AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
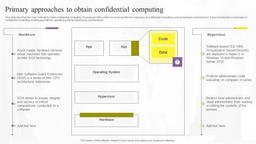
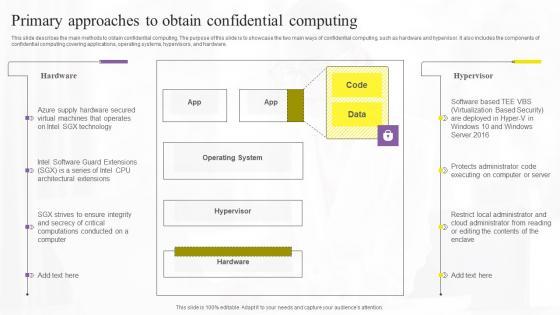
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
Features of these PowerPoint presentation slides:
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf with all 9 slides:
Use our Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Ratings and Reviews
5
- ★53
- ★41
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Rhys Moore
February 20, 2024
Colors used are bright and distinctive.by Collin Gonzales
February 20, 2024
Very unique, user-friendly presentation interface.by Del Holmes
February 20, 2024
Easily Editable.by George Miller
February 19, 2024
Very unique, user-friendly presentation interface.
View per page:
10