AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
3
Welcome to our assortment of Most Popular PowerPoint templates that are designed to assist you show your creative side and innovation your sphere. Planning and Innovation are two of the most important aspects of an emerging business. This section includes the designs that you require in your day to day presentations. Every day there are hundreds or even thousands of PowerPoint presentations created on various subjects such as business, medical, sales and marketing.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 174 Item(s)
Page








Slide 1 of 9
Persuade your audience using this Three Lines Of Defense Border Model Icon Introduction PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Three Lines, Defense Border, Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Persuade your audience using this Lines Of Defense Border In Healthcare Industry Icon Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Lines Defense Border, Healthcare, Industry. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Presenting Defense Border Lines For Risk Management And Governance Icon Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Defense Border, Lines Risk Management, Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.









Slide 1 of 9
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Find a pre-designed and impeccable Other ZTNA Architecture Deployment Approaches Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.








Slide 1 of 9
Presenting Bank Security Breached Icon Of Identity Fraud Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Bank Security, Breached Icon, Identity Fraud. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
Persuade your audience using this Security Operations Cyber Security Protection Icon Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Protection Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Persuade your audience using this Security Operations Cyber Security Icon With Lock Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Icon With Lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Persuade your audience using this Cyber Security Cases Action Plan Response Team Icon Ppt PowerPoint Presentation Icon Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Cases Action Plan, Response Team, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Presenting Cyber Security Cases Action Plan Response Analysis Icon Ppt PowerPoint Presentation Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security Cases, Action Plan Response, Analysis Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
Presenting Security Problem Management Icon To Mitigate Risk Ppt Ideas Outfit PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Problem, Management, Icon To Mitigate, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
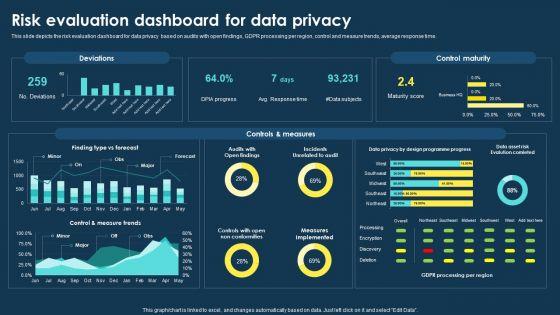
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Explore a selection of the finest Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.








Slide 1 of 9
Persuade your audience using this IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Managing, Cyber Security, Incident Response, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
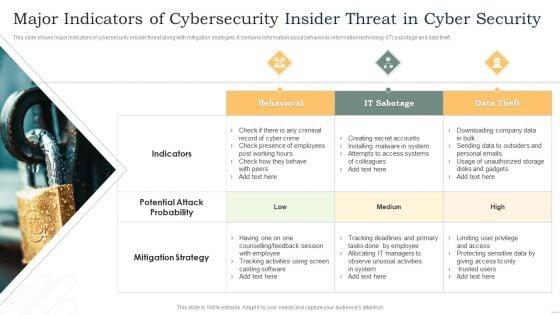
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Security Officer Service Company Profile Mission Vision And Core Values Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Core Values, Integrity, Commitment, Passion, Team work. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Officer Service Company Profile Case Study Ppt PowerPoint Presentation File Slideshow PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.









Slide 1 of 9
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Safety Escort Service, Executive Protection, Special Event Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.








Slide 1 of 9
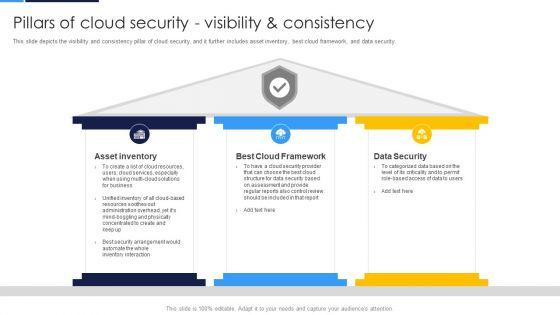
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Presenting Survey Insights On Cyber War Attacks Icons Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Survey Insights ,Cyber War, Attacks Icons This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Presenting Icon For Hotel Safety And Cyber Security Icon Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Hotel, Safety Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
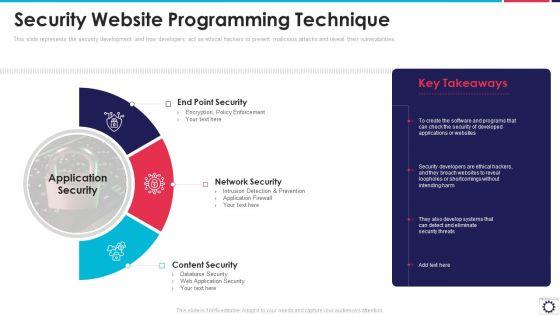
Slide 1 of 2
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
Presenting icon for information and cyber security risk management themes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for information and cyber security risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
Persuade your audience using this organizational manager achieving career growth with key for success diagrams pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including organizational manager achieving career growth with key for success. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Presenting manager with key solution for achieving business target themes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including manager with key solution for achieving business target. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Persuade your audience using this manager with key for generating profit in business graphics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including manager with key for generating profit in business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Persuade your audience using this manager instructing to drive key innovations in business download pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including manager instructing to drive key innovations in business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Slide 1 of 2
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
Persuade your audience using this scanning and storing virtual identity for face recognition icon designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including scanning and storing virtual identity for face recognition icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Slide 1 of 2
Presenting businessman using key for accessing virtual identity designs pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including businessman using key for accessing virtual identity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this authorized key for unlocking virtual identity icon slides pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authorized key for unlocking virtual identity icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Slide 1 of 2
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. This is a developing firm security strategy plan elevating brand protection strategy mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overt security features, covert security features, serialization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
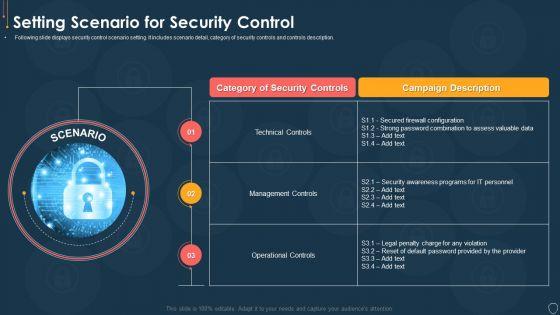
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Persuade your audience using this safety shield for database protection vector icon ppt powerpoint presentation file portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including safety shield for database protection vector icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Presenting secure sensitive information through communication software ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including secure sensitive information through communication software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this enter password for security vector icon ppt powerpoint presentation file professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including enter password for security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Persuade your audience using this person protecting data by using network access control ppt powerpoint presentation gallery infographics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including person protecting data by using network access control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting locked folder for confidential information vector icon ppt icon layout pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including locked folder for confidential information vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting vector showing security and warranty of data quality assurance icon ppt powerpoint presentation gallery example pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector showing security and warranty of data quality assurance icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this vector showing data quality verification icon ppt powerpoint presentation file background pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing data quality verification icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting data quality assurance and safety vector icon ppt powerpoint presentation gallery background image pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data quality assurance and safety vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Presenting circuit sign for data safety and security vector icon ppt pictures brochure pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including circuit sign for data safety and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Presenting company vulnerability administration need for vulnerability management introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detective controls, responsive controls, vulnerability management is a standard process, implementing a vulnerability management program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
Persuade your audience using this security access system on mobile with lock icon ppt powerpoint presentation portfolio design inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security access system on mobile with lock icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Persuade your audience using this office door with security access panel image ppt powerpoint presentation icon topics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including office door with security access panel image. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Presenting man opening door with security system on smart phone ppt powerpoint presentation model grid pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including man opening door with security system on smart phone. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this locked laptop for security vector icon ppt powerpoint presentation infographics inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including locked laptop for security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting biometric device for security access system icon ppt powerpoint presentation ideas picture pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including biometric device for security access system icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Persuade your audience using this user profile security vector icon ppt powerpoint presentation icon example file pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including user profile security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting user account privacy policy vector icon ppt powerpoint presentation gallery inspiration pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including user account privacy policy vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this security from unauthorized surveillance vector icon ppt powerpoint presentation gallery deck pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security from unauthorized surveillance vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting protecting pc security from hacker vector icon ppt powerpoint presentation file infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protecting pc security from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this password protection on laptop for security vector icon ppt powerpoint presentation gallery slide download pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including password protection on laptop for security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
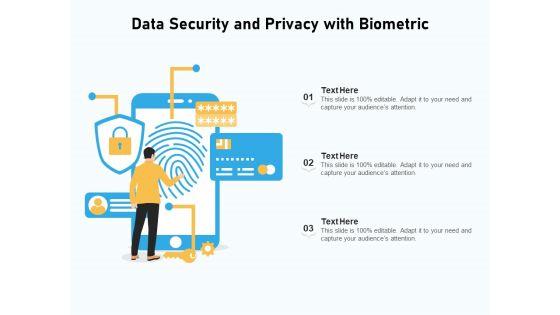
Presenting data security and privacy with biometric ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data security and privacy with biometric. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Persuade your audience using this data folder security vector icon ppt powerpoint presentation file rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data folder security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 174 Item(s)
Page
