AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Security Handled PowerPoint Presentation Templates and Google Slides
56 Item(s)












































Slide 1 of 55
Presenting this set of slides with name computer security incident handling ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are dashboard, management, cybersecurity, analysis, program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
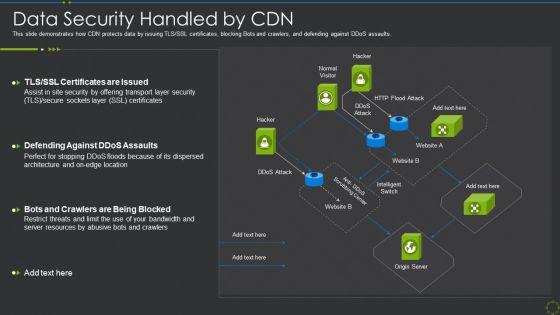
This slide demonstrates how CDN protects data by issuing TLS SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative data security handled by cdn ppt show clipart images pdf bundle. Topics like data security handled by cdn can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling weekly timeline with task name summary pdf. The topics discussed in these slides are weekly timeline with task name. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
Presenting this set of slides with name computer security incident handling vital records maintenance register icons pdf. The topics discussed in these slides are primary location of records, alternate location of records, other sources to obtain records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling timeframe for incident management infographics pdf. The topics discussed in these slides are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling staff training schedule with cost demonstration pdf. The topics discussed in these slides are packages, level 1, level 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling selecting security incident management software graphics pdf. The topics discussed in these slides are software, security incident forms, automated workflows, centralized platform, access rights, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
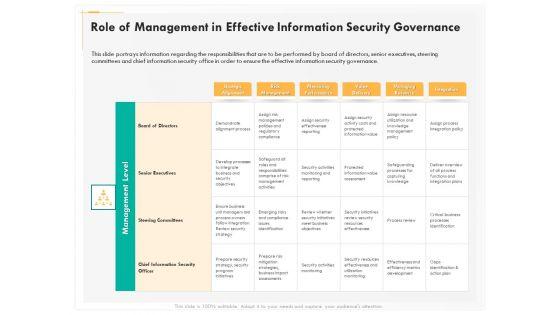
Presenting this set of slides with name computer security incident handling role of management in effective information security governance portrait pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
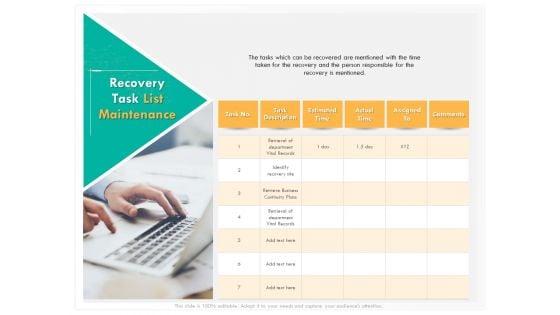
Presenting this set of slides with name computer security incident handling recovery task list maintenance background pdf. The topics discussed in these slides are task no., task description, estimated time, actual time, assigned to, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
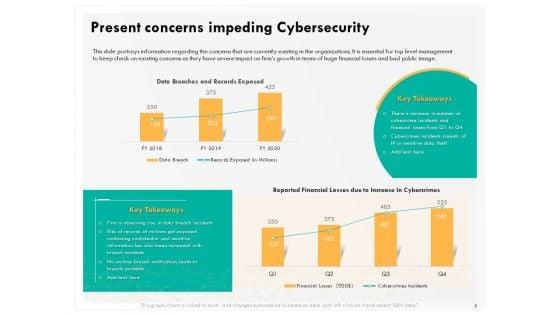
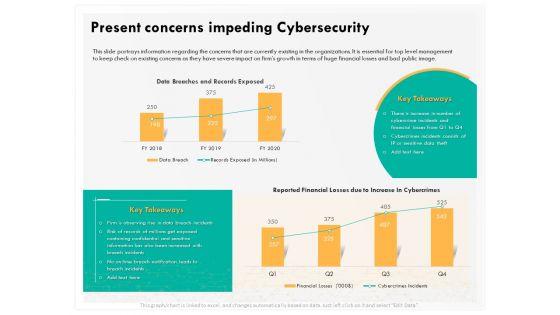
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
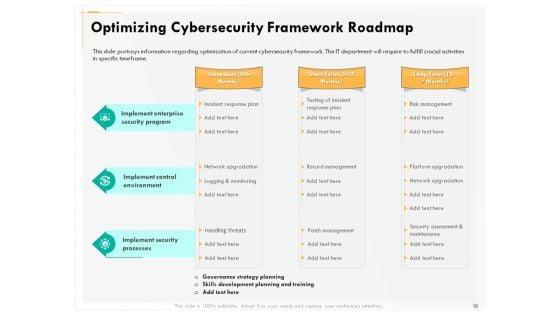
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
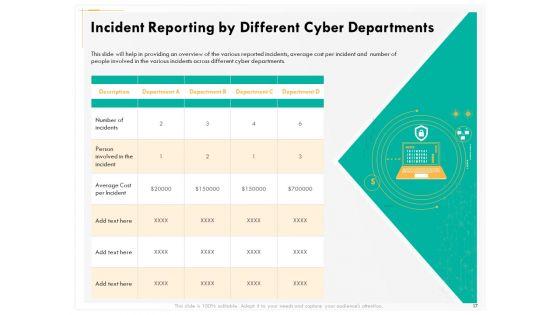
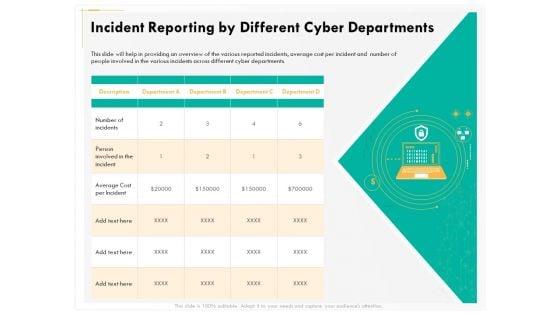
Presenting this set of slides with name computer security incident handling incident reporting by different cyber departments brochure pdf. The topics discussed in these slides are description, department a, department b, department c, department d. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling impact analysis effective security management graphics pdf. The topics discussed in these slides are no. of systems where security requirement not met, no. of access rights authorized, revoked, reset or changed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling essential contingency plan strategies ideas pdf. The topics discussed in these slides are contingency considerations, contingency solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling determining firm current capabilities inspiration pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
Presenting this set of slides containing editable icons for topic icons slide for computer security incident handling ppt ideas example topics pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.

Slide 1 of 2
Presenting this set of slides with name computer security incident handling thank you ppt summary designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling table of contents ppt show grid pdf. The topics discussed in these slides are dashboard, impact analysis, incident management, cost associated to firm, role of personnel, analyzing current scenario. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
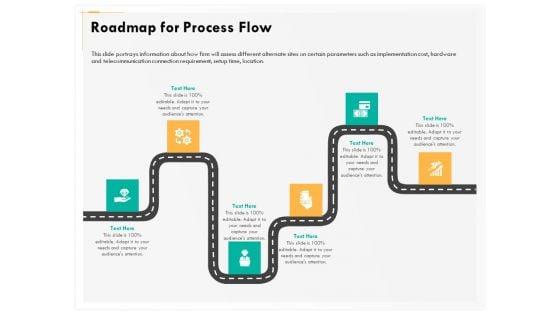
Presenting this set of slides with name computer security incident handling roadmap for process flow ppt professional slide portrait pdf. This is a six stage process. The stages in this process are roadmap, process flow. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
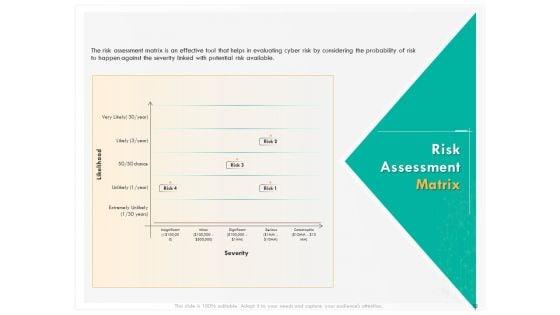
Presenting this set of slides with name computer security incident handling risk assessment matrix ppt show design ideas pdf. This is a four stage process. The stages in this process are minor, significant, serious, catastrophic, insignificant. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
Presenting this set of slides with name computer security incident handling our team ppt model files pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling our mission ppt styles slides pdf. This is a three stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling financial ppt portfolio pictures pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling dashboard ppt model introduction pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
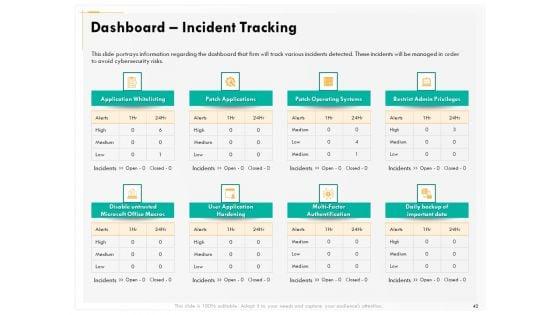
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
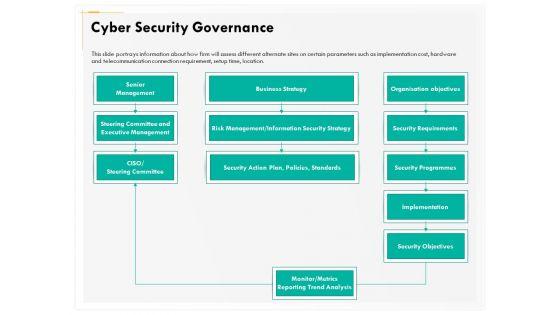
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
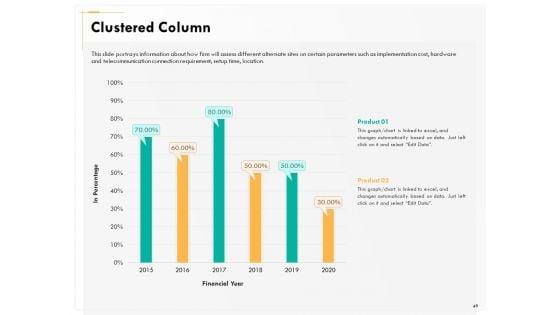
Presenting this set of slides with name computer security incident handling clustered column ppt show styles pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
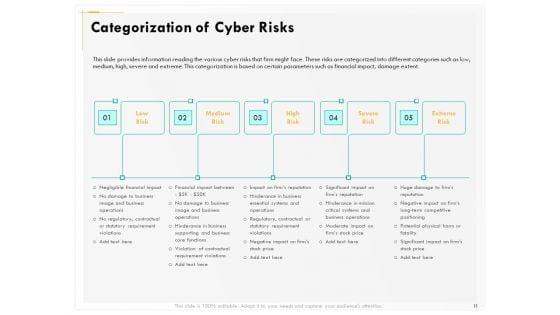
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling business impact assessment ppt infographics rules pdf. The topics discussed in these slides are strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling 30 60 90 days plan ppt file templates pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling dashboard cyber risk management download pdf. The topics discussed in these slides are risk rating breakdown, risk heat map, action plan breakdown, risk analysis progress, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
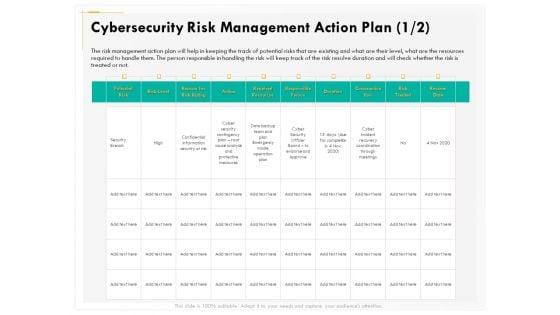
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
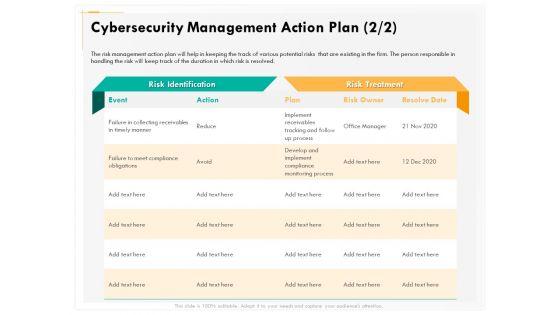
Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
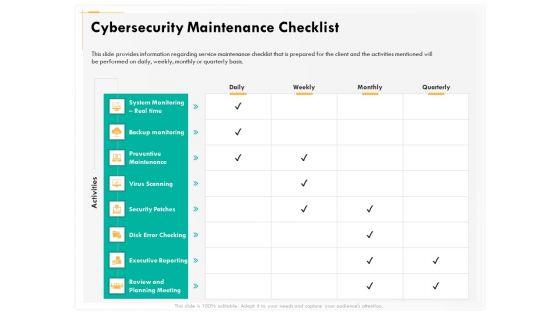
Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity contingency plan business impact analysis rules pdf. The topics discussed in these slides are business processes, vital resources, impact, recovery priorities, max allowable outage time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
Presenting this set of slides with name computer security incident handling budget for effective cybersecurity management clipart pdf. The topics discussed in these slides are functional area, software, implement duration, cost of implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
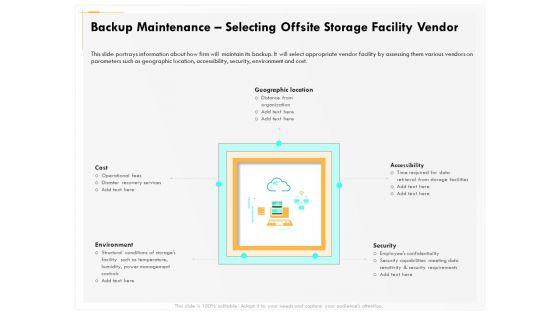
Presenting this set of slides with name computer security incident handling backup maintenance selecting offsite storage facility vendor guidelines pdf. The topics discussed in these slides are geographic location, accessibility, security, cost, environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling backup maintenance recovery budget planning professional pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, testing costs, supply costs, labor or contractor costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Slide 1 of 2
Presenting this set of slides with name computer security incident handling backup maintenance developing alternate sites slides pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
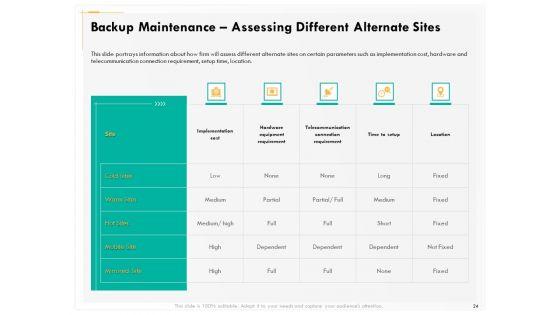
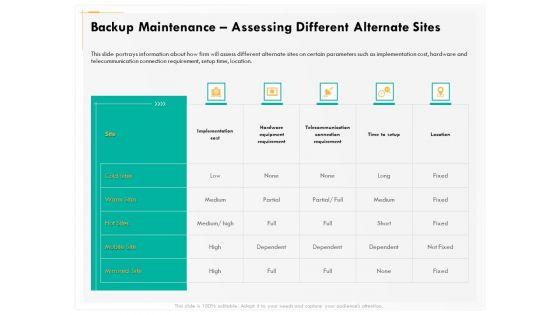
Presenting this set of slides with name computer security incident handling backup maintenance assessing different alternate sites infographics pdf. The topics discussed in these slides are implementation cost, hardware equipment requirement, telecommunication connection requirement, time to setup, location. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
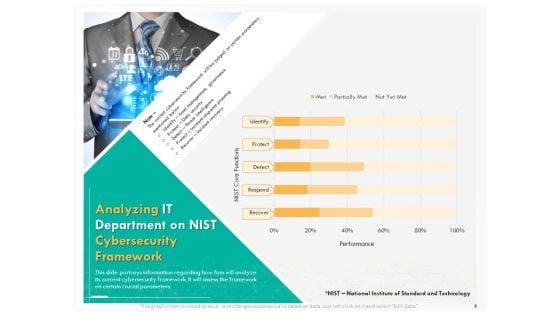
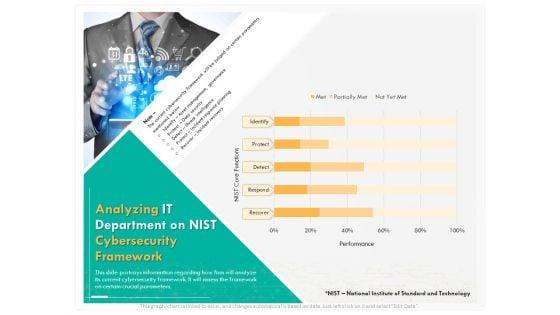
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
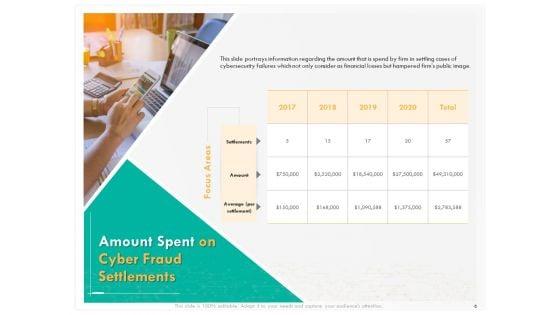
Presenting this set of slides with name computer security incident handling amount spent on cyber fraud settlements portrait pdf. The topics discussed in these slides are settlements, amount, average. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling agenda for cybersecurity management slides pdf. The topics discussed in these slides are determining roles and responsibilities of senior management and executives who are responsible in risk management, presenting optimize cybersecurity risk framework to senior management and executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling agenda for cybersecurity incident management template pdf. The topics discussed in these slides are department, priorities, maximum allowable downtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.








Slide 1 of 9
Incident Response Techniques Deployement Cyber Security Incident Handling Checklist Infographics PDF
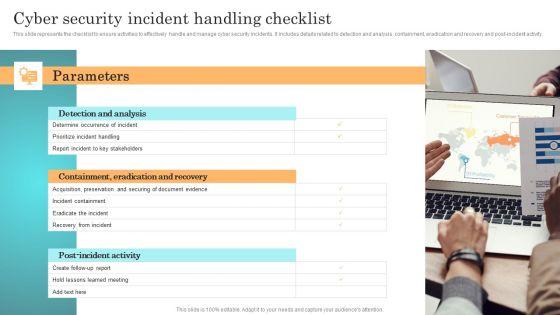
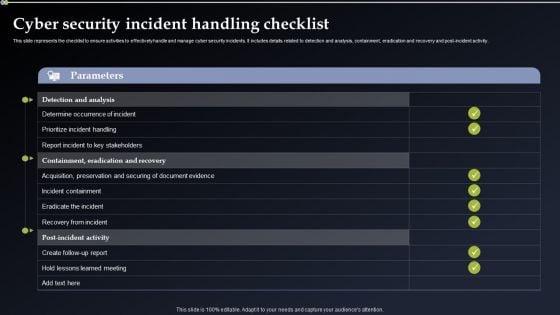
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF









Slide 1 of 9
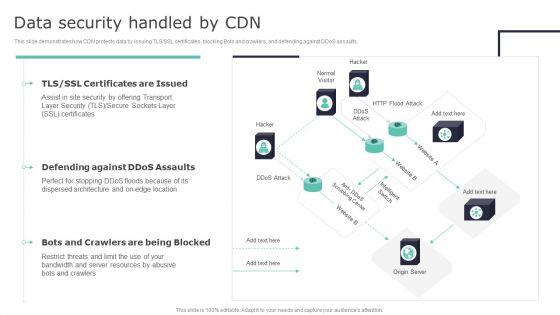
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.








Slide 1 of 9
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.








Slide 1 of 9
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates








Slide 1 of 9
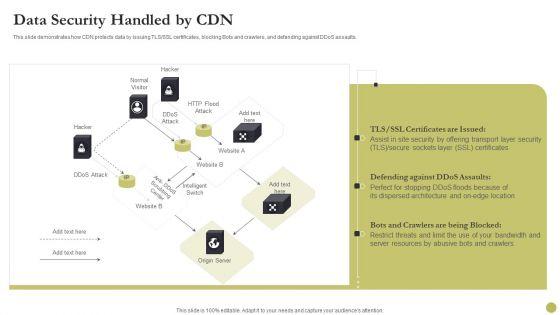
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.









Slide 1 of 9
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
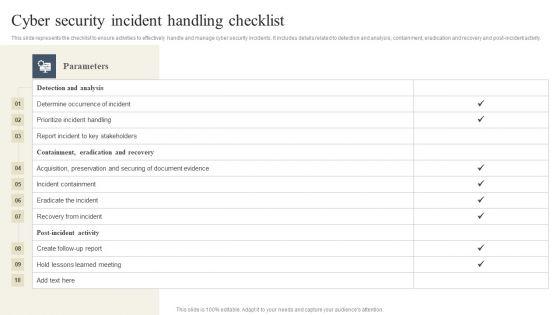
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. This Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today








Slide 1 of 9
CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.









Slide 1 of 9
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
56 Item(s)
