AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Cybersecurity Risk Mitigation PowerPoint Presentation Templates and Google Slides
8 Item(s)


Slide 1 of 2
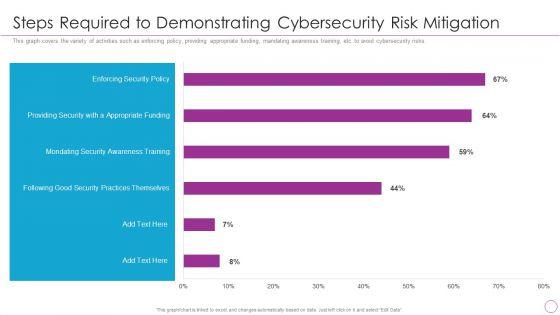
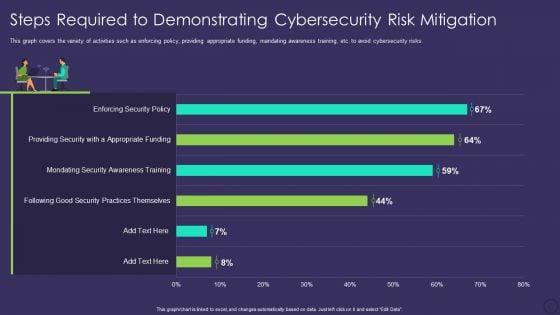
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
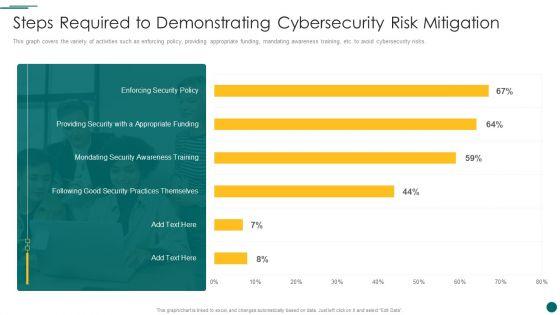
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF bundle. Topics like Steps Required Demonstrating, Cybersecurity Risk Mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
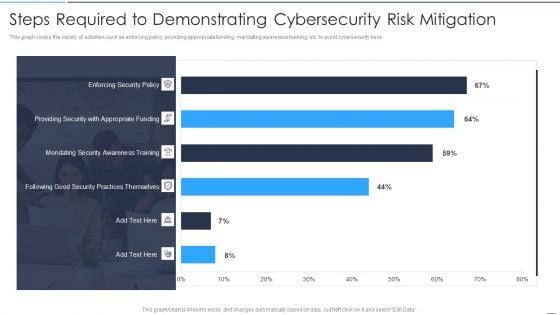
Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative comprehensive business digitization deck steps required to demonstrating cybersecurity risk mitigation microsoft pdf bundle. Topics like enforcing policy, providing appropriate funding, mandating awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto scaling. Presenting this PowerPoint presentation, titled Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto scaling.
8 Item(s)
