AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Confidential Computing Architecture Confidential Computing System Technology Introduction PDF
Features of these PowerPoint presentation slides:
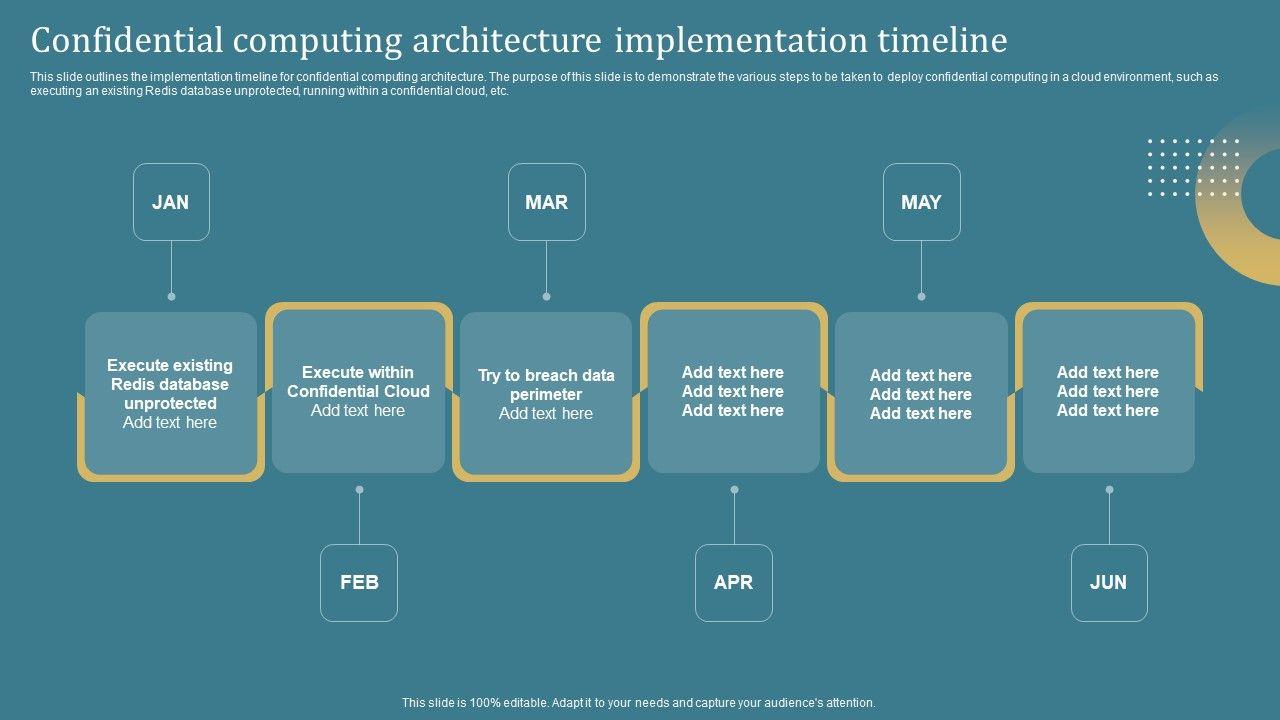
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find a pre-designed and impeccable Confidential Computing Architecture Confidential Computing System Technology Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Confidential Computing Architecture Confidential Computing System Technology Introduction PDF with all 9 slides:
Ratings and Reviews
5
- ★52
- ★40
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Tarun Saini
May 26, 2023
Graphics are very appealing to eyes.by AMRoy
May 26, 2023
Designs have enough space to add content.
View per page:
10