AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Features of these PowerPoint presentation slides:
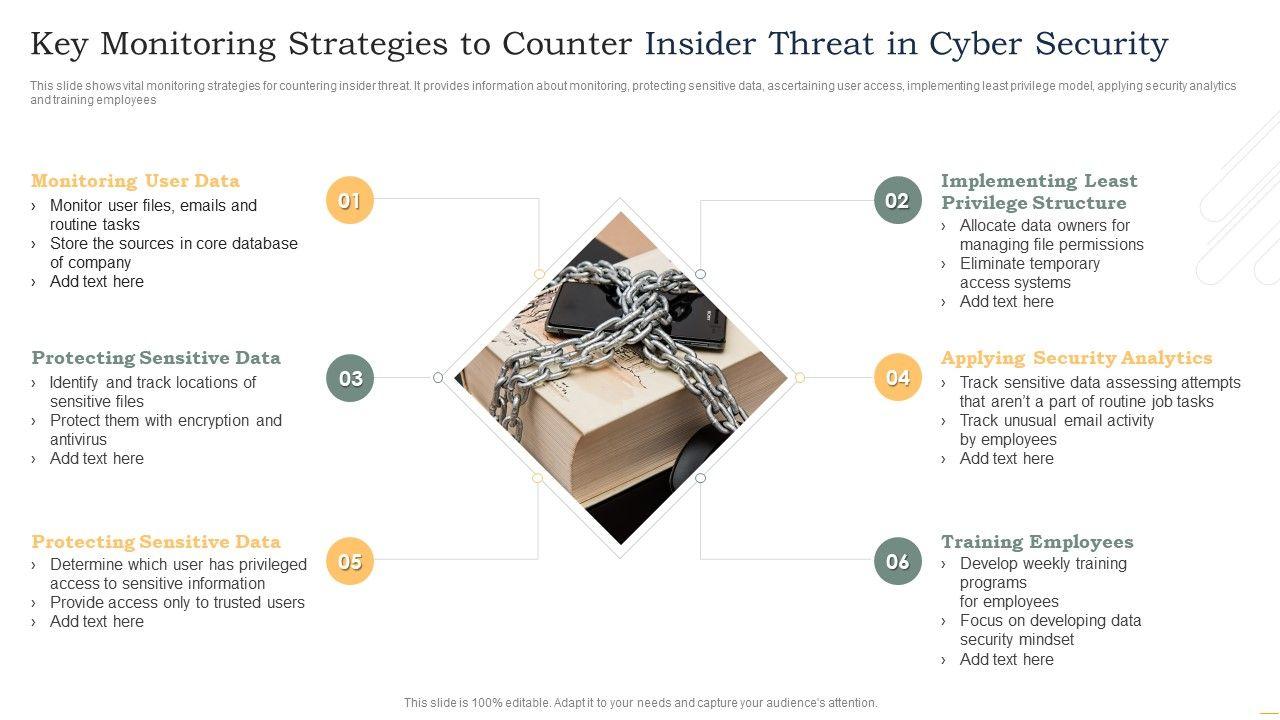
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF with all 9 slides:
Ratings and Reviews
4.5
- ★51
- ★41
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Art Cis
November 21, 2022
The content is very helpful from business point of view.by glen mccracken
November 21, 2022
Great experience, I would definitely use your services further.
View per page:
10