AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Threat response PowerPoint Presentation Templates and Google Slides
59 Item(s)

























Slide 1 of 47
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty seven slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Slide 1 of 2
Following slide illustrate KPI dashboard that can be used by organizations to track real time incident data. Kpis covered are number of tickets, average resolution time per customer, incidents registered per month. Presenting IT Threats Response Playbook Real Time Incident Management Dashboard Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Resolved Tickets, Average Resolution, Incidents Registered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
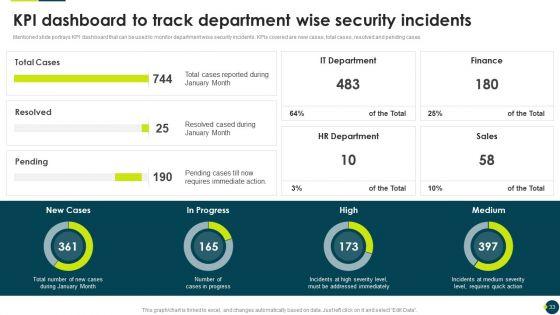
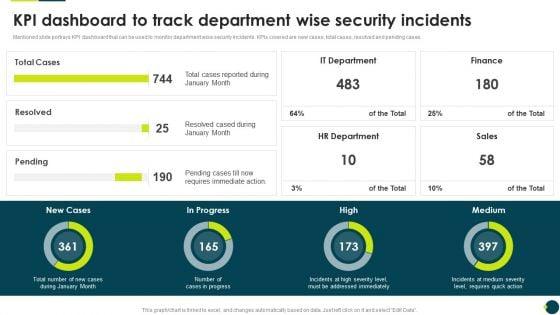
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a threat management at workplace roles and responsibilities to ensure work environment sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, internal investigations unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
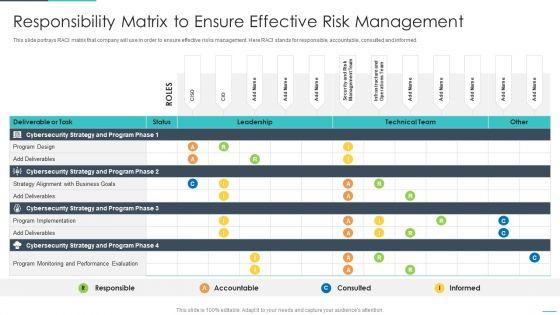
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative handling cyber threats digital era responsibility matrix to ensure effective ppt show inspiration pdf bundle. Topics like responsibility matrix to ensure effective risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative handling cyber threats digital era flow diagram of incident response process ppt infographics inspiration pdf bundle. Topics like preparatory, remediate eradicate, analyse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide provides the glimpse about the roles and responsibilities for participants involved in issue and escalation process such as project staff members, issue manager, project manager, project director and executive steering committee. Presenting how to intensify project threats participants roles and responsibilities for issue template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like project staff members, issue manager, project manager, project director, executive steering committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
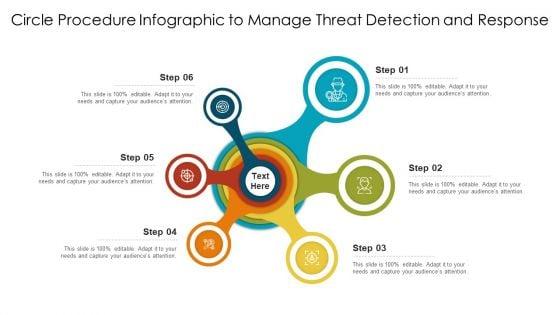
Persuade your audience using this circle procedure infographic to manage threat detection and response ppt styles sample pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure infographic to manage threat detection and response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Slide 1 of 2
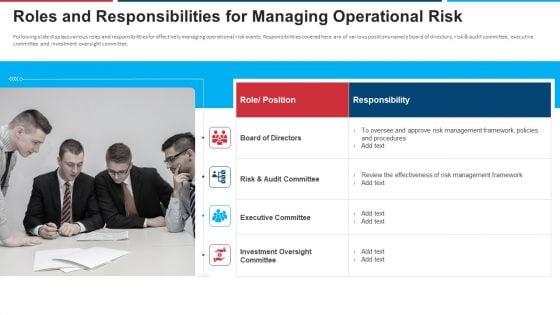
Following slide displays various roles and responsibilities for effectively managing operational risk events. Responsibilities covered here are of various positions namely board of directors, risk and audit committee, executive committee and investment oversight committee. This is a mitigation strategies for operational threat roles and responsibilities for managing operational risk ppt ideas gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like board of directors, risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
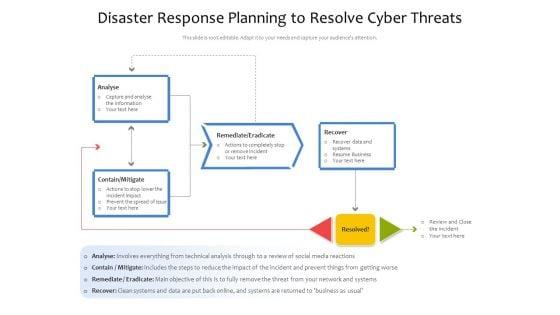
Showcasing this set of slides titled disaster response planning to resolve cyber threats ppt powerpoint presentation file gallery pdf. The topics addressed in these templates are analyse, remediate eradicate, contain mitigate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
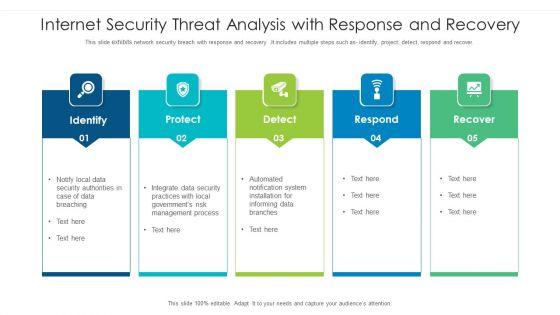
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Slide 1 of 2
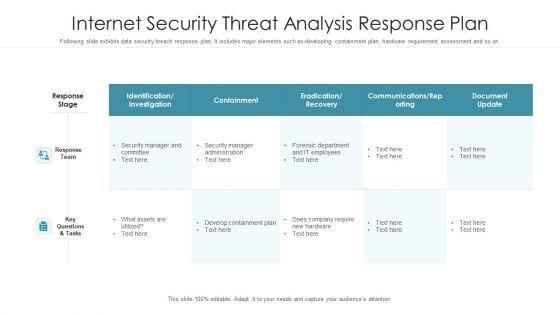
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
Presenting this set of slides with name threat detection response ppt powerpoint presentation gallery good cpb. This is an editable Powerpoint four stages graphic that deals with topics like threat detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Slide 1 of 2
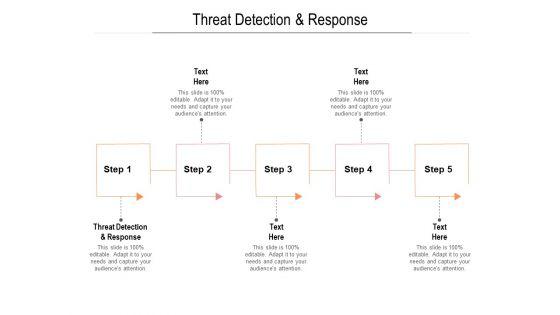
Presenting this set of slides with name threat detection and response ppt powerpoint presentation pictures information cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like threat detection and response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.








Slide 1 of 9
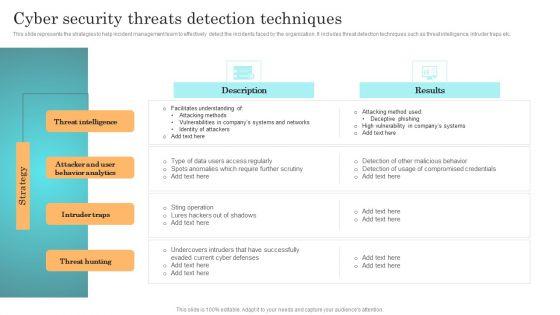
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.









Slide 1 of 9
This slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Responsible Technology Playbook Key Principles Associated With Agile Threat Modelling Topics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.









Slide 1 of 9
This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. This Responsible Technology Playbook Checklist To Manage Agile Threat Modelling Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Responsible Technology Playbook Checklist To Manage Agile Threat Modelling Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.








Slide 1 of 9
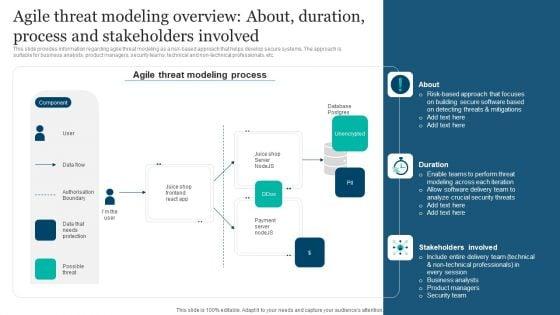
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.









Slide 1 of 9
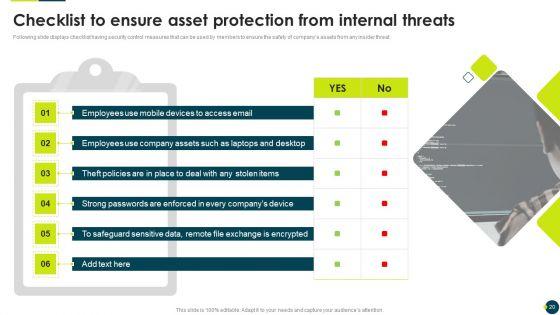
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.









Slide 1 of 9
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.









Slide 1 of 9
This slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting Cyber Data Security Threats Management Response Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prepare Incident, Response Plan, Detection Data Compromises, Eradicate Network Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
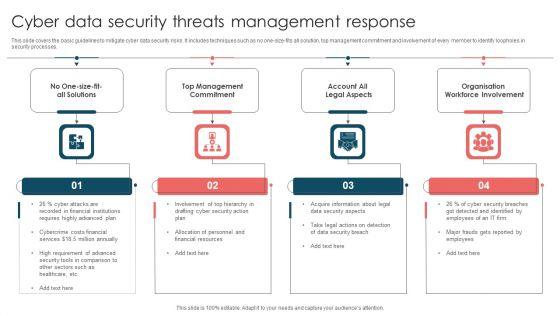
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
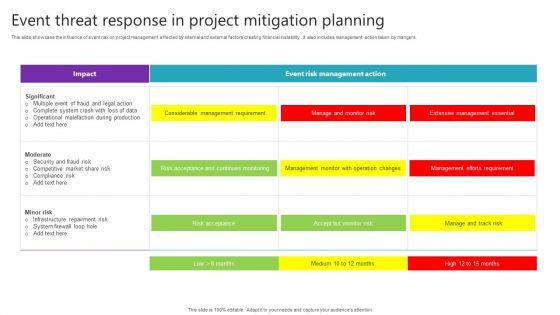
This slide showcase the influence of event risk on project management affected by internal and external factors creating financial instability . It also includes management action taken by mangers. Showcasing this set of slides titled Event Threat Response In Project Mitigation Planning Pictures PDF. The topics addressed in these templates are Considerable Management Requirement, Risk Acceptance, Risk Acceptance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.








Slide 1 of 9
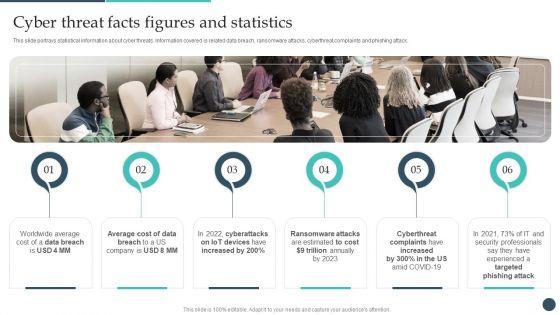
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.








Slide 1 of 9
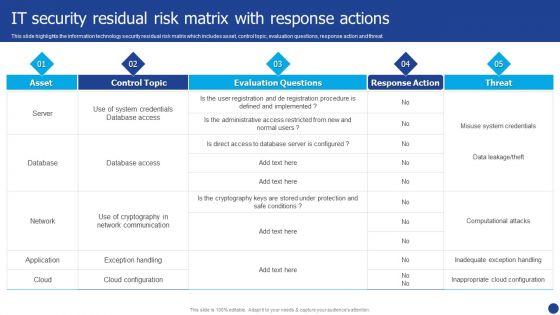
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.








Slide 1 of 9
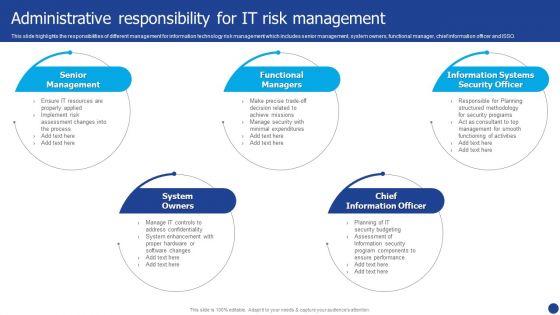
This slide highlights the responsibilities of different management for information technology risk management which includes senior management, system owners, functional manager, chief information officer and ISSO. This is a Information Technology Threat Mitigation Methods Administrative Responsibility For IT Risk Management Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Managers, Chief Information Officer, System Owners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.









Slide 1 of 9
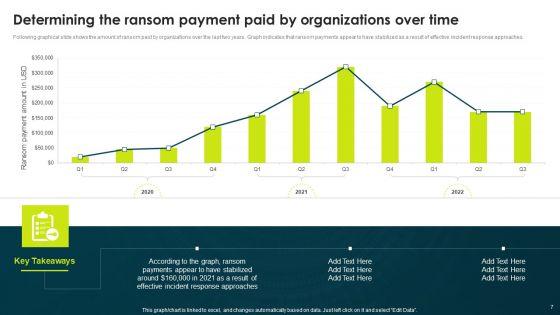
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.









Slide 1 of 9
Presenting Table Of Contents For IT Threats Response Playbook Slide Structure PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Responsibilities Incident, Asset Protection, Risk Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.









Slide 1 of 9
This is a IT Threats Response Playbook SWOT Analysis Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.








Slide 1 of 9
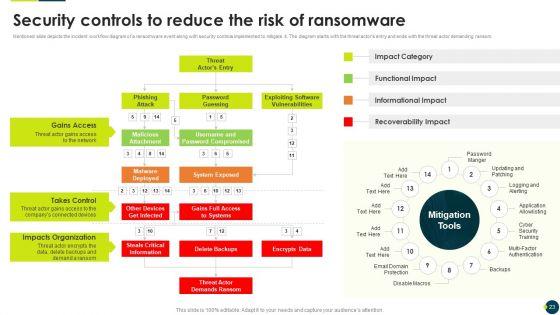
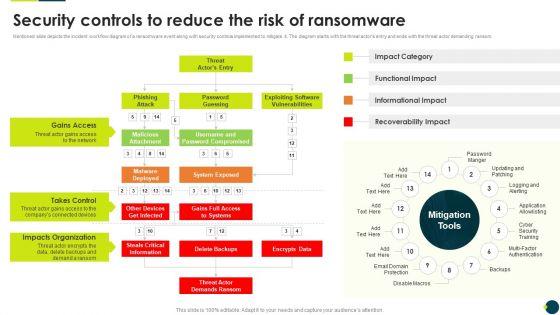
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
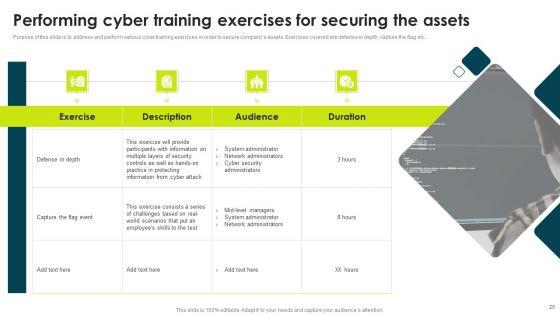
IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.








Slide 1 of 9
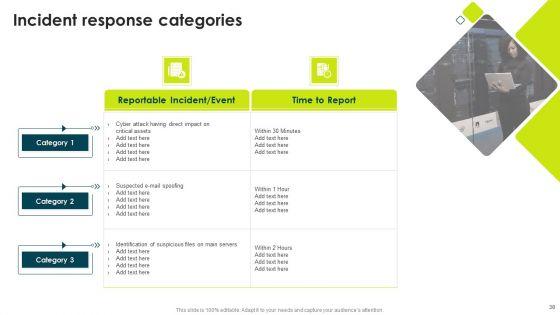
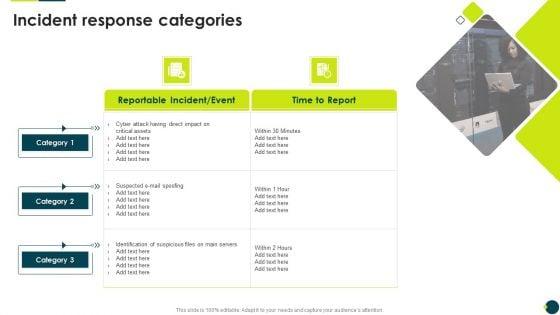
Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Incident Response Categories Rules PDF. Use them to share invaluable insights on Identification Suspicious, Direct Impact, Time To Report and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.








Slide 1 of 9
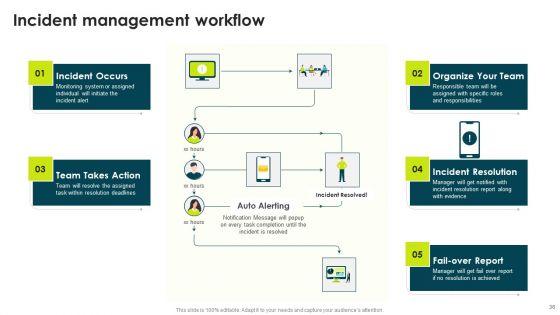
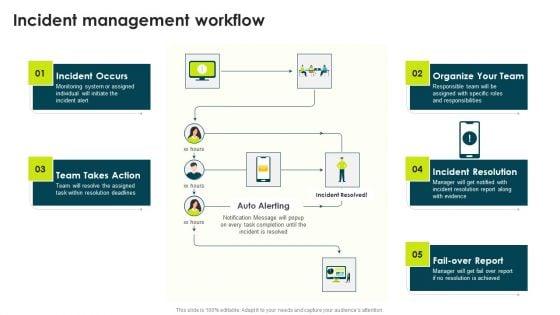
Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Incident Management Workflow Themes PDF bundle. Topics like Incident Occurs, Incident Resolution, Resolution Achieved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.








Slide 1 of 9
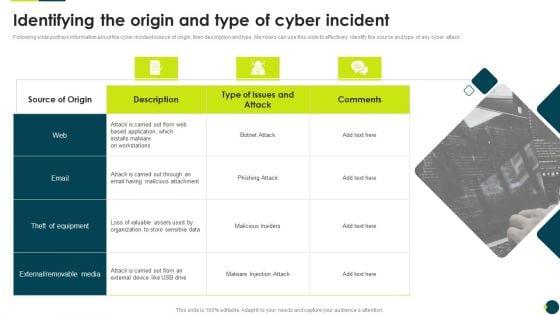
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.








Slide 1 of 9
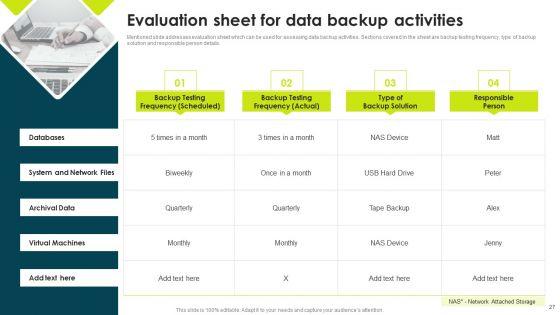
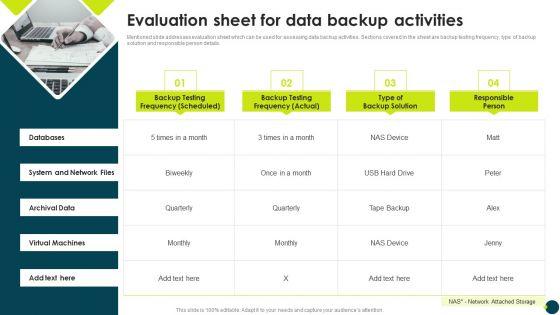
Mentioned slide addresses evaluation sheet which can be used for assessing data backup activities. Sections covered in the sheet are backup testing frequency, type of backup solution and responsible person details. Presenting IT Threats Response Playbook Evaluation Sheet For Data Backup Activities Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Archival Data, Virtual Machines, System And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.








Slide 1 of 9
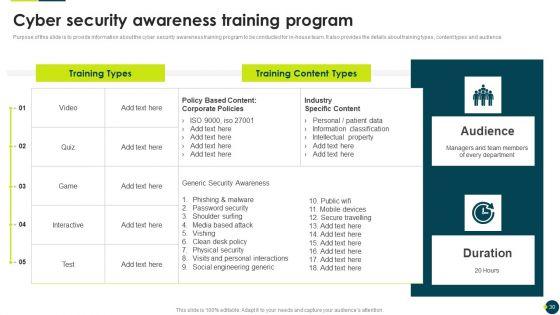
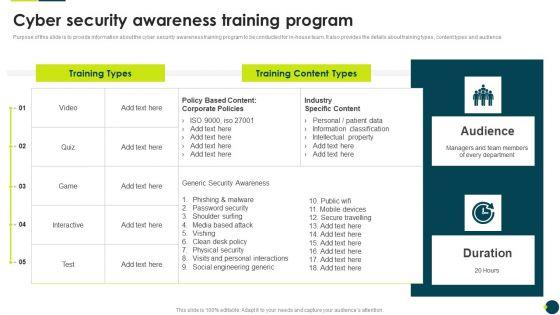
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF bundle. Topics like Conference Meeting, Incident Information, Various Departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.








Slide 1 of 9
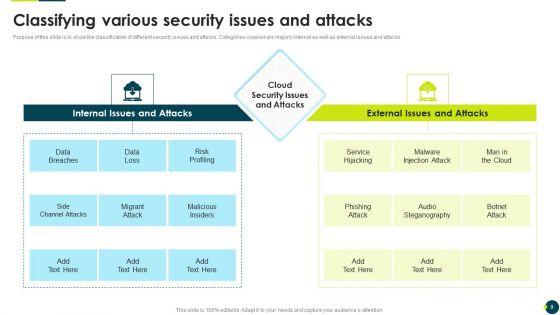
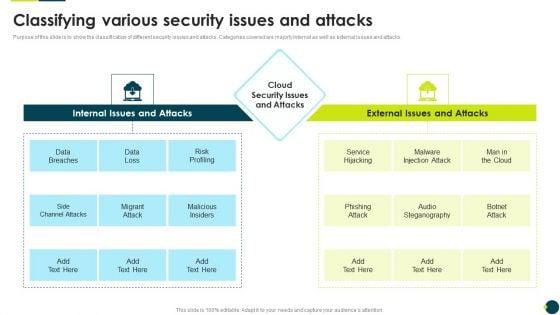
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.








Slide 1 of 9
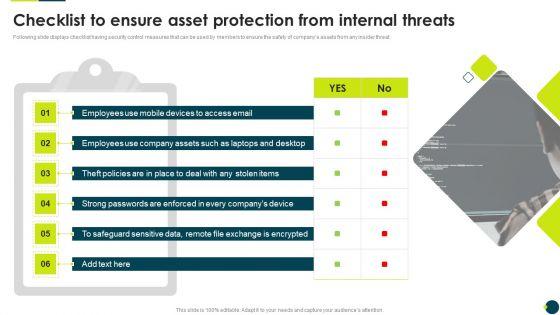
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.








Slide 1 of 9
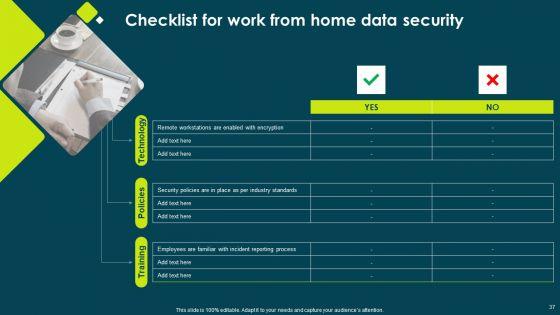
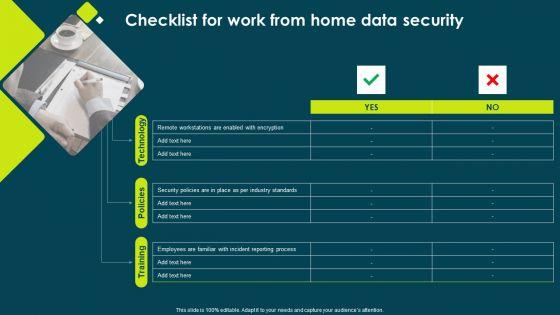
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
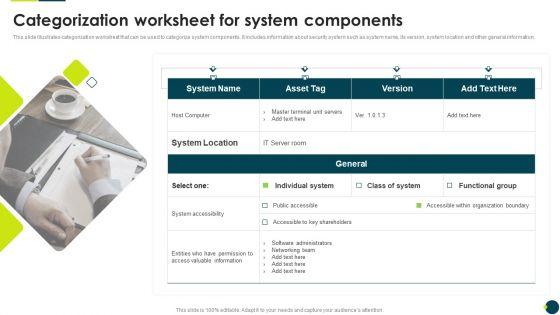








Slide 1 of 9
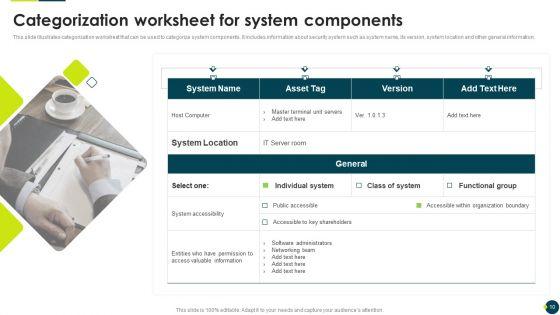
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information.Presenting IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like System Accessibility, Valuable Information, Organization Boundary. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.








Slide 1 of 9
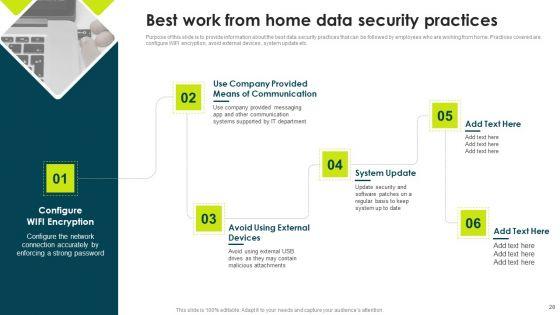
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
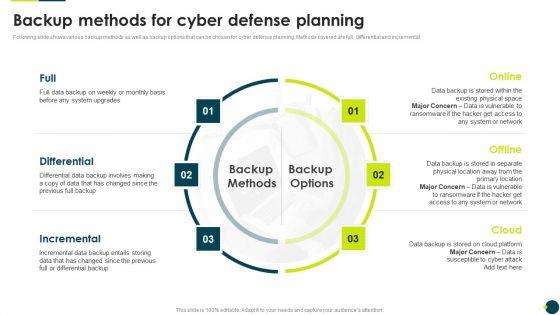








Slide 1 of 9
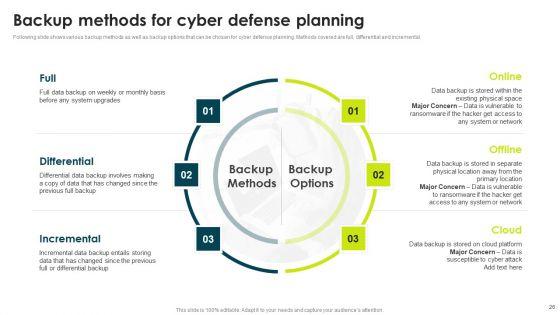
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.Presenting IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Differential, Incremental, Differential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.This is a IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Servers, Desktop Systems, Onsite Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
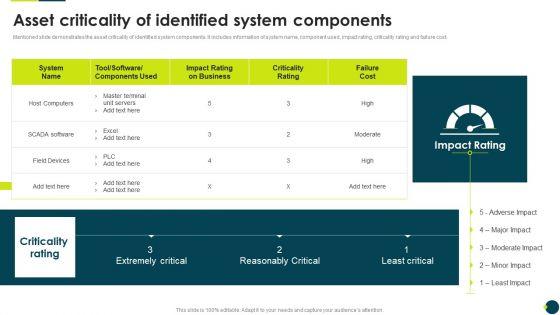








Slide 1 of 9
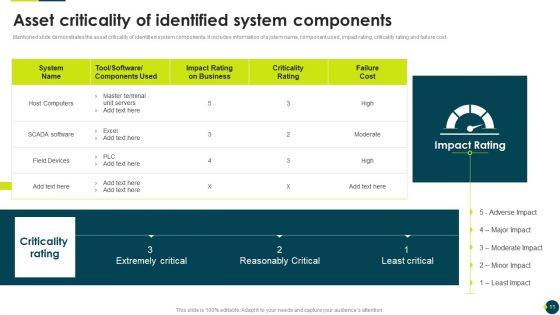
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.









Slide 1 of 9
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.









Slide 1 of 9
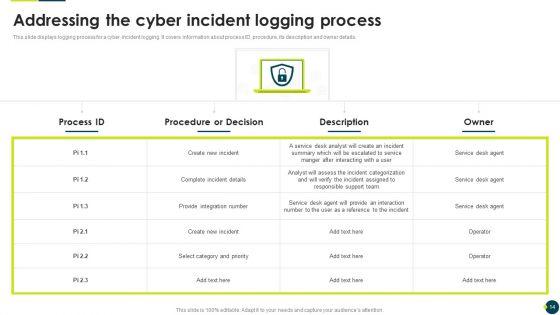
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.








Slide 1 of 9
Download our innovative and attention grabbing Icons Slide For IT Threats Response Playbook Download PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.









Slide 1 of 9
This slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Retrieve professionally designed Key Principles Associated With Agile Threat Responsible Tech Guide To Manage Download Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc.









Slide 1 of 9
This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Checklist To Manage Agile Threat Modelling Responsible Tech Guide To Manage Elements Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc.
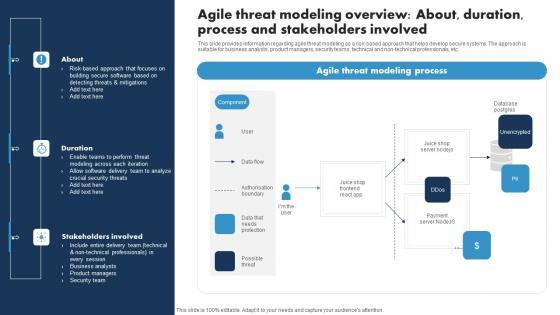








Slide 1 of 9
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
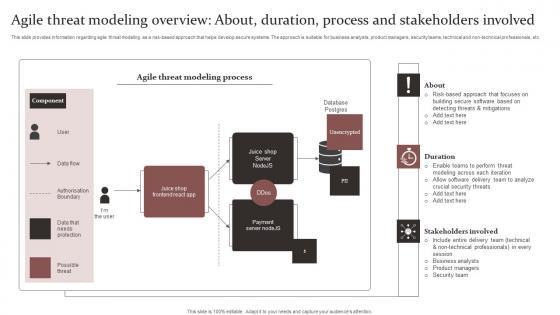








Slide 1 of 9
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Create an editable Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.
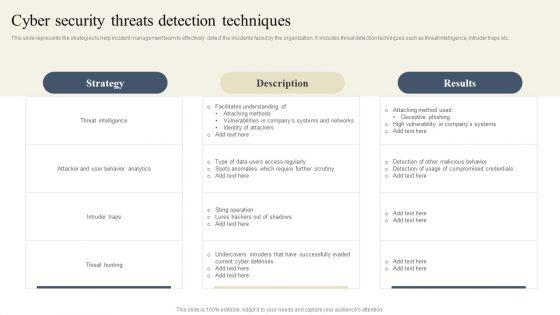








Slide 1 of 9
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
59 Item(s)

