Technology Security
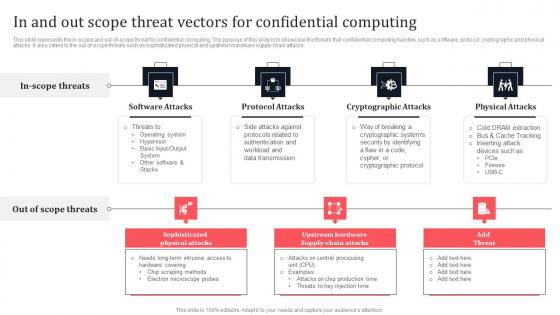
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
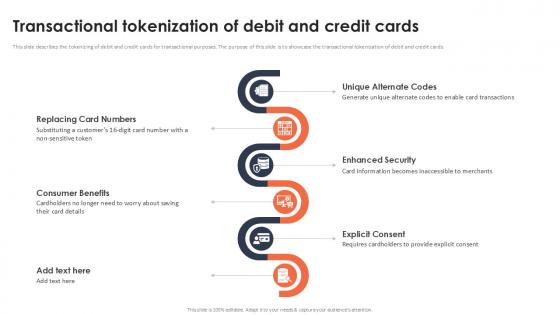
Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide
This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards.

Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint
This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc.
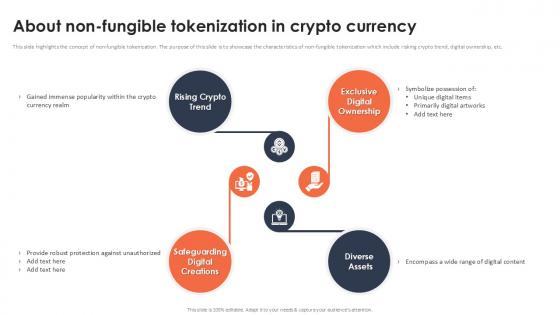
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.
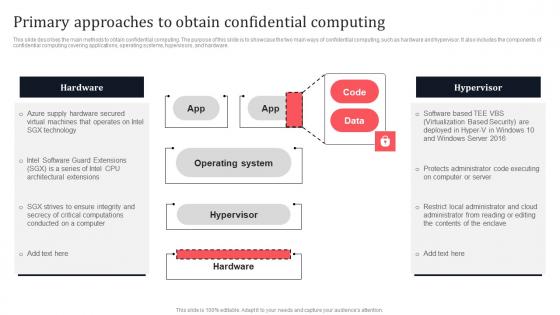
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
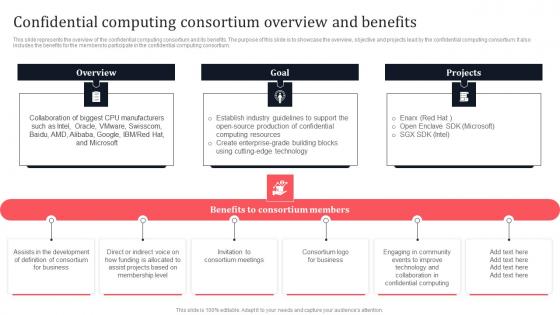
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
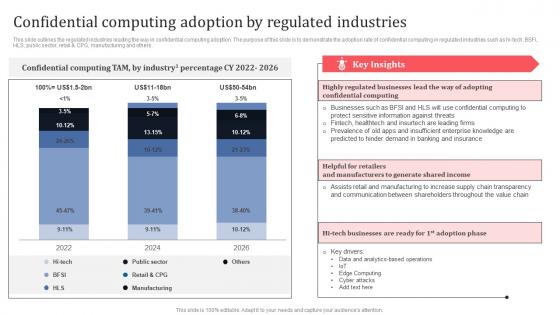
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
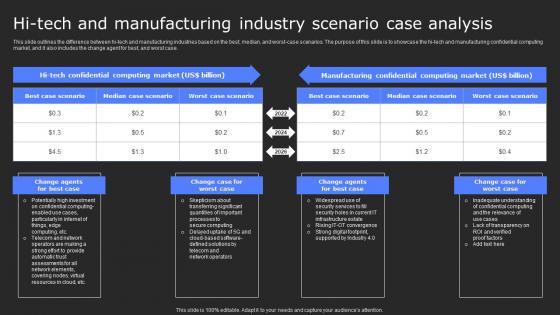
Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
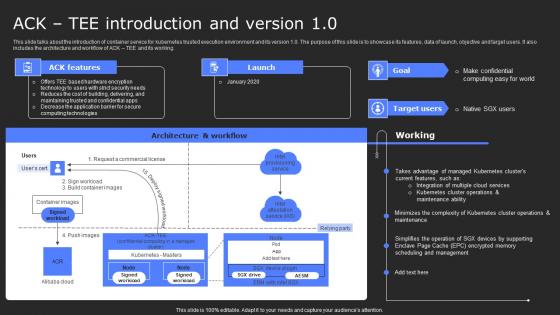
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.

Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Outline Example Topics
This is a analysis and valuation of equity securities ppt powerpoint presentation outline example topics. This is a three stage process. The stages in this process are industry analysis, valuation of equity securities, financial statement analysis.
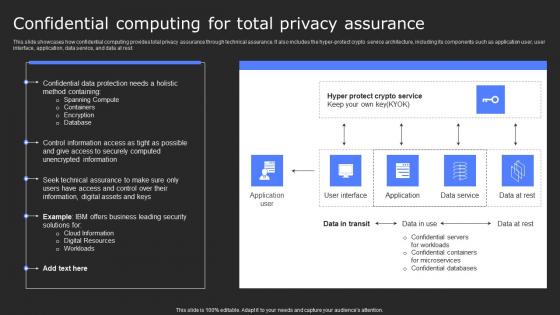
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
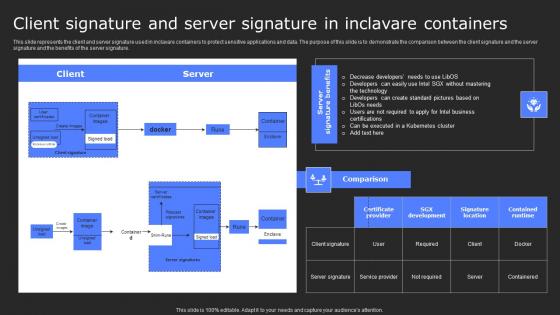
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
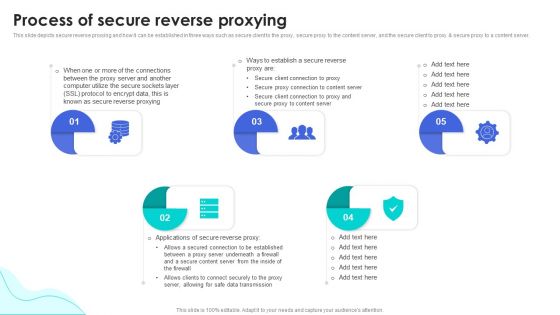
Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Make sure to capture your audiences attention in your business displays with our gratis customizable Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
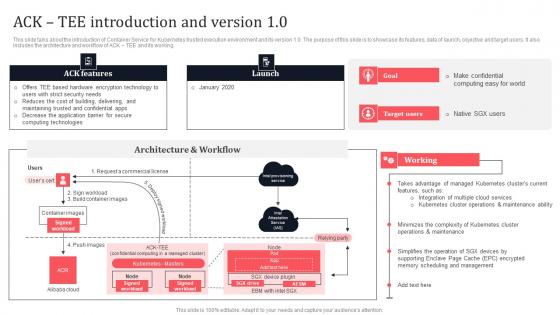
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
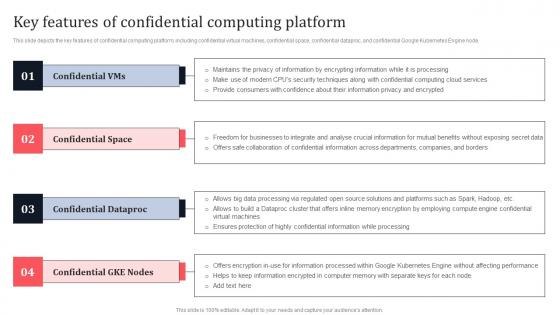
Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Find a pre-designed and impeccable Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node.
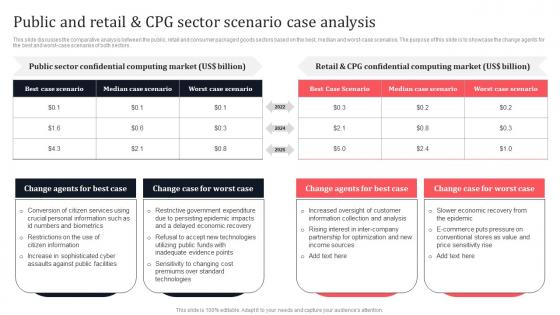
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.

Analyzing Multiple Sales Tactics For Securing Strategic Sales Plan To Enhance Introduction Pdf
This slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc. Want to ace your presentation in front of a live audience Our Analyzing Multiple Sales Tactics For Securing Strategic Sales Plan To Enhance Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc.

Redis Cache Data Structure IT Secure Server Configuration With Server Configuration Lock Diagrams PDF
This slide describes the secure server configuration with server configuration lock, which guarantees only users have access. Presenting redis cache data structure it secure server configuration with server configuration lock diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like securing, programmer, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
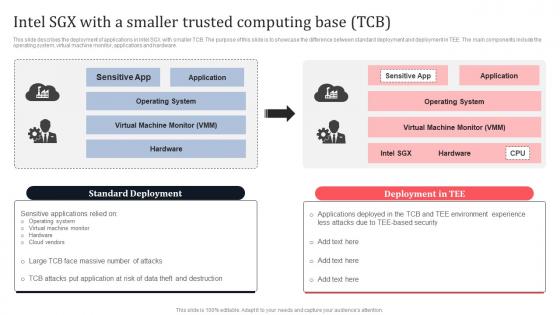
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
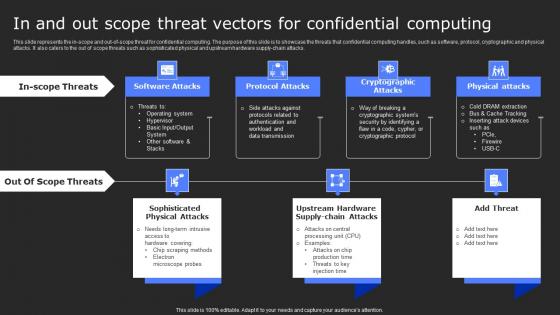
In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Take your projects to the next level with our ultimate collection of In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
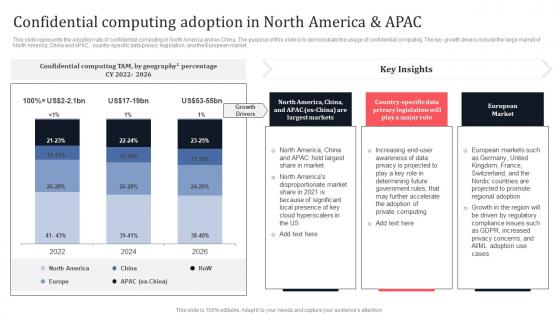
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
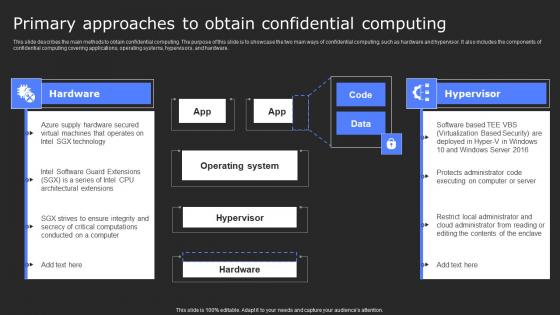
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
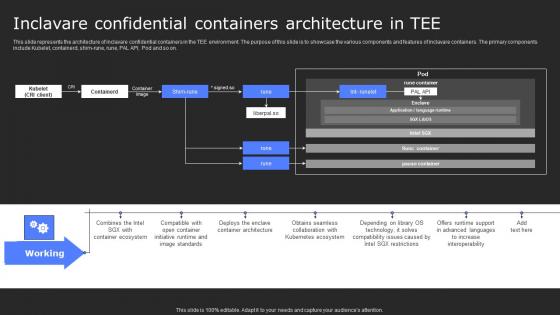
Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Do you know about Slidesgeeks Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
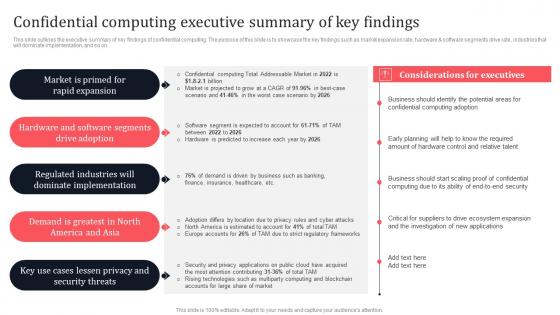
Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.

Golden Keys Combing Business Concept PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Golden Keys Combing Business Concept PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are a sure bet. Gauranteed to win against all odds. Download our Technology PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape.Use these PowerPoint slides for presentations relating to Two golden keys connected, Security, Business, Technology, Success, Shapes. The prominent colors used in the PowerPoint template are Yellow, Black, White. PowerPoint presentation experts tell us our Golden Keys Combing Business Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. PowerPoint presentation experts tell us our Security PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. You can be sure our Golden Keys Combing Business Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our Security PowerPoint templates and PPT Slides are designed to make your presentations professional. Presenters tell us our Golden Keys Combing Business Concept PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our Shapes PowerPoint templates and PPT Slides will make you look like a winner. Our Golden Keys Combing Business Concept PowerPoint Templates Ppt Backgrounds For Slides 0113 are fairly broadbased. They give you ample scope to address your mind.
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
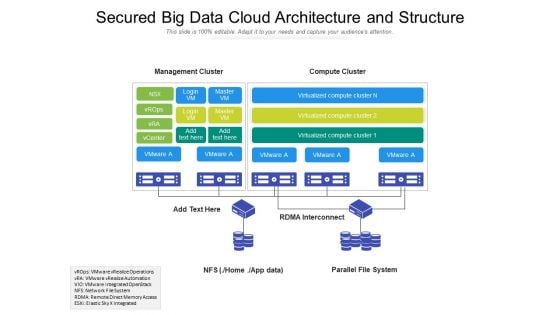
Secured Big Data Cloud Architecture And Structure Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name secured big data cloud architecture and structure ppt powerpoint presentation gallery example pdf. The topics discussed in these slide is secured big data cloud architecture and structure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Bank Vault To Secure Valuables And Money Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled bank vault to secure valuables and money ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are bank vault to secure valuables and money. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Secure Transaction During E Commerce Business Financial Operations Icon Guidelines PDF
Showcasing this set of slides titled secure transaction during e commerce business financial operations icon guidelines pdf The topics addressed in these templates are secure transaction during e commerce business financial operations icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Secure Payment Via Cheque Vector Icon Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting secure payment via cheque vector icon ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including secure payment via cheque vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Health Protection Plan For Secured Life Vector Icon Ppt PowerPoint Presentation Slides Examples PDF
Pitch your topic with ease and precision using this health protection plan for secured life vector icon ppt powerpoint presentation slides examples pdf. This layout presents information on health protection plan for secured life vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Safe And Secure Banking Services Framework For Payments Icon Mockup PDF
Presenting Safe And Secure Banking Services Framework For Payments Icon Mockup PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Safe Secure, Banking Services, Framework Payments This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Cloud Information Securitys Ppt Infographics Graphics PDF
This is a Table Of Contents For Cloud Information Securitys Ppt Infographics Graphics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threats Involved, Cloud Security, Compliance Violations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Business Intranet For Secure Communication Vector Icon Ppt PowerPoint Presentation Infographic Template Design Ideas PDF
Presenting business intranet for secure communication vector icon ppt powerpoint presentation infographic template design ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business intranet for secure communication vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
4 Phases Funnel Slide For Securing Your Business Ppt PowerPoint Presentation Gallery Elements PDF
Presenting 4 phases funnel slide for securing your business ppt powerpoint presentation gallery elements pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including 4 phases funnel slide for securing your business. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Online Money Transfer Icon Ppt PowerPoint Presentation File Show PDF
Presenting Secure Online Money Transfer Icon Ppt PowerPoint Presentation File Show PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Online Money, Transfer Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Construction Project Plan With Secure Financing Ppt PowerPoint Presentation Gallery Gridlines PDF
Showcasing this set of slides titled construction project plan with secure financing ppt powerpoint presentation gallery gridlines pdf. The topics addressed in these templates are project tasks, contract writing, contract signing, secure financing, obtain permits, site work. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Environments Best Suited For Efficient And Secure Supply Chains Information PDF
Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains information pdf bundle. Topics like environments best suited for efficient and secure supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Share Your Secure Data In Business Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Display your drive on our Share Your Secure Data In Business Data PowerPoint Templates PPT Backgrounds For Slides. Invigorate the audience with your fervour. Drive your team towards excellence. Steer them there with our Communication PowerPoint Templates. Drive your passion with our Business PowerPoint Templates. Steer yourself to achieve your aims. Environmental awareness is the call to answer. Our Share Your Secure Data In Business Data PowerPoint Templates Ppt Backgrounds For Slides 0713 will fit the bill.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
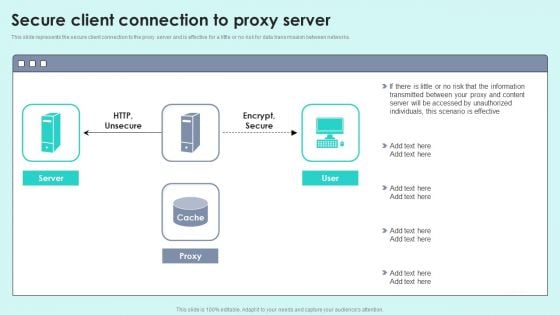
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
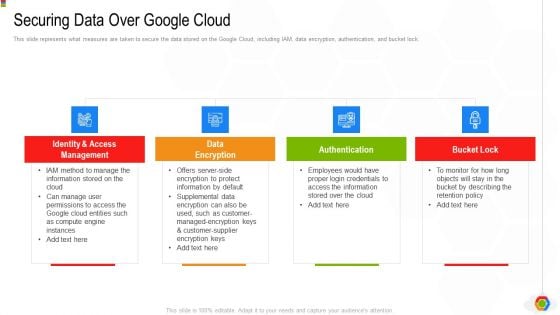
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure Virtual Data Storage Ppt PowerPoint Presentation Model Slide Download Cpb Pdf
Presenting this set of slides with name secure virtual data storage ppt powerpoint presentation model slide download cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like secure virtual data storage to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Show Infographics
This is a analysis and valuation of equity securities ppt powerpoint presentation show infographics. This is a three stage process. The stages in this process are industry analysis, financial statement analysis, management, marketing, business, strategy.

Application Development Life Cycle Overview And Importance Of Secure Sdlc Rules PDF
This slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost. Presenting application development life cycle need of software development life cycle sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Show Visual Aids
This is a analysis and valuation of equity securities ppt powerpoint presentation show visual aids. This is a three stage process. The stages in this process are marketing, business, management.
Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Icon Slide Portrait
This is a analysis and valuation of equity securities ppt powerpoint presentation icon slide portrait. This is a one stage process. The stages in this process are business, management, marketing, agenda.
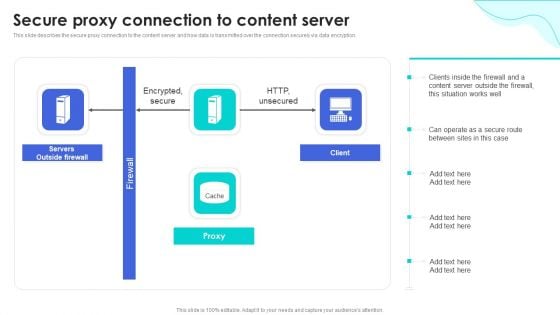
Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Network Protection Icon For Securing Customer Information Ppt PowerPoint Presentation Icon Pictures PDF
Persuade your audience using this network protection icon for securing customer information ppt powerpoint presentation icon pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network protection icon for securing customer information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Environments Best Suited For Efficient And Secure Supply Chains Template PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains template pdf bundle. Topics like inventory investment, strategy, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Shift Capital Fundraising Pitch Deck Details About Shifts Secure Storage Facility Formats PDF
This slide provides information about the storage facility at Shift and some details regarding the hub. Deliver an awe inspiring pitch with this creative shift capital fundraising pitch deck details about shifts secure storage facility formats pdf bundle. Topics like our secure storage facility, the hub can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
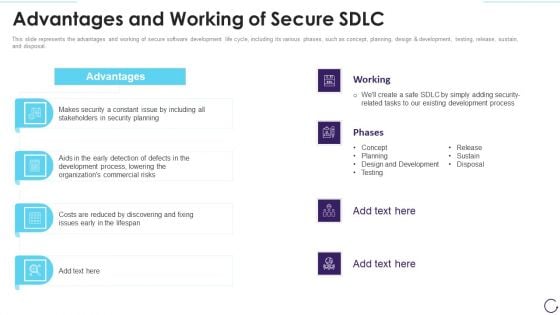
Application Development Life Cycle Advantages And Working Of Secure Sdlc Microsoft PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Presenting 30 60 90 days plan for software development life cycle structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advantages and working of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
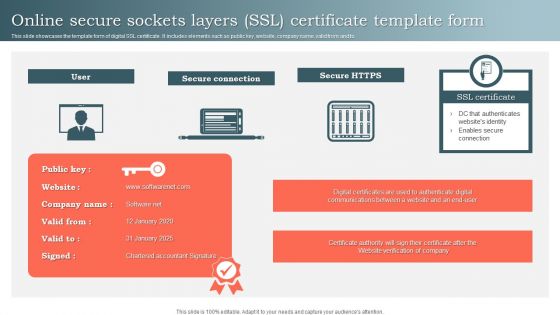
Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF
This slide showcases the template form of digital SSL certificate. It includes elements such as public key, website, company name, valid from and to. Presenting Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User, Secure Connection, Secure HTTPS, SSL Certificate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
30 60 90 Days Plan Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary 30 60 90 Days Plan Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this 30 60 90 Days Plan Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Explore a selection of the finest Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction To Secure Digital Wallets For Financial Transactions Ppt Infographics Influencers PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


 Continue with Email
Continue with Email

 Home
Home


































