AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Architecture Work PowerPoint Presentation Templates and Google Slides
25 Item(s)

Slide 1 of 2
This slide provides the glimpse about the sprint daily scrum meeting which focuses on story, to do, in progress, to verify and done tasks.This is a scrum architecture working on sprint daily scrum meetings pictures pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like generate procurement, receive customers, approve the execution You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Presenting this set of slides with name three trees architecture working with remote repositories ppt portfolio inspiration pdf. The topics discussed in these slides are working copy, staging area, local repository. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
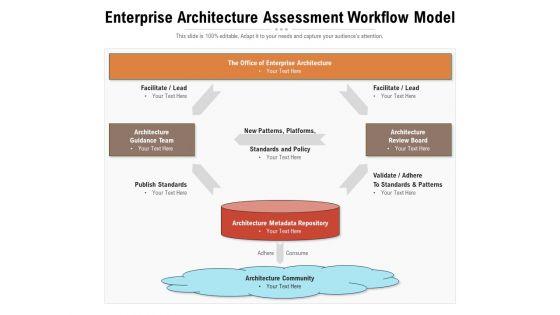
Presenting this set of slides with name enterprise architecture assessment workflow model ppt powerpoint presentation styles format pdf. This is a one stage process. The stages in this process are new patterns, platforms, architecture review board, architecture guidance team, architecture metadata repository. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
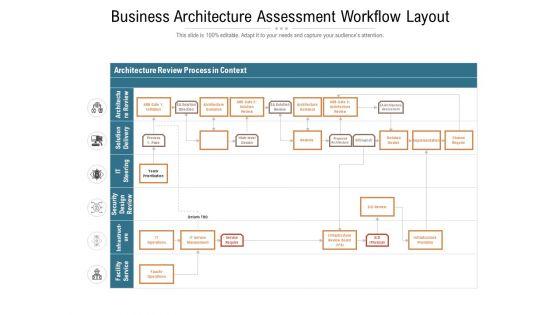
Presenting this set of slides with name business architecture assessment workflow layout ppt powerpoint presentation file inspiration pdf. The topics discussed in these slides are it operations, it service management, service require, analysis, infrastructure providing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
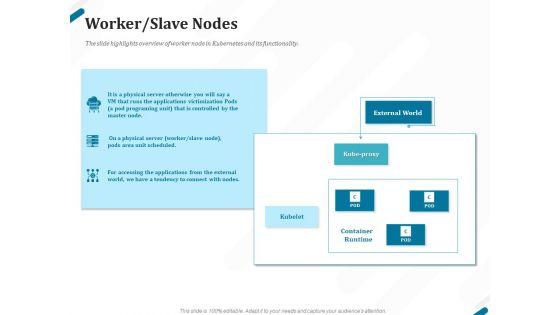
Presenting this set of slides with name kubernetes containers architecture overview worker slave nodes ppt ideas format pdf. The topics discussed in these slides are external world, kube proxy, kubelet, container, runtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
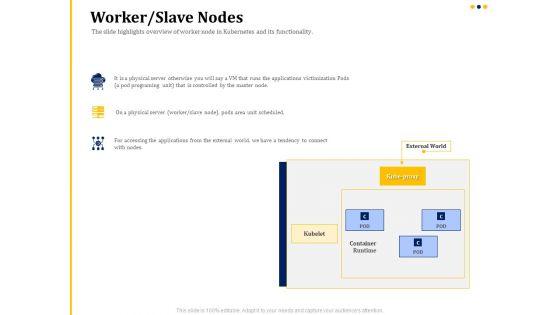
Presenting this set of slides with name understanding the kubernetes concepts and architecture worker slave nodes ppt infographics format pdf. The topics discussed in these slides are external world, kube proxy, kubelet, container runtime, pod. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.









Slide 1 of 9
This slide outlines the structure and working of blockchain technology. The purpose of this slide is to showcase the connection of blocks in a blockchain network, the collection of transactions and working. The components of a block include the header, the hash value of the previous block header, and the root of the hash tree. Make sure to capture your audiences attention in your business displays with our gratis customizable Architecture And Working Of Blockchain Technology Sample PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
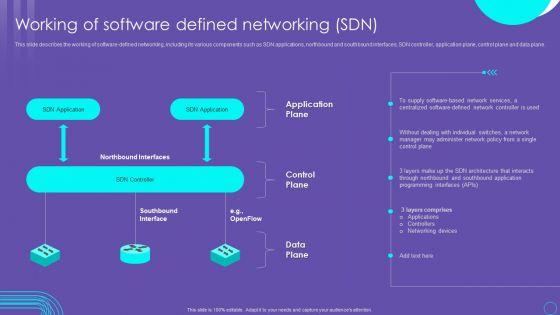








Slide 1 of 9
This slide describes the working of software defined networking, including its various components such as SDN applications, northbound and southbound interfaces, SDN controller, application plane, control plane and data plane. Slidegeeks is here to make your presentations a breeze with SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
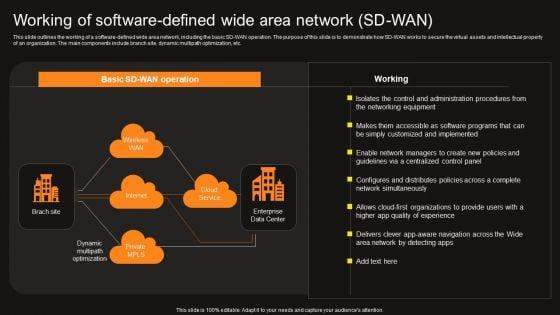








Slide 1 of 9
This slide outlines the working of a software-defined wide area network, including the basic sd wan operation. the purpose of this slide is to demonstrate how sd wan works to secure the virtual assets and intellectual property of an organization the main components include branch site, dynamic multipath optimization, etc. There are so many reasons you need a Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.









Slide 1 of 9
This slide outlines the organizations or groups working on open RAN, including the O-RAN Alliance Group, Nokia, and Samsung. O-RAN alliance group has launched RAN intelligent controller, distributed unit, and RRU specifications. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. O RAN Architecture Whos Working On Open RAN Ppt PowerPoint Presentation Gallery Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.









Slide 1 of 9
This slide represents the working of the Radio Access Network and core network. RAN is a visible part attached to towers and helps send and receive signals to and from phones, and it is the ultimate connection to the network. Do you know about Slidesgeeks O RAN Architecture Working Of RAN And Core Networks Ppt Summary Visual Aids PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
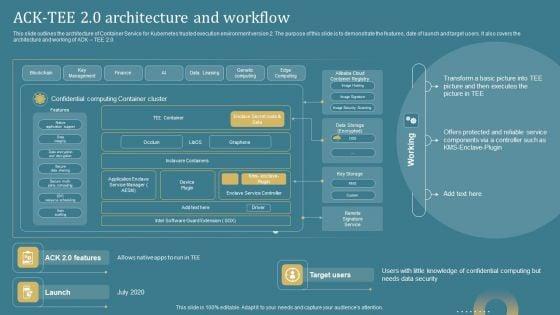








Slide 1 of 9
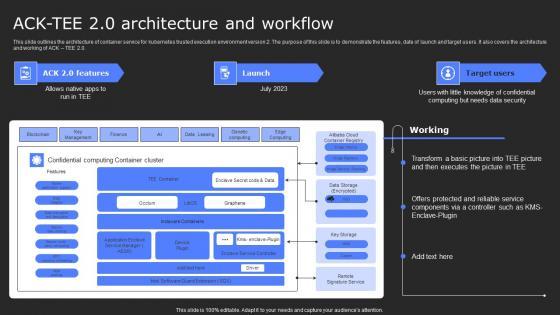
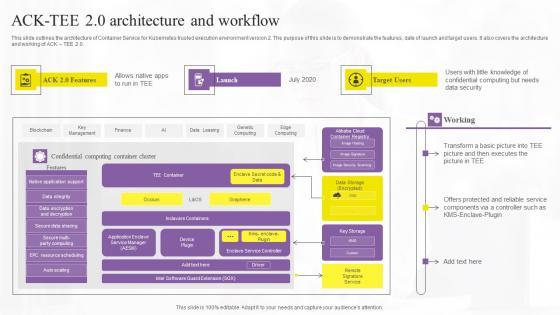
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Confidential Computing System Technology Acktee 20 Architecture And Workflow Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
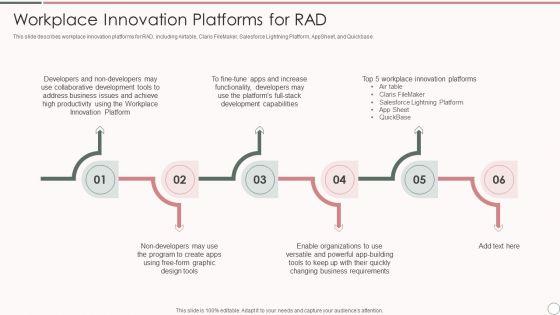








Slide 1 of 9
This slide describes workplace innovation platforms for RAD, including Airtable, Claris FileMaker, Salesforce Lightning Platform, AppSheet, and Quickbase.This is a Rapid Application Development Architecture Workplace Innovation Platforms For Rad Microsoft PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Collaborative Development, Development Capabilities, Enable Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 1
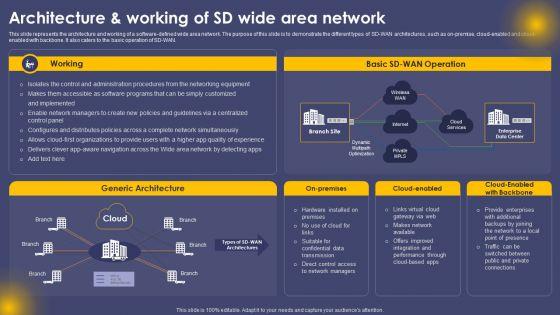
This slide represents the architecture and working of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. If you are looking for a format to display your unique thoughts, then the professionally designed Architecture And Working Of SD Wide Area Network Ppt Model Design Ideas PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Architecture And Working Of SD Wide Area Network Ppt Model Design Ideas PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.








Slide 1 of 9
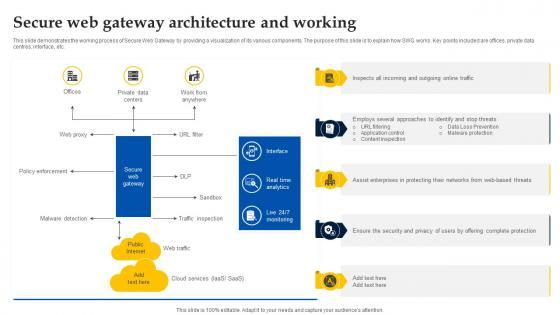
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.








Slide 1 of 9
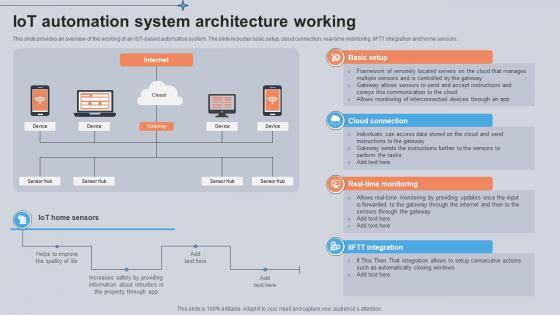
This slide provides an overview of the working of an IOT-based automation system. The slide includes basic setup, cloud connection, real-time monitoring, IIFTT integration and home sensors. If you are looking for a format to display your unique thoughts, then the professionally designed IoT Automation System Architecture Working Utilizing Smart Appliances IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IoT Automation System Architecture Working Utilizing Smart Appliances IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides an overview of the working of an IOT-based automation system. The slide includes basic setup, cloud connection, real-time monitoring, IIFTT integration and home sensors.









Slide 1 of 9
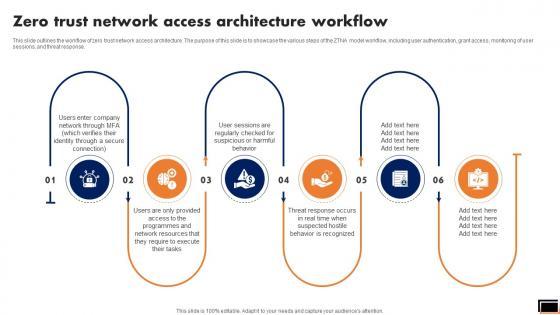
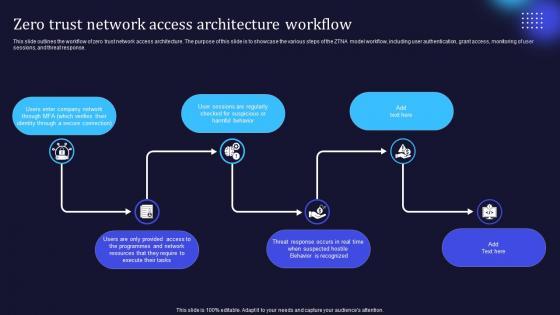
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.








Slide 1 of 9
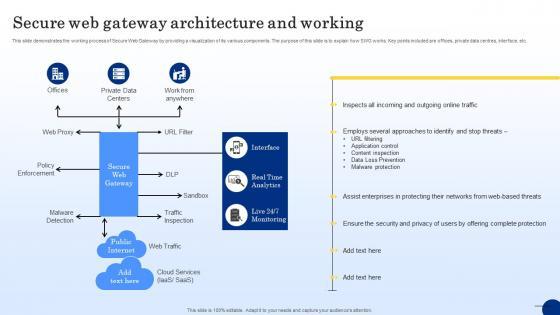
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.








Slide 1 of 9
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.








Slide 1 of 9
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.








Slide 1 of 9
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.









Slide 1 of 9
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.








Slide 1 of 9
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Find a pre-designed and impeccable ACK Tee 20 Architecture And Workflow Confidential Computing Technologies Structure Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
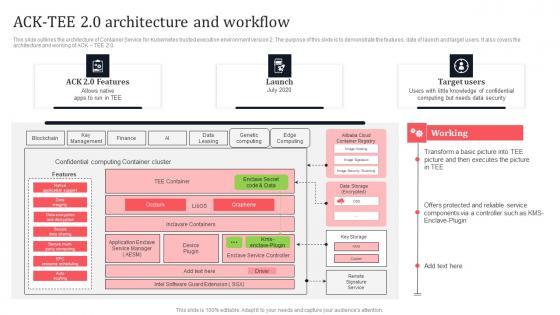








Slide 1 of 9
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.









Slide 1 of 9
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks has constructed Zero Trust Network Access Architecture Workflow Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
25 Item(s)
