.
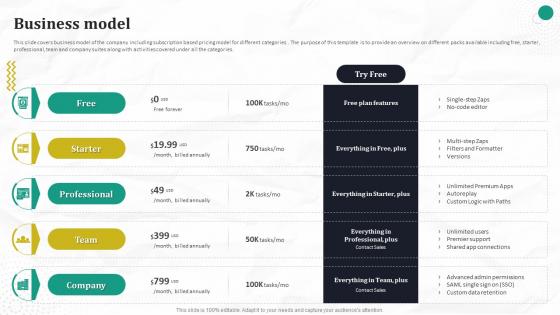
Business Model Automated Workflow Software Funding Pitch Deck For Company
This slide covers business model of the company including subscription based pricing model for different categories . The purpose of this template is to provide an overview on different packs available including free, starter, professional, team and company suites along with activities covered under all the categories. Boost your pitch with our creative Business Model Automated Workflow Software Funding Pitch Deck For Company. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers business model of the company including subscription based pricing model for different categories . The purpose of this template is to provide an overview on different packs available including free, starter, professional, team and company suites along with activities covered under all the categories.
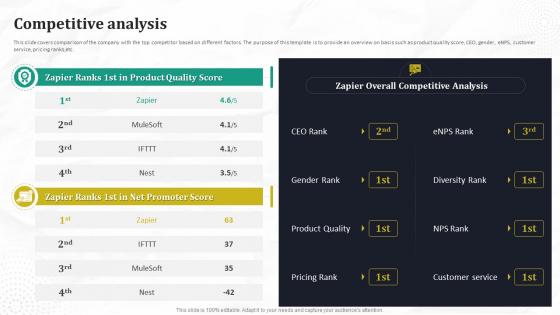
Competitive Analysis Automated Workflow Software Funding Pitch Deck For Company
This slide covers comparison of the company with the top competitor based on different factors. The purpose of this template is to provide an overview on basis such as product quality score, CEO, gender, eNPS, customer service, pricing ranks,etc. Want to ace your presentation in front of a live audience Our Competitive Analysis Automated Workflow Software Funding Pitch Deck For Company can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers comparison of the company with the top competitor based on different factors. The purpose of this template is to provide an overview on basis such as product quality score, CEO, gender, eNPS, customer service, pricing ranks,etc.

Competitive Analysis Task Management System Investor Funding Elevator Pitch Deck
This slide covers comparison of the company with the top competitor based on different factors. The purpose of this template is to provide an overview on basis such as starting price, pricing options, total features, integrations, ease of use, value for money, customer service, etc Want to ace your presentation in front of a live audience Our Competitive Analysis Task Management System Investor Funding Elevator Pitch Deck can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers comparison of the company with the top competitor based on different factors. The purpose of this template is to provide an overview on basis such as starting price, pricing options, total features, integrations, ease of use, value for money, customer service, etc

Funding History Task Management System Investor Funding Elevator Pitch Deck
This slide covers brief overview of company funds raising journey. The purpose of this template is to provide funding announced date, transaction name, number of investors and money raised. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Funding History Task Management System Investor Funding Elevator Pitch Deck. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Funding History Task Management System Investor Funding Elevator Pitch Deck today and make your presentation stand out from the rest This slide covers brief overview of company funds raising journey. The purpose of this template is to provide funding announced date, transaction name, number of investors and money raised.

Business Model Canvas Construction Retail Company Business Model BMC SS V
This slide provides the comprehensive business model of company and includes key components such as major partners, unique selling point USP, key resources, customer relationship, etc. Find a pre-designed and impeccable Business Model Canvas Construction Retail Company Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides the comprehensive business model of company and includes key components such as major partners, unique selling point USP, key resources, customer relationship, etc.

Customer Segments Construction Retail Company Business Model BMC SS V
This slide showcases target segment of company on the basis of home owners, third party sellers, builders, renovators along with need and pain points faced by customers. Want to ace your presentation in front of a live audience Our Customer Segments Construction Retail Company Business Model BMC SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases target segment of company on the basis of home owners, third party sellers, builders, renovators along with need and pain points faced by customers.

Business Model Canvas Car Manufacturing Company Business Model BMC SS V
This slide highlights the companys business model canvas to understand its overall business functioning. It involves key partners, key activities, USP, customer relationships, customer segments, etc. Find a pre-designed and impeccable Business Model Canvas Car Manufacturing Company Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the companys business model canvas to understand its overall business functioning. It involves key partners, key activities, USP, customer relationships, customer segments, etc.

Business Partner Global Innovation And Business Solutions Company Profile CP SS V
This slide represents business partners for Accenture, highlighting the description and solutions offered to clients. It covers partners such as Adobe, Salesforce, and SAP.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Business Partner Global Innovation And Business Solutions Company Profile CP SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents business partners for Accenture, highlighting the description and solutions offered to clients. It covers partners such as Adobe, Salesforce, and SAP.
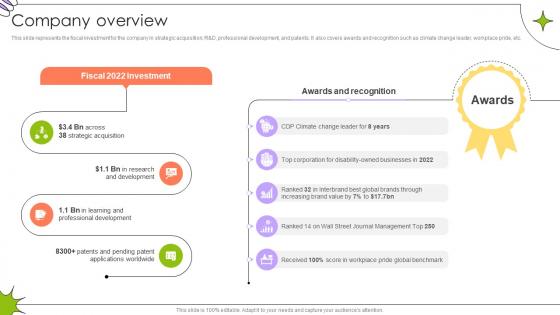
Company Overview Global Innovation And Business Solutions Company Profile CP SS V
This slide represents the fiscal investment for the company in strategic acquisition, RandD, professional development, and patents. It also covers awards and recognition such as climate change leader, workplace pride, etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Company Overview Global Innovation And Business Solutions Company Profile CP SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Company Overview Global Innovation And Business Solutions Company Profile CP SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the fiscal investment for the company in strategic acquisition, RandD, professional development, and patents. It also covers awards and recognition such as climate change leader, workplace pride, etc.

Competitor Analysis By Financials Global Innovation And Business Solutions Company Profile CP SS V
This slide represents competitor analysis for Accenture on the basis of parameters such as annual revenue, net profit and EBITA. It covers competitors PwC, Deloitte, EY and KPMG.Get a simple yet stunning designed Competitor Analysis By Financials Global Innovation And Business Solutions Company Profile CP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Competitor Analysis By Financials Global Innovation And Business Solutions Company Profile CP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents competitor analysis for Accenture on the basis of parameters such as annual revenue, net profit and EBITA. It covers competitors PwC, Deloitte, EY and KPMG.

Competitor Analysis Global Innovation And Business Solutions Company Profile CP SS V
This slide represents competitor analysis for Accenture on the basis of parameters such as headquarters, total experience, geographical presence and business strategy. It covers competitors PwC, Deloitte, EY and KPMG.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Competitor Analysis Global Innovation And Business Solutions Company Profile CP SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents competitor analysis for Accenture on the basis of parameters such as headquarters, total experience, geographical presence and business strategy. It covers competitors PwC, Deloitte, EY and KPMG.
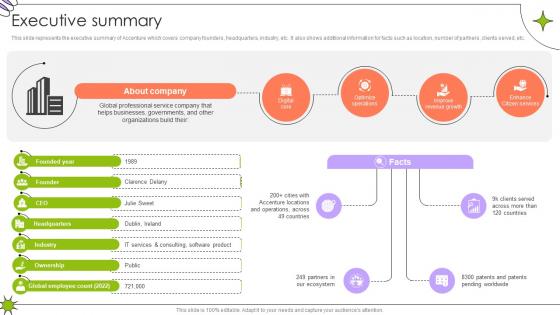
Executive Summary Global Innovation And Business Solutions Company Profile CP SS V
This slide represents the executive summary of Accenture which covers company founders, headquarters, industry, etc. It also shows additional information for facts such as location, number of partners, clients served, etc.If you are looking for a format to display your unique thoughts, then the professionally designed Executive Summary Global Innovation And Business Solutions Company Profile CP SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Executive Summary Global Innovation And Business Solutions Company Profile CP SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the executive summary of Accenture which covers company founders, headquarters, industry, etc. It also shows additional information for facts such as location, number of partners, clients served, etc.

Our Services Global Innovation And Business Solutions Company Profile CP SS V
This slide represents services of Accenture company which includes consulting and outsourcing which covers finance consulting, business strategy, change management, digital commerce etc.Explore a selection of the finest Our Services Global Innovation And Business Solutions Company Profile CP SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Our Services Global Innovation And Business Solutions Company Profile CP SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents services of Accenture company which includes consulting and outsourcing which covers finance consulting, business strategy, change management, digital commerce etc.
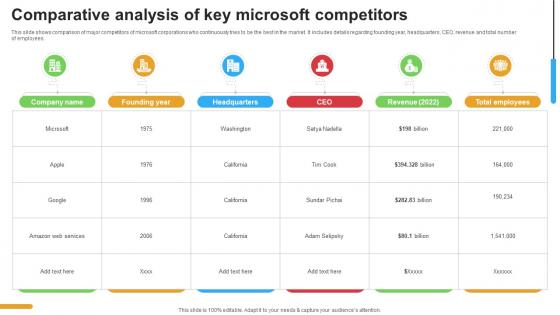
Micosoft Intensive Growth Comparative Analysis Of Key Microsoft Competitors Strategy SS V
This slide shows comparison of major competitors of microsoft corporations who continuously tries to be the best in the market. It includes details regarding founding year, headquarters, CEO, revenue and total number of employees. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Micosoft Intensive Growth Comparative Analysis Of Key Microsoft Competitors Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows comparison of major competitors of microsoft corporations who continuously tries to be the best in the market. It includes details regarding founding year, headquarters, CEO, revenue and total number of employees.
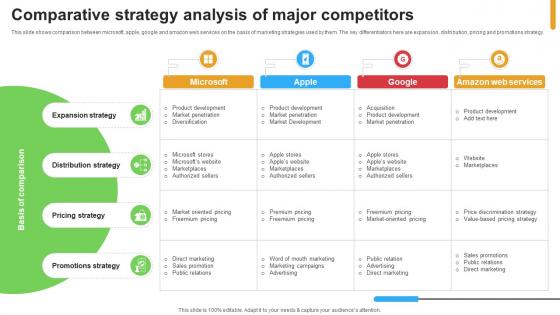
Micosoft Intensive Growth Comparative Strategy Analysis Of Major Competitors Strategy SS V
This slide shows comparison between microsoft, apple, google and amazon web services on the basis of marketing strategies used by them. The key differentiators here are expansion, distribution, pricing and promotions strategy. Present like a pro with Micosoft Intensive Growth Comparative Strategy Analysis Of Major Competitors Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide shows comparison between microsoft, apple, google and amazon web services on the basis of marketing strategies used by them. The key differentiators here are expansion, distribution, pricing and promotions strategy.
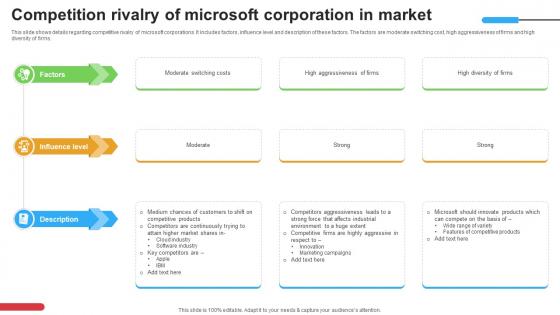
Micosoft Intensive Growth Competition Rivalry Of Microsoft Corporation In Market Strategy SS V
This slide shows details regarding competitive rivalry of microsoft corporations. It includes factors, influence level and description of these factors. The factors are moderate switching cost, high aggressiveness of firms and high diversity of firms. Slidegeeks is here to make your presentations a breeze with Micosoft Intensive Growth Competition Rivalry Of Microsoft Corporation In Market Strategy SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows details regarding competitive rivalry of microsoft corporations. It includes factors, influence level and description of these factors. The factors are moderate switching cost, high aggressiveness of firms and high diversity of firms.


 Continue with Email
Continue with Email

 Home
Home


































