AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Breach Prevention PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 88 Item(s)
Page






























Slide 1 of 50
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fifty slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Slide 1 of 2
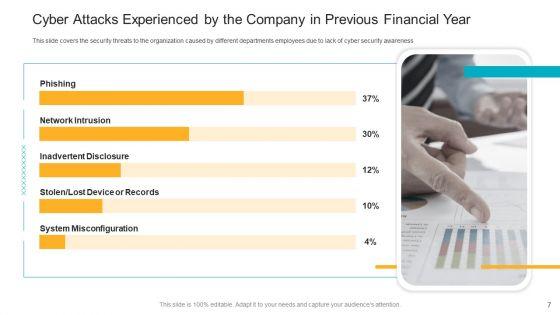
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
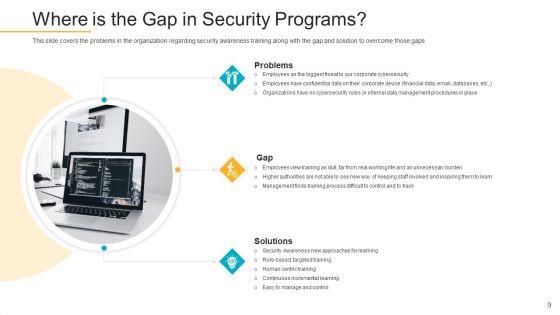
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a data breach prevention recognition where is the gap in security programs summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, solutions, gap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
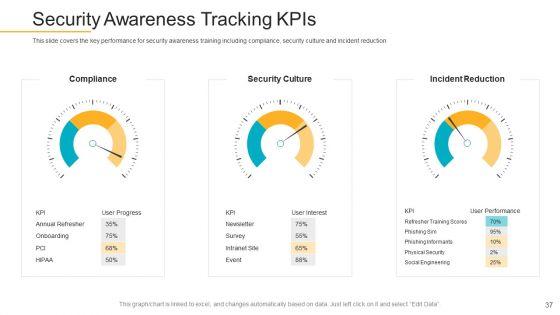
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
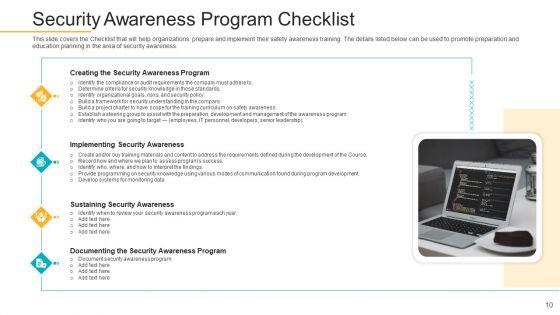
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
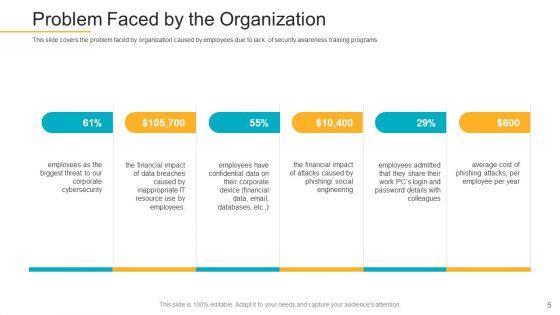
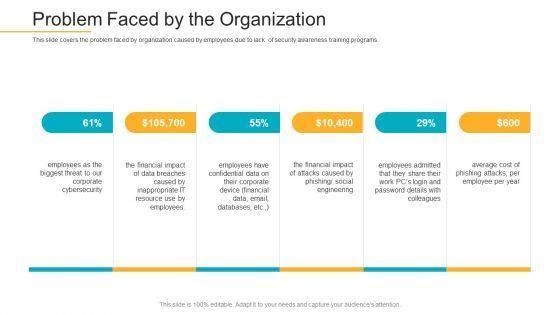
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. This is a data breach prevention recognition communication plan general format rules pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, description, frequency, audience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
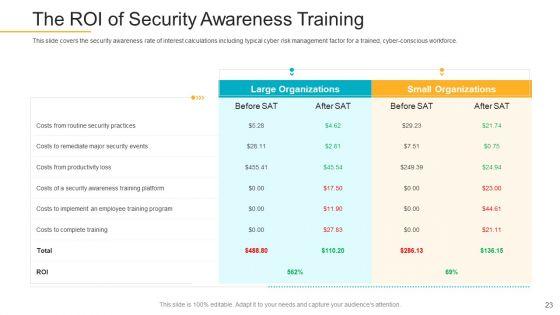
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver an awe-inspiring pitch with this creative data breach prevention recognition the roi of security awareness training brochure pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
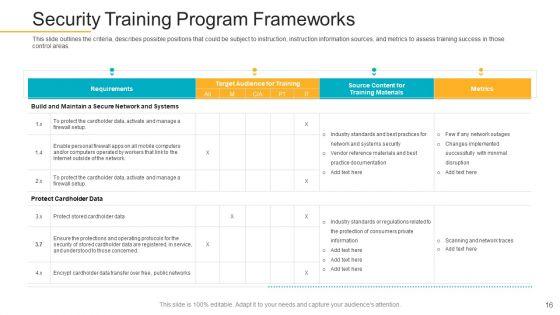
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
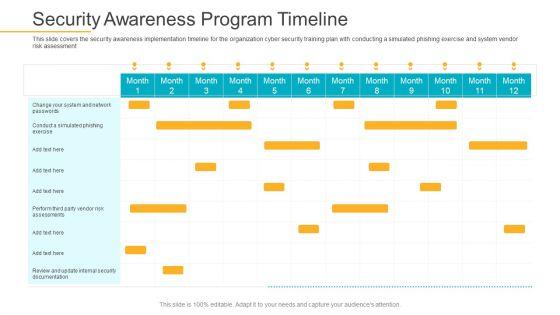
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
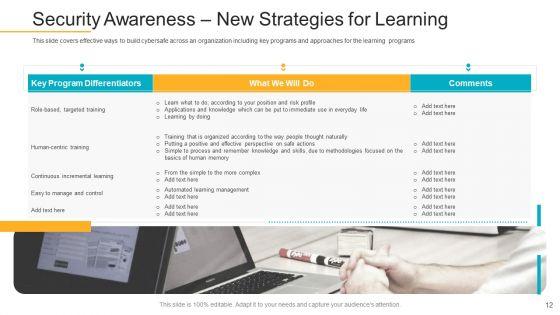
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
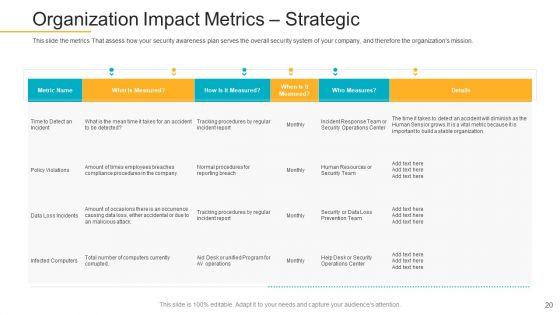
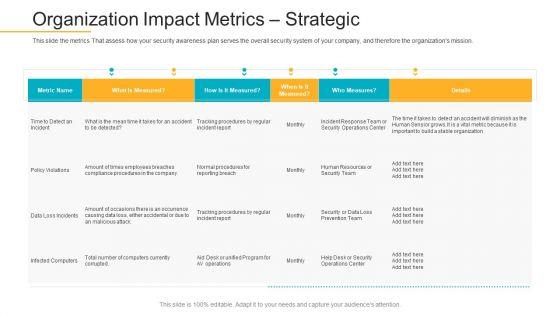
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization impact metrics strategic microsoft pdf. Use them to share invaluable insights on organization impact metrics strategic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
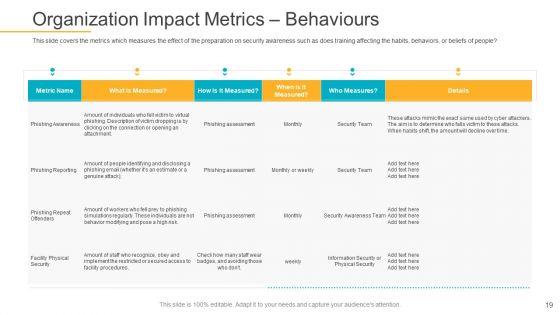
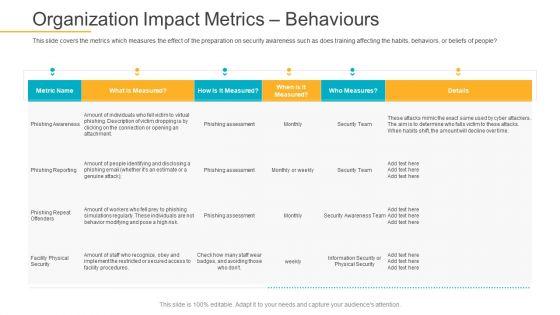
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people.Deliver an awe-inspiring pitch with this creative data breach prevention recognition organization impact metrics behaviours pictures pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver an awe-inspiring pitch with this creative data breach prevention recognition organization compliance metrics themes pdf bundle. Topics like organization compliance metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
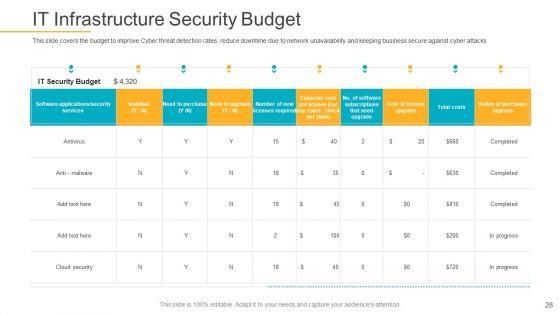
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
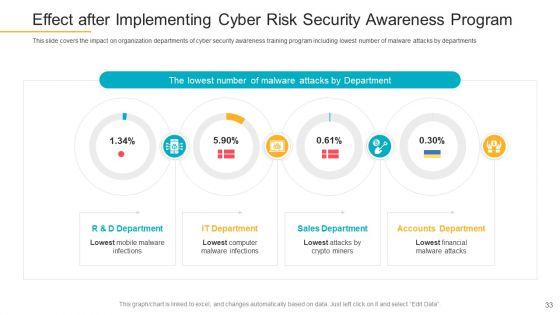
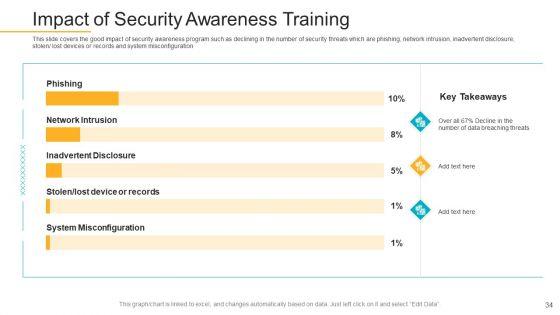
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
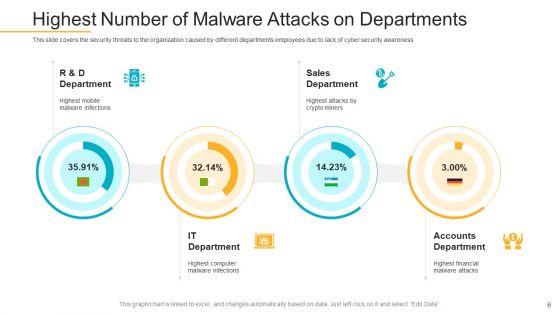
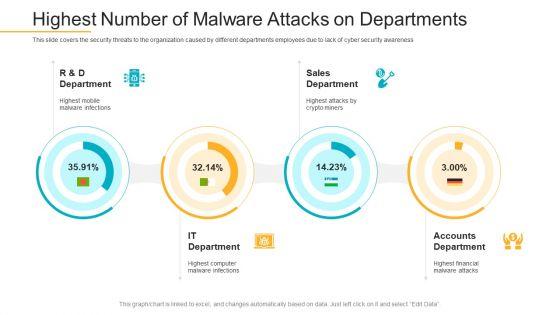
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative data breach prevention recognition employee security awareness training budget graphics pdf bundle. Topics like budget, capability level, renew, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
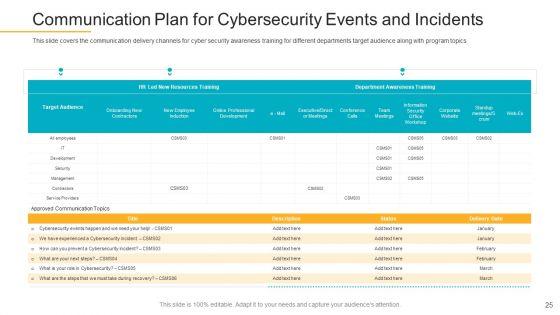
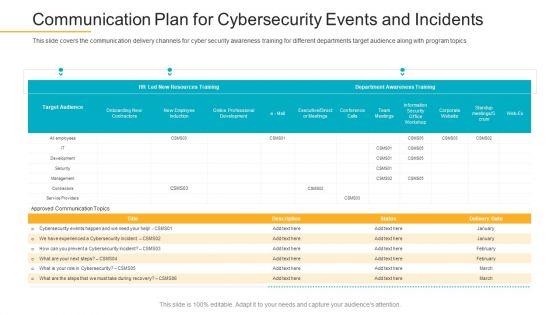
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
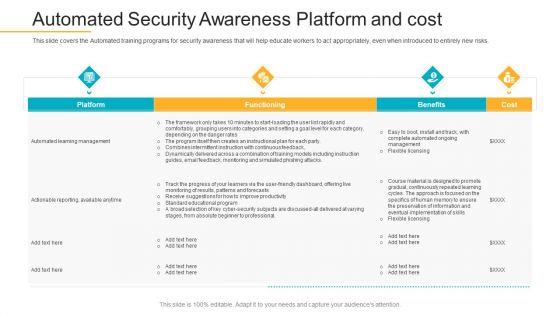
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative data breach prevention recognition automated security awareness platform and cost slides pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
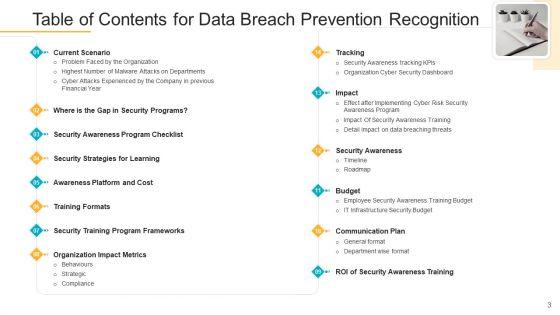
Presenting table of contents for data breach prevention recognition ppt model skills pdf to provide visual cues and insights. Share and navigate important information on fourteen stages that need your due attention. This template can be used to pitch topics like budget, communication plan, security awareness, security programs, cost. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
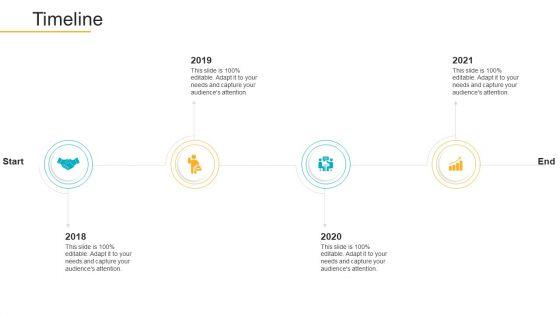
This is a data breach prevention recognition timeline ppt portfolio samples pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
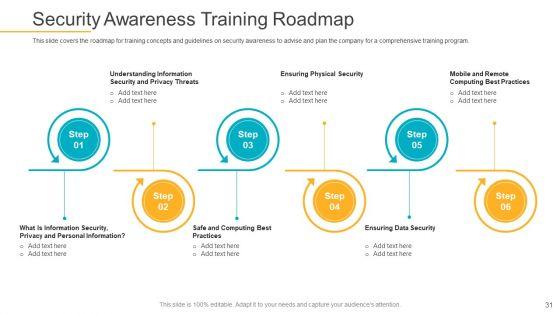
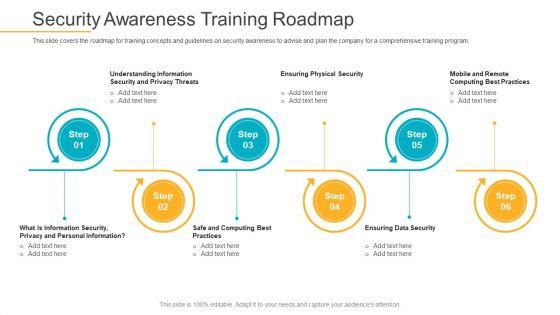
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a data breach prevention recognition security awareness training roadmap ppt gallery graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threats, data security, information, awareness, roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Presenting data breach prevention recognition post it notes ppt icon file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
This is a data breach prevention recognition location ppt icon objects pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Download our innovative and attention-grabbing data breach prevention recognition icons slide ppt styles designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Slide 1 of 2
This is a data breach prevention recognition comparison ppt icon background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topic like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
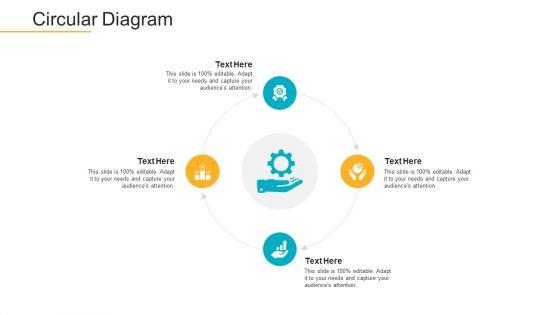
Presenting data breach prevention recognition circular diagram ppt portfolio infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like circular diagram. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a agenda for data breach prevention recognition ppt styles layouts pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information systems, cybersecurity incidents, policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.








Slide 1 of 9
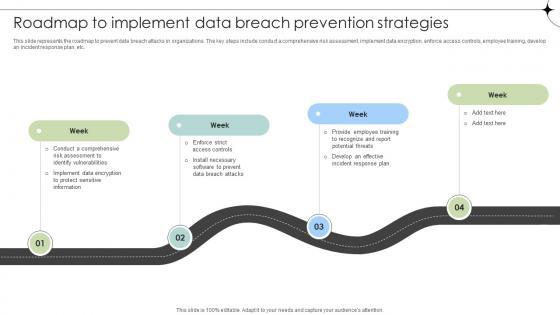
This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.Boost your pitch with our creative Roadmap To Implement Data Breach Prevention Strategies Data Fortification Strengthening Defenses. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.








Slide 1 of 9
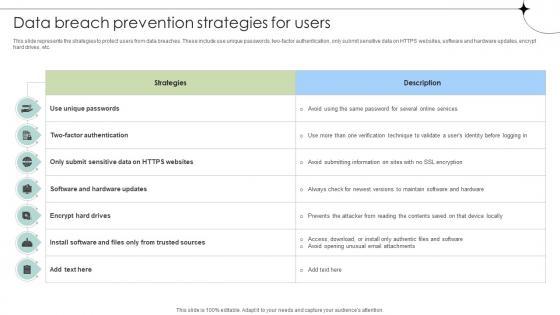
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.









Slide 1 of 9
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.









Slide 1 of 9
This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc.








Slide 1 of 10
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.









Slide 1 of 9
Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.








Slide 1 of 9
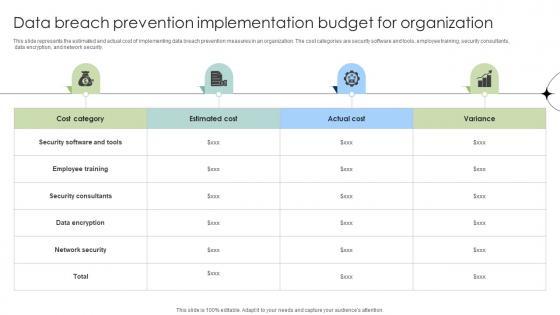
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.









Slide 1 of 9
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.








Slide 1 of 10
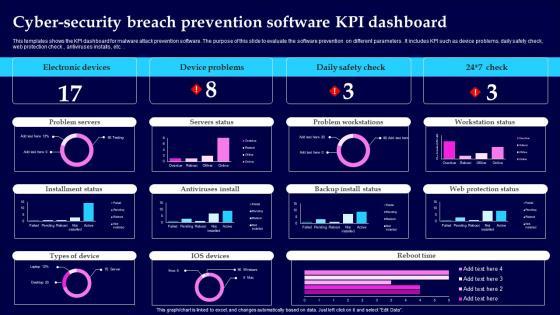
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.








Slide 1 of 9
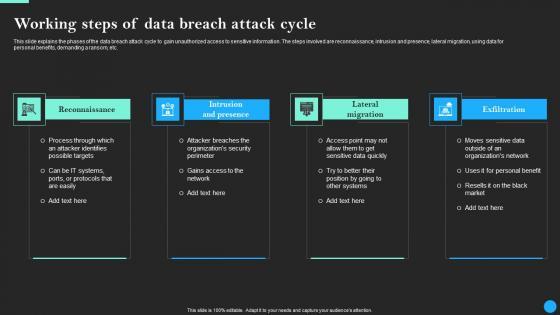
This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf today and make your presentation stand out from the rest This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc.








Slide 1 of 9
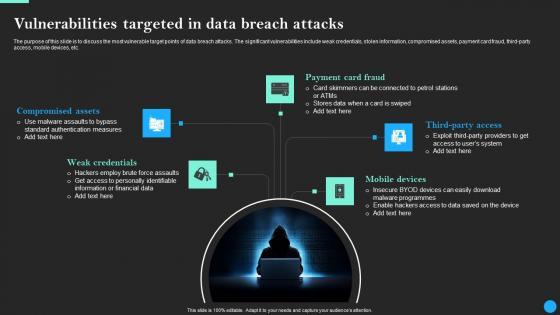
Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Breach Prevention Inspiration Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc.









Slide 1 of 9
Present like a pro with Types Of Information Leaked In Data Breach Data Breach Prevention Brochure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc.








Slide 1 of 9
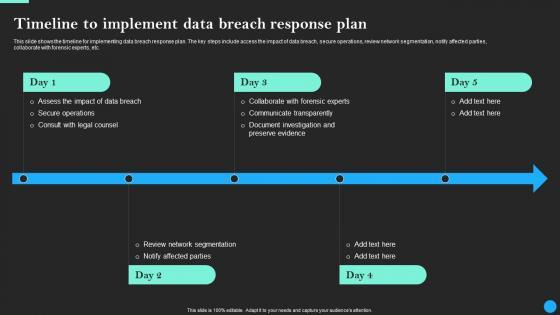
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Breach Prevention Template Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc.








Slide 1 of 9
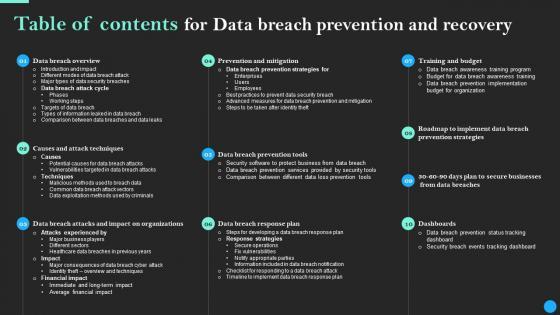
Get a simple yet stunning designed Table Of Contents For Data Breach Prevention And Recovery Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Table Of Contents For Data Breach Prevention And Recovery Brochure Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Our Table Of Contents For Data Breach Prevention And Recovery Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.








Slide 1 of 9
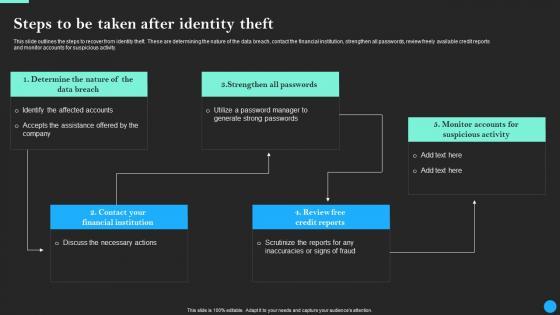
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the steps to recover from identity theft. These are determining the nature of the data breach, contact the financial institution, strengthen all passwords, review freely available credit reports and monitor accounts for suspicious activity.








Slide 1 of 9
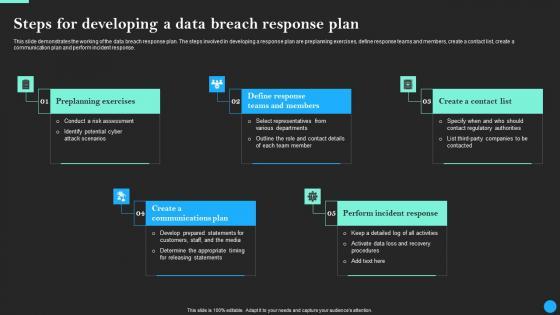
There are so many reasons you need a Steps For Developing A Data Breach Response Plan Data Breach Prevention Demonstration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response.









Slide 1 of 9
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.








Slide 1 of 10
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.








Slide 1 of 9
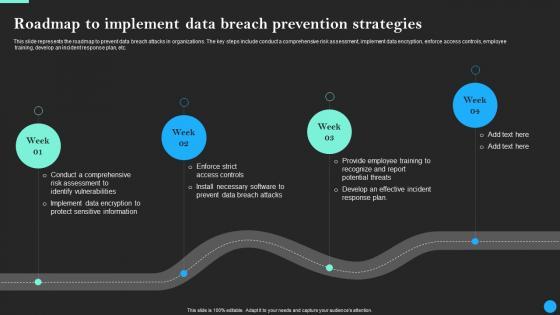
Create an editable Roadmap To Implement Data Breach Prevention Strategies Rules Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Roadmap To Implement Data Breach Prevention Strategies Rules Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.










Slide 1 of 10
Boost your pitch with our creative Potential Causes For Data Breach Attacks Data Breach Prevention Ideas Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.









Slide 1 of 9
Find a pre-designed and impeccable Phases Of Data Breach Attack Cycle Data Breach Prevention Template Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc.








Slide 1 of 9
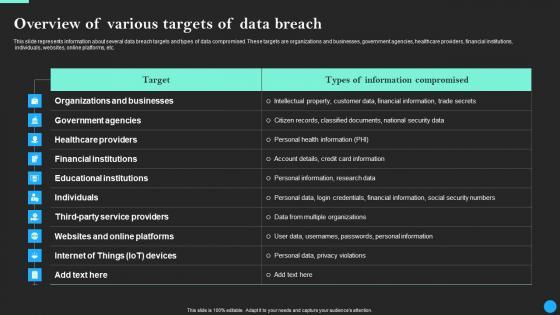
This slide represents information about several data breach targets and types of data compromised. These targets are organizations and businesses, government agencies, healthcare providers, financial institutions, individuals, websites, online platforms, etc. Do you know about Slidesgeeks Overview Of Various Targets Of Data Breach Data Breach Prevention Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents information about several data breach targets and types of data compromised. These targets are organizations and businesses, government agencies, healthcare providers, financial institutions, individuals, websites, online platforms, etc.








Slide 1 of 10
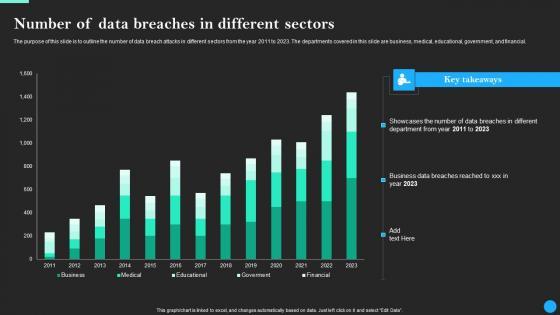
The purpose of this slide is to outline the number of data breach attacks in different sectors from the year 2011 to 2023. The departments covered in this slide are business, medical, educational, government, and financial. Take your projects to the next level with our ultimate collection of Number Of Data Breaches In Different Sectors Data Breach Prevention Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to outline the number of data breach attacks in different sectors from the year 2011 to 2023. The departments covered in this slide are business, medical, educational, government, and financial.








Slide 1 of 9
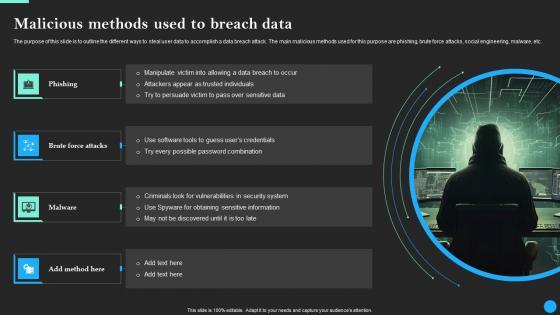
The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc. This Malicious Methods Used To Breach Data Data Breach Prevention Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc.









Slide 1 of 9
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf. This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc.








Slide 1 of 9
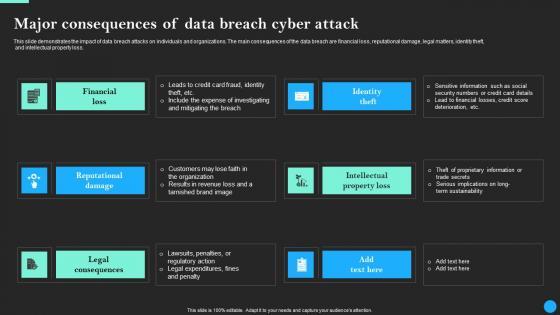
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.









Slide 1 of 9
This slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc. Slidegeeks has constructed Information Included In Data Breach Notification Data Breach Prevention Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc.








Slide 1 of 9
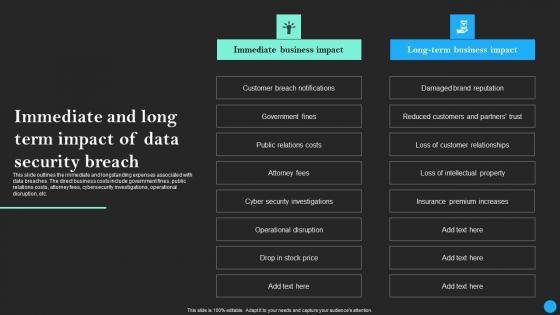
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.








Slide 1 of 9
Introducing our well designed Icons Slide For Data Breach Prevention And Recovery Summary Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Data Breach Prevention And Recovery Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 88 Item(s)
Page
