AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Traditional It PowerPoint Presentation Templates and Google Slides
13 Item(s)

Slide 1 of 3
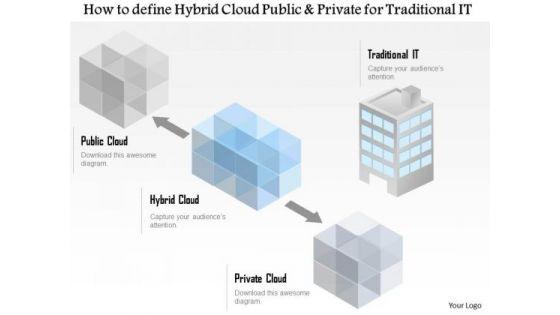
This technology diagram has been designed with graphic of hybrid cloud with user connectivity. This diagram slide depicts the concept of cloud technology for private and public use. Download this diagram for your cloud technology related presentations.



Slide 1 of 3
This image slide displays the concept of hybrid cloud. This image slide has been designed with graphic of computer servers, service tools, hybrid cloud, private and public cloud. Use this image slide, in your presentations to express views on hybrid networking, communication and technology. This image slide will enhance the quality of your presentations.


Slide 1 of 2
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
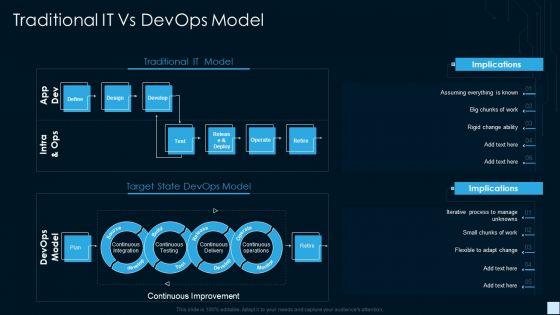
Deliver an awe inspiring pitch with this creative devops strategy development report it traditional it vs devops model ideas pdf bundle. Topics like continuous integration, continuous testing, continuous delivery, continuous operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide covers the difference of DevOps from traditional IT based on Production Team, load checking crashes, Operations Staff, , data center sites, and storage needs Deliver an awe inspiring pitch with this creative devops for information technology how is devops different from traditional it microsoft pdf bundle. Topics like control strategy, technology performance management, operations team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative difference between cloud security solutions and traditional it solutions cloud computing security it ppt ideas example topics pdf bundle. Topics like cloud security, traditional it security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
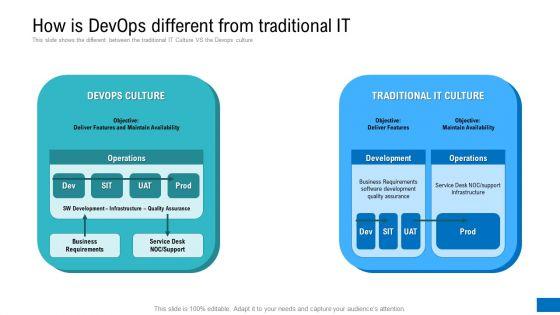
Slide 1 of 2
This is a how is devops different from traditional it ppt gallery design inspiration pdf. template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business requirements, operations, traditional it culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.








Slide 1 of 9
Showcasing this set of slides titled Icon For Comparative Analysis Of Cloud And Traditional Computing It Security Rules PDF. The topics addressed in these templates are Icon Comparative Analysis Cloud, Traditional Computing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.









Slide 1 of 9
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
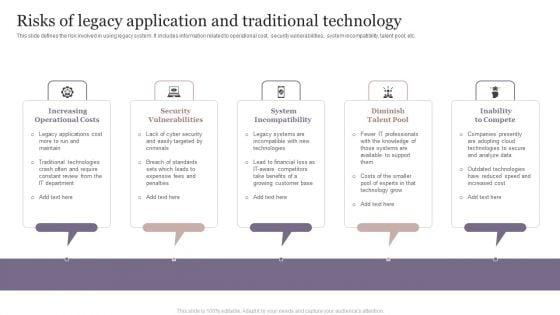
This slide defines the risk involved in using legacy system. It includes information related to operational cost, security vulnerabilities, system incompatibility, talent pool, etc. Persuade your audience using this Risks Of Legacy Application And Traditional Technology Mockup PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Increasing Operational Costs, Security Vulnerabilities, System Incompatibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
Mentioned slide showcases working of blockchain technology in the banking sector, which can be used to store large amount of data in the form of blocks. The process begins with requesting a transaction, storing in P2P, validation and verification of data, creating new blocks, adding blocks to existing chain etc. Pitch your topic with ease and precision using this Impact Of Shifting From Traditional To Technology Based Blockchain And Distributed Ledger Technology Model Rules PDF. This layout presents information on Traditional Model, Blockchain Based Model, Propensity For Fraud. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.









Slide 1 of 9
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses.Presenting Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Reduced Infrastructure, Resource Utilization, Diminished Opportunity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration. Presenting this PowerPoint presentation, titled Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration.
13 Item(s)
