AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
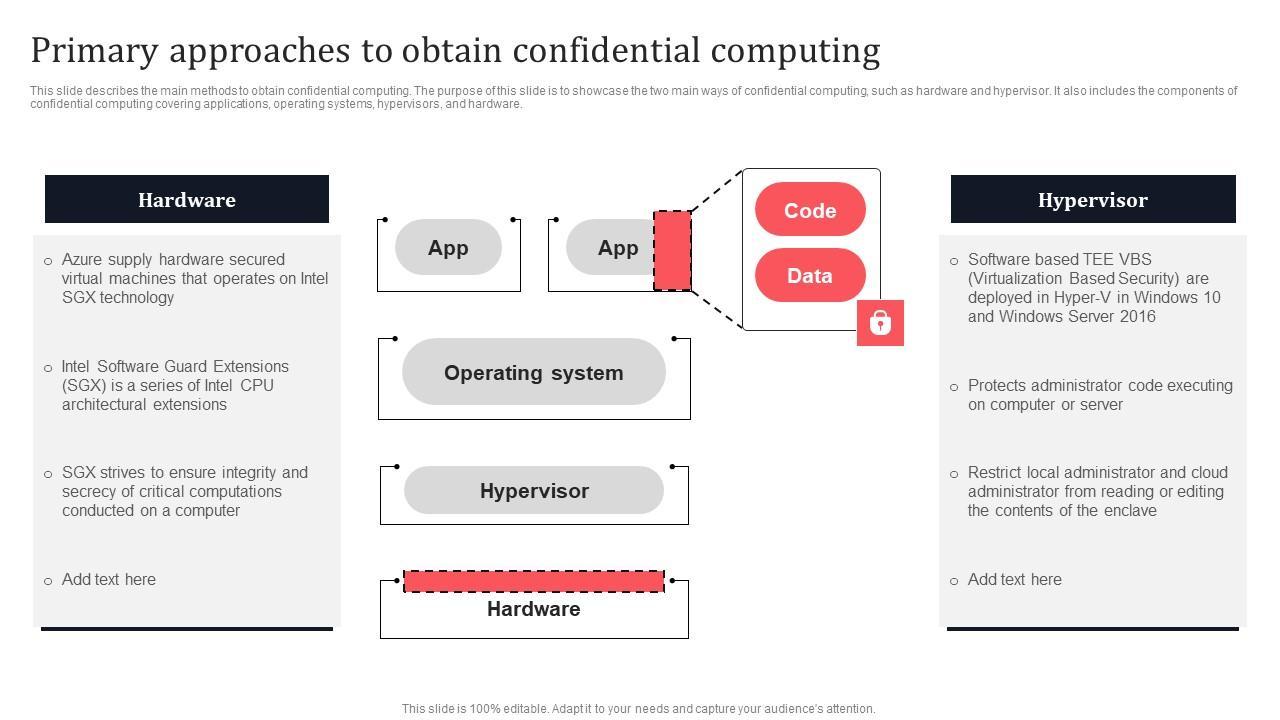
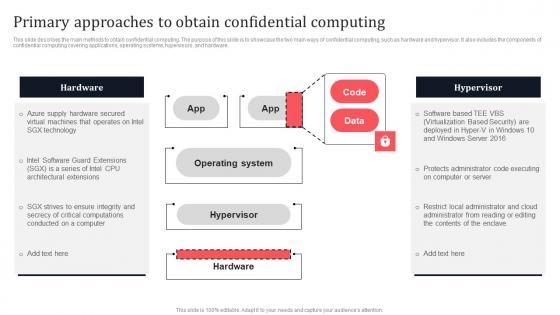
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
Features of these PowerPoint presentation slides:
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf with all 9 slides:
Use our Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Ratings and Reviews
4.5
- ★51
- ★43
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by O'Ryan Edwards
January 24, 2024
Innovative and Colorful designs.by Craig Moreno
January 24, 2024
Great designs, really helpful.by Byrne Cruz
January 23, 2024
Amazing product with appealing content and design.by Chase Howard
January 23, 2024
The Designed Graphic are very professional and classic.
View per page:
10