AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Confidential data PowerPoint Presentation Templates and Google Slides
24 Item(s)



























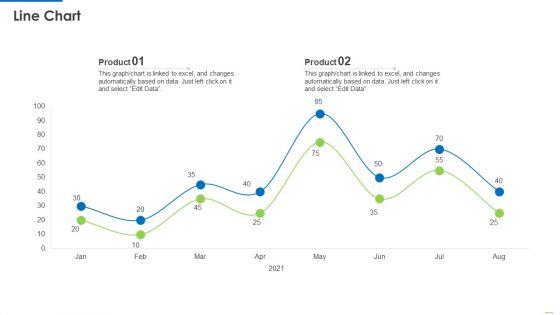


Slide 1 of 42
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
Slide 1 of 2
Presenting Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benefit Of Block Chain, Technology For Securing, Confidential Data Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Slide 1 of 2
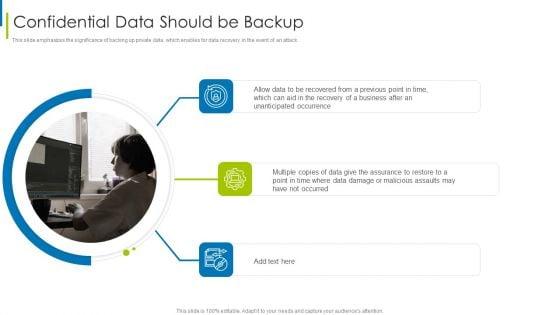
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
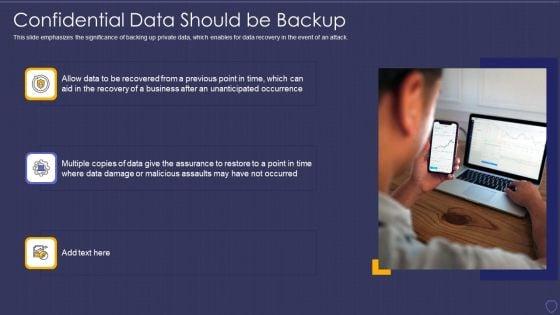
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data roadmap professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Introducing our well designed Executing security management program to mitigate threats and safeguard confidential organizational data icons slide inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Slide 1 of 2
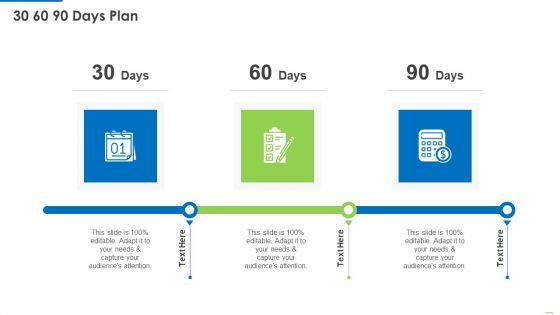
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Presenting Agenda for executing security management program to mitigate threats and safeguard confidential organizational data clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like effective response procedures, intentional or otherwise, enable organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Persuade your audience using this hacker stealing business confidential data base through internet threats ppt powerpoint presentation file pictures pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hacker stealing business confidential data base through internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Presenting data breach vector showing confidential documents ppt powerpoint presentation gallery skills pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breach vector showing confidential documents. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Presenting person working to hack confidential data ppt powerpoint presentation file images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person working to hack confidential data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
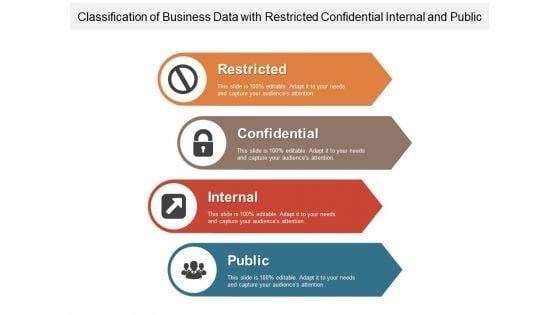
Slide 1 of 2
Presenting this set of slides with name classification of business data with restricted confidential internal and public ppt powerpoint presentation infographics slides pdf. This is a four stage process. The stages in this process are restricted, confidential, internal, public. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name classification of business data with public internal confidential and secret ppt powerpoint presentation gallery slides pdf. This is a four stage process. The stages in this process are public use, internal use, confidential, top secret. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
Presenting this set of slides with name classification of business data with public employee confidential and management restricted ppt powerpoint presentation icon layout ideas pdf. This is a five stage process. The stages in this process are public, confidential, employee confidential, management restricted, private. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
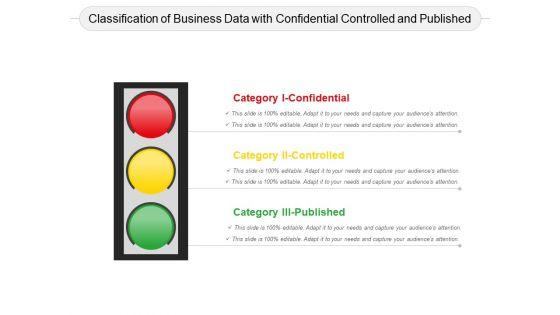
Slide 1 of 2
Presenting this set of slides with name classification of business data with confidential controlled and published ppt powerpoint presentation summary layout pdf. This is a three stage process. The stages in this process are classification of business data with confidential controlled and published. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name confidentiality data protection ppt powerpoint presentation outline slideshow cpb. This is an editable Powerpoint three stages graphic that deals with topics like confidentiality data protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.









Slide 1 of 9
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.








Slide 1 of 9
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
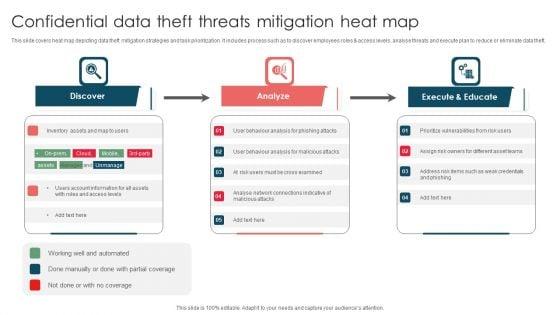
This slide covers heat map depicting data theft mitigation strategies and task prioritization. It includes process such as to discover employees roles and access levels, analyse threats and execute plan to reduce or eliminate data theft. Presenting Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Discover, Analyze, Execute And Educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Take your projects to the next level with our ultimate collection of Integrating Data Privacy System Integrity And Confidentiality Principle Of GDPR Law Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.



















Slide 1 of 19
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Data Segment Categories Confidential Essentials Process Technologies Ppt Presentation has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Types Of Data Segments, Data Segmentation Categories, Categories Of Data Segments, Data Categorization Techniques, Data Segment Classification-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. Our Data Segment Categories Confidential Essentials, Process, and Technologies templates are expertly designed to provide visually appealing and professional backdrop for any presentation. Perfect for showcasing complex topics, these templates assist you present with confidence and expertise.









Slide 1 of 9
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
24 Item(s)
