10 List

Zero Trust Model Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. Explore a selection of the finest Zero Trust Model Key Points To Choose Zero Trust Solution here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Key Points To Choose Zero Trust Solution to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
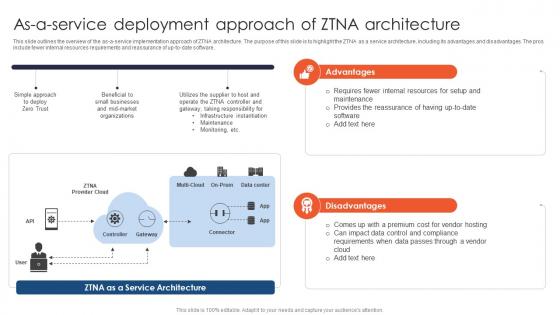
Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
Big Real Time Data Streaming Use Cases Ppt Icon Maker Pdf
This slide depicts big real-time data streaming use cases and features. It includes various applications such as media streaming, real time analytics, e-commerce purchases, credit card fraud detection and personalized customer experience. Showcasing this set of slides titled Big Real Time Data Streaming Use Cases Ppt Icon Maker Pdf. The topics addressed in these templates are Real Time Analytics, E Commerce Purchases, Credit Card Fraud. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts big real-time data streaming use cases and features. It includes various applications such as media streaming, real time analytics, e-commerce purchases, credit card fraud detection and personalized customer experience.
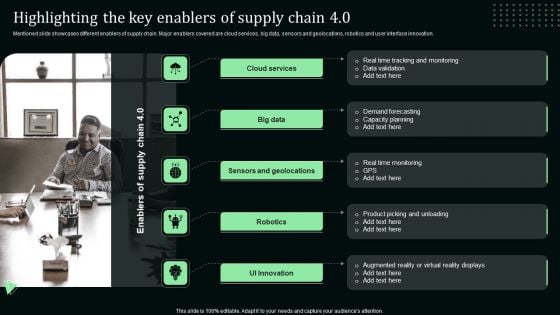
Highlighting The Key Enablers Of Supply Chain 4 0 Stand Out Digital Supply Chain Tactics Enhancing Infographics PDF
Mentioned slide showcases different enablers of supply chain. Major enablers covered are cloud services, big data, sensors and geolocations, robotics and user interface innovation.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Highlighting The Key Enablers Of Supply Chain 4 0 Stand Out Digital Supply Chain Tactics Enhancing Infographics PDF from Slidegeeks and deliver a wonderful presentation.
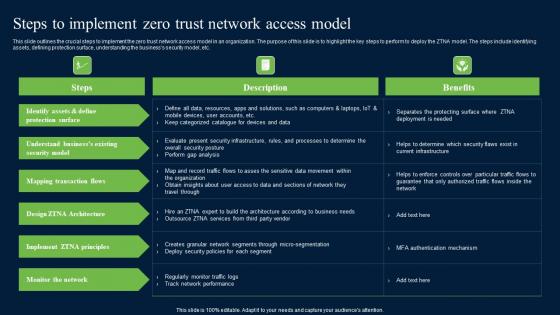
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Quality Assurance Templates Set 3 Harnessing Technology With Quality 4 0 Approach Diagrams PDF
Mentioned slide displays information about harnessing the technology with different quality approaches that results in continuous improvement. Presenting quality assurance templates set 3 harnessing technology with quality 4 0 approach diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like enabling technology, production change, quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Crucial Building Blocks Of Essup Methodology IT Determine Use Case 2 0 Essentials In Essup Elements PDF
This slide provides information regarding use case 2.0 essential in essential unified process in terms of objective, key considerations and key competencies. Get a simple yet stunning designed Crucial Building Blocks Of Essup Methodology IT Determine Use Case 2 0 Essentials In Essup Elements PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Crucial Building Blocks Of Essup Methodology IT Determine Use Case 2 0 Essentials In Essup Elements PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Critical Principles Of Zero Trust Network Access Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Critical Principles Of Zero Trust Network Access Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.
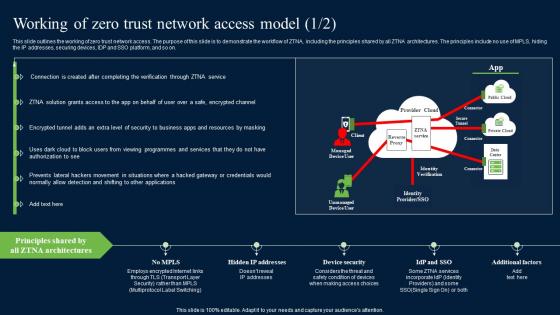
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
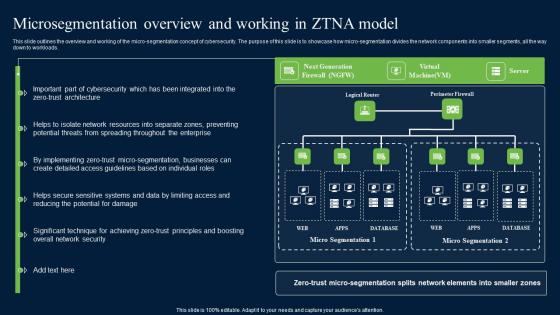
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
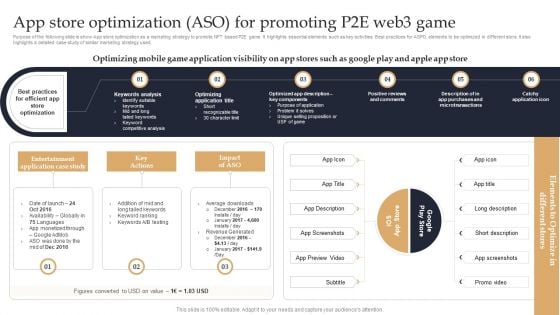
Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan App Store Optimization ASO For Promoting Information PDF
Purpose of the following slide is show account based marketing strategy to promote NFT based P2E game. It highlights essential elements such as key activities social media ads, e-mail campaign. It also highlights a detailed case study of similar marketing strategy used. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan App Store Optimization ASO For Promoting Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Global Gaming Industry Rules PDF
The following slide highlights revenue of gaming industry per country, it segregated these geographical locations on the basis of total revenue potential and number of active players. Slidegeeks is here to make your presentations a breeze with Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Global Gaming Industry Rules PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan PR Awareness Campaign For Promoting Portrait PDF
Purpose of the following slide is show PR awareness campaign as a marketing strategy to promote NFT based P2E game. It highlights essential elements such as key activities guest blogging, partner with P2E brand and media outlet etc. It also highlights a detailed case study of similar marketing strategy used. This modern and well-arranged Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan PR Awareness Campaign For Promoting Portrait PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
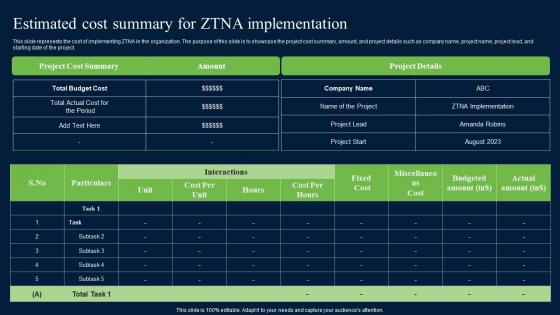
Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.
Stages In Parallel Row Simultaneous Processes Ppt Sample Business Plan Template PowerPoint Slides
We present our stages in parallel row simultaneous processes ppt sample business plan template PowerPoint Slides.Download and present our Symbol PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download and present our Advertising PowerPoint Templates because you have it all down to a nicety, slice by slice, layer by layer. Download our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Business PowerPoint Templates because everybody knows The world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised. Present our Success PowerPoint Templates because your quest has taken you well onto the path of success.Use these PowerPoint slides for presentations relating to Abstract, Advertising, Arrow, Art, Backdrop, Background, Banner, Blank, Blue, Bright, Business, Card, Clean, Color, Concept, Creative, Decoration, Design, Element, Eps10 Vector, Glossy, Graphic, Green, Illustration, Isolated, Label, Message, Modern, Motion, Numbers, Offer, Orange, Page, Paper, Presentation, Shiny, Sign, Space, Step, Style, Symbol. The prominent colors used in the PowerPoint template are Green, Gray, Black. Customers tell us our stages in parallel row simultaneous processes ppt sample business plan template PowerPoint Slides are designed by a team of presentation professionals. Use our Banner PowerPoint templates and PPT Slides are Elegant. PowerPoint presentation experts tell us our stages in parallel row simultaneous processes ppt sample business plan template PowerPoint Slides are Vintage. People tell us our Art PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. We assure you our stages in parallel row simultaneous processes ppt sample business plan template PowerPoint Slides are Cheerful. People tell us our Blue PowerPoint templates and PPT Slides are Tasteful. Get success in a flash with our Stages In Parallel Row Simultaneous Processes Ppt Sample Business Plan Template PowerPoint Slides. Try us out and see what a difference our templates make.
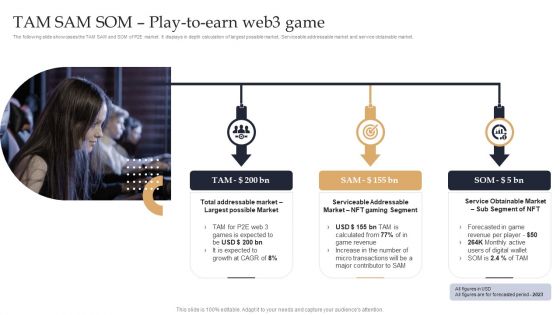
Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan TAM SAM SOM Play To Earn Demonstration PDF
The following slide showcases the TAM SAM and SOM of P2E market. It displays in depth calculation of largest possible market, Serviceable addressable market and service obtainable market. Explore a selection of the finest Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan TAM SAM SOM Play To Earn Demonstration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan TAM SAM SOM Play To Earn Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
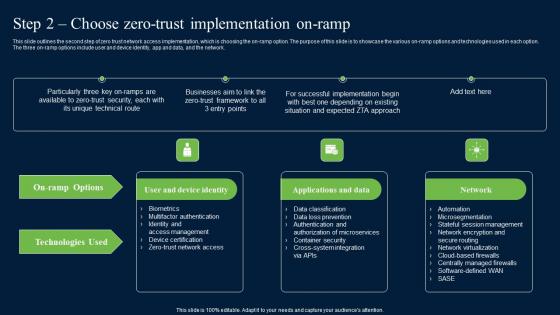
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Road Ahead Timeline Ideas PDF
Welcome to our selection of the Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Road Ahead Timeline Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
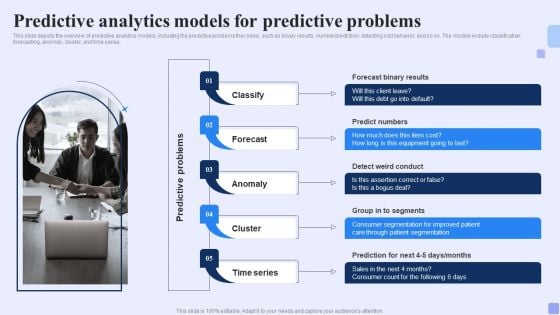
Predictive Analytics Models For Predictive Problems Forward Looking Analysis IT Clipart PDF
This slide depicts the overview of predictive analytics models, including the predictive problems they solve, such as binary results, number prediction, detecting odd behavior, and so on. The models include classification, forecasting, anomaly, cluster, and time series. Are you searching for a Predictive Analytics Models For Predictive Problems Forward Looking Analysis IT Clipart PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Predictive Analytics Models For Predictive Problems Forward Looking Analysis IT Clipart PDF from Slidegeeks today.
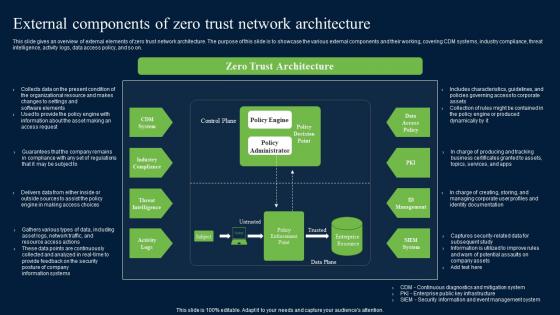
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
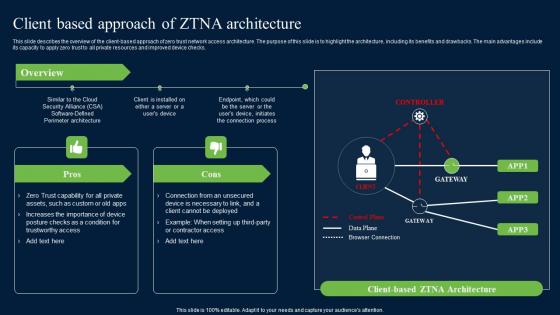
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
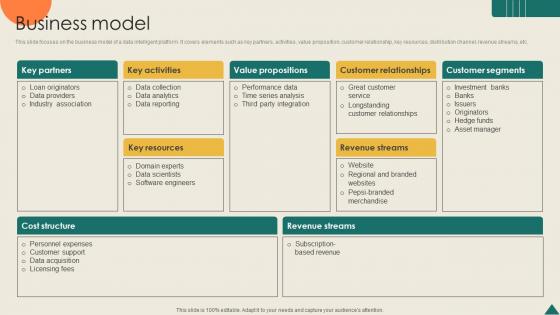
Business Model Financial Analytics Platform Investor Elevator Pitch Deck
This slide focuses on the business model of a data intelligent platform. It covers elements such as key partners, activities, value proposition, customer relationship, key resources, distribution channel, revenue streams, etc. Are you searching for a Business Model Financial Analytics Platform Investor Elevator Pitch Deck that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Business Model Financial Analytics Platform Investor Elevator Pitch Deck from Slidegeeks today. This slide focuses on the business model of a data intelligent platform. It covers elements such as key partners, activities, value proposition, customer relationship, key resources, distribution channel, revenue streams, etc.

Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Discord For P2E Game Marketing For Promoting Summary PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web 3 0 Blockchain Based P2E Mobile Game Sector Report Promotional Plan Discord For P2E Game Marketing For Promoting Summary PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

A50 Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
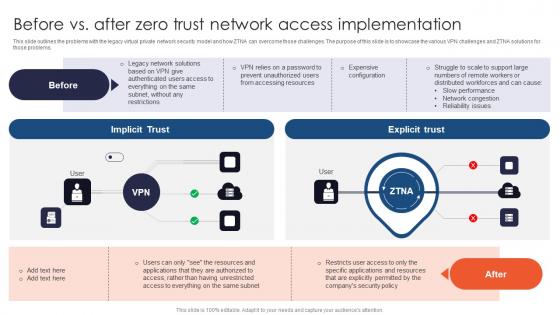
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access Service Initiated Zero Trust Network Topology Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
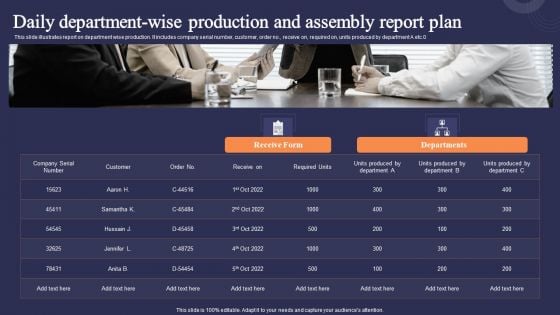
Daily Department Wise Production And Assembly Report Plan Brochure PDF
This slide illustrates report on department wise production. It includes company serial number, customer, order no., receive on, required on, units produced by department A etc 0.Persuade your audience using this Daily Department Wise Production And Assembly Report Plan Brochure PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Produced Department, Receive Form, Customer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides
We present our block to multiple values lin centre and on arms ppt business plan template PowerPoint Slides.Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download our Puzzles or Jigsaws PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Process and Flows PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to abstract, binary, business, code, commerce, communication, computer, concept, connect, connection, corporate, cyberspace, data, digital, download, ecommerce, electronic, futuristic, global, hacker, information, internet, multiple, network, networking, online, program, programming, security, software, tech, technology, values. The prominent colors used in the PowerPoint template are Blue, Gray, White. Get classy with our Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides. They ensure A-list clients.

Table Of Contents For Essential Unified Procedure Essup IT Determine Ppt Ideas Example PDF
Presenting table of contents for essential unified procedure essup it determine ppt ideas example pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like use case 2 0 essentials, component essentials, model essentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
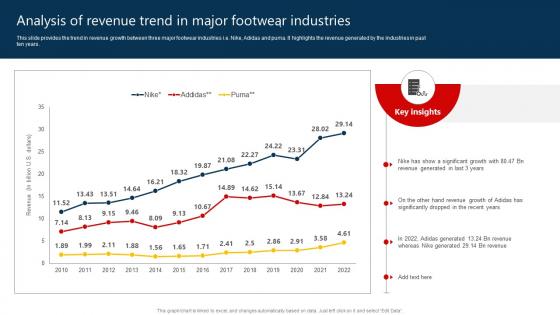
The Marketing Mix Of Analysis Of Revenue Trend In Major Footwear Industries Strategy SS V
This slide provides the trend in revenue growth between three major footwear industries i.e. Nike, Adidas and puma. It highlights the revenue generated by the industries in past ten years. Are you searching for a The Marketing Mix Of Analysis Of Revenue Trend In Major Footwear Industries Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download The Marketing Mix Of Analysis Of Revenue Trend In Major Footwear Industries Strategy SS V from Slidegeeks today. This slide provides the trend in revenue growth between three major footwear industries i.e. Nike, Adidas and puma. It highlights the revenue generated by the industries in past ten years.

Binary Code Matrix Background PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with binary code the internet data transfer a free interpretation Evaluate plans with our Binary Code Matrix Background PowerPoint Templates And PowerPoint Backgrounds 0511. Download without worries with our money back guaranteee.
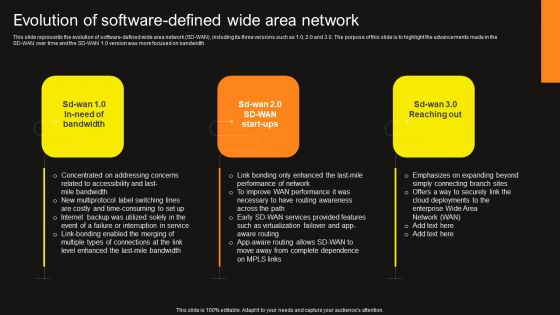
Virtual WAN Architecture Evolution Of Software Defined Wide Area Network Inspiration PDF
This slide represents the evolution of software-defined wide area network sd-wan, including its three versions such as 1 0, 2 0 and 3 0. the purpose of this slide is to highlight the advancements made in the sd-wan over time and the sd-wan 1.0 version was more focused on bandwidth. Welcome to our selection of the Virtual WAN Architecture Evolution Of Software Defined Wide Area Network Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Table Of Contents For Empowering Organization With Zero Trust Network Access Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Empowering Organization With Zero Trust Network Access Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Empowering Organization With Zero Trust Network Access Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
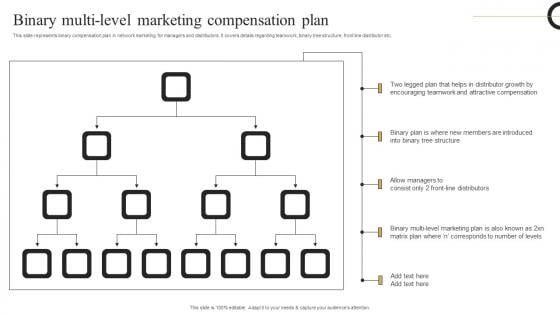
Binary Multi Level Marketing Strategic Plan Develop Multi Level Marketing Template Pdf
This slide represents binary compensation plan in network marketing for managers and distributors. It covers details regarding teamwork, binary tree structure, front line distributor etc. Create an editable Binary Multi Level Marketing Strategic Plan Develop Multi Level Marketing Template Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Binary Multi Level Marketing Strategic Plan Develop Multi Level Marketing Template Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents binary compensation plan in network marketing for managers and distributors. It covers details regarding teamwork, binary tree structure, front line distributor etc.

Zero Based Budgeting Ppt PowerPoint Presentation Pictures Ideas Cpb
Presenting this set of slides with name zero based budgeting ppt powerpoint presentation pictures ideas cpb. This is an editable Powerpoint one stages graphic that deals with topics like zero based budgeting ppt powerpoint presentation pictures ideas cpb to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
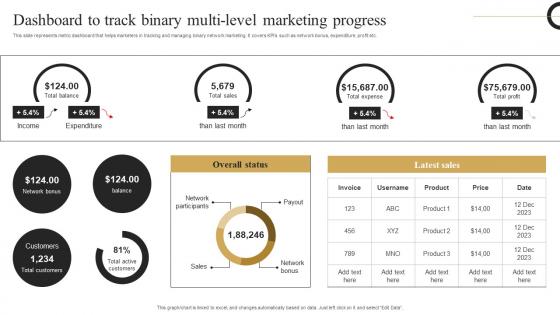
Dashboard Track Binary Multi Strategic Plan Develop Multi Level Marketing Microsoft Pdf
This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Dashboard Track Binary Multi Strategic Plan Develop Multi Level Marketing Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc.
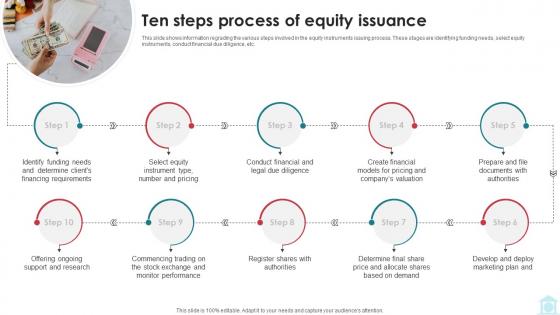
Ten Steps Process Of Equity Issuance Mastering Investment Banking Fin SS V
This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Ten Steps Process Of Equity Issuance Mastering Investment Banking Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc.
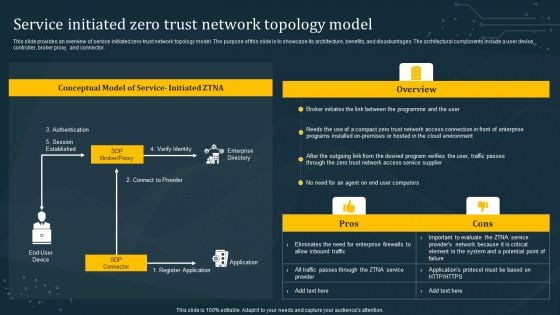
Service Initiated Zero Trust Network Topology Model Clipart PDF
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Get a simple yet stunning designed Service Initiated Zero Trust Network Topology Model Clipart PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Service Initiated Zero Trust Network Topology Model Clipart PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
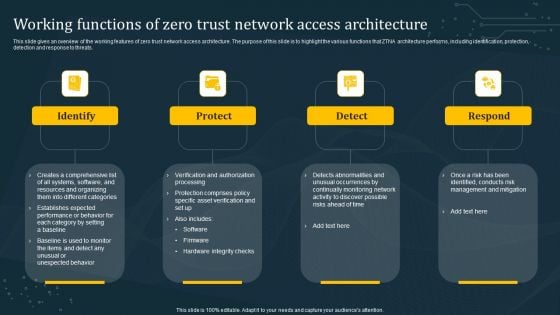
Working Functions Of Zero Trust Network Access Architecture Introduction PDF
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Explore a selection of the finest Working Functions Of Zero Trust Network Access Architecture Introduction PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Working Functions Of Zero Trust Network Access Architecture Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
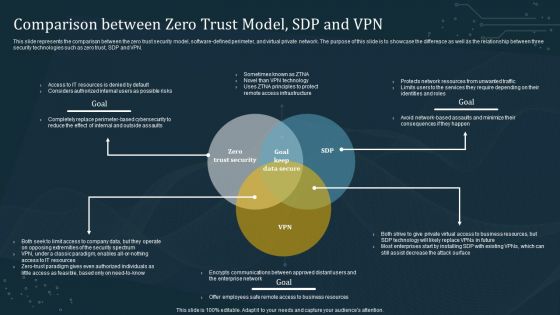
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Low Mass Binary In Powerpoint And Google Slides Cpb
Introducing our well designed Low Mass Binary In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Low Mass Binary. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Low Mass Binary In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
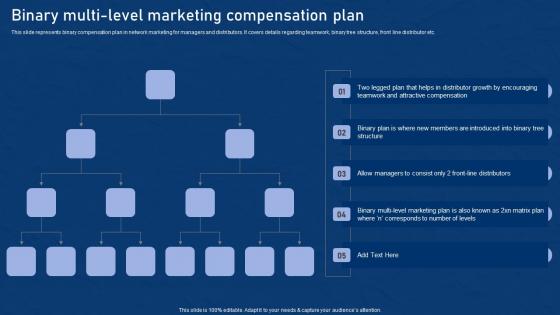
Binary Multi Level Marketing Effective Network Marketing Promotion Tactics Elements Pdf
This slide represents binary compensation plan in network marketing for managers and distributors. It covers details regarding teamwork, binary tree structure, front line distributor etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Binary Multi Level Marketing Effective Network Marketing Promotion Tactics Elements Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents binary compensation plan in network marketing for managers and distributors. It covers details regarding teamwork, binary tree structure, front line distributor etc.
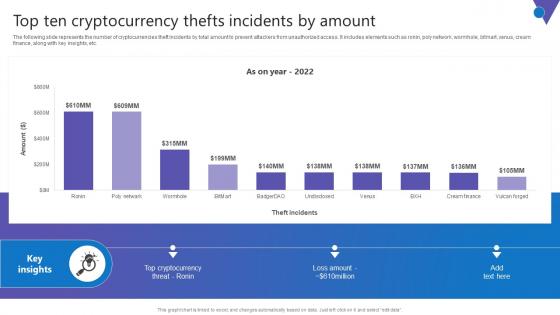
Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc. Want to ace your presentation in front of a live audience Our Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc.
Binary Coding For Information Transfer Vector Icon Ppt PowerPoint Presentation Gallery Skills PDF
Showcasing this set of slides titled binary coding for information transfer vector icon ppt powerpoint presentation gallery skills pdf. The topics addressed in these templates are binary coding for information transfer vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
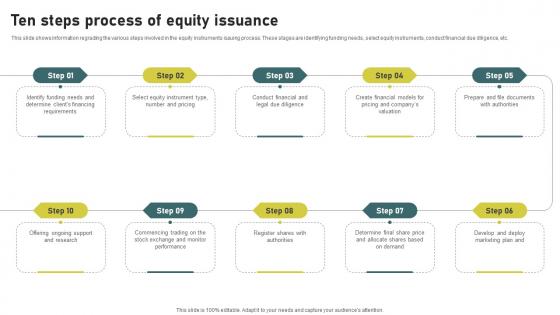
Ten Steps Process Of Equity Issuance Investment Banking Simplified Functions Fin SS V
This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Ten Steps Process Of Equity Issuance Investment Banking Simplified Functions Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc.
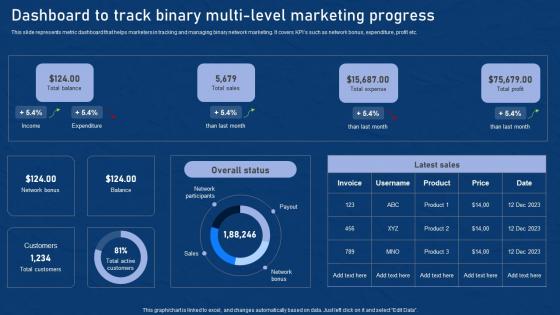
Dashboard To Track Binary Multi Level Effective Network Marketing Promotion Tactics Infographics Pdf
This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Dashboard To Track Binary Multi Level Effective Network Marketing Promotion Tactics Infographics Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Dashboard To Track Binary Multi Level Effective Network Marketing Promotion Tactics Infographics Pdf. This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc.

Dashboard To Track Binary Multi Level Marketing Progress Multi Level Marketing Infographics Pdf
This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Dashboard To Track Binary Multi Level Marketing Progress Multi Level Marketing Infographics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents metric dashboard that helps marketers in tracking and managing binary network marketing. It covers KPIs such as network bonus, expenditure, profit etc.
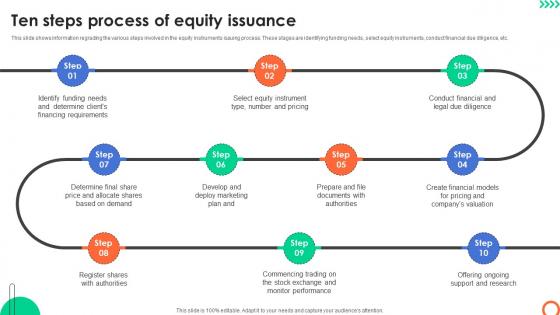
Ten Steps Process Of Equity Issuance Understanding Investment Banking Framework Fin SS V
This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc. Welcome to our selection of the Ten Steps Process Of Equity Issuance Understanding Investment Banking Framework Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide shows information regrading the various steps involved in the equity instruments issuing process. These stages are identifying funding needs, select equity instruments, conduct financial due diligence, etc.
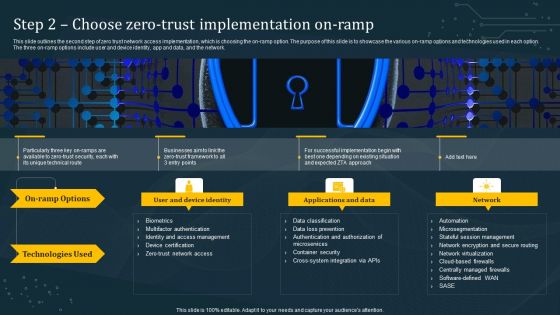
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first


 Continue with Email
Continue with Email

 Home
Home


































