AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
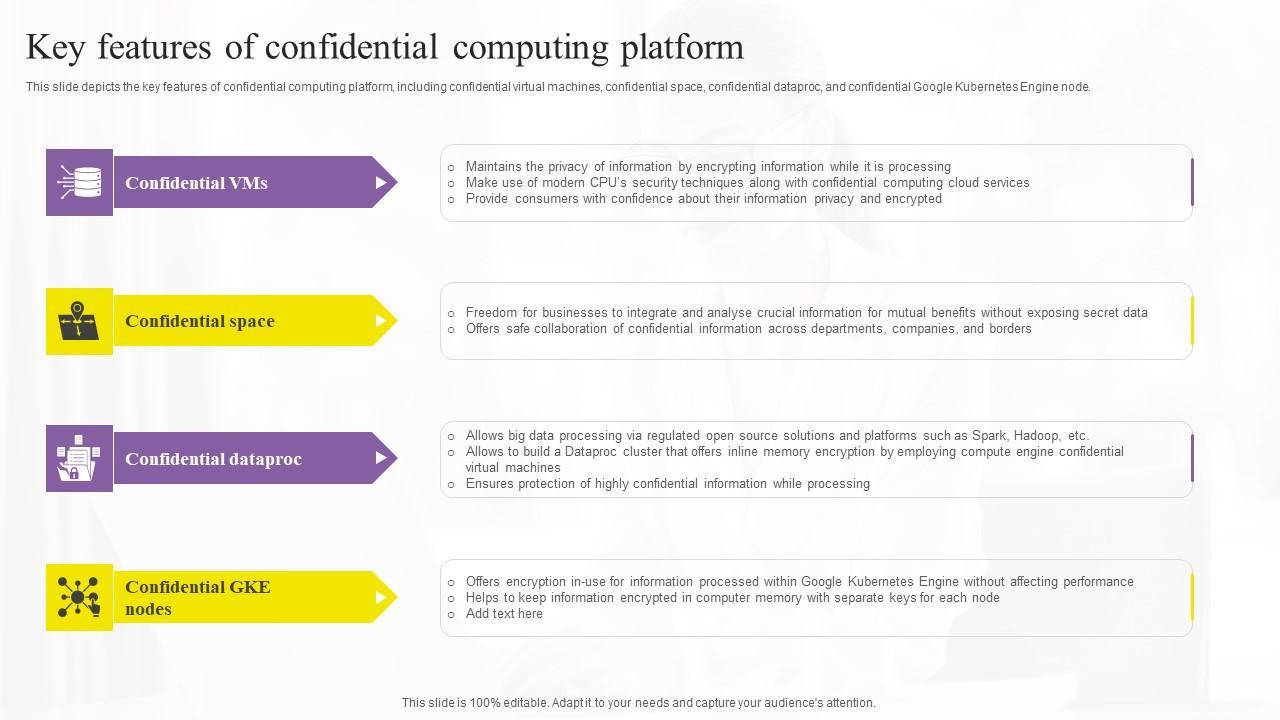
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.
Features of these PowerPoint presentation slides:
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Presenting this PowerPoint presentation, titled Key Features Of Confidential Computing Technologies Introduction Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Features Of Confidential Computing Technologies Introduction Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Features Of Confidential Computing Technologies Introduction Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Key Features Of Confidential Computing Technologies Introduction Pdf with all 9 slides:
Use our Key Features Of Confidential Computing Technologies Introduction Pdf to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Ratings and Reviews
4.5
- ★52
- ★42
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Jacob Wilson
February 21, 2024
Helpful product design for delivering presentation.by Brown Baker
February 21, 2024
Visually stunning presentation, love the content.by Donte Duncan
February 20, 2024
Top Quality presentations that are easily editable.by Miller Rogers
February 20, 2024
Attractive design and informative presentation.
View per page:
10