AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
User Activity PowerPoint Presentation Templates and Google Slides
5 Item(s)


Slide 1 of 2
This slide shows information technology dashboard depicting user activity which can be referred by IT managers to track leads and make decisions. It includes information about sessions, signups, position, size, industry, customers, quality leads, etc. Pitch your topic with ease and precision using this IT Performance Dashboard Depicting User Activity Inspiration PDF. This layout presents information on Monthly Recurring Revenue, Average Revenue Per, Account Quality Leads, Customers Position Sessions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Slide 1 of 2
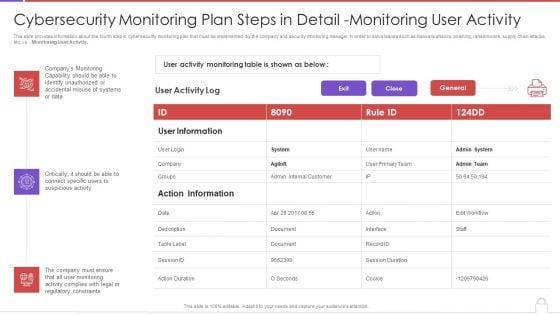
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
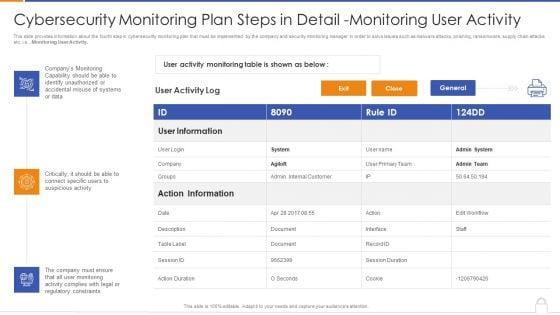
Slide 1 of 2
Presenting cybersecurity monitoring plan steps in detail monitoring user activity themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like accidental misuse of systems, regulatory constraints, suspicious activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
Persuade your audience using this social media user activities list vector icon brochure pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including social media user activities list vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
5 Item(s)
