AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Vulnerability summary PowerPoint Presentation Templates and Google Slides
15 Item(s)


Slide 1 of 2
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration hybrid managed siem model summary pdf bundle. Topics like correlation, aggregation, collection, event sources, our company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
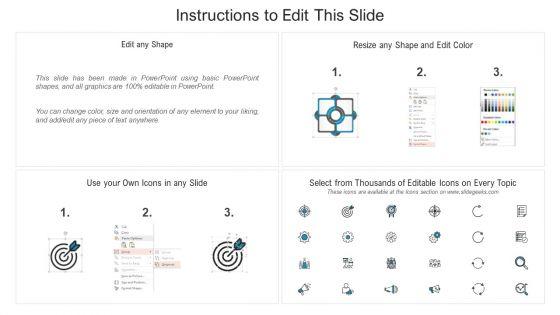
This is a enhancing cyber safety with vulnerability administration how siem works summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like correlation, behavior analytics, normalization, taxonomy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
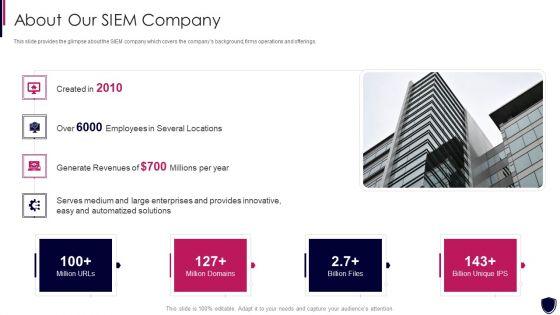
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. Presenting enhancing cyber safety with vulnerability administration about our siem company summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like about our siem company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
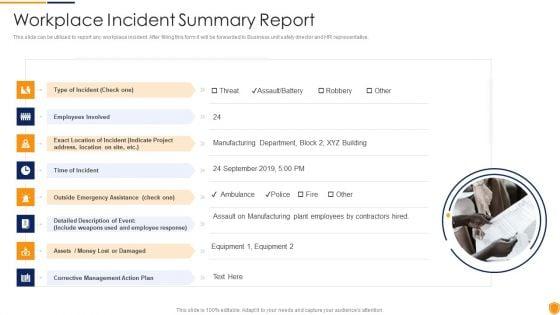
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a mitigating cybersecurity threats and vulnerabilities workplace incident summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like type of incident, time of incident, corrective management action plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
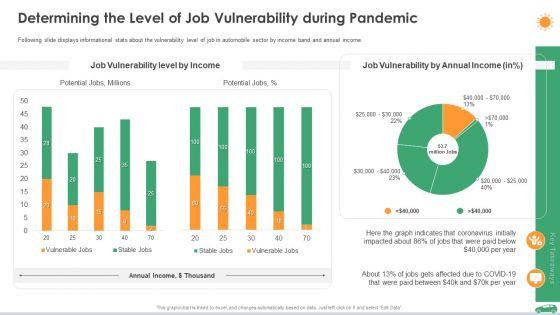
Following slide displays informational stats about the vulnerability level of job in automobile sector by income band and annual income. Deliver an awe inspiring pitch with this creative determining the level of job vulnerability during pandemic ppt slides summary pdf bundle. Topics like determining the level of job vulnerability during pandemic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
Presenting company vulnerability administration determine the state of the program summary pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like review the strategy with stakeholders, determine what each stakeholder need, determine what the current process provides. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
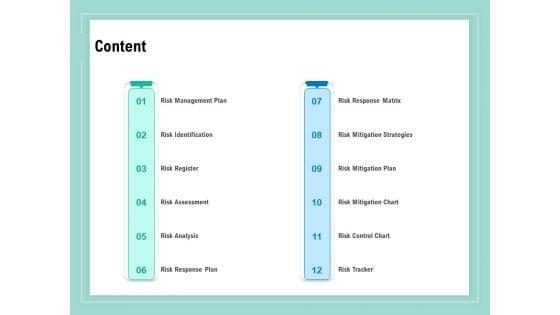
Presenting this set of slides with name vulnerability assessment methodology content ppt summary infographics pdf. The topics discussed in these slides are risk identification, risk register, risk assessment, risk analysis, risk mitigation plan, risk mitigation chart, risk tracker, risk management plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
Presenting this set of slides with name vulnerability assessment methodology circular diagram ppt icon summary pdf. This is a six stage process. The stages in this process are circular diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
Presenting this set of slides with name vulnerability management tracking system ppt powerpoint presentation summary images cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability management tracking system to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.








Slide 1 of 9
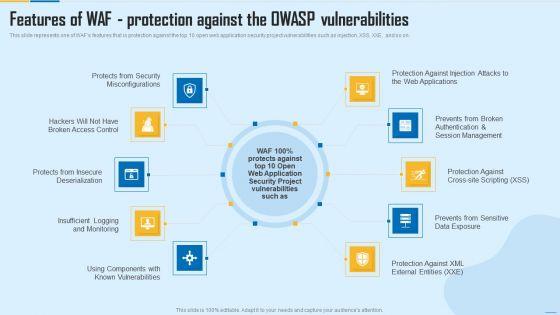
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.









Slide 1 of 9
The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management. Showcasing this set of slides titled Key Steps Involved In Vulnerability Handling Process Flowchart Summary Pdf. The topics addressed in these templates are Perform Vulnerability Scan, Measure Vulnerability Risk, Prioritize Address Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management.









Slide 1 of 9
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.









Slide 1 of 9
This slide showcases customer onboarding framework through know your customer KYC approach. It provides information about assess, implement, validation, testing, monitoring, control, risk rating, risk score, enhanced due diligence EDD, etc. The Customer Onboarding Framework Minimizing Customer Transaction Vulnerabilities Summary Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases customer onboarding framework through know your customer KYC approach. It provides information about assess, implement, validation, testing, monitoring, control, risk rating, risk score, enhanced due diligence EDD, etc.








Slide 1 of 9
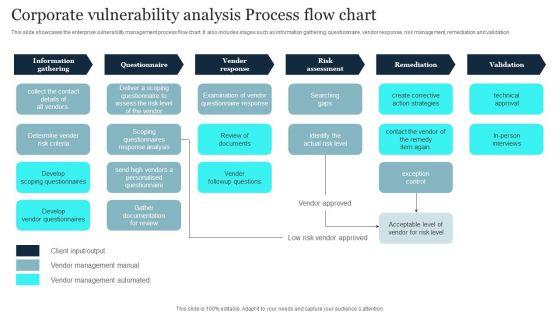
This slide showcases the enterprise vulnerability management process flow chart. It also includes stages such as information gathering, questionnaire, vendor response, risk management, remediation and validation. Pitch your topic with ease and precision using this Corporate Vulnerability Analysis Process Flow Chart Summary PDF. This layout presents information on Vender Response, Risk Assessment, Information Gathering. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
15 Item(s)
