Access Control
CASB 2 0 IT Popular Cloud Access Security Broker Vendors
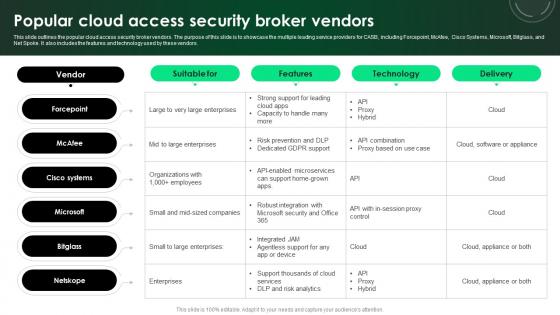
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors.

A47 Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable A47 Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Model Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. The Zero Trust Model Main Pillars Of Zero Network Trust Access is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

Zero Trust Model Comparison Between ZTNA And Secure Access Service
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Comparison Between ZTNA And Secure Access Service and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Zero Trust Model Top Zero Trust Network Access Software Solutions
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Top Zero Trust Network Access Software Solutions and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.
Access Situation In Powerpoint And Google Slides Cpb
Introducing our well-designed Access Situation In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Access Situation. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Access Situation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents Zero Trust Network Access Ppt File Deck
Find highly impressive Table Of Contents Zero Trust Network Access Ppt File Deck on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Zero Trust Network Access Ppt File Deck for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Table Of Contents Zero Trust Network Access Ppt File Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Sharing Access Over Ownership Model Business Case DT SS V
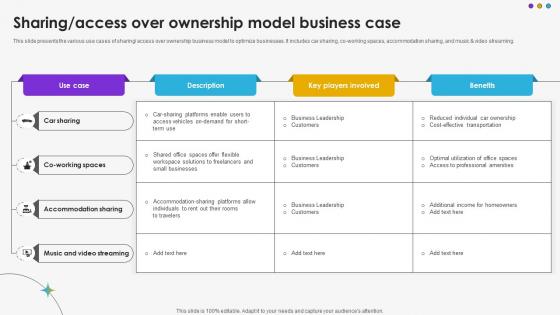
This slide presents the various use cases of sharing or access over ownership business model to optimize businesses. It includes car sharing, co-working spaces, accommodation sharing, and music and video streaming.Want to ace your presentation in front of a live audience Our Sharing Access Over Ownership Model Business Case DT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide presents the various use cases of sharing or access over ownership business model to optimize businesses. It includes car sharing, co-working spaces, accommodation sharing, and music and video streaming.
Icons Slide For Zero Trust Network Access Ppt Diagram Images
Present like a pro with Icons Slide For Zero Trust Network Access Ppt Diagram Images. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Icons Slide For Zero Trust Network Access Ppt Diagram Images are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Zero Trust Network Access ZTNA Introduction
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Zero Trust Network Access ZTNA Introduction to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Zero Trust Network Access ZTNA Introduction. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
Chatgpt Access Websites In Powerpoint And Google Slides Cpb
Introducing our well designed Chatgpt Access Websites In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Chatgpt Access Websites. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Chatgpt Access Websites In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Production Access In Powerpoint And Google Slides Cpb
Introducing our well-designed Production Access In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Production Access. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Production Access In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Overview Sharing Access Over Ownership Business Model DT SS V
This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.This Overview Sharing Access Over Ownership Business Model DT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.
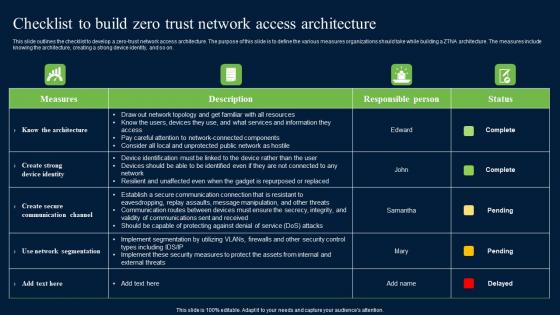
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
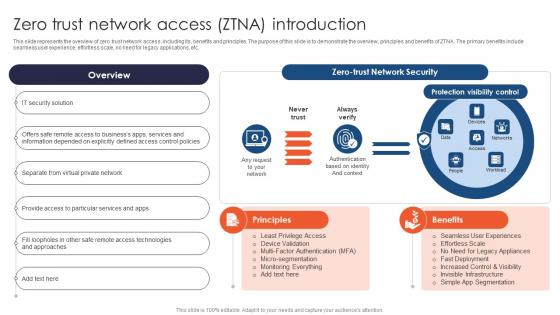
Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Zero Trust Model Technologies Used In Zero Trust Network Access
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Technologies Used In Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Technologies Used In Zero Trust Network Access today and make your presentation stand out from the rest This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.
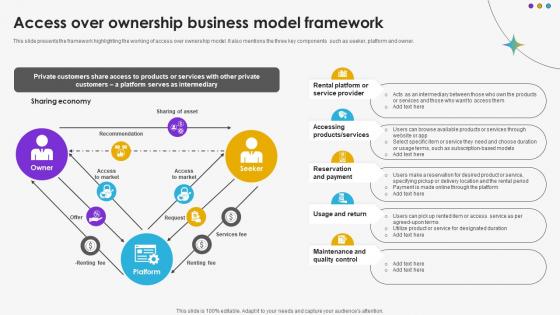
Access Over Ownership Business Model Framework DT SS V
This slide presents the framework highlighting the working of access over ownership model. It also mentions the three key components such as seeker, platform and owner.Find a pre-designed and impeccable Access Over Ownership Business Model Framework DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents the framework highlighting the working of access over ownership model. It also mentions the three key components such as seeker, platform and owner.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.
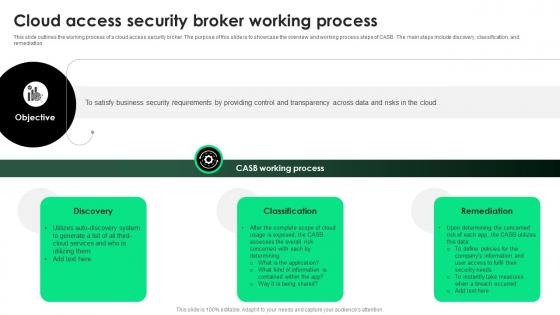
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
Access Services In Powerpoint And Google Slides Cpb
Introducing our well-designed Access Services In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Access Services. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Access Services In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

CASB 2 0 IT Cloud Access Security Broker Architectural Components
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. This modern and well-arranged CASB 2 0 IT Cloud Access Security Broker Architectural Components provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
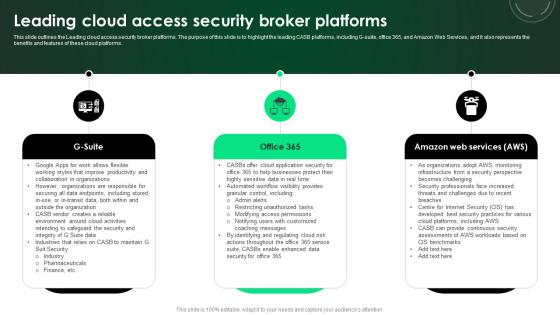
CASB 2 0 IT Leading Cloud Access Security Broker Platforms
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. There are so many reasons you need a CASB 2 0 IT Leading Cloud Access Security Broker Platforms. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
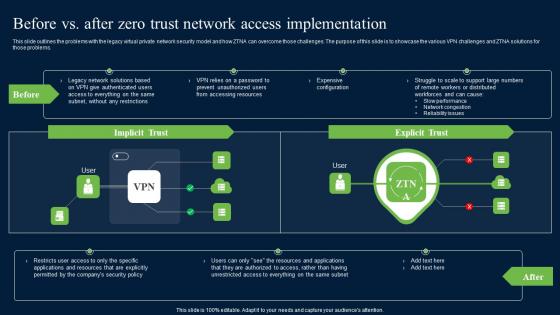
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Journal Access In Powerpoint And Google Slides Cpb
Introducing our well designed Journal Access In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Journal Access. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Journal Access In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
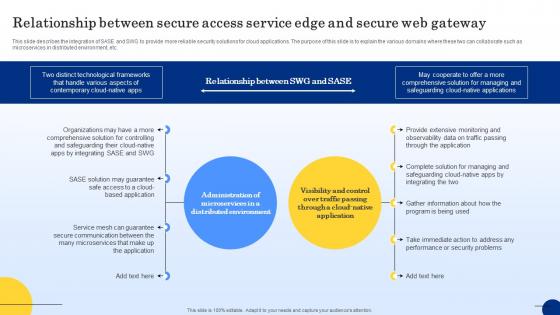
Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.
Access Form Templates Ppt PowerPoint Presentation Layouts Sample Cpb
This is a access form templates ppt powerpoint presentation layouts sample cpb. This is a four stage process. The stages in this process are access form templates.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Virtualbox Internet Access In Powerpoint And Google Slides Cpb
Introducing our well designed Virtualbox Internet Access In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Virtualbox Internet Access. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Virtualbox Internet Access In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
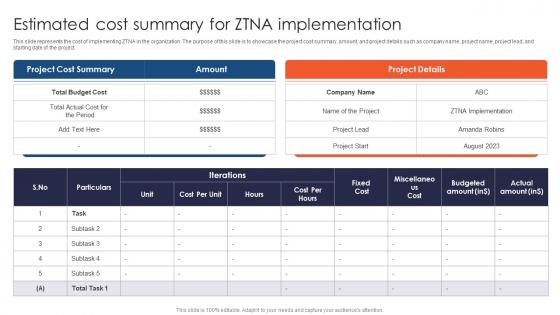
Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Are you searching for a Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation from Slidegeeks today. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges today and make your presentation stand out from the rest This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Zero Trust Model Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Zero Trust Network Access Implementation Challenges from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.
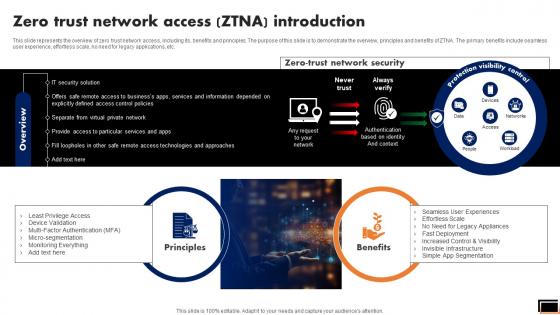
Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
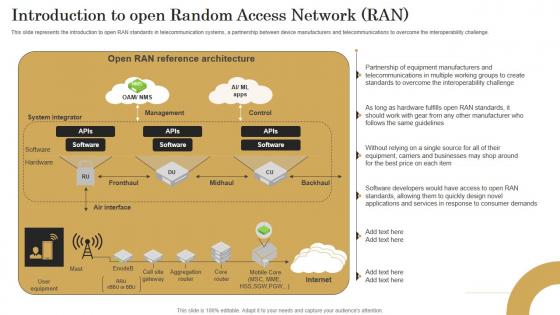
Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Open Random Access Revolutionizing Mobile Networks Ideas PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge.
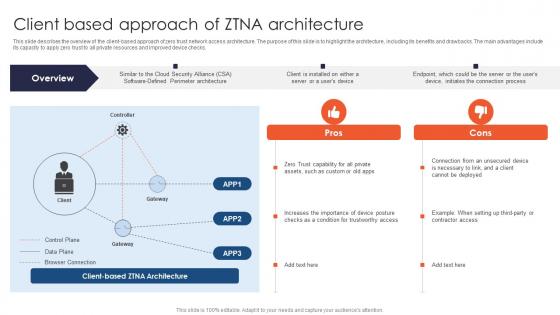
Zero Trust Network Access Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. This modern and well-arranged Zero Trust Network Access Client Based Approach Of ZTNA Architecture provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Take your projects to the next level with our ultimate collection of Zero Trust Network Access Logical Components Of Zero Trust Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
Complete Data Easy Access To Data Ppt Example
This is a complete data easy access to data ppt example. This is a four stage process. The stages in this process are trust data, complete data, easy access to data, intuitive tools.
House Training Program Custom Access Ppt PowerPoint Presentation Show Visuals
This is a house training program custom access ppt powerpoint presentation show visuals. This is a six stage process. The stages in this process are house training program, custom access.
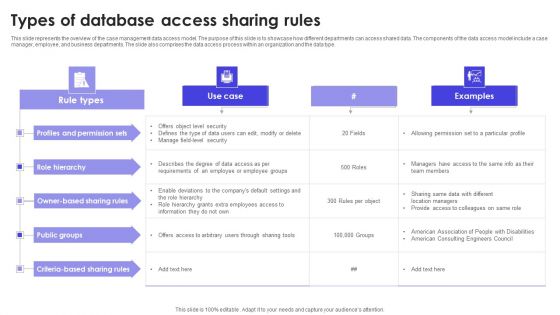
Types Of Database Access Sharing Rules Slides PDF
This slide represents the overview of the case management data access model. The purpose of this slide is to showcase how different departments can access shared data. The components of the data access model include a case manager, employee, and business departments. The slide also comprises the data access process within an organization and the data type. Showcasing this set of slides titled Types Of Database Access Sharing Rules Slides PDF. The topics addressed in these templates are Public Groups, Role Hierarchy, Permission Sets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
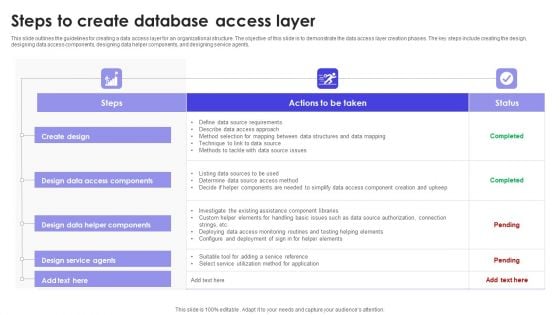
Steps To Create Database Access Layer Slides PDF
This slide outlines the guidelines for creating a data access layer for an organizational structure. The objective of this slide is to demonstrate the data access layer creation phases. The key steps include creating the design, designing data access components, designing data helper components, and designing service agents. Showcasing this set of slides titled Steps To Create Database Access Layer Slides PDF. The topics addressed in these templates are Data Access Components, Create Design, Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
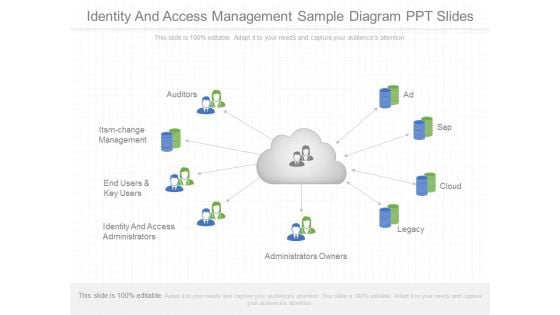
Identity And Access Management Sample Diagram Ppt Slides
This is a identity and access management sample diagram ppt slides. This is a nine stage process. The stages in this process are auditors, itsm change management, end users and key users, identity and access administrators, administrators owners, legacy, cloud, sap, ad.
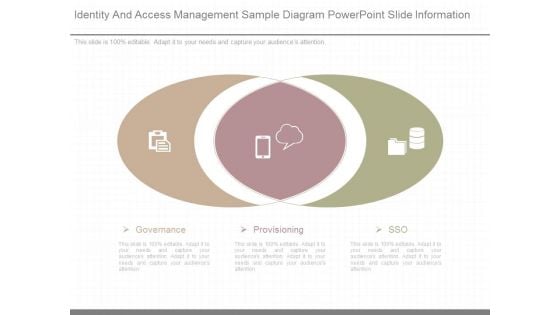
Identity And Access Management Sample Diagram Powerpoint Slide Information
This is a identity and access management sample diagram powerpoint slide information. This is a two stage process. The stages in this process are governance, provisioning, sso.
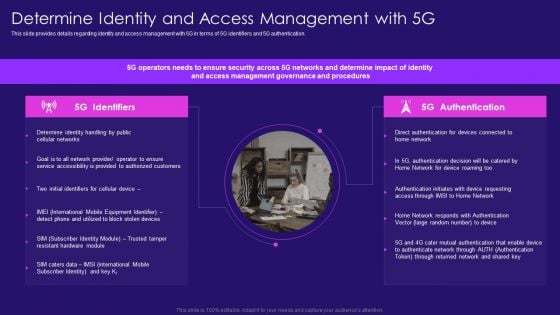
Determine Identity And Access Management With 5G Information PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. Deliver an awe inspiring pitch with this creative Determine Identity And Access Management With 5G Information PDF bundle. Topics like Determine Identity, Accessibility Provided, Identifiers Cellular can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
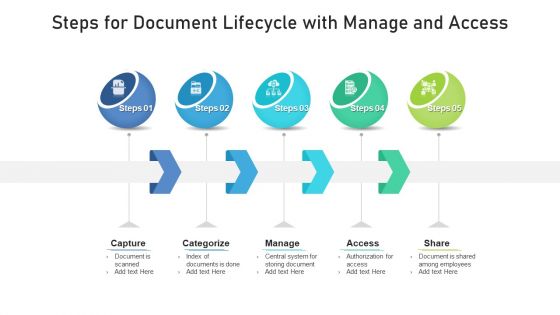
Steps For Document Lifecycle With Manage And Access Template PDF
Presenting steps for document lifecycle with manage and access template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including capture, categorize, manage, access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
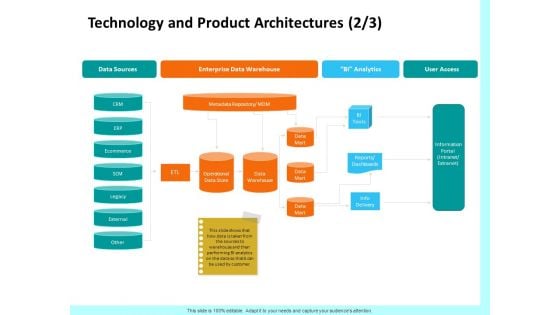
Firm Productivity Administration Technology And Product Architectures Access Background PDF
Presenting this set of slides with name firm productivity administration technology and product architectures access background pdf. This is a one stage process. The stages in this process are data sources, enterprise data warehouse, bi analytics, user access, crm, erp, ecommerce, scm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon For Server Database Access Management Background PDF
Persuade your audience using this Icon For Server Database Access Management Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Server Database, Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Based Identify And Access Management Technique Introduction PDF
Presenting Cloud Based Identify And Access Management Technique Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Based Identify, Access Management, Technique. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































