AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
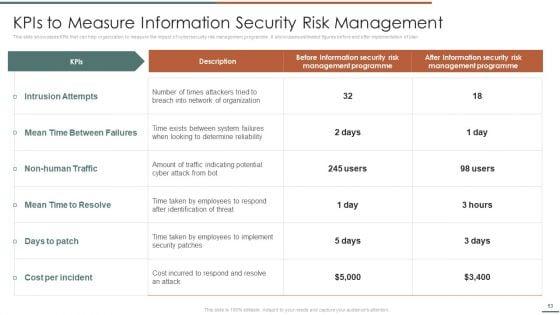
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
It security evaluation PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 97 Item(s)
Page













































Slide 1 of 71
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of sevnty one slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.













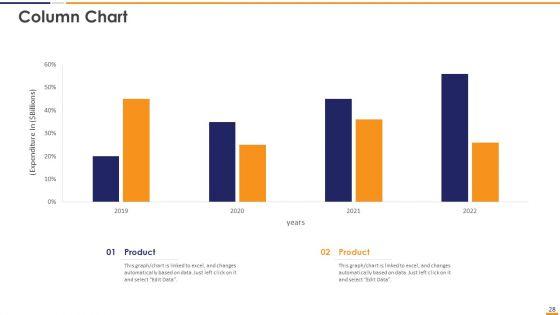

Slide 1 of 29
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes IT Security Evaluation Scorecard Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of twenty nine slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

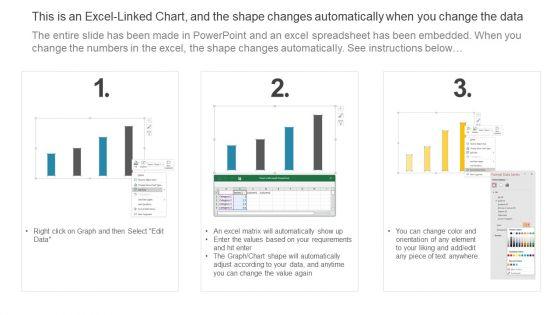
Slide 1 of 2
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. There are so many reasons you need a Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.


Slide 1 of 2
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
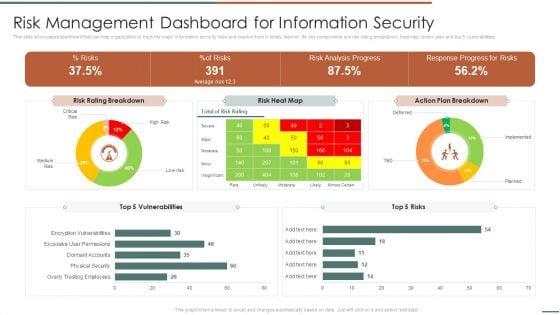

Slide 1 of 2
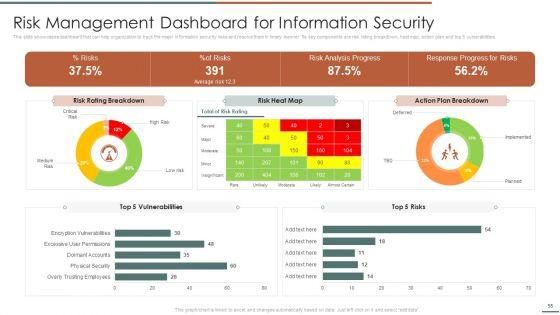
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
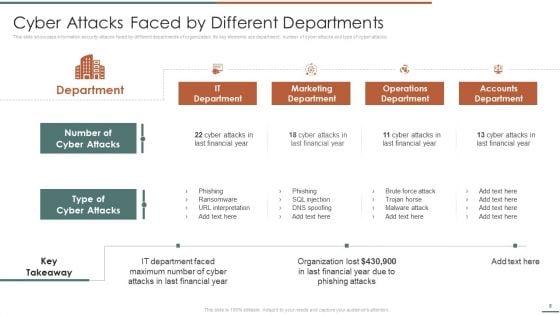
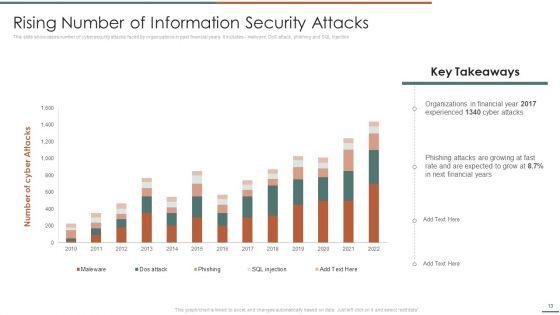
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
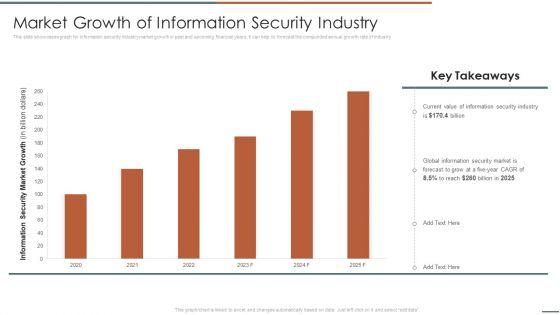
Slide 1 of 2
Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF
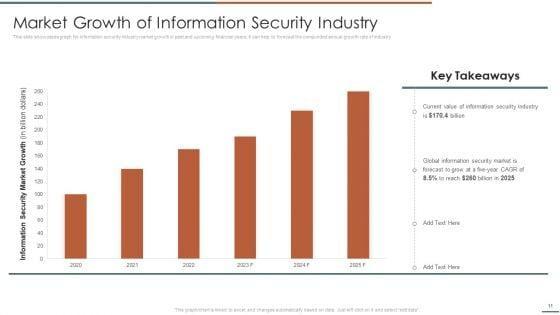
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF. Use them to share invaluable insights on Information Security, Global Information, Security Market and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
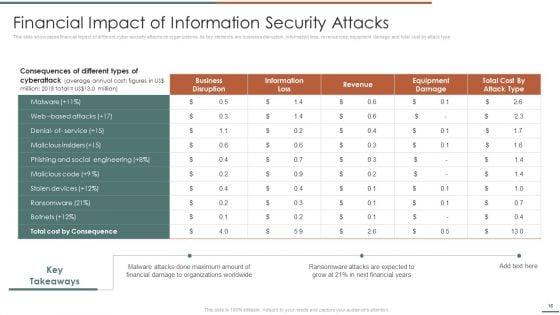
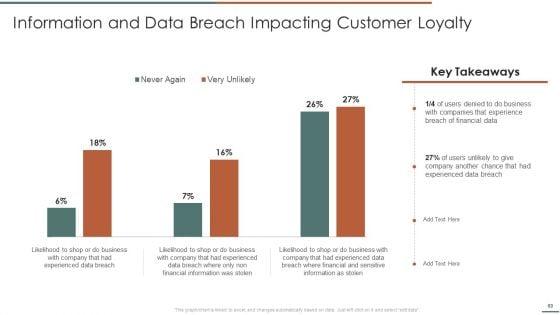
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
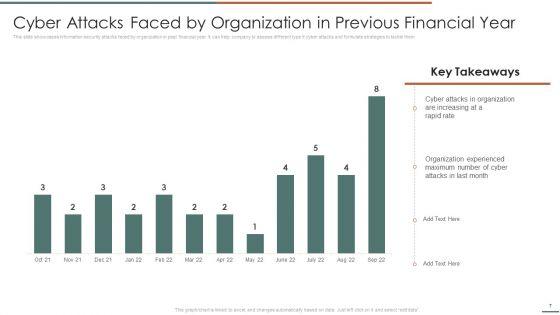
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF. Use them to share invaluable insights on Attacks In Organization, Organization Experienced, Attacks Last and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
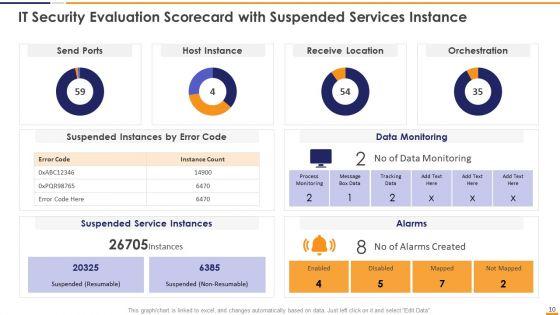
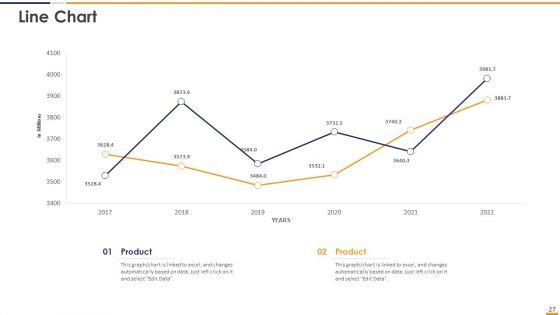
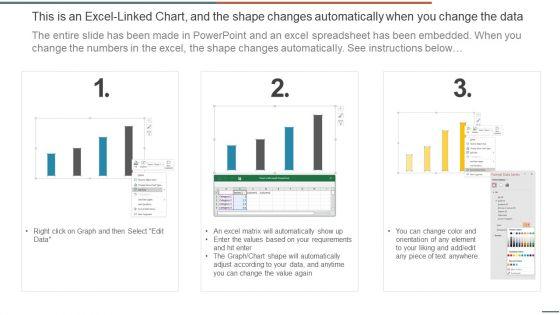
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Suspended Services Instance Graphics PDF. Use them to share invaluable insights on Send Ports Alarms, Host Instance Orchestration, Receive Location Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
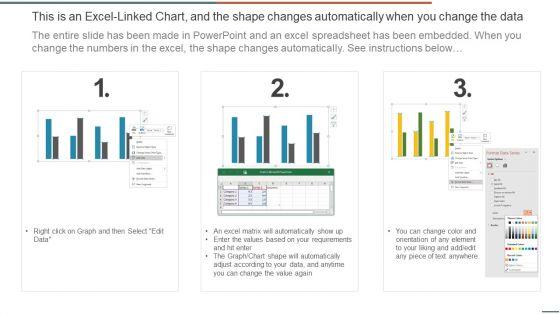
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF bundle. Topics like IT Support Employee, Per Thousand End, user Over Time, Uptime And Downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
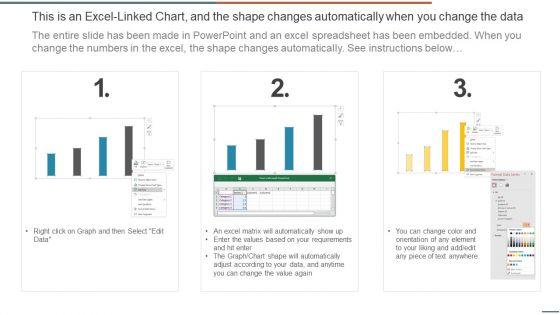
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
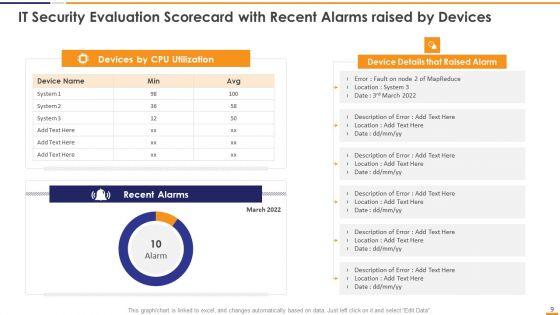
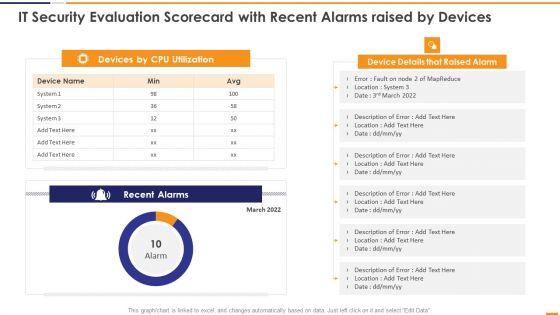
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF bundle. Topics like Devices CPU Utilization, Device Details Raised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
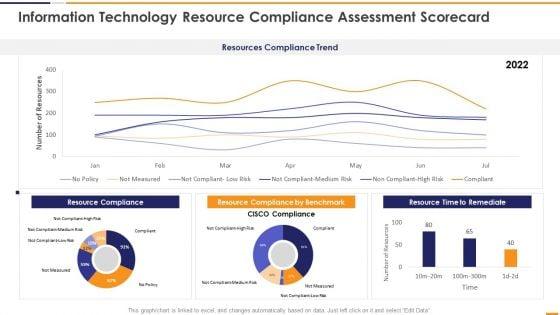
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
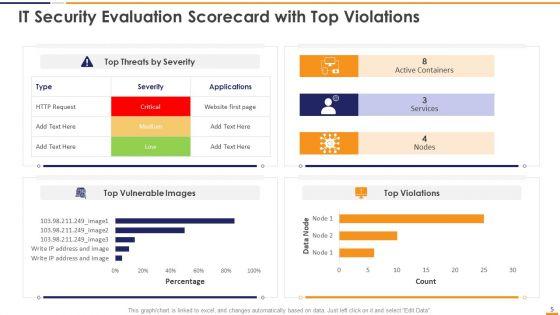
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
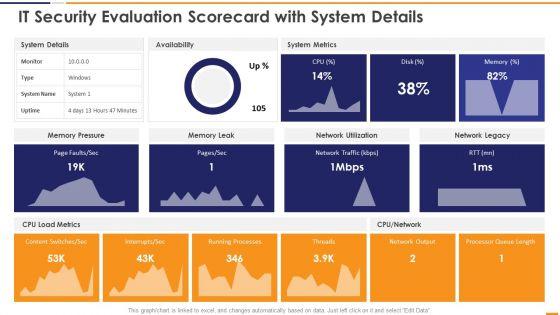
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
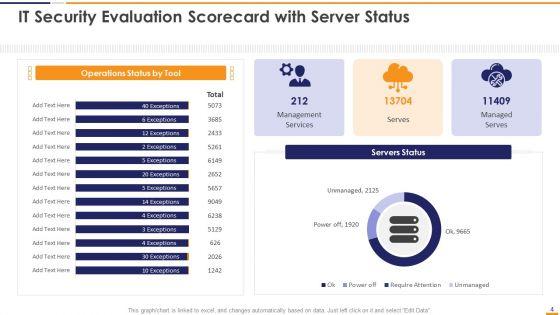
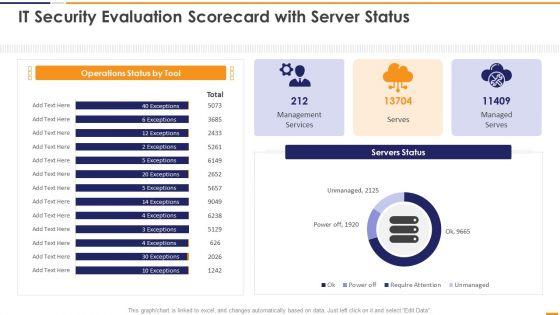
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
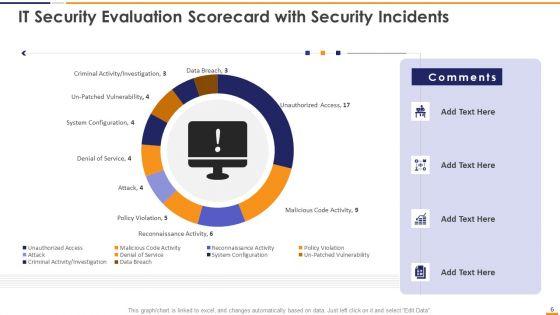
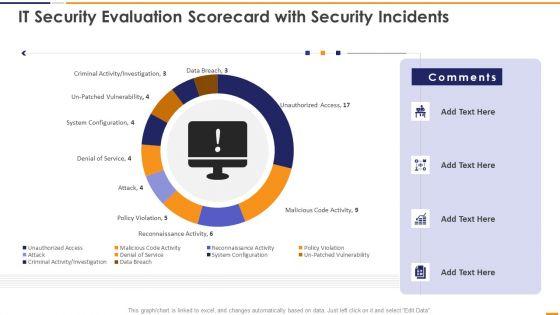
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Security Incidents Ppt Pictures Vector PDF. Use them to share invaluable insights on Unauthorized Access Sales, Malicious Code Activity, Reconnaissance Activity Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
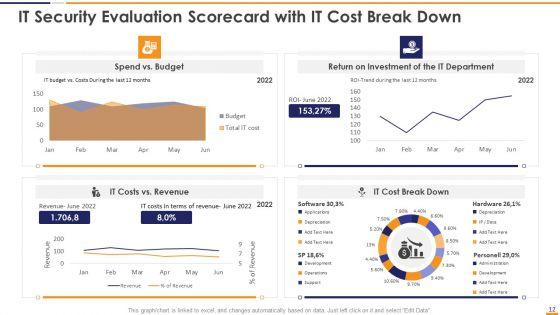
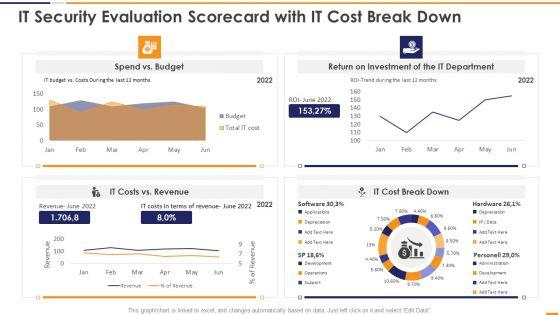
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
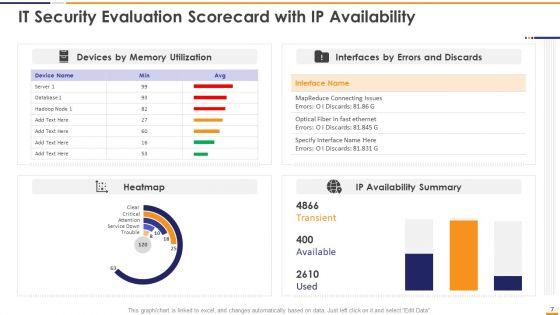
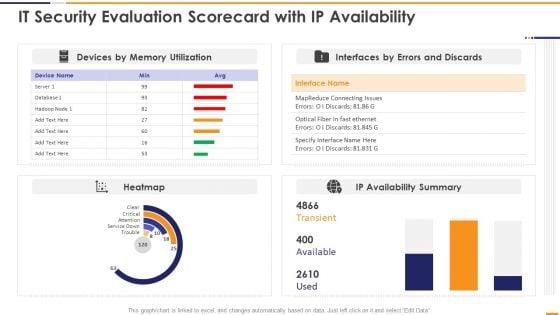
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
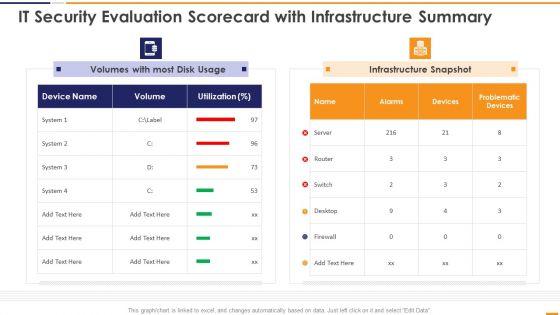
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF bundle. Topics like Volumes Most Disk, Usage Infrastructure Snapshot can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
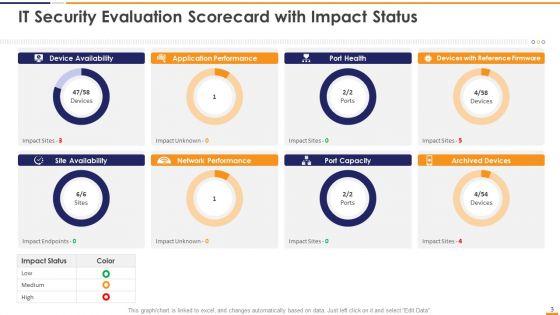
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
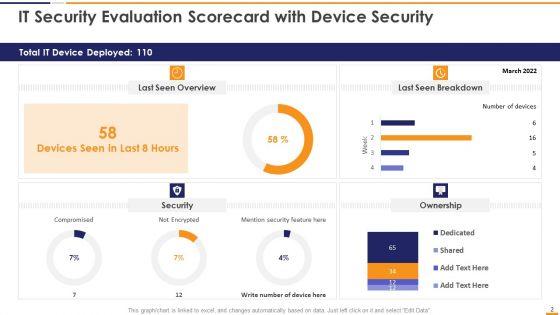
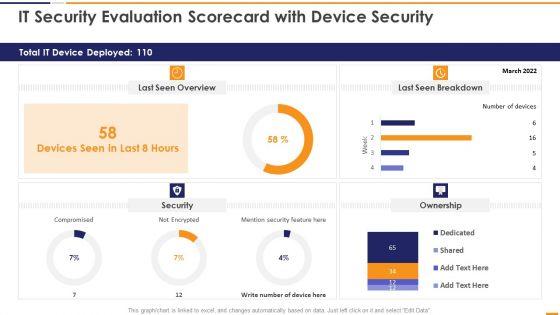
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
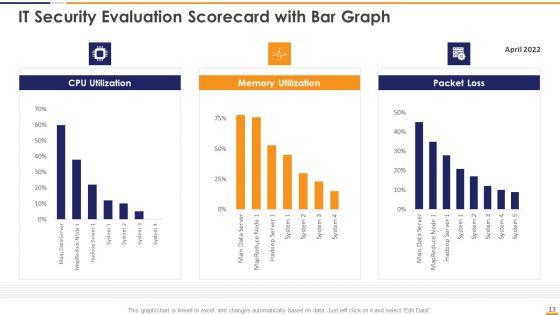
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
Introducing our well designed Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Slide 1 of 2
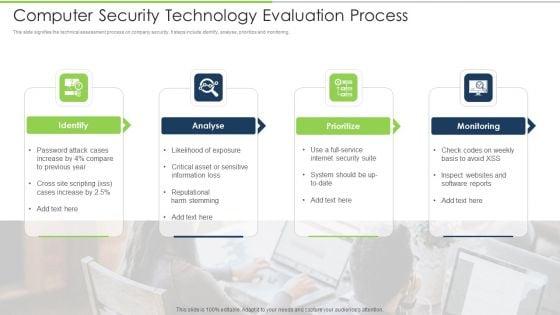
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Slide 1 of 2
This is a program evaluation templates bundle security risk assessment ppt infographic template brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like solution, risk, asset and consequences, vulnerability, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
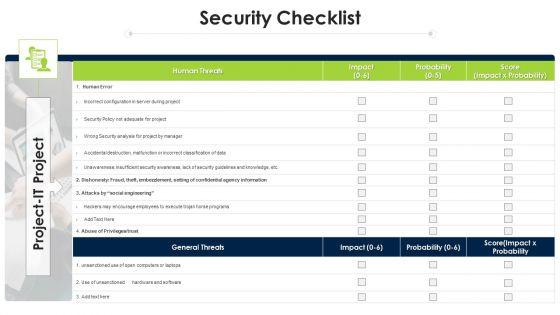
Deliver and pitch your topic in the best possible manner with this program evaluation templates bundle security checklist ppt outline graphics tutorials pdf. Use them to share invaluable insights on project it project, human threats, general threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
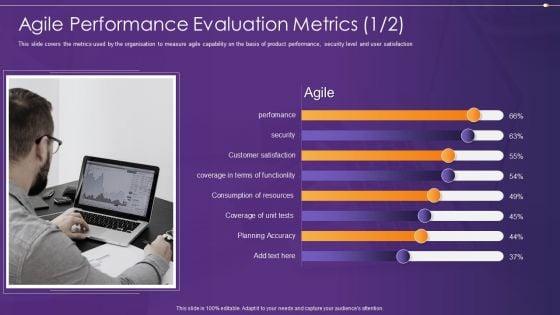
This slide covers the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction Deliver and pitch your topic in the best possible manner with this agile information technology project administration agile performance evaluation metrics security ideas pdf. Use them to share invaluable insights on agile performance evaluation metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
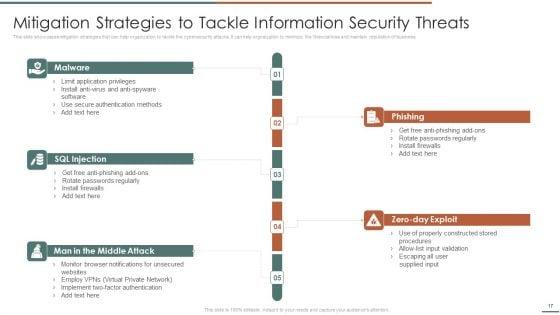
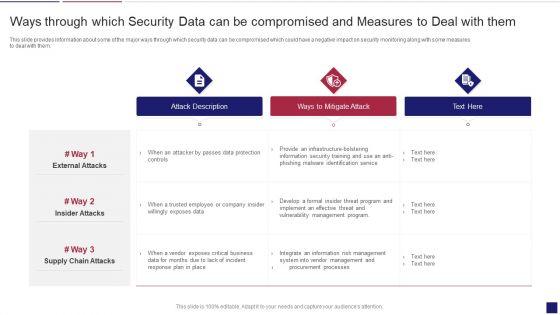
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
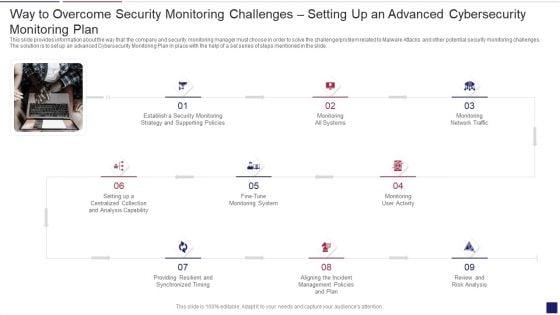
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
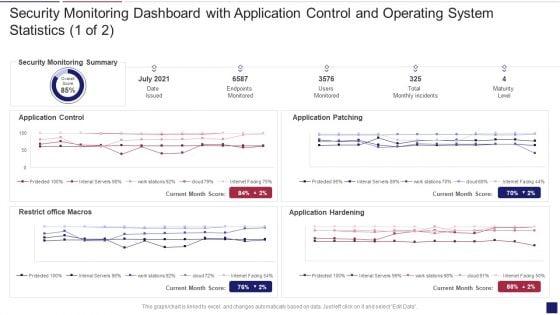
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
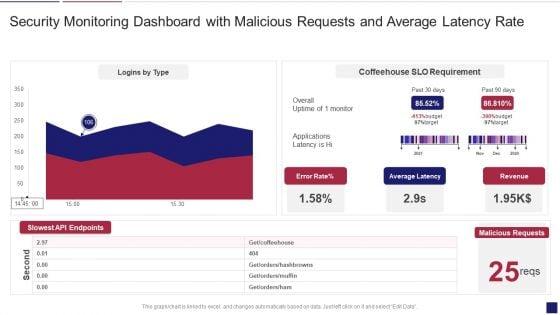
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks security monitoring dashboard rate summary pdf. Use them to share invaluable insights on security monitoring dashboard with malicious requests and average latency rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
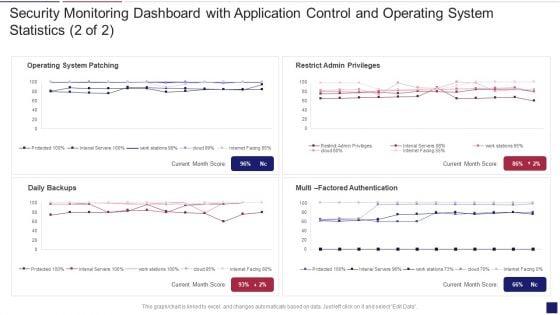
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
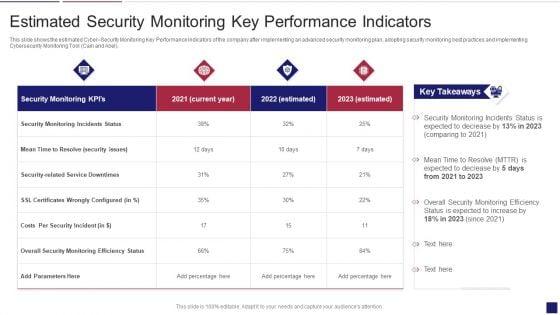
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
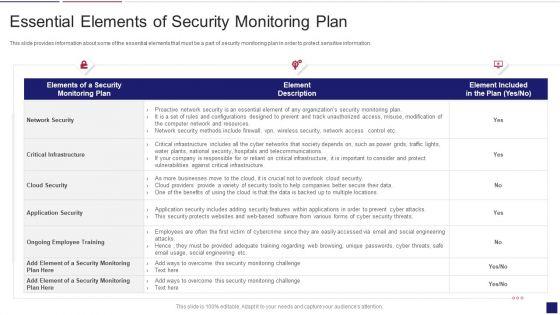
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
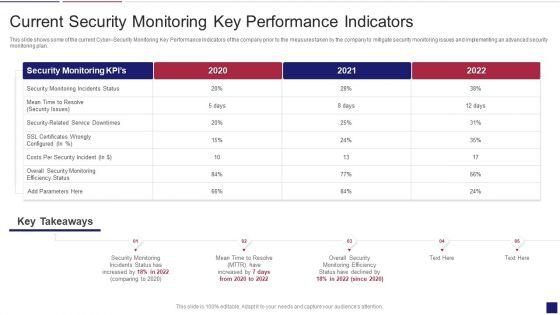
Slide 1 of 2
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
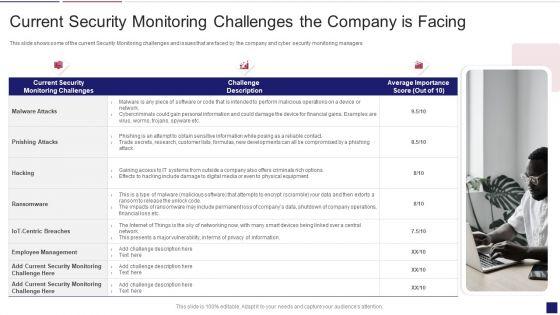
Slide 1 of 2
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a continuous development evaluation plan eliminate cyber attacks current security monitoring key portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
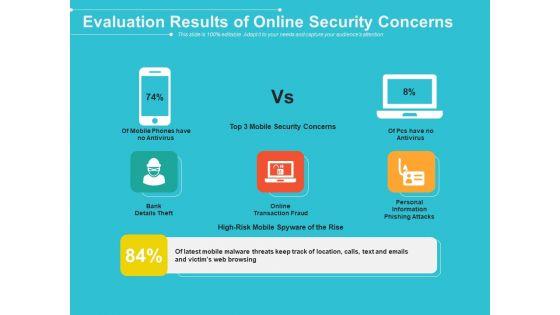
Slide 1 of 2
Pitch your topic with ease and precision using this evaluation results of online security concerns ppt powerpoint presentation file summary pdf. This layout presents information on evaluation results of online security concerns. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
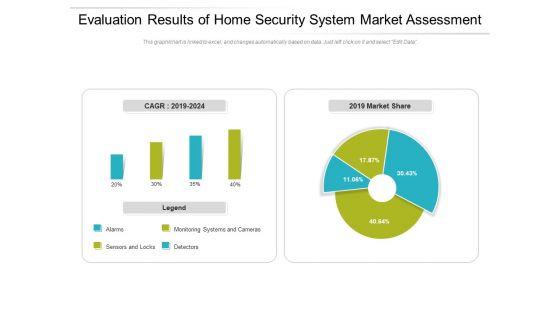
Slide 1 of 2
Pitch your topic with ease and precision using this evaluation results of home security system market assessment ppt powerpoint presentation gallery deck pdf. This layout presents information on monitoring, market, detectors. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.








Slide 1 of 9
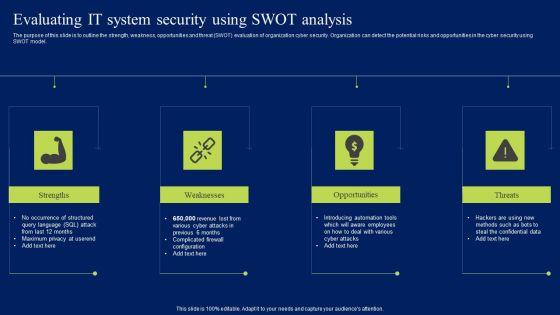
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today









Slide 1 of 9
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.








Slide 1 of 9
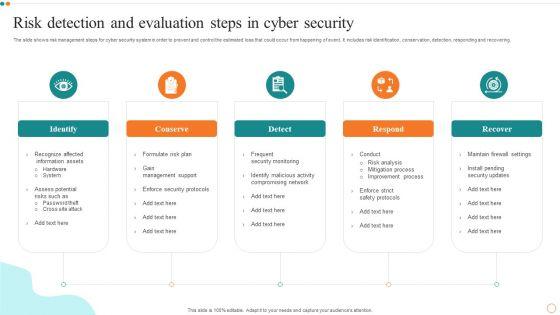
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
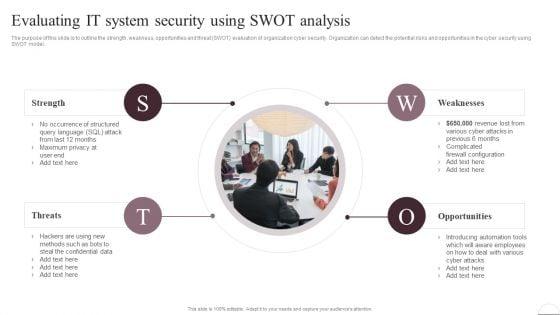
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Slide 1 of 1
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.








Slide 1 of 9
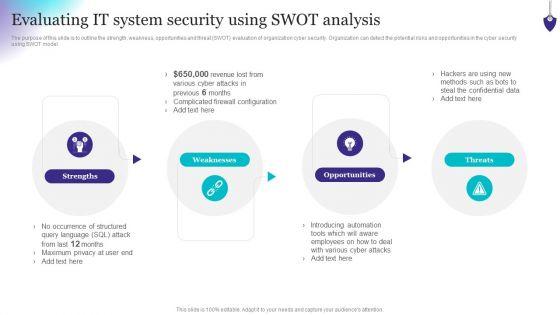
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.









Slide 1 of 9
This slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Persuade your audience using this Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Planning, Execution, Implement, Initiation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
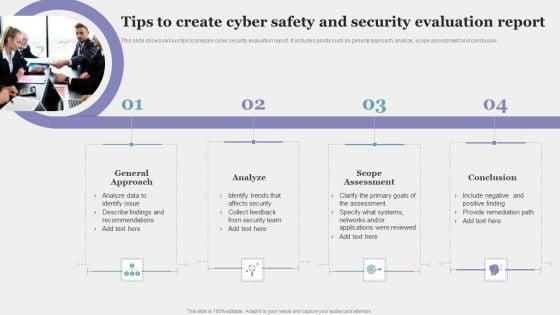








Slide 1 of 9
This slide shows various tips to prepare cyber security evaluation report. It includes points such as general approach, analyze, scope assessment and conclusion. Persuade your audience using this Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including General Approach, Analyze, Scope Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
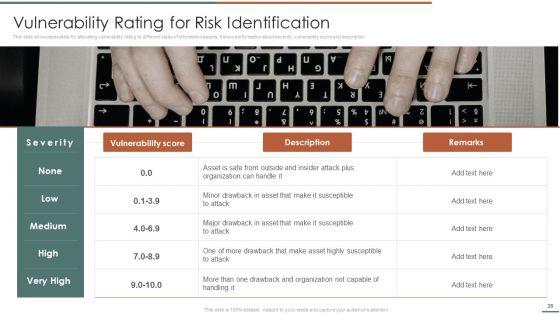
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.









Slide 1 of 9
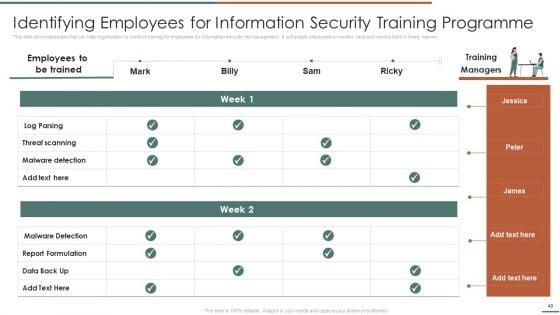
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF bundle. Topics like Cybersecurity Awareness, Malware Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
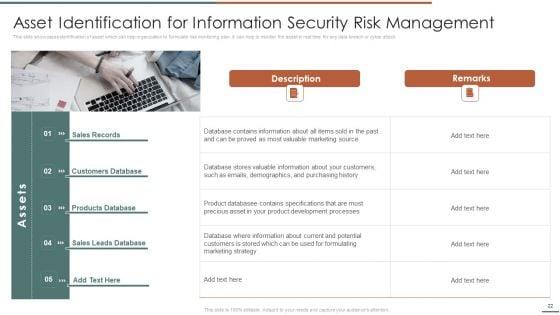
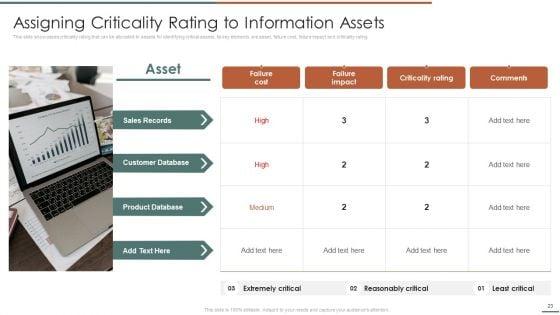
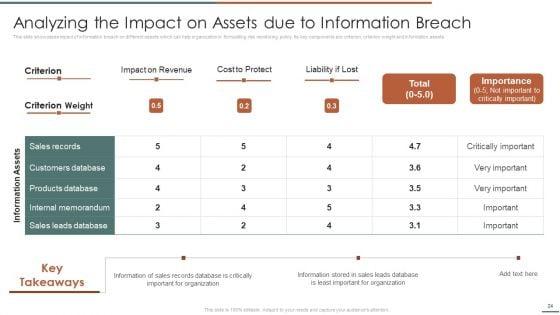
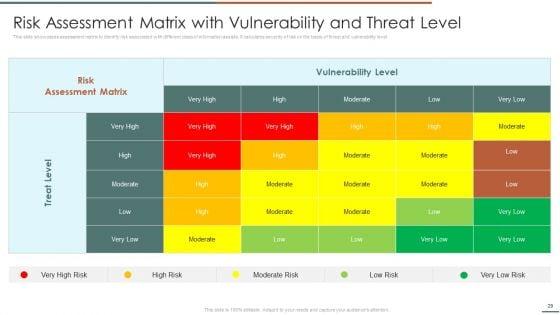
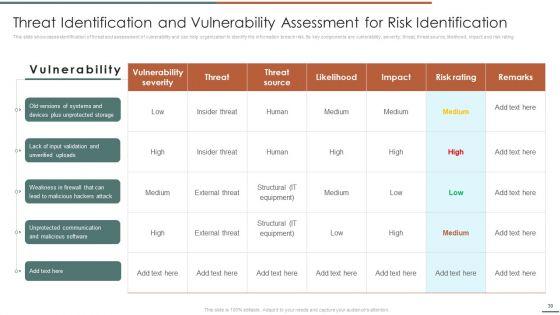
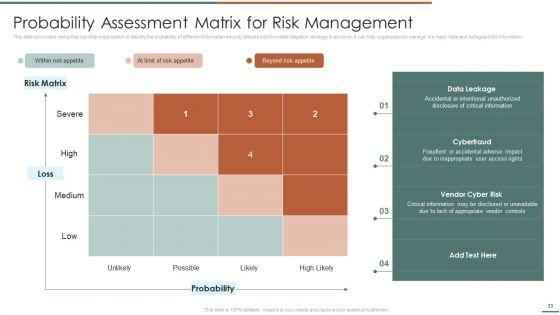
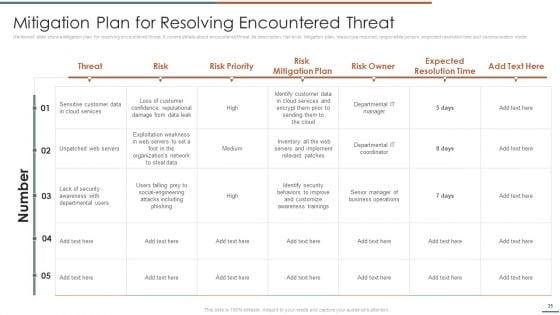
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.









Slide 1 of 9
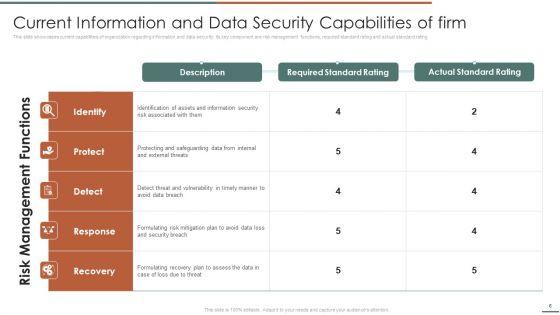
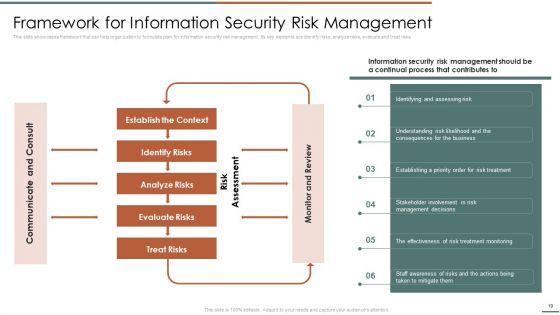
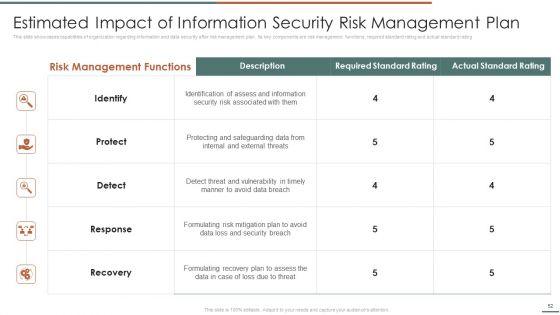
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF bundle. Topics like Awareness And Training, Protective Technology, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
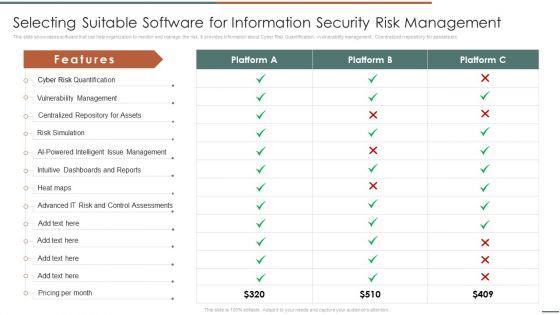








Slide 1 of 9
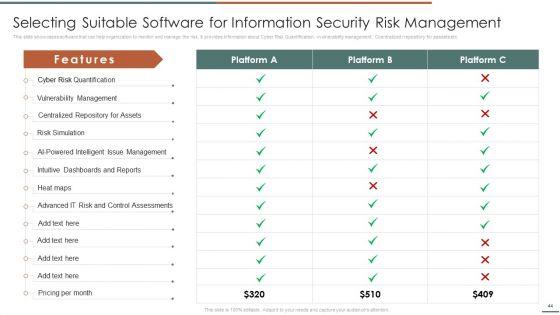
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 97 Item(s)
Page
