AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Phishing PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 127 Item(s)
Page















Slide 1 of 17
Share a great deal of information on the topic by deploying this Phishing Attacks Awareness Training Ppt PowerPoint Presentation Complete With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of seventeen slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.










Slide 1 of 14
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber phishing scams and attacks ppt powerpoint presentation complete with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the fourteen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.


Slide 1 of 2
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Slide 1 of 2
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.


Slide 1 of 2
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Welcome to our selection of the Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Slide 1 of 2
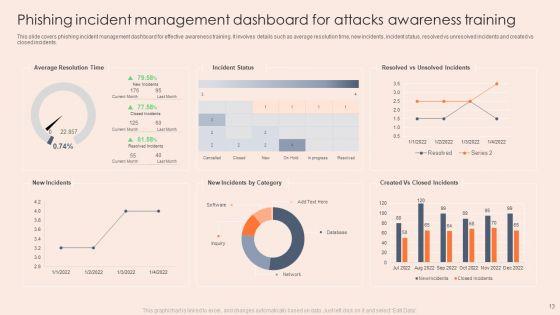
This slide covers phishing incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Pitch your topic with ease and precision using this Phishing Incident Management Dashboard For Attacks Awareness Training Icons PDF. This layout presents information on Phishing Incident Management Dashboard, Attacks Awareness Training. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Slide 1 of 2
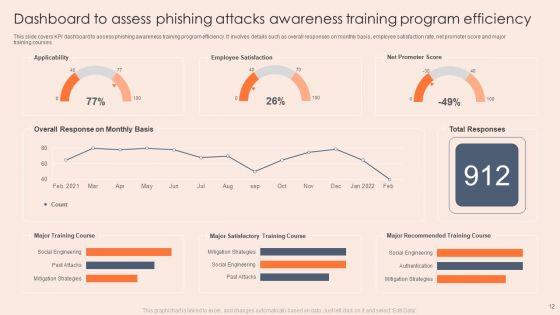
This slide covers KPI dashboard to assess phishing awareness training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Showcasing this set of slides titled Dashboard To Assess Phishing Attacks Awareness Training Program Efficiency Professional PDF. The topics addressed in these templates are Applicability, Employee Satisfaction, Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
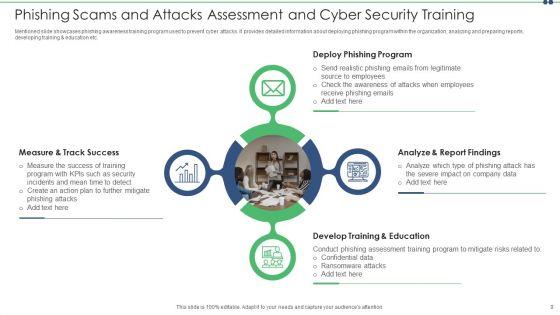
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
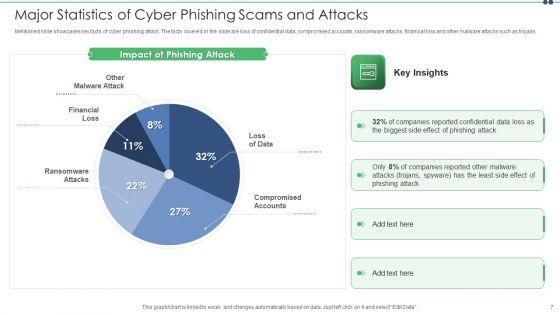
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
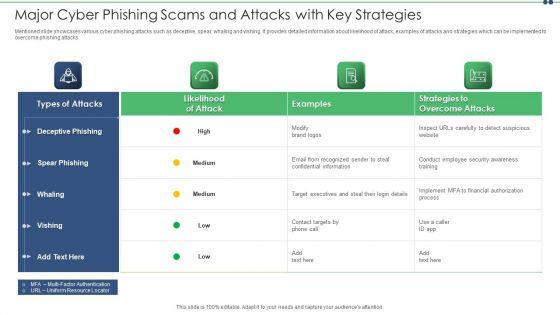

Slide 1 of 2
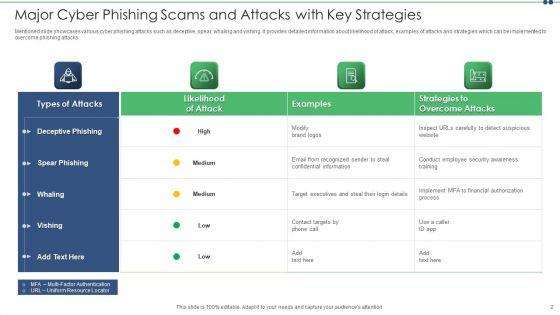
Mentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Showcasing this set of slides titled major cyber phishing scams and attacks with key strategies slides pdf. The topics addressed in these templates are target, information, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
Mentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Persuade your audience using this key statistics of cyber phishing scams and attacks pictures pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including average, email. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
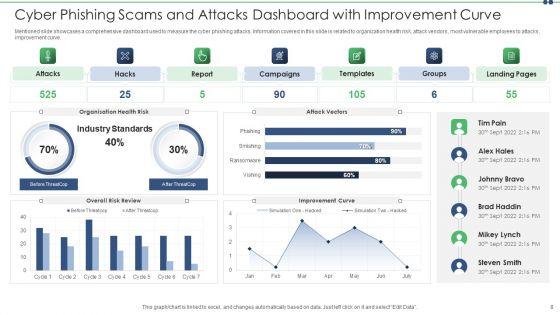
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
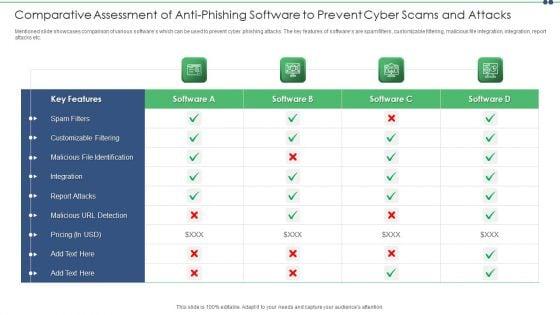
Slide 1 of 2
Mentioned slide showcases comparison of various softwares which can be used to prevent cyber phishing attacks. The key features of softwares are spam filters, customizable filtering, malicious file integration, integration, report attacks etc. Showcasing this set of slides titled comparative assessment of anti phishing software to prevent cyber scams and attacks structure pdf. The topics addressed in these templates are comparative assessment of anti phishing software to prevent cyber scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
Mentioned slide showcases multistep model of cyber phishing attack. The model include points such as attacker sends the email, user opens the email, target system exploitation, installation of RAT etc. Persuade your audience using this 7 step model of spear phishing scams and attacks designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including internal network, compromised system, targeted users. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
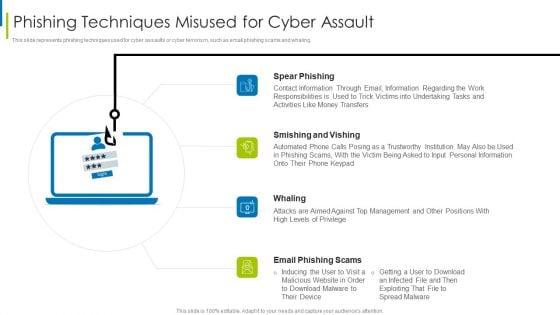
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. This is a cyber terrorism assault phishing techniques misused for cyber assault slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smishing and vishing, spear phishing, contact information through You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
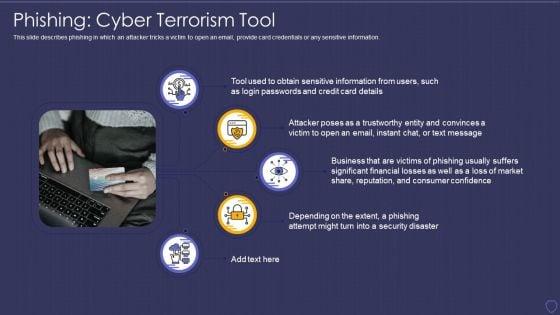
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information.Presenting cyber terrorism assault phishing cyber terrorism tool slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like attacker poses, sensitive information, business that are victims In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
This is a white hat hacking what is phishing attack ppt outline design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, purchasing, required, source. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
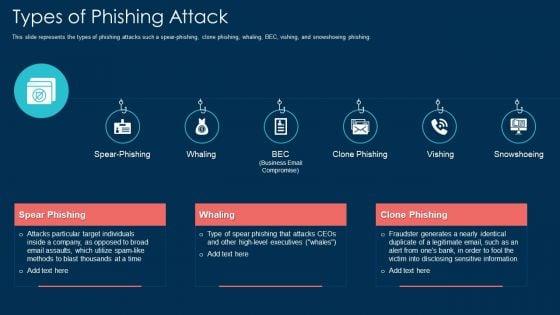
This slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Presenting types of phishing attack ppt outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like types of phishing attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
This slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. This is a security measures to prevent phishing attacks ppt gallery deck pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, organization, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Presenting global cyber terrorism incidents on the rise it phishing techniques misused for cyber assault ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like spear phishing, smishing and vishing, whaling, email phishing scams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Presenting global cyber terrorism incidents on the rise it phishing cyber terrorism tool rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like phishing cyber terrorism tool. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
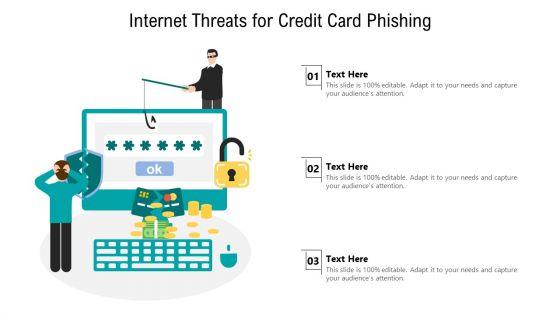
Persuade your audience using this internet threats for credit card phishing ppt powerpoint presentation file layouts pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including internet threats for credit card phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
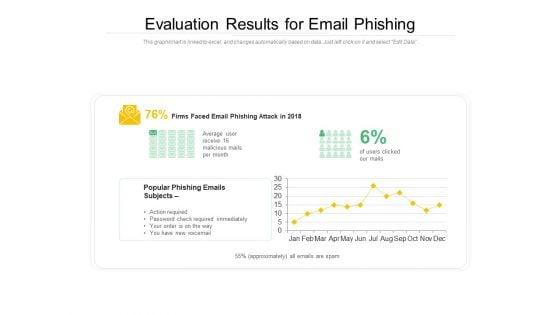
Showcasing this set of slides titled evaluation results for email phishing ppt powerpoint presentation gallery format pdf. The topics addressed in these templates are evaluation results for email phishing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
Presenting this set of slides with name types phishing email ppt powerpoint presentation outline background image cpb. This is an editable Powerpoint five stages graphic that deals with topics like types phishing email to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.









Slide 1 of 9
This slide covers comparative analysis of phishing and simulation training tools. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis Of Phishing And Simulation Training Program Tools Professional PDF. The topics addressed in these templates are Assess Employees, Price, User Rating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.









Slide 1 of 9
Persuade Your Audience Using This Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF. This PPT Design Covers Five Stages, Thus Making It A Great Tool To Use. It Also Caters To A Variety Of Topics Including Updating Security Software, Backing Up Data, Block Unreliable Websites. Download This PPT Design Now To Present A Convincing Pitch That Not Only Emphasizes The Topic But Also Showcases Your Presentation Skills.








Slide 1 of 9
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.









Slide 1 of 9
This slide covers need of phishing awareness training within organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why Phishing Attacks Awareness Training Is Essential For Employees Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assures Staff Education, Enhances Organizational Reputation, Boosts Confidence. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide covers phishing awareness training program and development procedure to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Presenting Phishing Attacks Awareness Training Program Process Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Training Need, Evaluate Training Program, Identify Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Presenting Phishing Attacks Awareness Training Program Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
Presenting Phishing Attacks Awareness Training Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
Presenting Phishing Attacks Awareness Training For Employees Icon Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness Training, Employees Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide covers monthly phishing awareness training program timeline.It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Pitch your topic with ease and precision using this Monthly Phishing Awareness Training Program Timeline Infographics PDF. This layout presents information on Risk Assessments, System, Awareness Training Program Timeline. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.









Slide 1 of 9
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide covers key steps to conduct effective phishing awareness training plan. It involves five steps such as analyse training need, plan, deploy,measure training and optimize results. Persuade your audience using this Key Steps To Conduct Phishing Attacks Awareness Training Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Analyze, Plan, Deploy, Measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide covers employee questionnaire to assess phishing training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess Phishing Attacks Awareness Training Effectiveness Formats PDF. The topics addressed in these templates are Organization, Equipment, Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.









Slide 1 of 9
This slide covers key ways to conduct effective phishing training for employees for overall development. It involves interactive video learning, PowerPoint presentations, quizzes and chunk lessons. Persuade your audience using this Effective Methods Of Phishing Attacks Awareness Training Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Interactive Video Learning, Powerpoint Presentations, Quizzes. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
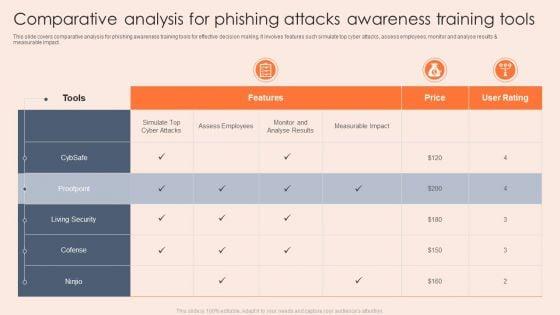
This slide covers comparative analysis for phishing awareness training tools for effective decision making. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF. The topics addressed in these templates are Analyse Results, Measurable Impact, Living Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.









Slide 1 of 9
This slide covers best practices for phishing awareness training plan for successful implementation. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Phishing Attacks Awareness Training Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Establishing Basics, Including Everyone. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide illustrates various types of phishing scams in banks and safety measures. It includes scams like spoof bank emails, spoof bank websites and chase bank phishing scam. Showcasing this set of slides titled Financial Phishing Institution Scam And Mitigation Strategies Sample PDF. The topics addressed in these templates are Bank Phishing Scams, Spoof Bank Emails, Spoof Bank Websites. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.








Slide 1 of 9
Presenting Insider Threat Icon For Financial Information Phishing Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Insider Threat Icon, Financial Information Phishing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide represents the working of evil twin phishing attacks. The key points include set up evil twin fake access point, set up a fake captive portal, push users to sign into evil twin wi-fi and steal victims personal information and login credentials. Take your projects to the next level with our ultimate collection of Working Process Of Evil Twin Phishing Attack Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the working of evil twin phishing attacks. The key points include set up evil twin fake access point, set up a fake captive portal, push users to sign into evil twin wi-fi and steal victims personal information and login credentials.








Slide 1 of 9
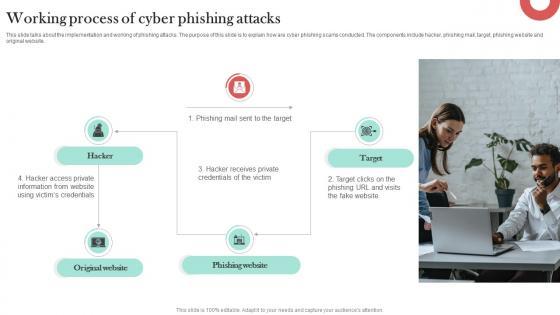
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website.









Slide 1 of 9
This slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc.Take your projects to the next level with our ultimate collection of Working Procedure Of Spear Phishing Attack Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc.








Slide 1 of 9
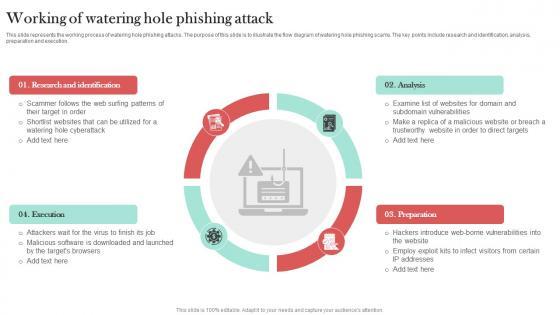
This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. This Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution.









Slide 1 of 9
This slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Working Of Phishing Training Programs Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Working Of Phishing Training Programs Man In The Middle Phishing IT. This slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade.









Slide 1 of 9
This slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Presenting this PowerPoint presentation, titled Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc.









Slide 1 of 9
This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc. Slidegeeks has constructed Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc.









Slide 1 of 9
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.








Slide 1 of 10
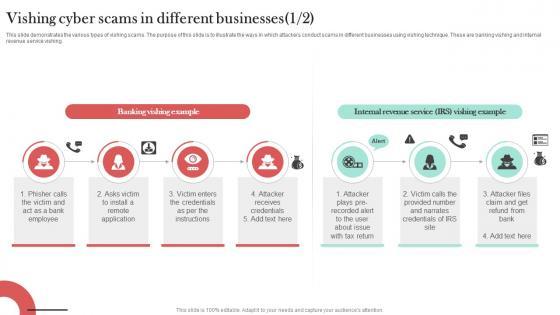
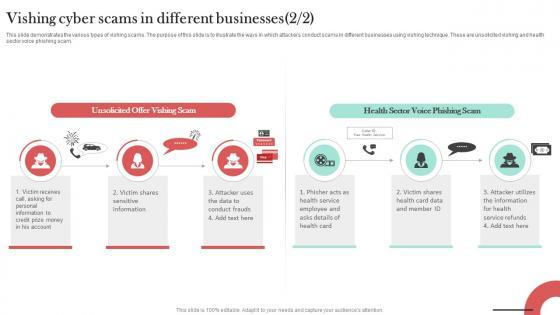
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.









Slide 1 of 9
This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. The Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing.









Slide 1 of 9
This slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Understanding The Process Of E Mail Man In The Middle Phishing IT from Slidegeeks and deliver a wonderful presentation. This slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 127 Item(s)
Page
