AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Exploitation PowerPoint Presentation Templates and Google Slides
48 Item(s)































Slide 1 of 58
Pitch yourself both in house and outside by utilizing this complete deck. This cyber exploitation it ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty eight slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.


Slide 1 of 2
This slide depicts the email prevention guidelines for employees, including spam filters and multi-factor authentication for email login credentials. Presenting cyber exploitation it email prevention guidelines for employees formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like usage of a spam filter, usage of mfa. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Deliver an awe inspiring pitch with this creative table of contents for cyber exploitation it pictures pdf bundle. Topics like budget, implementation plan, strategies to prevent hacking, impact of new strategies on business, current situation of the business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
Introducing our well designed icons slide for cyber exploitation it portrait pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Slide 1 of 2
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
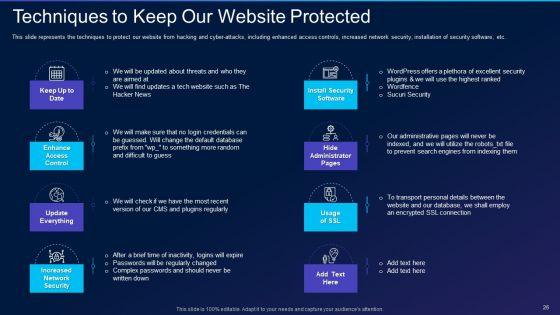
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
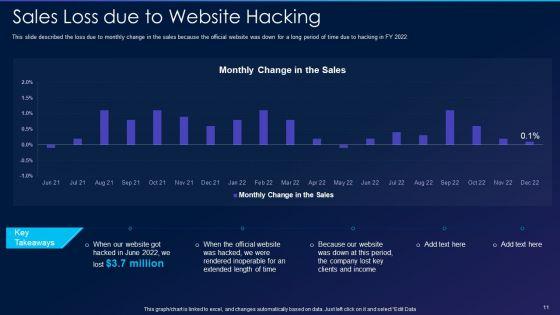
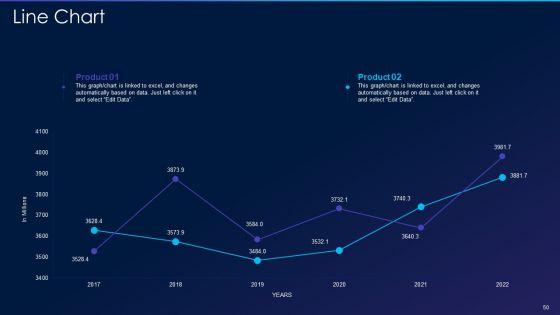
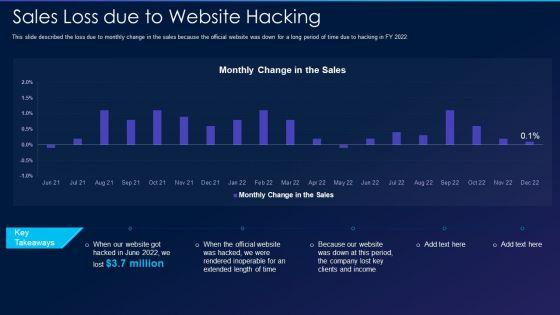
This slide described the loss due to monthly change in the sales because the official website was down for a long period of time due to hacking in FY 2022. Deliver an awe inspiring pitch with this creative cyber exploitation it sales loss due to website hacking designs pdf bundle. Topics like sales loss due to website hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
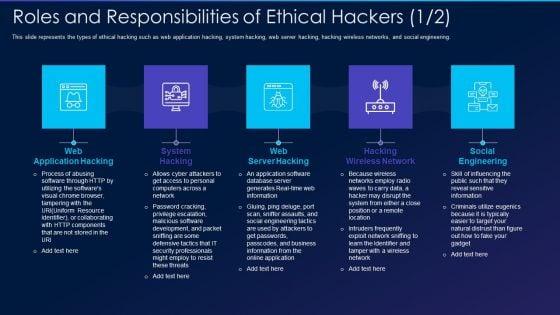
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Presenting cyber exploitation it roles and responsibilities of ethical hackers pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like web application hacking, system hacking, web server hacking, hacking wireless network, social engineering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
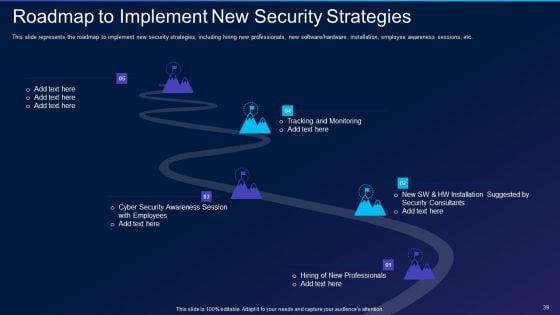
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
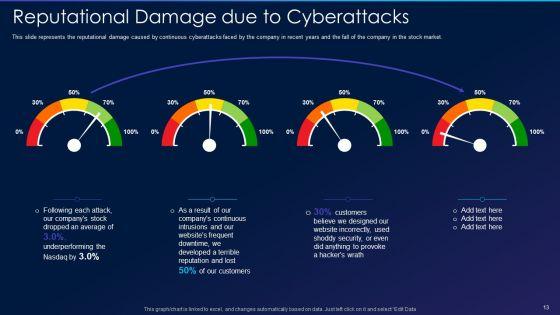
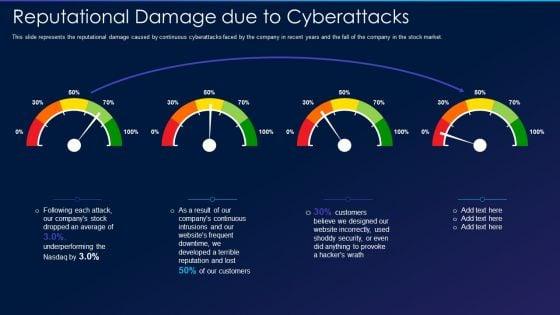
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an awe inspiring pitch with this creative cyber exploitation it reputational damage due to cyberattacks professional pdf bundle. Topics like continuous, developed, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
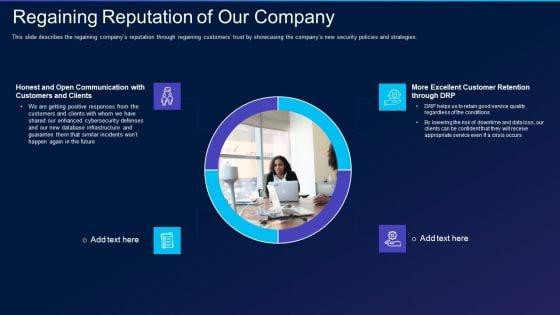
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
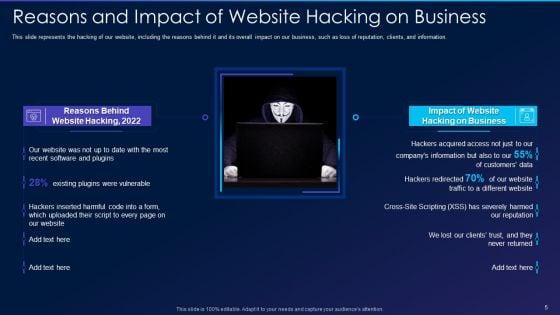
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information. Presenting cyber exploitation it reasons and impact of website hacking on business elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reasons behind website hacking, 2022, impact of website hacking on business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
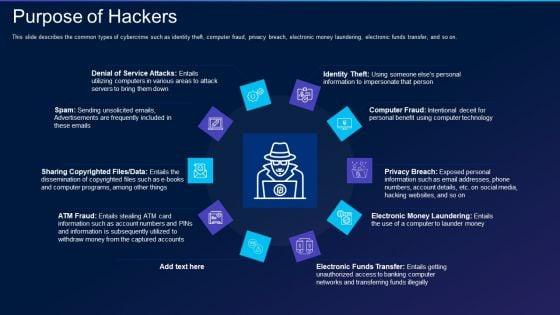
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Deliver an awe inspiring pitch with this creative cyber exploitation it purpose of ethical hacking portrait pdf bundle. Topics like vulnerabilities, management, process, weaknesses, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
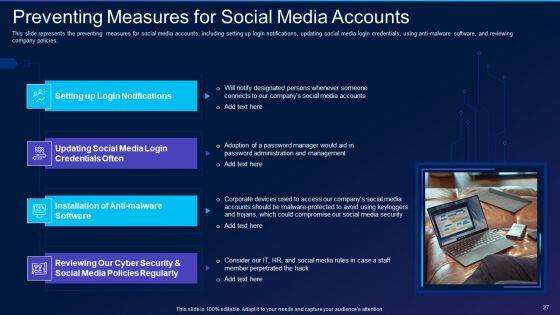
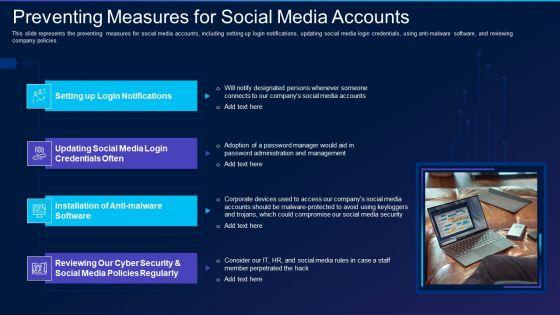
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
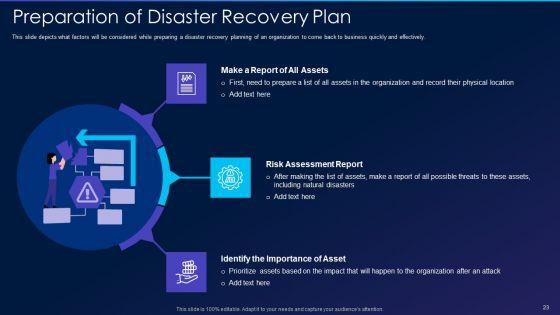
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively. This is a cyber exploitation it preparation of disaster recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of asset. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks. Presenting cyber exploitation it phases of hacking information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reconnaissance, maintaining access, scanning, clearing track, gaining access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
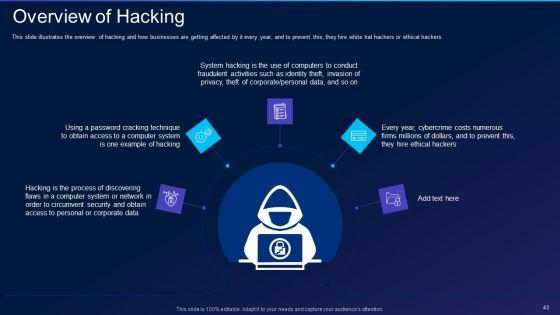
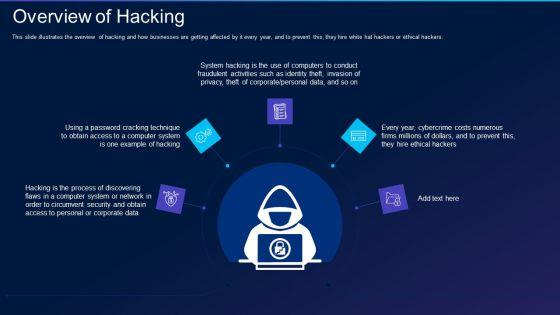
This slide illustrates the overview of hacking and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers. This is a cyber exploitation it overview of hacking information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, process, technique. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
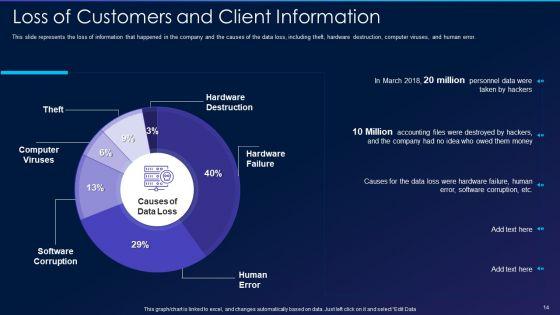
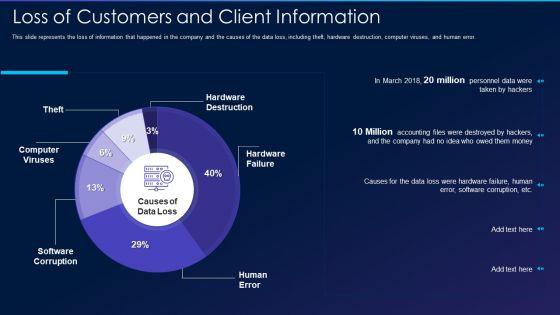
This slide represents the loss of information that happened in the company and the causes of the data loss, including theft, hardware destruction, computer viruses, and human error. Deliver and pitch your topic in the best possible manner with this cyber exploitation it loss of customers and client information guidelines pdf. Use them to share invaluable insights on computer viruses, software corruption, hardware failure, hardware destruction, human error and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative cyber exploitation it loss due to different cyber attacks designs pdf bundle. Topics like loss due to different cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Presenting cyber exploitation it is ethical hacking legal inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like is ethical hacking legal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
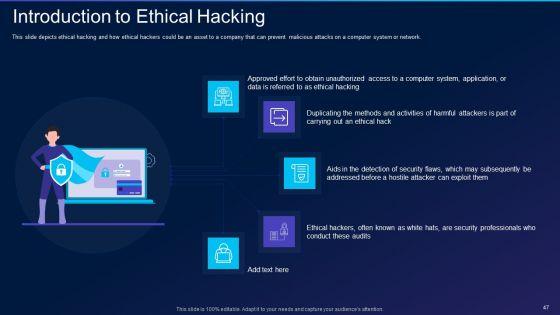
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
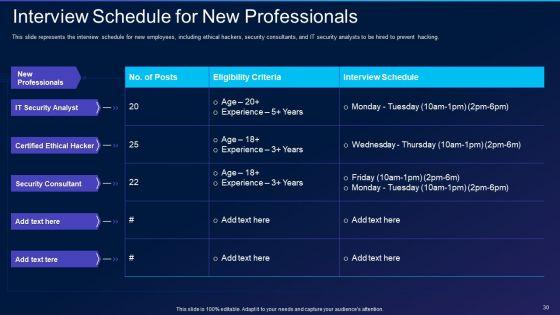
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
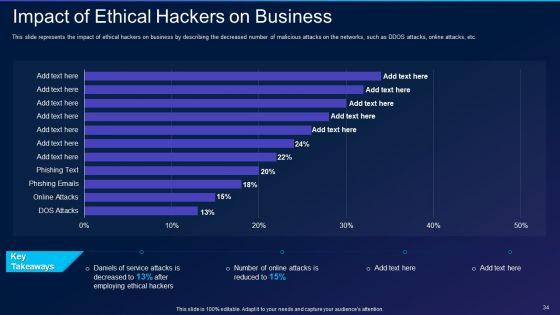
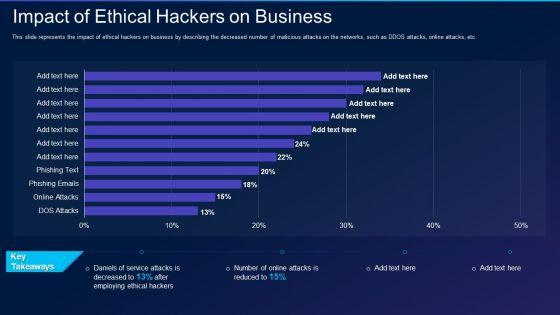
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc. Deliver an awe inspiring pitch with this creative cyber exploitation it impact of ethical hackers on business template pdf bundle. Topics like impact of ethical hackers on business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
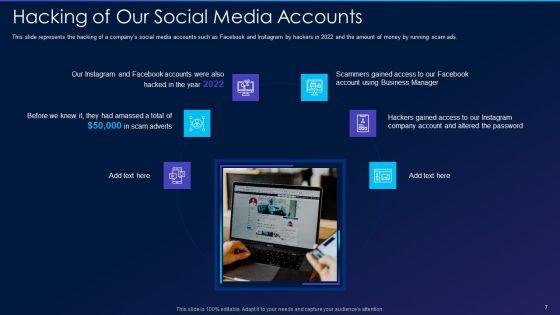
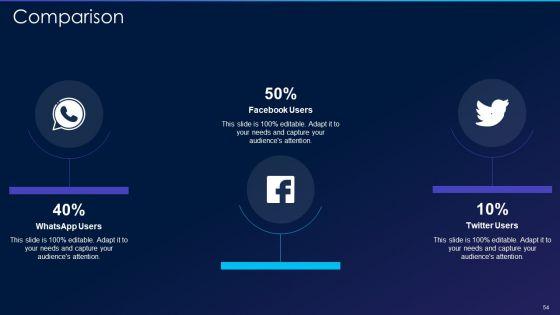
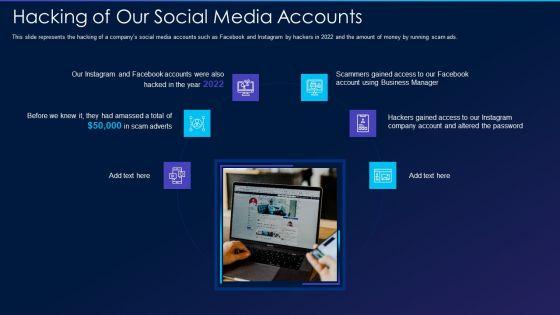
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2022 and the amount of money by running scam ads. This is a cyber exploitation it hacking of our social media accounts template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hacking of our social media accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
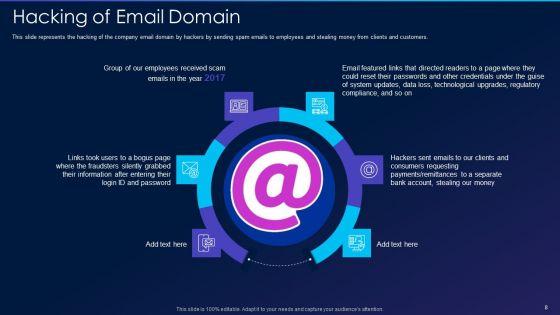
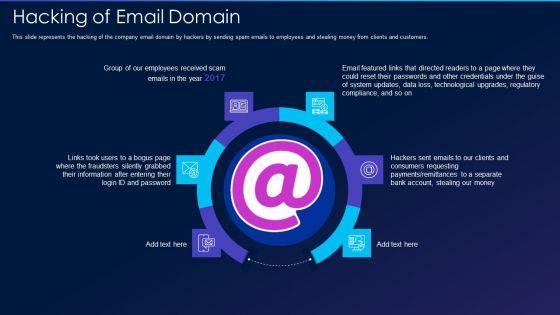
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers. Presenting cyber exploitation it hacking of email domain professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hacking of email domain. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
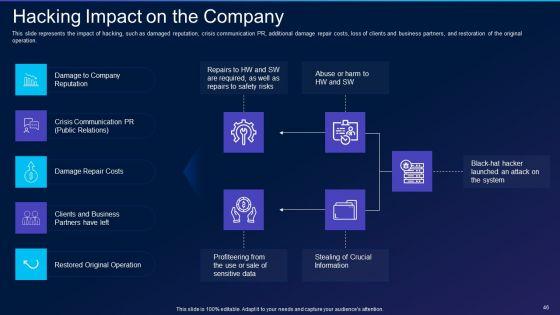
This slide represents the impact of hacking, such as damaged reputation, crisis communication PR, additional damage repair costs, loss of clients and business partners, and restoration of the original operation. This is a cyber exploitation it hacking impact on the company clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business, crisis communication, reputation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
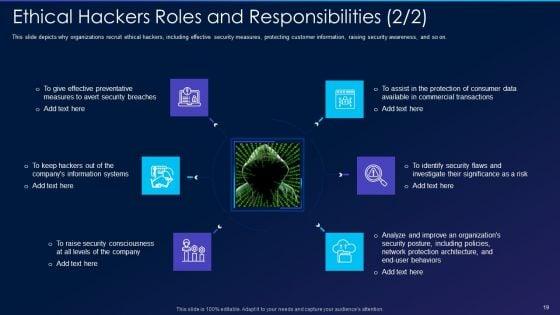
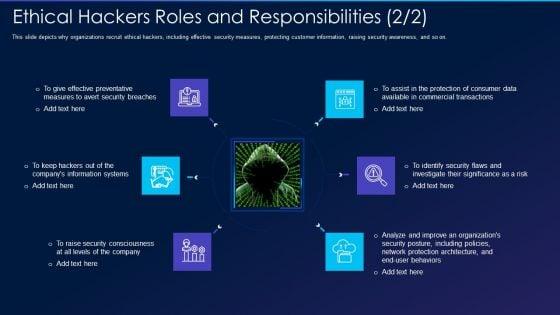
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
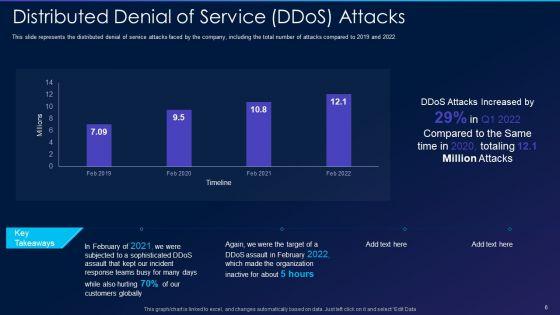
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2019 and 2022. Deliver and pitch your topic in the best possible manner with this cyber exploitation it distributed denial of service ddos attacks professional pdf. Use them to share invaluable insights on distributed denial of service ddos attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
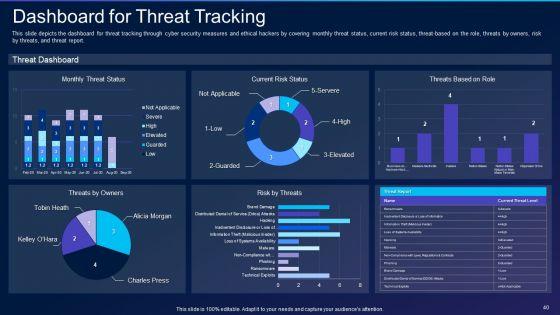
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
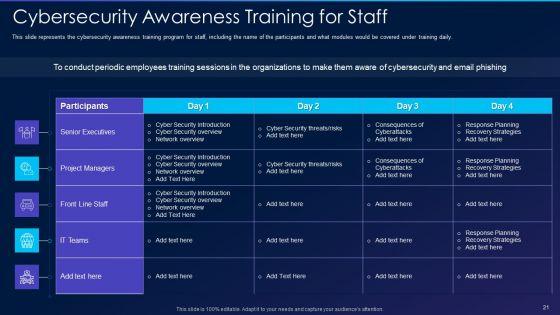
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this cyber exploitation it cybersecurity awareness training for staff formats pdf. Use them to share invaluable insights on senior executives, project managers, front line staff, it teams and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
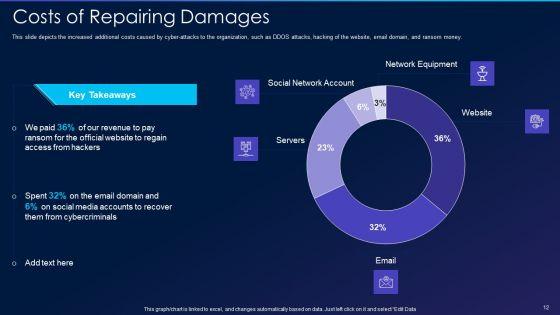
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money. Deliver an awe inspiring pitch with this creative cyber exploitation it costs of repairing damages themes pdf bundle. Topics like social network account, servers, network equipment, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
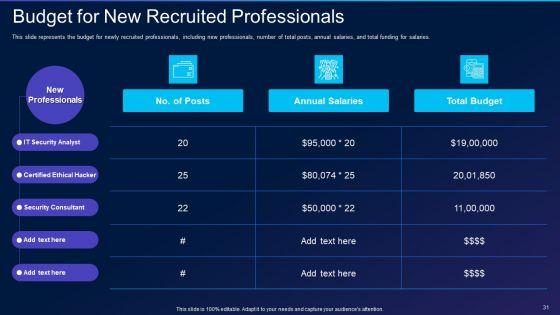
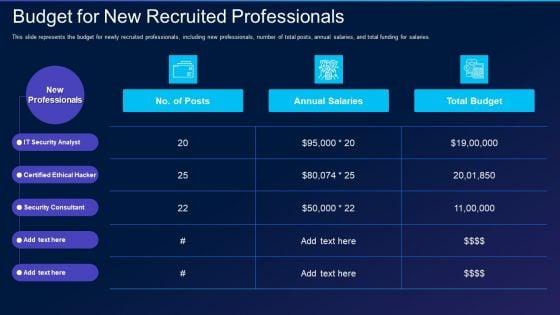
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries. Deliver and pitch your topic in the best possible manner with this cyber exploitation it budget for new recruited professionals demonstration pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
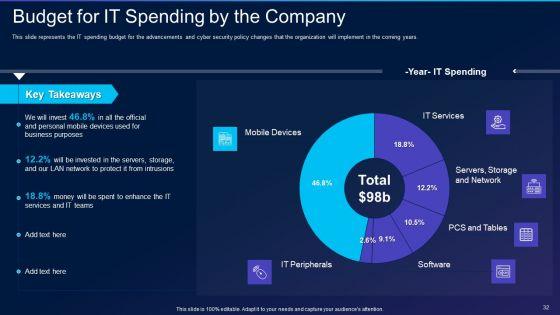
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
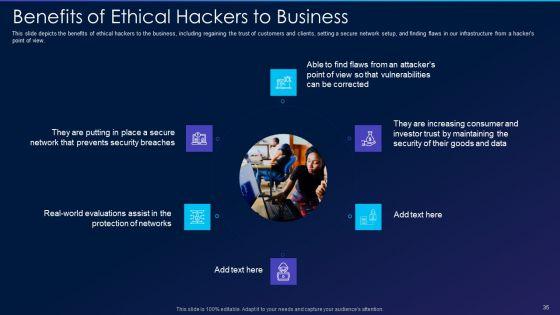
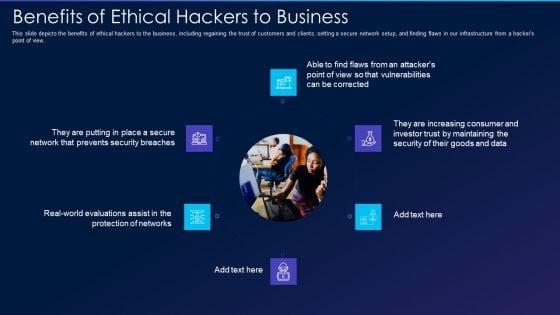
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a cyber exploitation it backup of sensitive information elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services, manipulation, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions. Presenting cyber exploitation it altered business practices due to hacking ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like altered business practices due to hacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
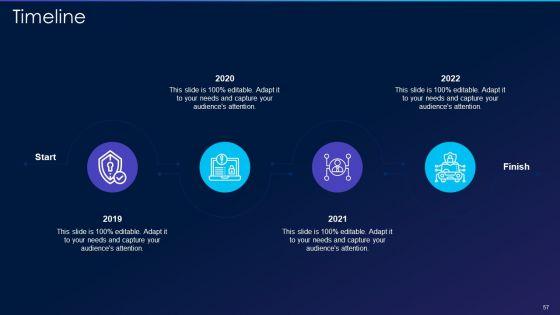
This slide represents the 30-60-90 days plan to implement new strategies in the company, including the tasks performed in each month interval. This is a cyber exploitation it 30 60 90 days plan for new strategies implementation pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan for new strategies implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
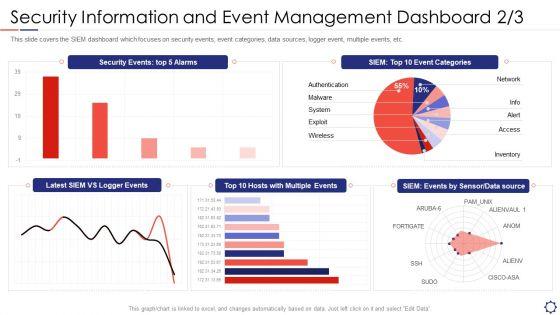
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver and pitch your topic in the best possible manner with this siem security information and event management dashboard exploit slides pdf. Use them to share invaluable insights on network, authentication, wireless, inventory, access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
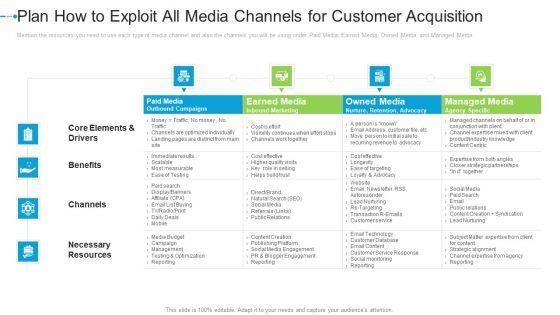
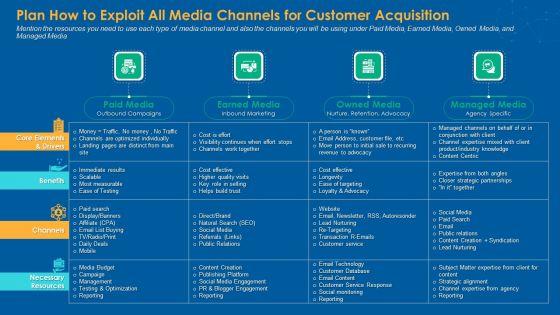
Mention the resources you need to use each type of media channel and also the channels you will be using under Paid Media, Earned Media, Owned Media, and Managed Media. Deliver and pitch your topic in the best possible manner with this plan how to exploit all media channels for customer acquisition information pdf. Use them to share invaluable insights on paid media, earned media, owned media, managed media and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
Mention the resources you need to use each type of media channel and also the channels you will be using under Paid Media, Earned Media, Owned Media, and Managed Media. Deliver an awe-inspiring pitch with this creative plan how to exploit all media channels for customer acquisition icons pdf bundle. Topics like paid media, earned media, owned media, managed media can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
Mention the resources you need to use each type of media channel and also the channels you will be using under Paid Media, Earned Media, Owned Media, and Managed Media. Deliver an awe inspiring pitch with this creative plan how to exploit all media channels for customer acquisition internet marketing strategies to grow your business formats pdf bundle. Topics like paid media, earned media, owned media, managed media can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
Deliver an awe inspiring pitch with this creative plan how to exploit all media channels for customer acquisition professional pdf bundle. Topics like nurture, retention advocacy, inbound marketing, agency specific can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
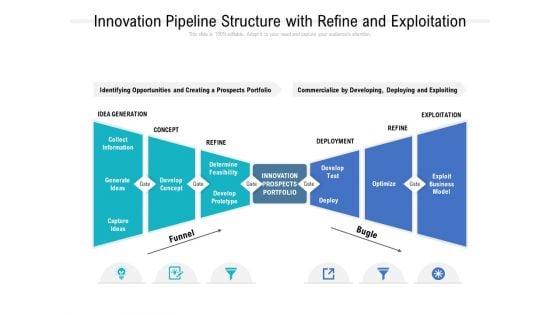
Presenting this set of slides with name innovation pipeline structure with refine and exploitation ppt powerpoint presentation styles visual aids. The topics discussed in these slides are collect information, generate ideas, capture ideas, develop concept, concept, idea generation, exploitation, development, refine, funnel, optimize, exploit business model, innovation prospects portfolio. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.









Slide 1 of 9
This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Welcome to our selection of the Data Exploitation Methods Used By Criminals Data Fortification Strengthening Defenses. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc.









Slide 1 of 9
This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Explore a selection of the finest Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc.








Slide 1 of 9
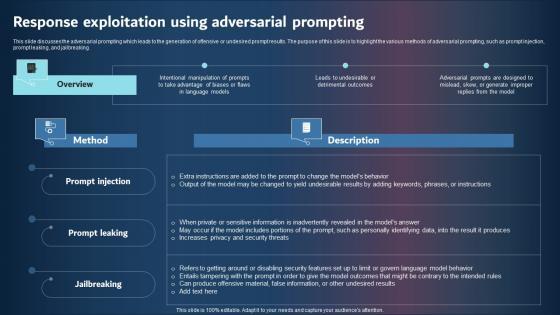
This slide discusses the adversarial prompting which leads to the generation of offensive or undesired prompt results. The purpose of this slide is to highlight the various methods of adversarial prompting, such as prompt injection, prompt leaking, and jailbreaking. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Response Exploitation Using Adversarial Prompting Inspiration Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the adversarial prompting which leads to the generation of offensive or undesired prompt results. The purpose of this slide is to highlight the various methods of adversarial prompting, such as prompt injection, prompt leaking, and jailbreaking.
48 Item(s)
