Access Icon
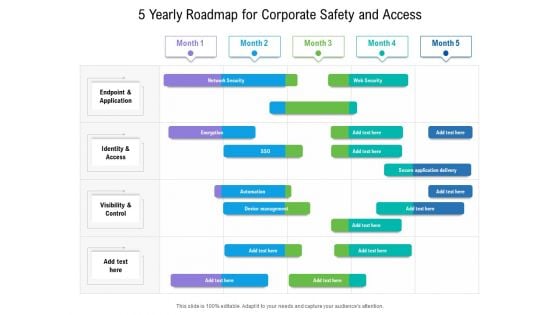
5 Yearly Roadmap For Corporate Safety And Access Sample
We present our 5 yearly roadmap for corporate safety and access sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 5 yearly roadmap for corporate safety and access sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
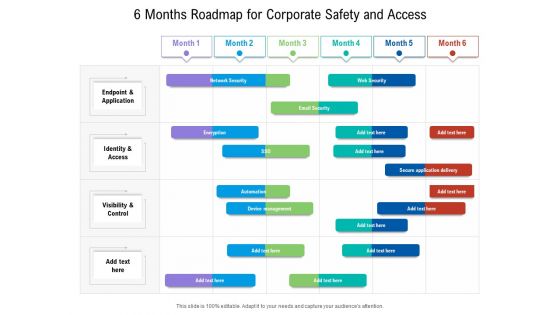
6 Months Roadmap For Corporate Safety And Access Demonstration
We present our 6 months roadmap for corporate safety and access demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months roadmap for corporate safety and access demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
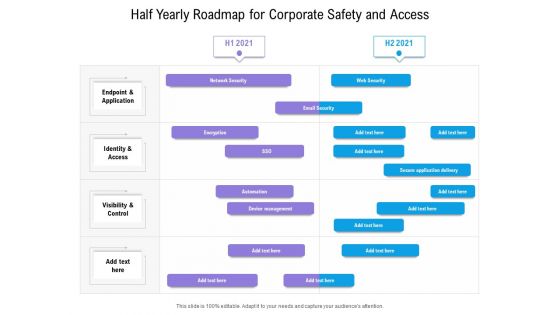
Half Yearly Roadmap For Corporate Safety And Access Ideas
We present our half yearly roadmap for corporate safety and access ideas. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly roadmap for corporate safety and access ideas in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Quarterly Roadmap For Corporate Safety And Access Graphics
We present our quarterly roadmap for corporate safety and access graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly roadmap for corporate safety and access graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Benefits Access Management Ppt PowerPoint Presentation Professional Smartart Cpb
Presenting this set of slides with name benefits access management ppt powerpoint presentation professional smartart cpb. This is an editable Powerpoint four stages graphic that deals with topics like benefits access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
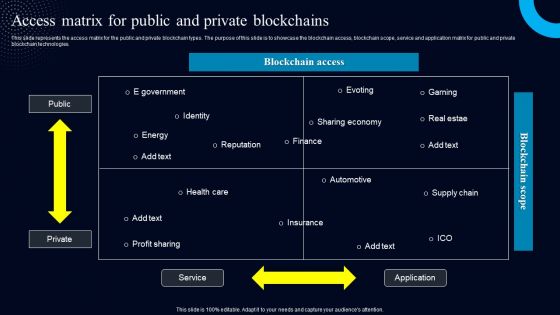
Access Matrix For Public And Private Blockchains Structure PDF
This slide represents the access matrix for the public and private blockchain types. The purpose of this slide is to showcase the blockchain access, blockchain scope, service and application matrix for public and private blockchain technologies. Find a pre-designed and impeccable Access Matrix For Public And Private Blockchains Structure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Access All Areas Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with concept of the internet depicting wide variety of resources available Branch out with our Access All Areas Internet PowerPoint Themes And PowerPoint Slides 0511. You will come out on top.
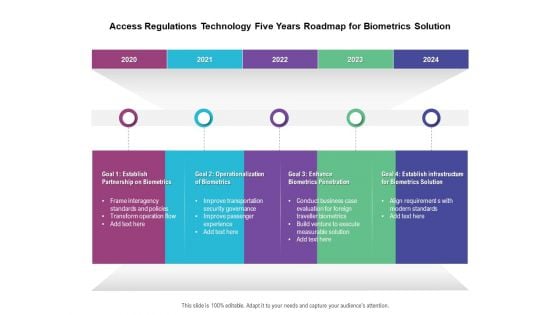
Access Regulations Technology Five Years Roadmap For Biometrics Solution Portrait
We present our access regulations technology five years roadmap for biometrics solution portrait. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched access regulations technology five years roadmap for biometrics solution portrait in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.
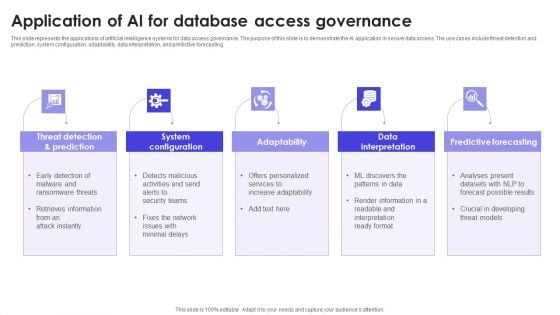
Application Of AI For Database Access Governance Summary PDF
This slide represents the applications of artificial intelligence systems for data access governance. The purpose of this slide is to demonstrate the AI application in secure data access. The use cases include threat detection and prediction, system configuration, adaptability, data interpretation, and predictive forecasting. Presenting Application Of AI For Database Access Governance Summary PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prediction, System Configuration, Adaptability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
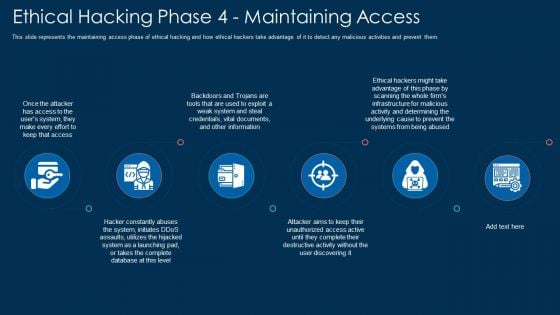
Ethical Hacking Phase 4 Maintaining Access Ppt Professional Grid PDF
This slide represents the maintaining access phase of ethical hacking and how ethical hackers take advantage of it to detect any malicious activities and prevent them. This is a ethical hacking phase 4 maintaining access ppt professional grid pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, determining. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Maximizing Access To Public Information Availability Rules PDF
This slide represents maximizing access to public data availability such as increase data availability, default, public data disclosure, decision making, data quality and data governance. Presenting maximizing access to public information availability rules pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including data governance, data quality, decision making. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
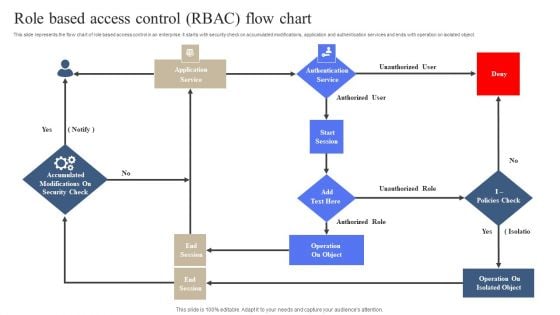
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
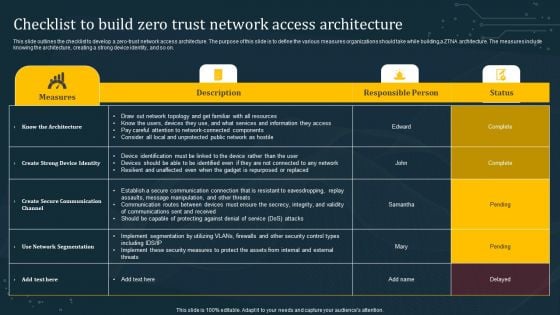
Checklist To Build Zero Trust Network Access Architecture Diagrams PDF
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Build Zero Trust Network Access Architecture Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Checklist To Build Zero Trust Network Access Architecture Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
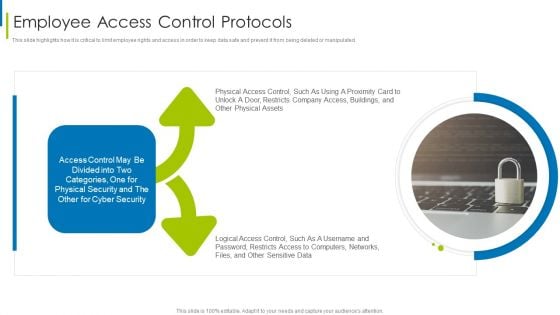
Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a large chrome key protruding out from the window Fight off critics with our Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811. Be confident and convinced of your assessment.
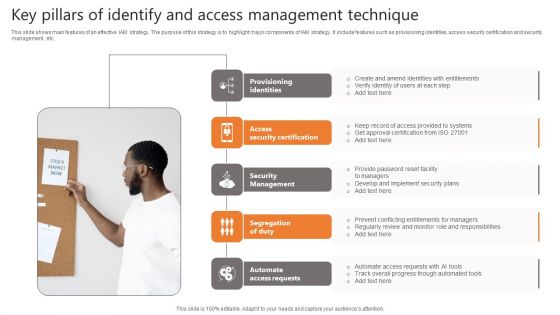
Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top Tenets Of Zero Trust Network Access Model Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Top Tenets Of Zero Trust Network Access Model Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
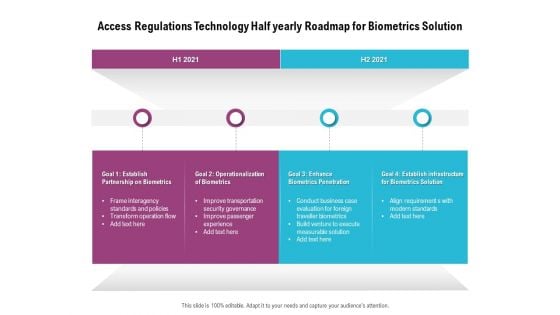
Access Regulations Technology Half Yearly Roadmap For Biometrics Solution Diagrams
Introducing our access regulations technology half yearly roadmap for biometrics solution diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Internet Computer World Access PowerPoint Slides And Ppt Diagram Templates
Internet computer world access PowerPoint Slides And PPT Diagram TemplatesThese high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Fact of the matter is that you have great ideas. Drive this ability home with our Internet Computer World Access PowerPoint Slides And Ppt Diagram Templates.
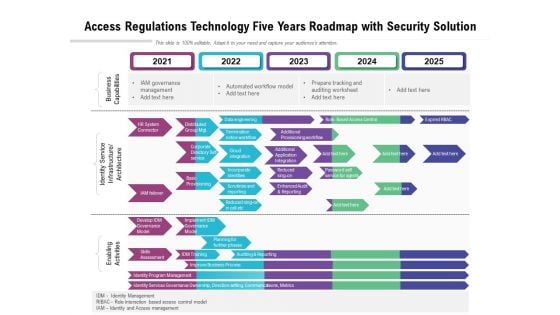
Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
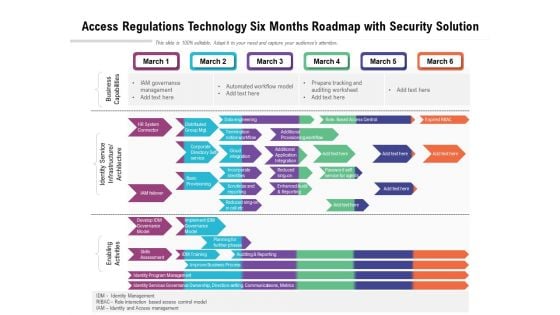
Access Regulations Technology Six Months Roadmap With Security Solution Brochure
Introducing our access regulations technology six months roadmap with security solution brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
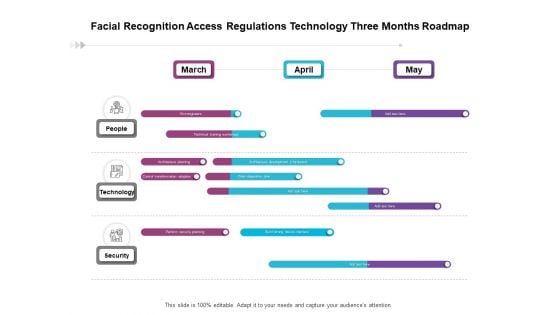
Facial Recognition Access Regulations Technology Three Months Roadmap Formats
Presenting our jaw dropping facial recognition access regulations technology three months roadmap formats. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
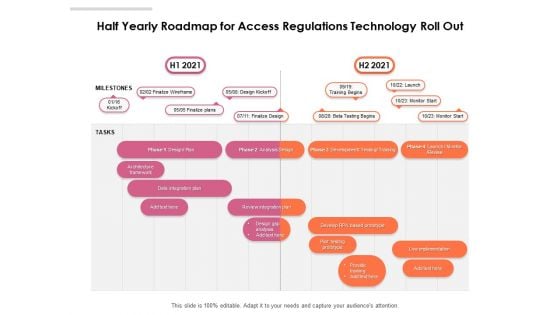
Half Yearly Roadmap For Access Regulations Technology Roll Out Topics
Introducing our half yearly roadmap for access regulations technology roll out topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
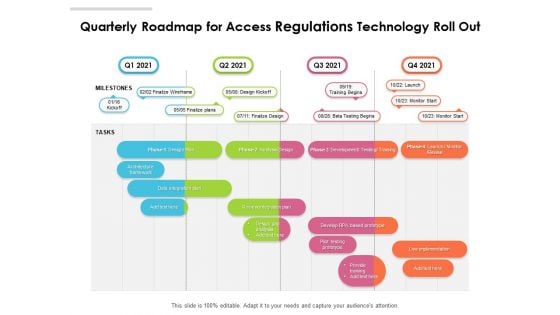
Quarterly Roadmap For Access Regulations Technology Roll Out Demonstration
Presenting our jaw dropping quarterly roadmap for access regulations technology roll out demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Six Months Roadmap For Access Regulations Technology Roll Out Summary
Presenting our innovatively structured six months roadmap for access regulations technology roll out summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
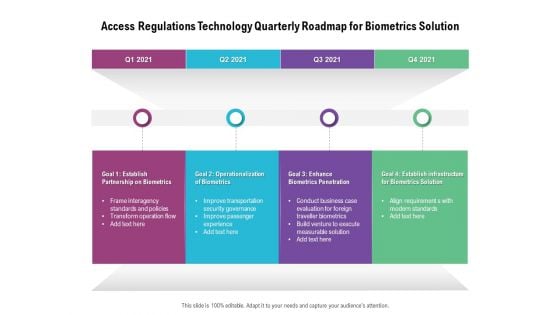
Access Regulations Technology Quarterly Roadmap For Biometrics Solution Background
Presenting our jaw dropping access regulations technology quarterly roadmap for biometrics solution background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
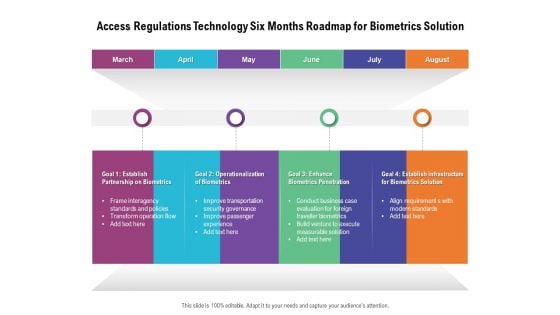
Access Regulations Technology Six Months Roadmap For Biometrics Solution Mockup
Presenting our innovatively structured access regulations technology six months roadmap for biometrics solution mockup Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
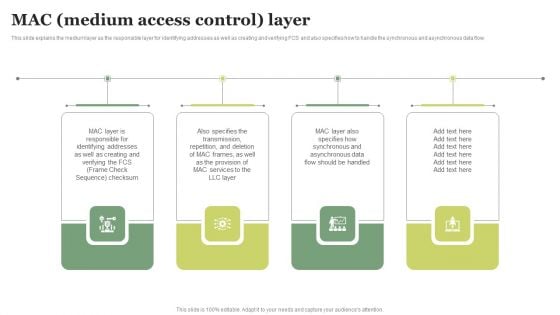
FDDI Deployment Mac Medium Access Control Layer Designs PDF
This slide explains the medium layer as the responsible layer for identifying addresses as well as creating and verifying FCS and also specifies how to handle the synchronous and asynchronous data flow. Whether you have daily or monthly meetings, a brilliant presentation is necessary. FDDI Deployment Mac Medium Access Control Layer Designs PDF can be your best option for delivering a presentation. Represent everything in detail using FDDI Deployment Mac Medium Access Control Layer Designs PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
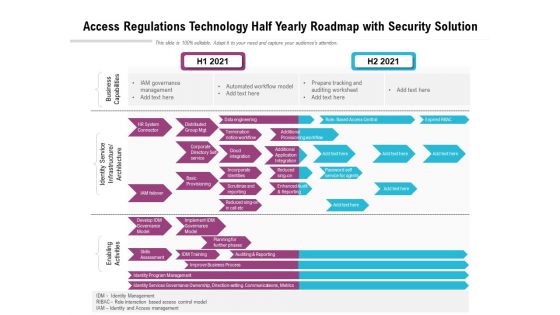
Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
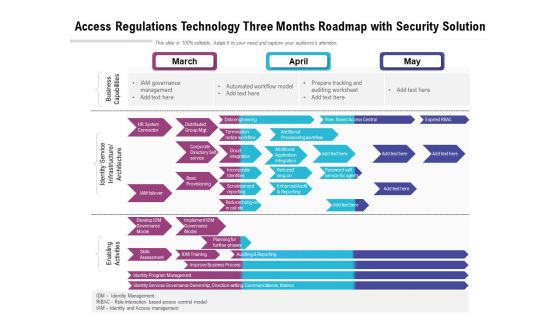
Access Regulations Technology Three Months Roadmap With Security Solution Guidelines
Presenting our jaw dropping access regulations technology three months roadmap with security solution guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
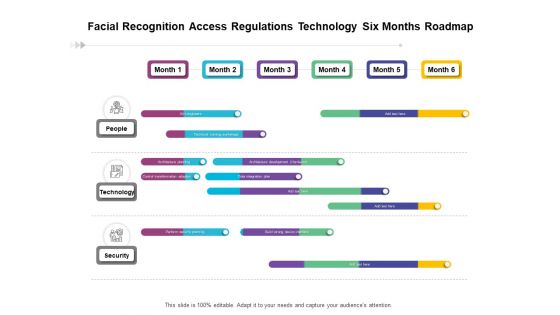
Facial Recognition Access Regulations Technology Six Months Roadmap Background
Presenting the facial recognition access regulations technology six months roadmap background. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
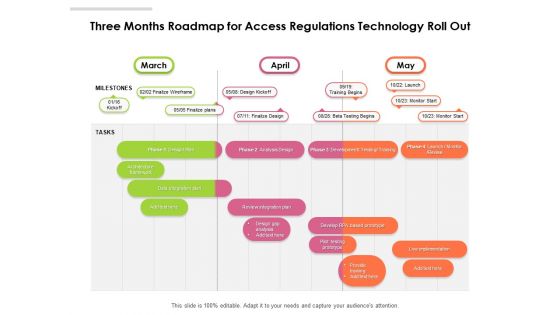
Three Months Roadmap For Access Regulations Technology Roll Out Slides
Presenting the three months roadmap for access regulations technology roll out slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
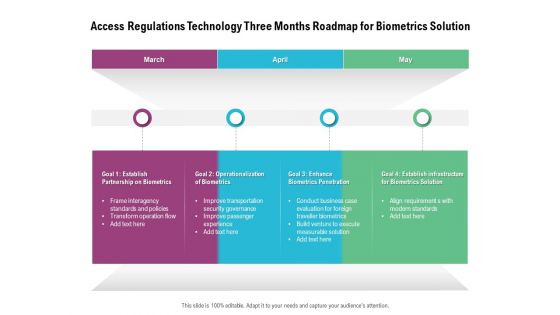
Access Regulations Technology Three Months Roadmap For Biometrics Solution Ideas
Presenting the access regulations technology three months roadmap for biometrics solution ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
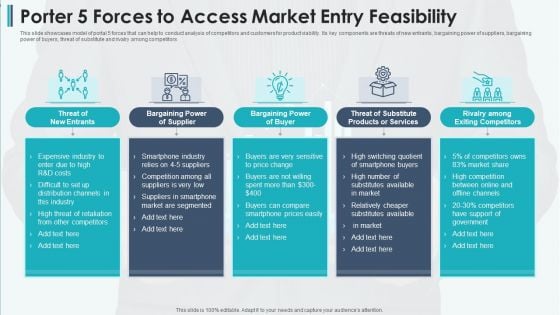
Porter 5 Forces To Access Market Entry Feasibility Professional PDF
This slide showcases model of portal 5 forces that can help to conduct analysis of competitors and customers for product viability. Its key components are threats of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute and rivalry among competitors Presenting porter 5 forces to access market entry feasibility professional pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including bargaining power of supplier, bargaining power of buyer, threat of substitute products or services This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
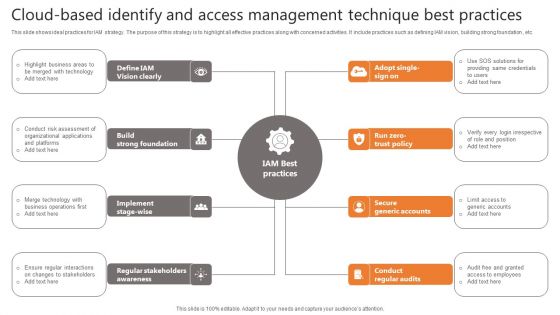
Cloud-Based Identify And Access Management Technique Best Practices Slides PDF
This slide shows ideal practices for IAM strategy. The purpose of this strategy is to highlight all effective practices along with concerned activities. It include practices such as defining IAM vision, building strong foundation , etc. Presenting Cloud-Based Identify And Access Management Technique Best Practices Slides PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Vision Clearly, Strong Foundation, Secure Generic Accounts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Identity Card Employee Access Ppt PowerPoint Presentation Complete Deck
This identity card employee access ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this identity card employee access ppt powerpoint presentation complete deck PPT slideshow.

Access Card Employee Corporate Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this access card employee corporate ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
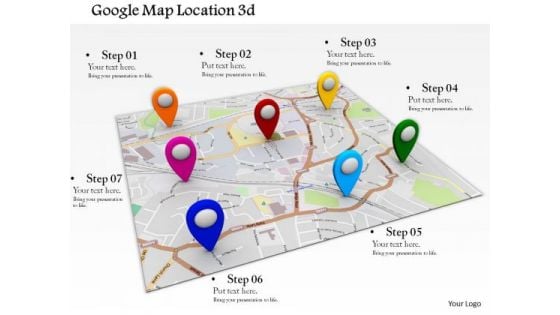
Stock Photo Google Maps Location Access PowerPoint Slide
Use this google maps image slide to make presentations related to technology, satellites, GPS or wireless networks. Design your presentation with this amazing slide and impress your audiences.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
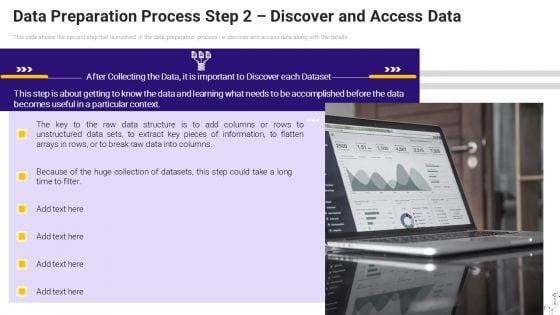
Effective Data Arrangement For Data Accessibility And Processing Readiness Data Preparation Process Step 2 Discover And Access Data Diagrams PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details. This is a effective data arrangement for data accessibility and processing readiness data preparation process step 2 discover and access data diagrams pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data preparation process step 2 discover and access data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
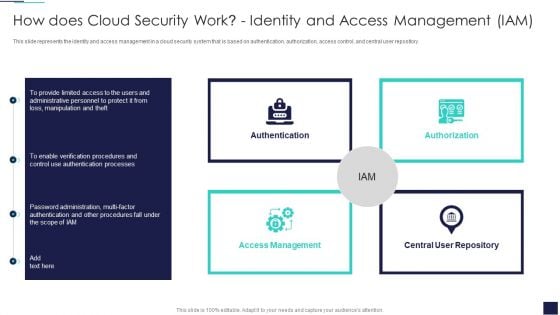
Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
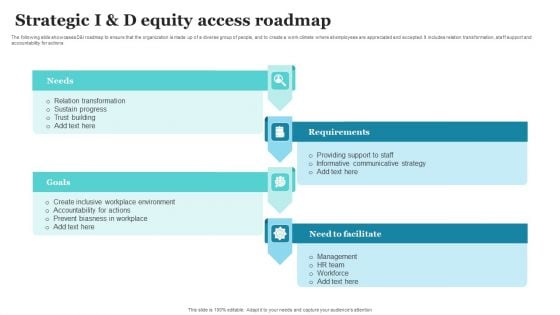
Strategic I And D Equity Access Roadmap Ppt PowerPoint Presentation Gallery Ideas PDF
The following slide showcases DandI roadmap to ensure that the organization is made up of a diverse group of people, and to create a work climate where all employees are appreciated and accepted. It includes relation transformation, staff support and accountability for actions. Presenting Strategic I And D Equity Access Roadmap Ppt PowerPoint Presentation Gallery Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Needs, Requirements, Need To Facilitate, Goals. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ERP Software Solutions With Access Control Ppt PowerPoint Presentation Portfolio Pictures PDF
Presenting erp software solutions with access control ppt powerpoint presentation portfolio pictures pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including access control, human resources, finance accounting, engineering, project management, data services, crm, purchasing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
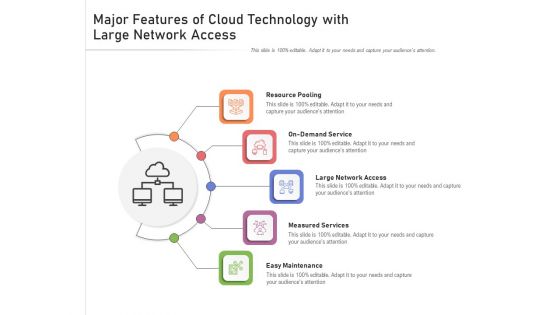
Major Features Of Cloud Technology With Large Network Access Ppt PowerPoint Presentation Gallery Graphics Pictures PDF
Presenting major features of cloud technology with large network access ppt powerpoint presentation gallery graphics pictures pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including resource pooling, on demand service, large network access, measured services, easy maintenance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
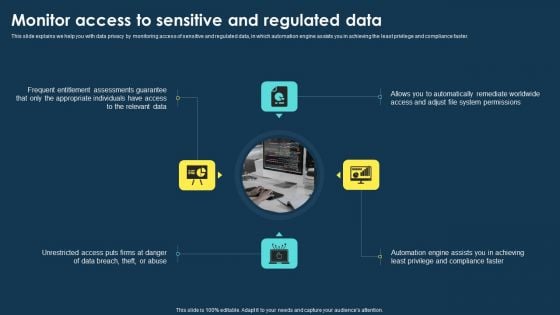
Integrating Data Privacy System Monitor Access To Sensitive And Regulated Data Sample PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. Find a pre-designed and impeccable Integrating Data Privacy System Monitor Access To Sensitive And Regulated Data Sample PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
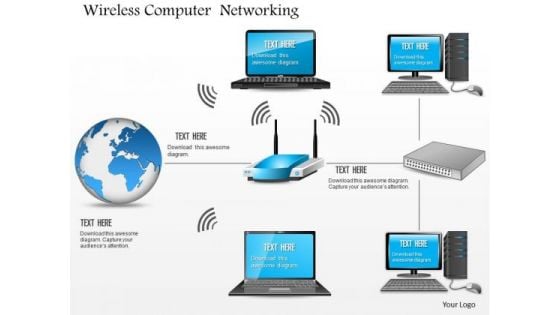
1 Wireless Computer Networking Wifi Access Point Connected To Globe Computers Ppt Slides
This image slide displays wireless computer networking Wi-Fi access point connected to globe computers. This image slide has been designed with graphic of globe, wireless router and various technology devices. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on global, wireless networking in your presentations. This image may also be used in computer education presentations. This image slide will impart professional appearance to your presentations.
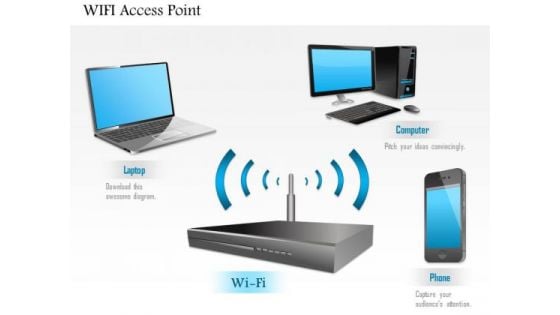
1 Wifi Access Point Connected To Mobile Phone And Laptop Over Wireless Network Ppt Slides
This image slide displays Wi-Fi access point connected various technology devices. This image slide has been designed with graphic of wireless router, mobile phone, laptop and computer. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on wireless networking in your presentations. This image may also be used in computer education presentations. This image slide will impart professional appearance to your presentations.
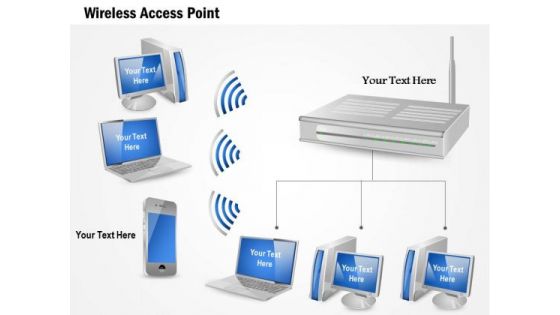
1 Wireles Access Point Communication With Mobile Laptop Desktop Computers Ppt Slide
This image slide displays wireless network. This image slide has been designed with graphic of laptops, desktops, mobile, router and WI-FI signal. You may change color, size and orientation of any icon to your liking. Use this image slide, in your presentations to express views on wireless networking, communication and technology. This image slide will enhance the quality of your presentations.
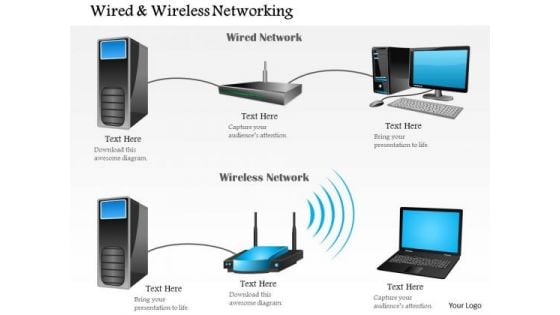
1 Wired And Wireless Networking Shown With Router And Access Point Ppt Slide
This image slide explain the concept of wired and wireless communication. This image slide has been designed with graphic of one wired network with desktop, server and router and one wireless network with server, router and laptop. You may change color, size and orientation of any icon to your liking. Use this image slide, in your presentations to express views on different types of network, communication and technology. This image slide will help you create interesting presentations.
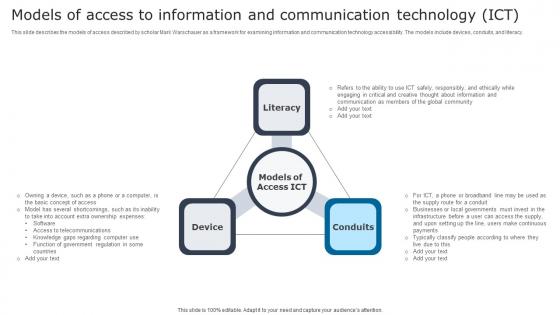
Models Of Access To Information Digital Signage In Internal Communication Channels Slides Pdf
This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy. Want to ace your presentation in front of a live audience Our Models Of Access To Information Digital Signage In Internal Communication Channels Slides Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy.
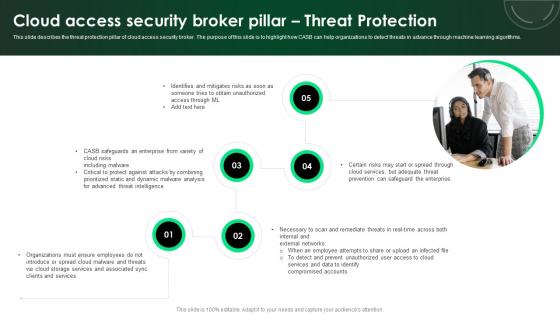
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
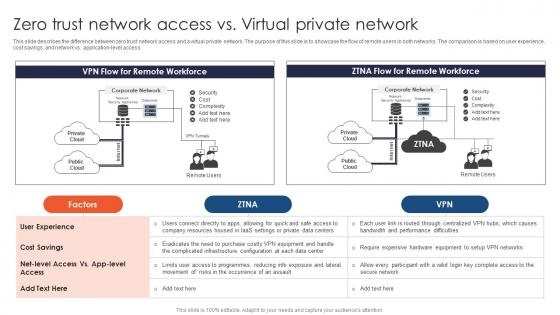
Zero Trust Network Access Vs Virtual Private Network Ppt File Example File
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Are you searching for a Zero Trust Network Access Vs Virtual Private Network Ppt File Example File that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Vs Virtual Private Network Ppt File Example File from Slidegeeks today. This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.

Power BI Restrict Access Report In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Power BI Restrict Access Report In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Power BI Restrict Access Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Power BI Restrict Access Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Zero Trust Network Access Ppt Diagram Lists
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Table Of Contents For Zero Trust Network Access Ppt Diagram Lists can be your best option for delivering a presentation. Represent everything in detail using Table Of Contents For Zero Trust Network Access Ppt Diagram Lists and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. Our Table Of Contents For Zero Trust Network Access Ppt Diagram Lists are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
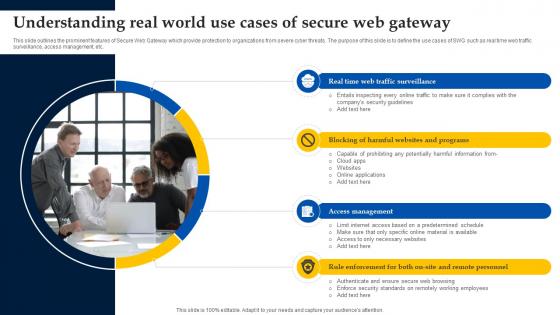
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.

Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Retrieve professionally designed Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Zero Trust Model Top Tenets Of Zero Trust Network Access Model
Find highly impressive Zero Trust Model Top Tenets Of Zero Trust Network Access Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Top Tenets Of Zero Trust Network Access Mode for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Zero Trust Model Top Tenets Of Zero Trust Network Access Model are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP
Find highly impressive Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Web Access Control Solution IT Ppt Powerpoint Presentation Complete Deck With Slides

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

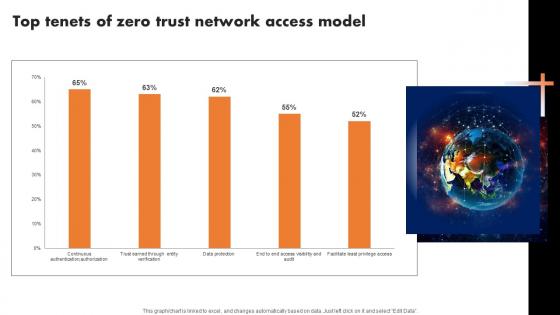
Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf today and make your presentation stand out from the rest This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
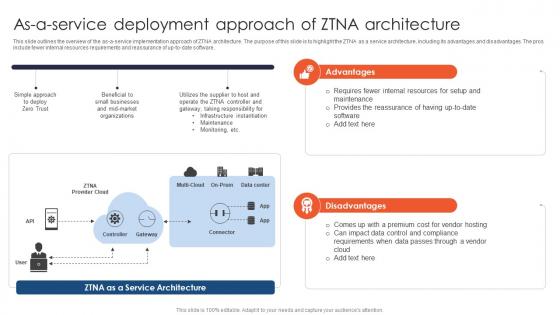
Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
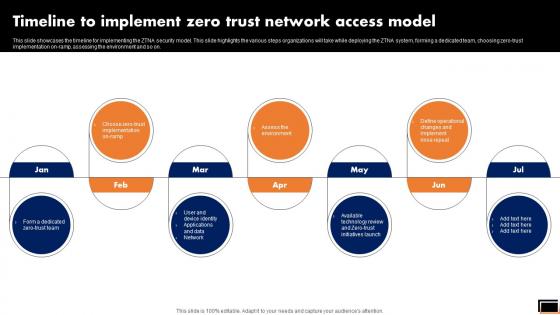
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

Web Access Control Solution Best Practices For Secure Web Gateway Implementation
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Best Practices For Secure Web Gateway Implementation can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Best Practices For Secure Web Gateway Implementation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.

Web Access Control Solution Steps To Select Next Generation Secure Web Gateway
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Steps To Select Next Generation Secure Web Gateway can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Steps To Select Next Generation Secure Web Gateway and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.

Zero Trust Model Reasons To Adopt Zero Trust Network Access Model
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Do you know about Slidesgeeks Zero Trust Model Reasons To Adopt Zero Trust Network Access Model These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.
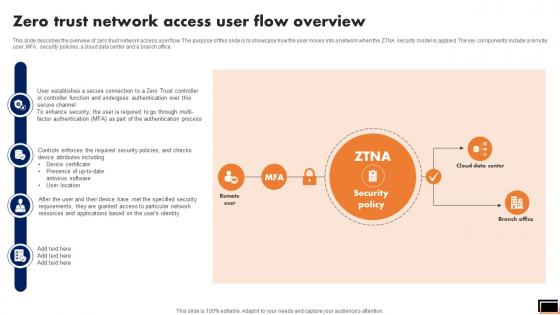
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
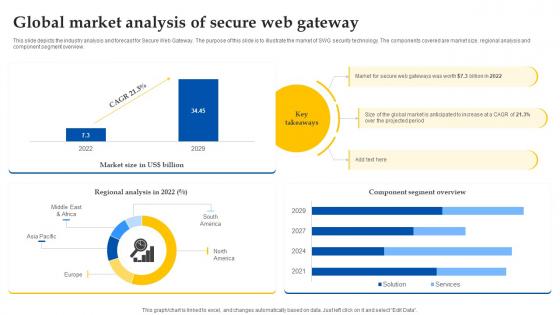
Web Access Control Solution Global Market Analysis Of Secure Web Gateway
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. This Web Access Control Solution Global Market Analysis Of Secure Web Gateway is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Web Access Control Solution Global Market Analysis Of Secure Web Gateway features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.

Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Present like a pro with Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc.
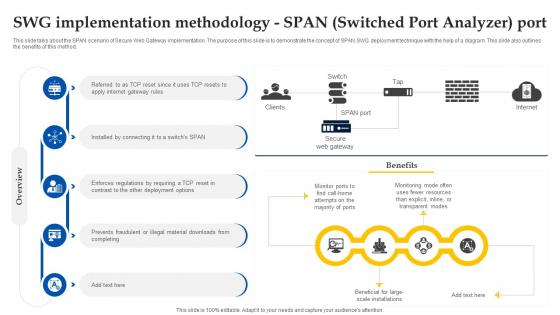
Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find highly impressive Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
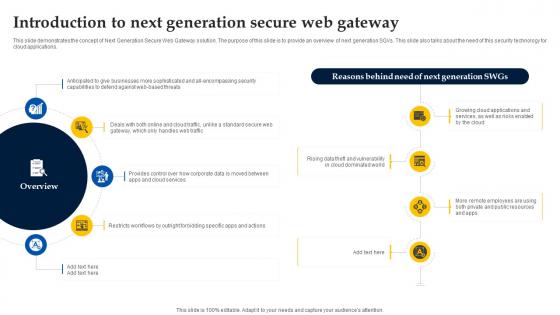
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.
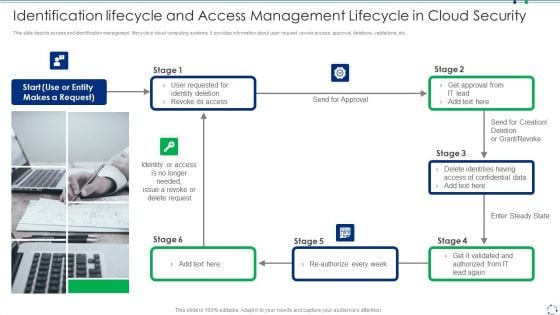
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. There are so many reasons you need a Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.
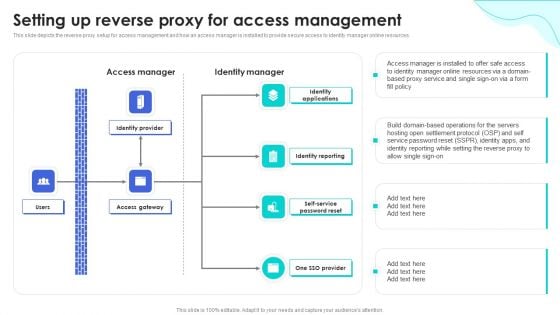
Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Create an editable Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
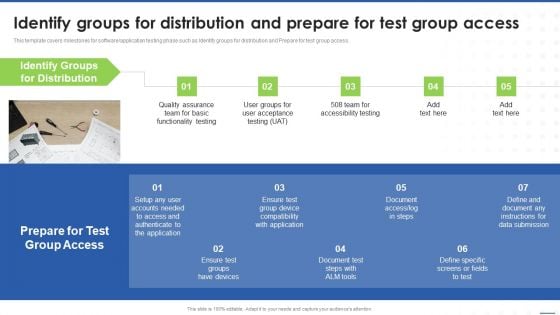
Identify Groups For Distribution And Prepare For Test Group Access Graphics PDF
This template covers milestones for software or application testing phase such as Identify groups for distribution and Prepare for test group access.Deliver an awe inspiring pitch with this creative Identify Groups For Distribution And Prepare For Test Group Access Graphics PDF bundle. Topics like Quality Assurance, Functionality Testing, Accessibility Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
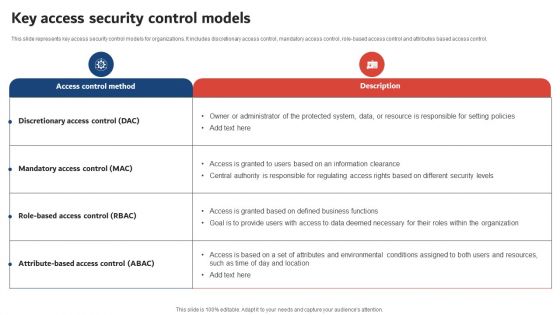
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
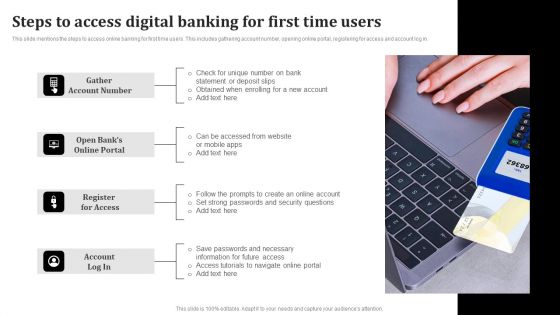
Steps To Access Digital Banking For First Time Users Topics PDF
This slide mentions the steps to access online banking for first time users. This includes gathering account number, opening online portal, registering for access and account log in. Presenting Steps To Access Digital Banking For First Time Users Topics PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Gather Account Number, Register For Access, Account Log In. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Virtual Identify Biometric Access Control With Finger Print Scanner Themes PDF
Presenting virtual identify biometric access control with finger print scanner themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including virtual identify biometric access control with finger print scanner. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
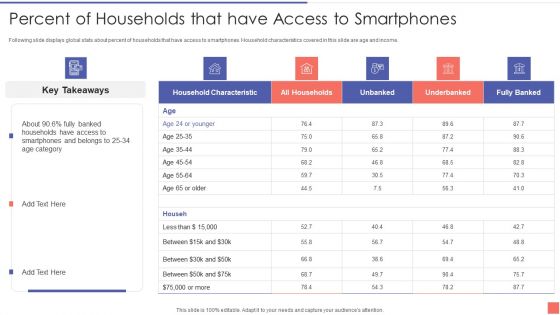
Providing Electronic Financial Services To Existing Consumers Percent Of Households That Have Access Diagrams PDF
Deliver an awe inspiring pitch with this creative Providing Electronic Financial Services To Existing Consumers Percent Of Households That Have Access Diagrams PDF bundle. Topics like Percent Of Households That Have Access To Smartphones can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
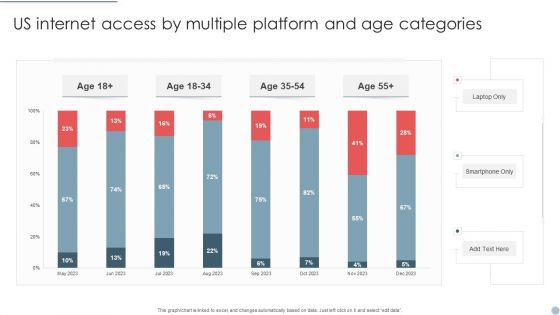
US Internet Access By Multiple Platform And Age Categories Pictures PDF
Pitch your topic with ease and precision using this US Internet Access By Multiple Platform And Age Categories Pictures PDF. This layout presents information on US Internet Access, Multiple Platform, Age Categories. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
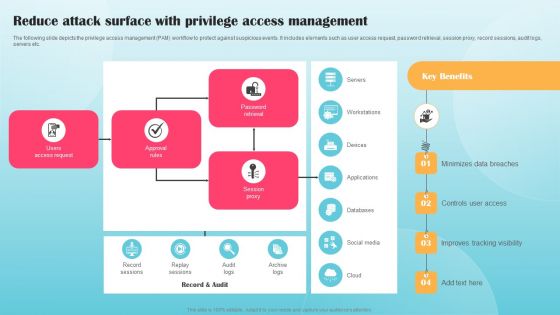
Reduce Attack Surface With Privilege Access Management Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Want to ace your presentation in front of a live audience Our Reduce Attack Surface With Privilege Access Management Ppt PowerPoint Presentation Diagram Graph Charts PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Parked Vehicles With Barrier Security Access Ppt PowerPoint Presentation Gallery Portfolio PDF
Presenting parked vehicles with barrier security access ppt powerpoint presentation gallery portfolio pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including parked vehicles with barrier security access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Finger Print Scanning To Access Virtual Identity Infographics PDF
Presenting smart phone finger print scanning to access virtual identity infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including smart phone finger print scanning to access virtual identity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Wireless Network Security System To Prevent Unauthorized Access To Internet Elements PDF
Presenting wireless network security system to prevent unauthorized access to internet elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system to prevent unauthorized access to internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
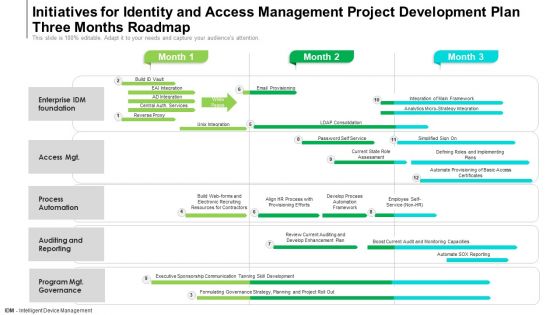
Initiatives For Identity And Access Management Project Development Plan Three Months Roadmap Formats
We present our initiatives for identity and access management project development plan three months roadmap formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for identity and access management project development plan three months roadmap formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
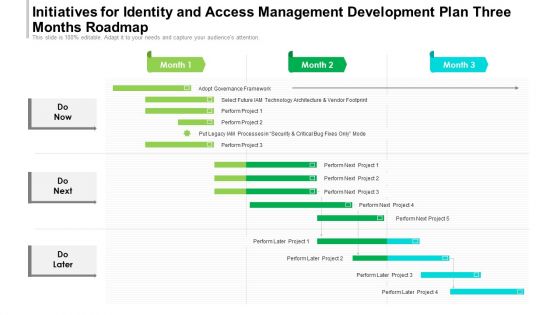
Initiatives For Identity And Access Management Development Plan Three Months Roadmap Introduction
We present our initiatives for identity and access management development plan three months roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for identity and access management development plan three months roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
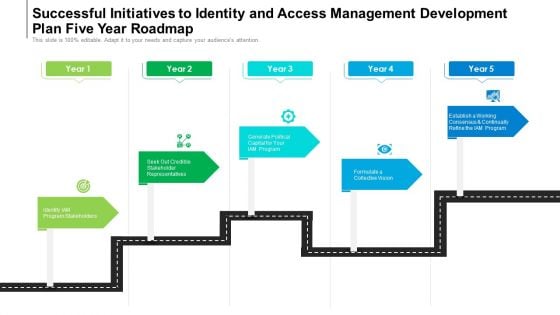
Successful Initiatives To Identity And Access Management Development Plan Five Year Roadmap Infographics
We present our successful initiatives to identity and access management development plan five year roadmap infographics. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched successful initiatives to identity and access management development plan five year roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
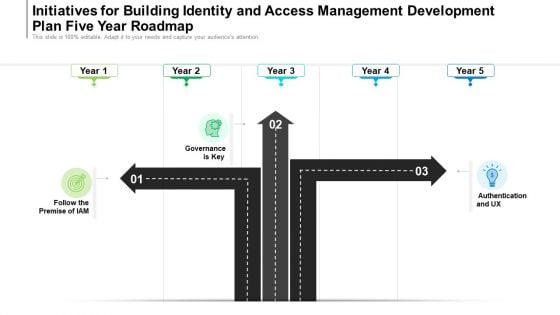
Initiatives For Building Identity And Access Management Development Plan Five Year Roadmap Ideas
We present our initiatives for building identity and access management development plan five year roadmap ideas. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched initiatives for building identity and access management development plan five year roadmap ideas in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

1 Random Access Memory Ram Chip Flash Pcb Pcie Device Ppt Slides
RAM is random access memory which is popularly known as computer memory. This diagram is designed with RAM chip flash PCB PCIE device. This image gives you ideal backdrop to make technology related presentations.

Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. This Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Open Radio Access Network IT Relationship Between Open RAN And Private 5G Themes PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Docsend Capital Raising Pitch Deck Controls For Limiting Doc Access Themes PDF
This slide shows the controls for limiting doc access such as tracking doc forwarding, Expiration dates, etc.Deliver an awe inspiring pitch with this creative Docsend Capital Raising Pitch Deck Controls For Limiting Doc Access Themes PDF bundle. Topics like Expiration Dates, Passcode Required, Download Restrictions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
7 Petal Diagram For Cloud Access With Secure Authentication Ppt PowerPoint Presentation File Designs PDF
Persuade your audience using this 7 petal diagram for cloud access with secure authentication ppt powerpoint presentation file designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including 7 petal diagram for cloud access with secure authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
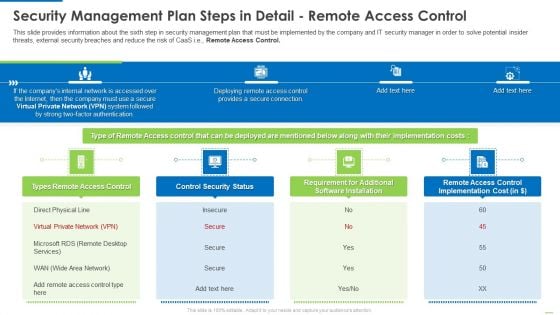
Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Introduction To Mobile Money In Developing Countries Percent Of Households That Have Access Diagrams PDF
Following slide displays global stats about percent of households that have access to smartphones. Household characteristics covered in this slide are age and income.Deliver and pitch your topic in the best possible manner with this introduction to mobile money in developing countries percent of households that have access diagrams pdf Use them to share invaluable insights on household characteristic, unbanked, fully banked and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
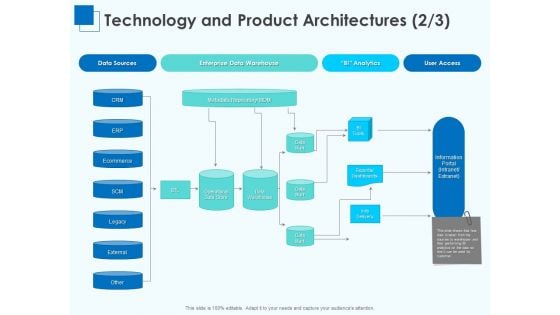
Corporate Intelligence Business Analysis Technology And Product Architectures Access Inspiration PDF
Presenting corporate intelligence business analysis technology and product architectures access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data sources, enterprise data warehouse, analytics, user access. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
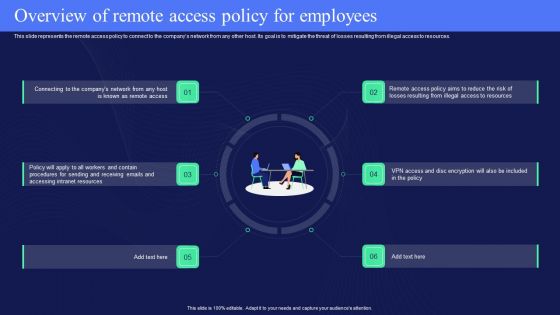
IT Policies And Procedures Overview Of Remote Access Policy For Employees Template PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. Retrieve professionally designed IT Policies And Procedures Overview Of Remote Access Policy For Employees Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
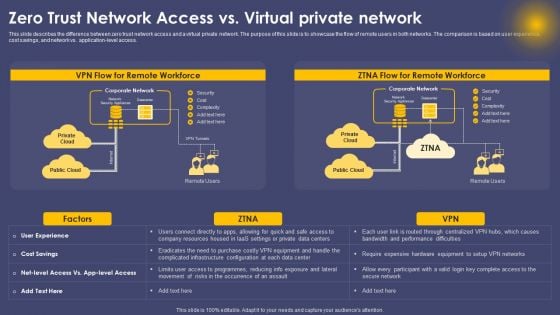
Zero Trust Network Access Vs Virtual Private Network Ppt Layouts Graphics Tutorials PDF
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Retrieve professionally designed Zero Trust Network Access Vs Virtual Private Network Ppt Layouts Graphics Tutorials PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Person Opening Office Door With Security Access Control System Ppt PowerPoint Presentation Styles Rules PDF
Presenting person opening office door with security access control system ppt powerpoint presentation styles rules pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including person opening office door with security access control system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Model Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Critical Principles Of Zero Trust Network Access Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Critical Principles Of Zero Trust Network Access Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
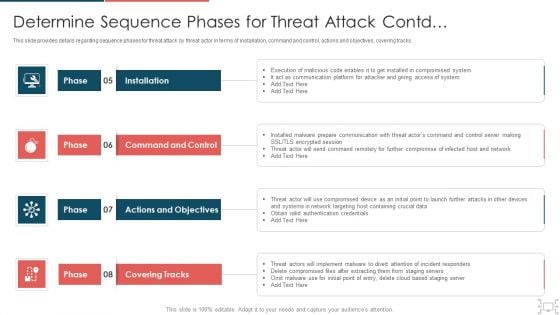
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Preparation Infrastructure And Phases Data Preparation Process Step 2 Discover And Access Data Brochure PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details.Presenting Data Preparation Infrastructure And Phases Data Preparation Process Step 2 Discover And Access Data Brochure PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Preparation Process, Existing Catalogue, Analysts Aware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
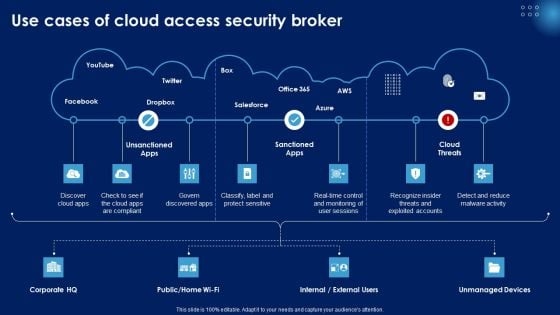
Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
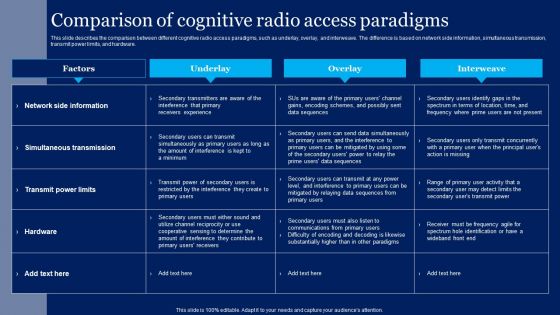
Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. Get a simple yet stunning designed Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
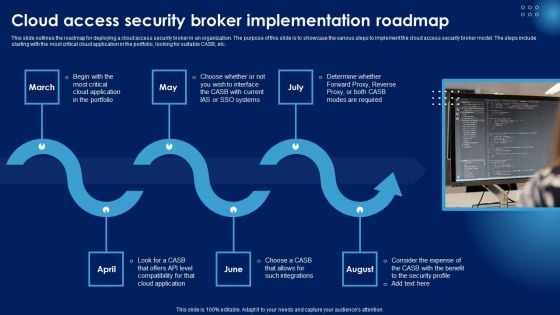
Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF
This slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Get a simple yet stunning designed Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
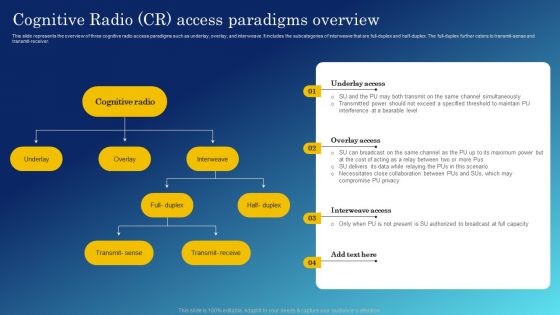
Cognitive Sensing Innovation Cognitive Radio CR Access Paradigms Overview Professional PDF
Empowering Organization With Zero Trust Network Access Table Of Contents Themes PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Empowering Organization With Zero Trust Network Access Table Of Contents Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Empowering Organization With Zero Trust Network Access Table Of Contents Themes PDF.

Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF
This slide represents the timeline for open random access network deployment, including the steps to be performed to effectively implement open RAN, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

 Home
Home